Apple has updated its privacy page with new information and product images. First launched in 2015, Apple shares how the company manages the privacy of its customers. Transparency reports like government requests for information are also shown. Along with recently publishing a Face ID white paper, the company is trying hard to reassure its customers that our data is safe.

Apple’s Privacy
The page starts off with strong language in an opening paragraph:
At Apple, we believe privacy is a fundamental human right. And so much of your personal information — information you have a right to keep private — lives on your Apple devices. Your heart rate after a run. Which news stories you read first. Where you bought your last coffee. What websites you visit. Who you call, email, or message. Every Apple product is designed from the ground up to protect that information. And to empower you to choose what you share and with whom. We’ve proved time and again that great experiences don’t have to come at the expense of your privacy and security. Instead, they can support them.
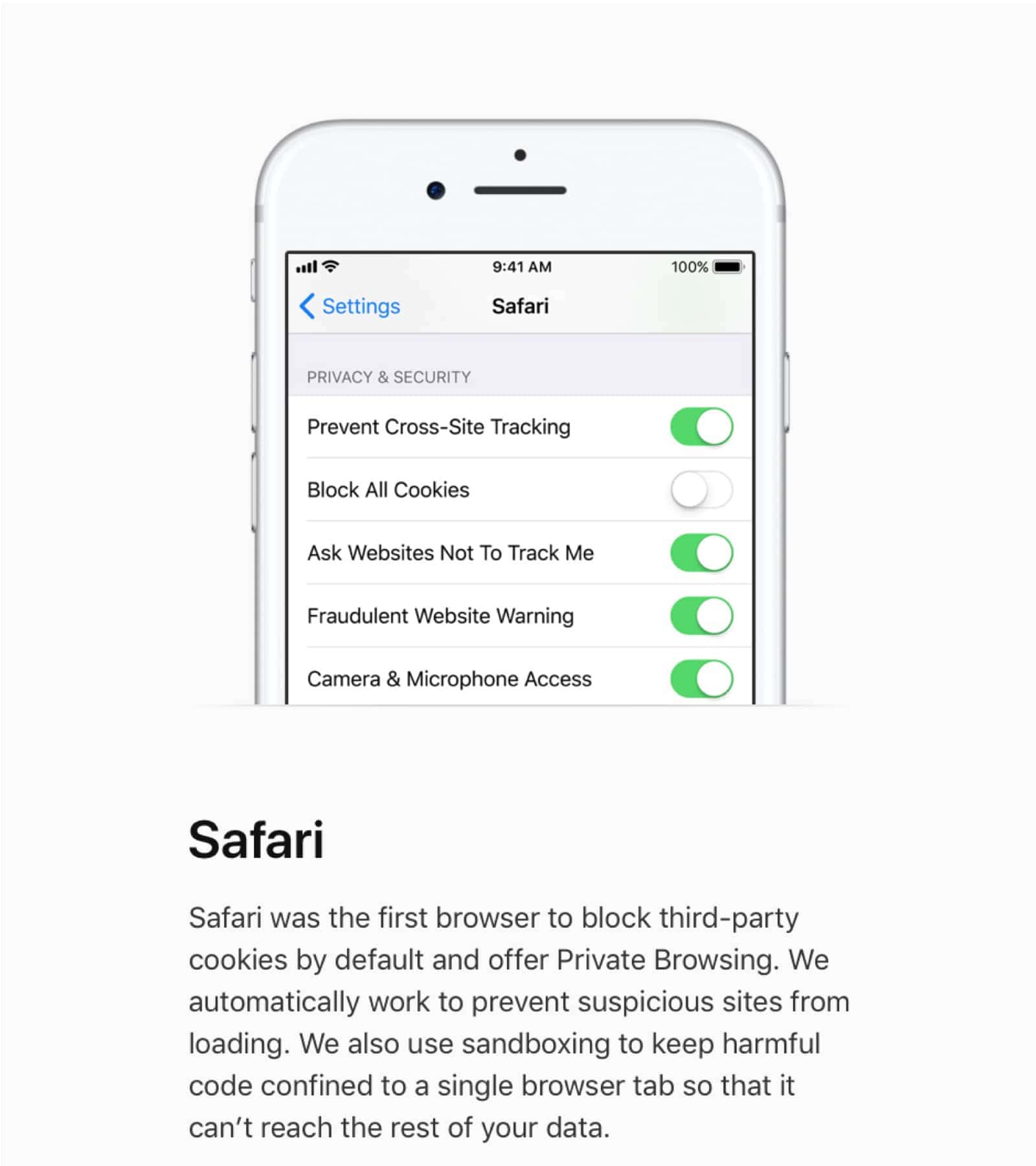
Next, the page discusses how your information is kept safe, whether it’s stored in the cloud or kept on your device. Encryption is used throughout the products and services. Apple encrypts data stored in iCloud too, with a minimum of 128-bit AES encryption for the majority of data:
- Photos
- Documents
- Calendars
- Contacts
- iCloud Keychain
- Backup
- Bookmarks
- Reminders
- Find My iPhone
- Find My Friends
- Mail (encrypted in transit)
- Notes
Transparency Reports
Like most American companies, Apple regularly gets government requests for customer data. The majority of these requests are for devices, financial identifiers, accounts, account restriction/deletion/preservation, U.S. National Security Orders, and emergency requests. Apple requires a search warrant for all content requests for the U.S. government.
For international governments, they have to comply with the U.S. Electronic Communications Privacy Act (ECPA). Legal process guidelines [PDF] are shared that detail exactly what happens when law enforcement requests customer information.
