The Vietnamese team is at it again with a new Face ID hack with a US$200 ‘Evil Twin’ mask. In the previous hack (which wasn’t really a hack), the researchers made a 3D scan of a person’s head, then created a mask using latex. But the team didn’t show the Face ID enrollment process, or how long it took to unlock the iPhone X with the mask. With this latest proof-of-concept, they’ve answered these questions. (via Forbes).
Face ID Hack Mask
In a video, the team shows version 2.0 of the hacking mask, which you can see below. The team named the mask the ‘artificial twin’ because it attempts to replicate what would happen if a person’s identical twin unlocked an iPhone X.
A spokesperson for the team said they chose not to tell Apple about their new techniques because the company didn’t respond to reports of the previous hack. Ngo Tuan Anh, Bkav’s vice president of cybersecurity. said:
About two weeks ago, we recommended that only very important people such as national leaders, large corporation leaders, billionaires, etc., should be cautious when using Face ID…However, with this research result, we have to raise the severity level to every casual users: Face ID is not secure enough to be used in business transactions.
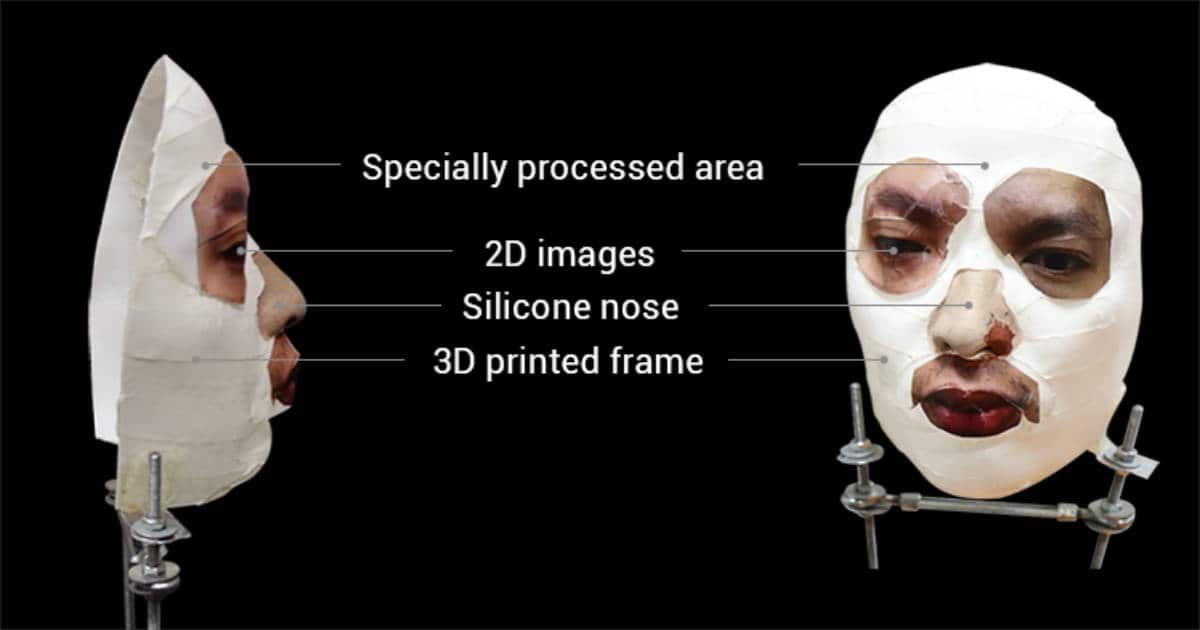
The team used a 3D scanning booth for the mask, taking photos of a person at different angles in two seconds, along with an infrared image of your face. Then, using a 3D printer with stone powder as material, they print the twin mask of your face. Using the infrared image, they cut the eyes from the image in a way that it tricks Face ID (in a manner not disclosed), then glued the eyes to the mask.
Just like the last test though, this isn’t something your average criminal isn’t likely to do. This requires specialized tools to target specific individuals. “…However, you can see from the way this experiment is done it is very tricky to position the device just so. That suggests that mask has to be used in very particular circumstances.”
Blofeld: Mr Bond, you leave me no choice. We will have to resort to extreme measures to access your iPhone, which contains your government’s top secrets, and even the Queen’s recipe for plumb pudding.
Bond: Oh, do tell. What have you in mind?
Blofeld: Do you see this device, Mr Bond? It’s a portable scanner. We’re going to tie you that chair. Then we’re going to scan your face, construct that into a 3D image of your face, using latex and other diabolical thingees which we won’t name, and let that set for a few hours. And then, do you know what we’re going to do, Mr Bond?
Bond: I’m all ears.
Blofeld: I…Oh, I see what you did there. Very clever. But it won’t save you. We’re going to use that face to open your iPhone, and there’s nothing you can do to stop us.
Bond: You don’t simply want to hold the phone up to my face? Just asking.
Blofeld: Insufficiently diabolical, Mr. Bond. Now, hold still for camera.
[Hours later]
Blofeld: Now, Mr Bond, let’s open your iPhone and steal all of your secrets! Bwahahahaha!
[Phone unlocks and…Says it’s ready to set up]
Blofeld: I don’t understand. What is this?
Bond: While you were making your mask, I used my Apple Watch to alert Q Branch that you had my iPhone and had them wipe it. Oh, and arranged for the SAS to help me blow up your headquarters, kill off your minions, deliver my Aston Martin and rescue the girl. If it’s any consolation, you can keep the bloody phone. I’m on a replacement plan.
No. IF IT ACTUALLY WORKS AT ALL, this is a finicky technique that requires the person trying to break in to have direct access to the person who owns the phone in order to get an image of their face and then do a 3D printed model of it. This is a parlour trick, not a real hancing technique.
There is also another aspect of this. A variation of NIMBY. If this were a real technique that actually worked as well as advertized, something that I would NOT put my faith in from the evidence so far, I suspect there would be people from MIT, from various BlackHat/WhiteHat groups, from Silicon Valley doing it. So far it’s only been this bunch of unknowns from VietNam. That reduces their credibility to zero in my book.
I call bogus on this whole thing.