Security researcher Jonathan Leitschuh recently published information of a Zoom zero day vulnerability. Here’s how to protect yourself.
Zoom Zero Day
Basically, the flaw lets any website force you to join a Zoom call and activating your Mac’s camera without your permission. It also lets websites to perform a denial of service (DoS) attack by repeatedly making you join an invalid call.
But it gets worse. When you install Zoom it installs a localhost web server on your Mac. This is what makes Zoom work, so you can join a video call just by clicking a link. But it also lets Zoom be reinstalled without your permission.
Zoom says they don’t have evidence that the zero day was ever used. If a user did click a malicious link, it’s obvious that a video call is starting. But the company will update the app later this month to give users more control over the app settings.
What You Can Do
Since Zoom leaves its web server behind even if you delete the app, we’ll have to use Terminal to manually delete it. But you can also open Zoom, go to Settings > Video, and uncheck the box that says Turn off my video when joining a meeting.
Method 1: Open Terminal and paste the command below:
defaults write ~/Library/Preferences/us.zoom.config.plist ZDisableVideo 1
This disables Zoom’s video capabilities for your user account only.
Method 2: To disable video access for all users, paste the command below:
sudo defaults write /Library/Preferences/us.zoom.config.plist ZDisableVideo 1
Method 3: To shut down the web server, run
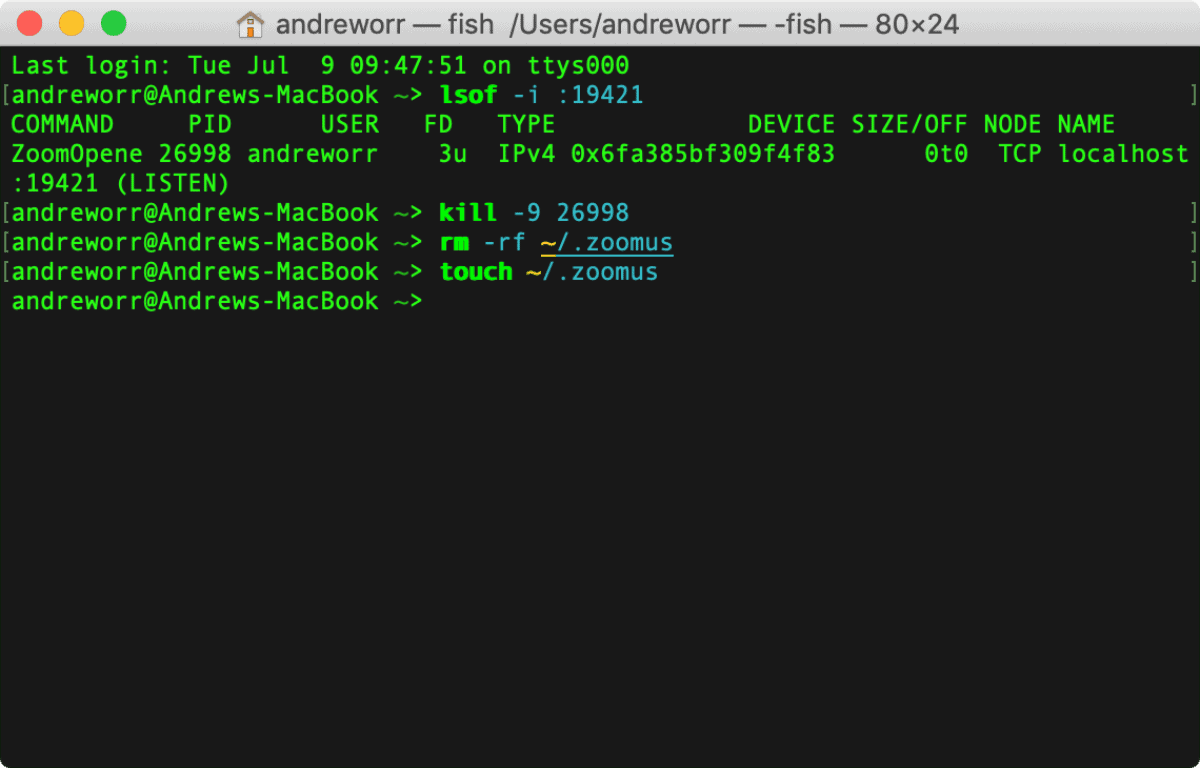
lsof -i :19421
to get the process identifier. You’ll have to do this while Zoom is running. Then enter
kill -9 <process ID>
You can then delete the ~/.zoomus directory to remove the web server application files. To find it, open Finder, click Go > Go to Folder in the menu bar, and type ~/.zoomus.
Finally, to stop the web server from being restored with new updates, paste the commands below:
rm -rf ~/.zoomus touch ~/.zoomus
Further Reading:
Move away from macOS. It’s wide-open to the simplest vulnerabilities. What other code can it run unchallenged ? Move now.
If one’s camera is activated without permission by this flaw, does the camera’s green light go on? If so, it would give the user visual evidence they’ve been affected.