Research shows that more than five billion people now have internet access. This statistic includes young children watching Cocomelon, students completing their homework, and working professionals from various fields. Unfortunately, bad actors with malicious intent are also online. While Apple’s system is known for its robust security features, it’s not immune to infections.
Cybercriminals employ a range of cyberattacks, with phishing being one of the most common. If left unchecked, hackers can steal and exploit sensitive data. Fortunately, there are several best practices for phishing protection that Mac users can follow. Let’s dive in.
What Is Phishing?
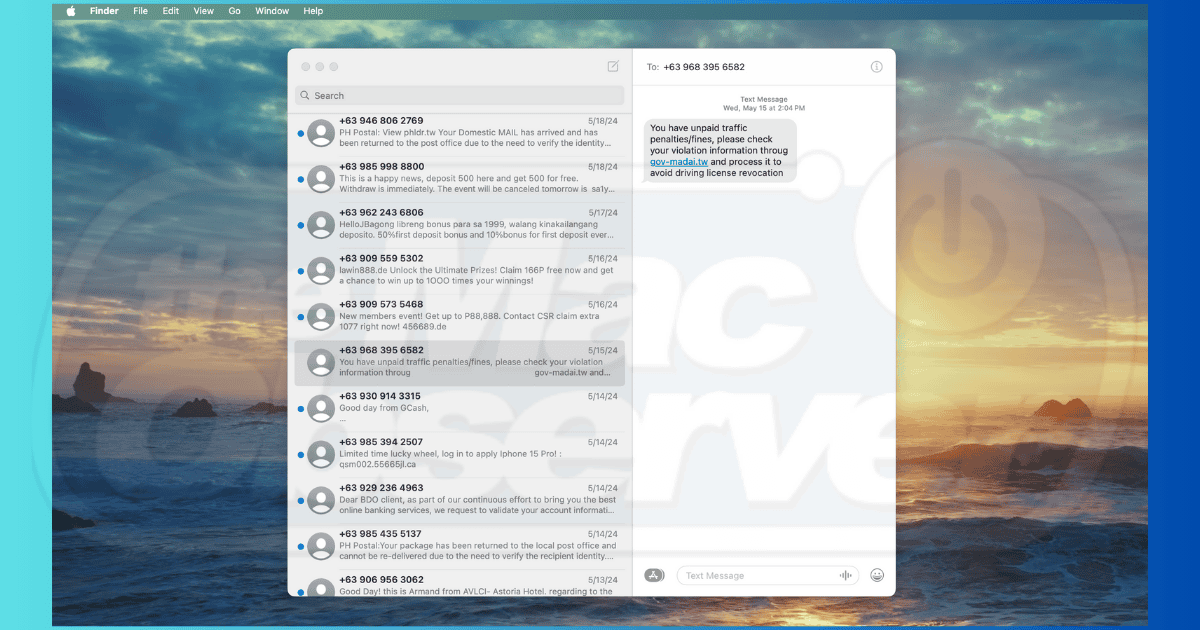
At a basic level, phishing is a type of cyber scam where criminals trick you into divulging personal information. They send emails or messages masquerading as someone you’ll likely trust, such as your bank or a known company. These deceptive messages will likely ask you to click on a link or download an attachment. Once you do, they can use malware-infected pop-ups, file downloads, and web pages to crawl your device.
How To Prevent Phishing
Phishing is avoidable as long as you know what to watch out for and how to block this deceptive ploy.
1. Learn How To Recognize Phishing
Try to spot suspicious emails and messages that are most likely phishing attempts. For instance, I always notice grammar mistakes, which are usually obvious and intentional. They’re designed that way to filter out people who won’t notice them because they also won’t notice other red flags
Watch out for urgent requests and other statements that convince you to take immediate action. Likewise, be wary of unfamiliar sender addresses—if it seems fishy, it probably is.
2. Install Antivirus Software
You can use good antivirus software to catch phishing attempts. For instance, Intego Antivirus is designed to filter out suspicious files and links and prevent them from doing any damage. It will also scan for malware that hackers might have installed on your Mac when you’ve clicked a link or downloaded a file.
3. Practice Proper Cyber Hygiene Practices
Proper cyber hygiene means being cautious with your online activities. Be careful with the personal information you share, double-check the sites you visit, and never click on random hyperlinks.
It’s also helpful if you use strong, unique passwords. Make sure that they don’t contain any of your personal information and that you have a different password for each of your accounts.
You can use Keychain Access on your Mac to manage your passwords, so you don’t have to remember all of them. With your iCloud Keychain turned on, you can create more complex passwords.
