AT&T Alien Labs discovered malware it dubs BotenaGo. It affects millions of routers and Internet of Things devices found with smart homes. The “devastating” part comes from the fact that it uses over 30 separate exploits due to insecure devices.
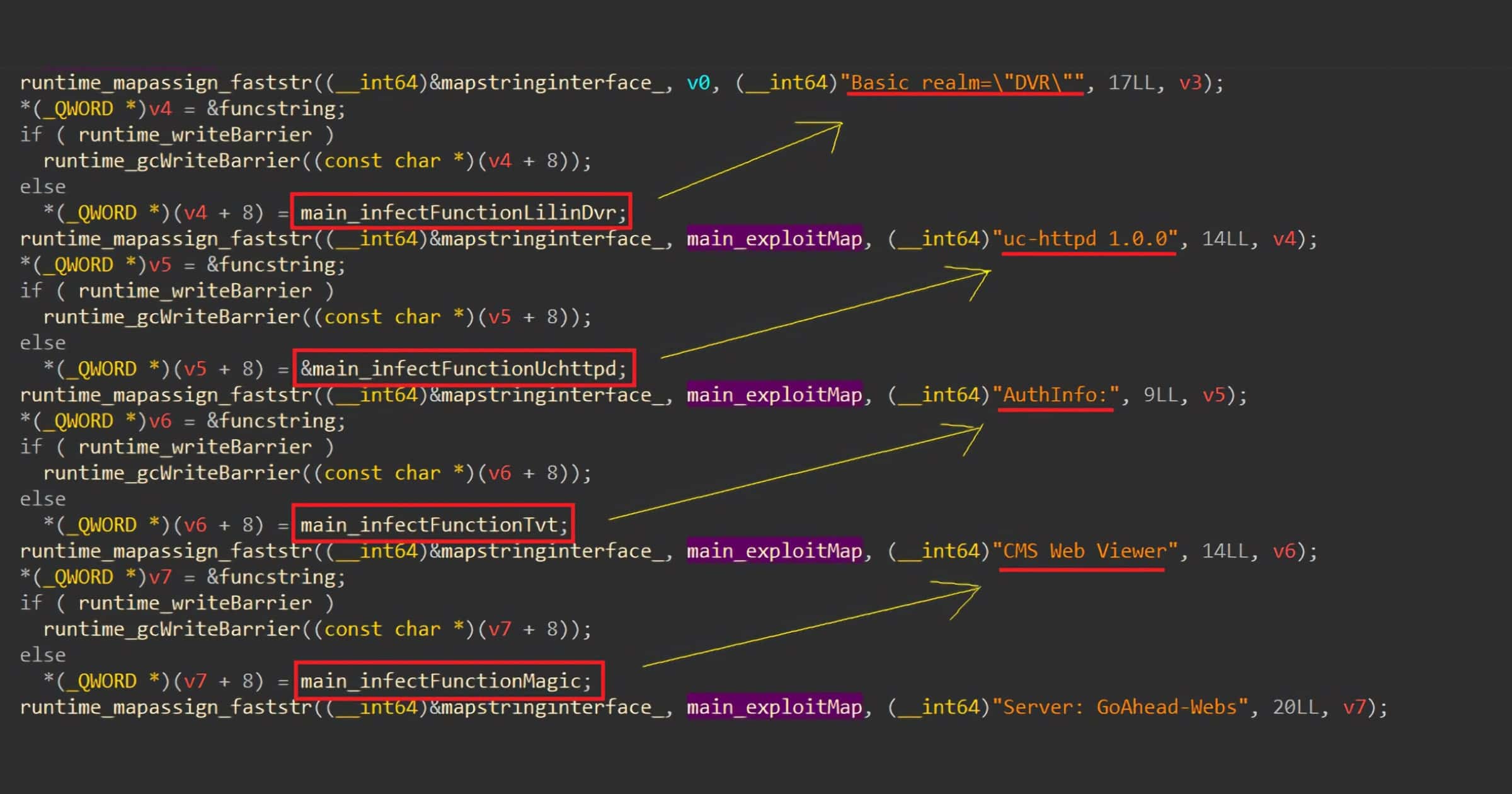
The BotenaGo malware starts by initializing global infection counters that will be printed to the screen, informing the hacker about total successful infections. It then looks for the ‘dlrs’ folder in which to load shell scripts files. A loaded script will be concatenated as ‘echo -ne %s >> ‘. If the ‘dlrs’ folder is missing, the malware will stop and exit at this point. For the last and most important preparation, the malware calls the function ‘scannerInitExploits’, which initiates the malware attack surface by mapping all offensive functions with its relevant string that represent the targeted system.
Check It Out: New ‘BotenaGo’ Targets Routers and Smart Home Devices in Devastating Attack
Andrew:
A sobering read. Many thanks for sharing.
This, in addition to other recent and continuing articles, is a principal reason why yours truly has not invested in IoT and other ‘smart’ devices. Without question, progress is being made in harmonising these, but far less is being published on how, and at what level, these are being hardened against ongoing attack.
As this article illustrates, this is an attack on both routers and the smart home devices. While I trust Apple to apply industry-leading security protocols to their equipment, neither my router nor my third-party appliances are made by Apple. And yes, having lived in more than one surveillance state, I’m well aware that there are other ways to be compromised; but why facilitate it?
Until more is done and published on that front, I will continue to use inert (stupid) devices, and keep non-essential smart-capable appliances offline, like an animal, and thereby limit my exposure and opportunity to have my convenience appliances repurposed to self-installed and optimally located surveillance equipment.
Thanks for reporting on this Andrew.