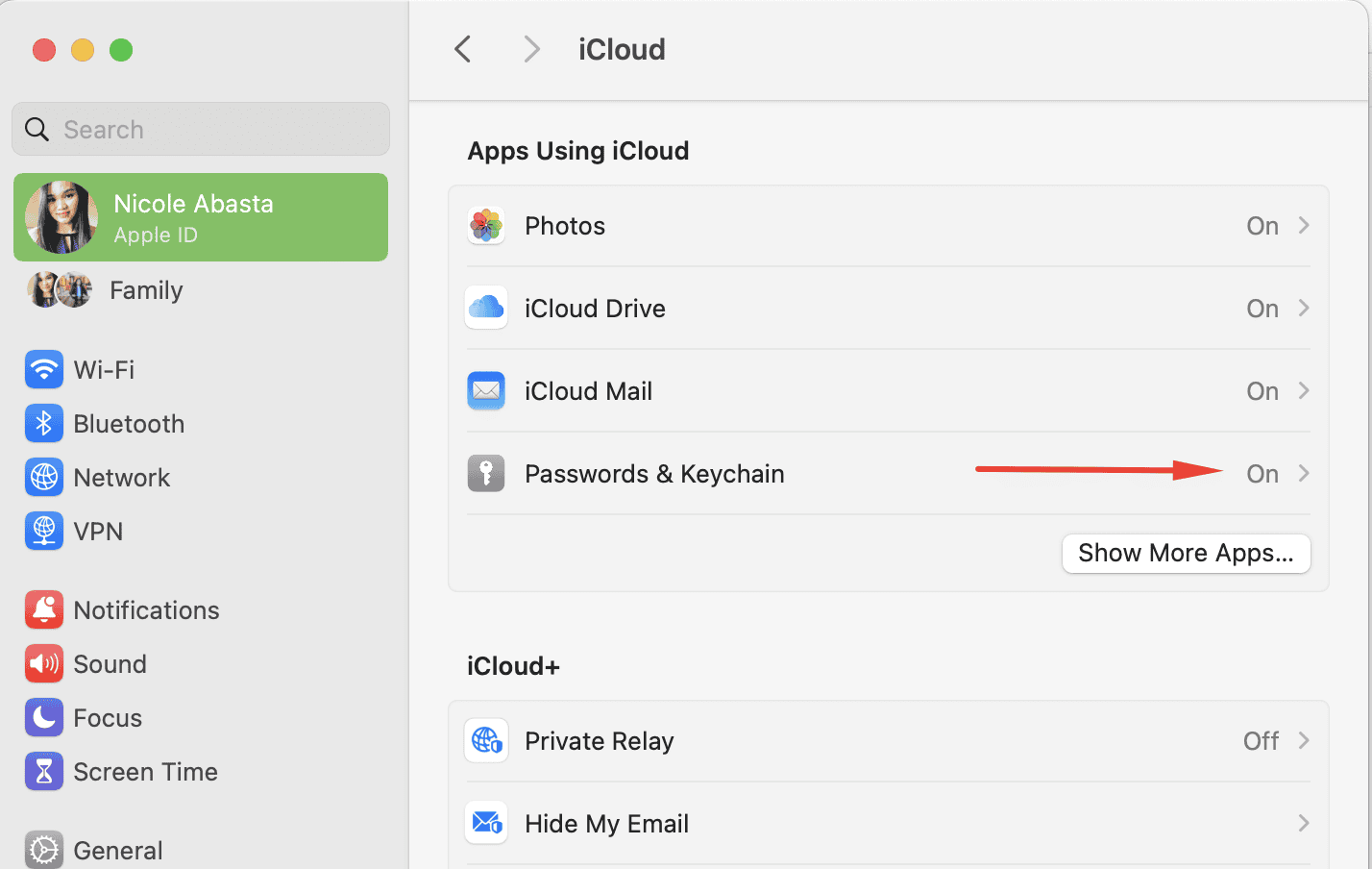
Here’s how to set up iCloud Keychain:
- Go to Systems Settings.
- Click your Apple ID profile, then choose iCloud.
- Toggle on Passwords & Keychain.
When you visit a website or an email platform, and you log in, an option to save the password will pop up. Choose to save it, and it will be stored in your keychain. It will then autofill your information on any device that you approve.
4. Keep Your Apps And Software Up-To-Date
Apps and software developers regularly release updates to fix security holes that hackers could exploit. Set your Mac to update automatically to ensure you’re always protected against sophisticated phishing threats.
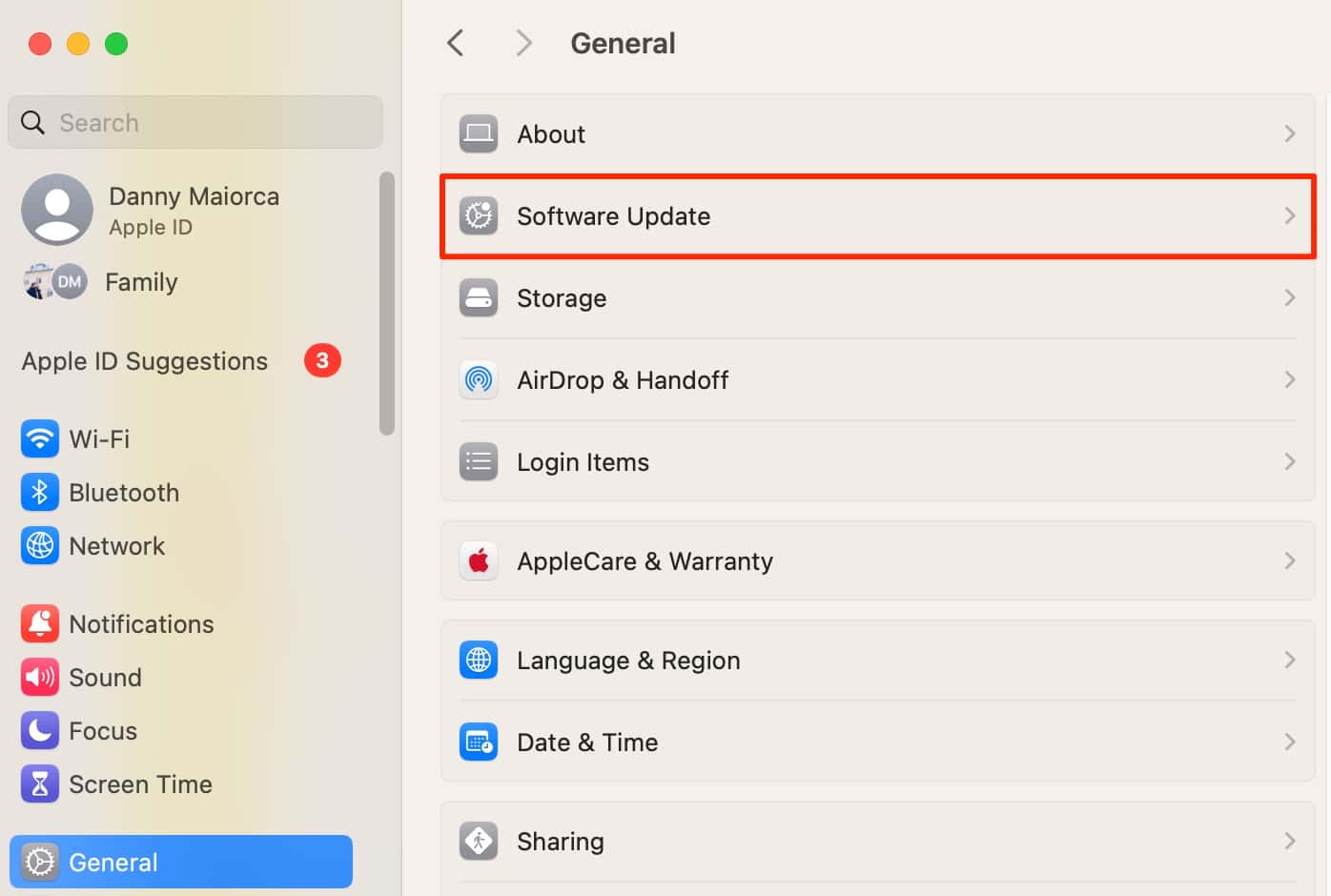
- Go to Systems Settings.
- Click General, then click Software Update.
- Toggle on Automatic Updates.
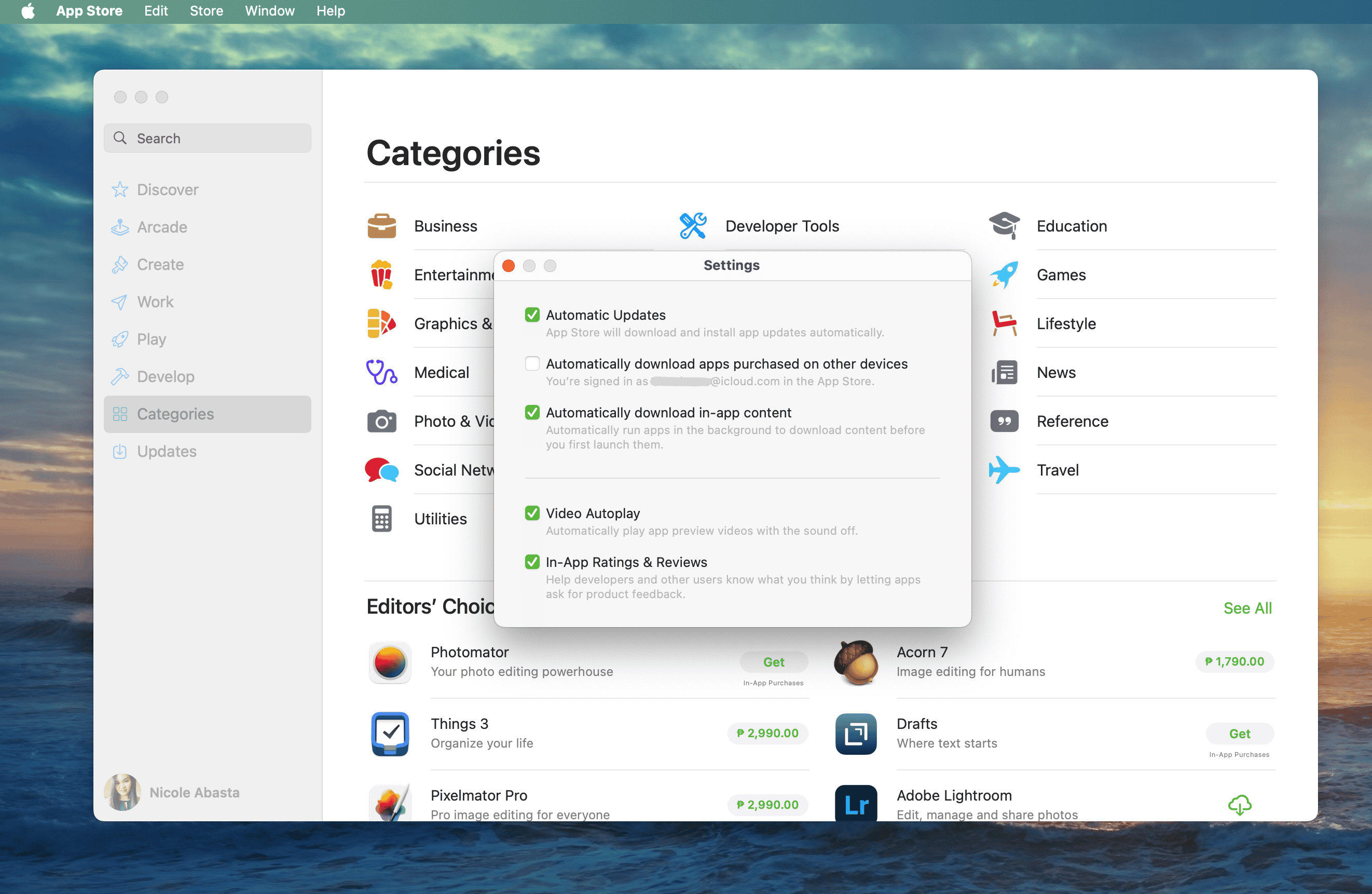
Here’s how to set auto-updates for apps on your Mac:
- Open the App Store.
- Go to App Store > Settings.
- Tick the check box for Automatic Updates.
5. Nail Down Your Privacy Settings
Check your Mac’s privacy settings, including the apps that you installed on your computer. You can control access to your data, such as which apps have access to your location or contacts.
Many apps request access to your data, but they might not need it to function. So, make sure that you only give permissions to apps that you trust and that need access to work properly. You should also limit ad tracking to reduce the amount of data advertisers can collect about you.
6. Use Spam And Web Filters
Most email services (e.g., Gmail, Outlook, and Yahoo) have built-in spam filters. They automatically detect suspicious messages and move them to the spam or junk folder. Make sure that the filters are activated in your accounts.
Safari and other browsers also have built-in filters and pop-up blockers, so make sure that you enable them to enhance your protection against phishing. You can typically find them in your browser’s privacy or security settings.
7. Use 2FA to Boost Mac Phishing Protection
You can add an extra layer of security against phishing by enabling two-factor authentication (2FA). This means that in addition to your password, you need to verify your login activity through a code sent to your phone. So, even if bad actors get your password, they won’t be able to access your accounts without the second factor.
What To Do If You Suspect A Phishing Attack?
If you recognize a phishing email or message on your Mac, immediately remove them without clicking any links or downloading any attachments. You can flag or report them as spam before deletion. Likewise, report the incident to your email provider or app developer, and reach out to the company impersonated.
If you’ve responded to phishing or accidentally clicked a suspicious link, change your passwords immediately. Check your accounts for activities you don’t recognize and report them to your service provider.
You can report phishing emails to [email protected], or file a complaint at reportfraud.ftc.gov. If you suspect identity theft as a result of phishing, you can also call 877-IDTHEFT (1-877-438-4338).
Remember to be vigilant and implement the best practices we discussed above to reduce the risk of falling victim to phishing attacks. When you take proactive steps toward Mac phishing protection, you can carry on with your online activities with confidence and peace of mind. As best practice, learn how to remove hackers from your iPhone as well.