An iOS exploit called Insomnia was used between January and March 2020 to spy on Uyghurs in China.
Key Takeaways
- Insomnia affects iOS 12.3, iOS 12.3.1, and iOS 12.3.2. Apple patched it in iOS 12.4.
- It was used by multiple Chinese entities, most notably the hacking entity known as ‘Evil Eye’.
Details
Using a chain of exploits, Evil Eye used an open source framework called IRONSQUIRREL to use a vulnerability in WebKit that was patched in 2019. If this initial attack is successful, the group then installs malware called Insomnia.
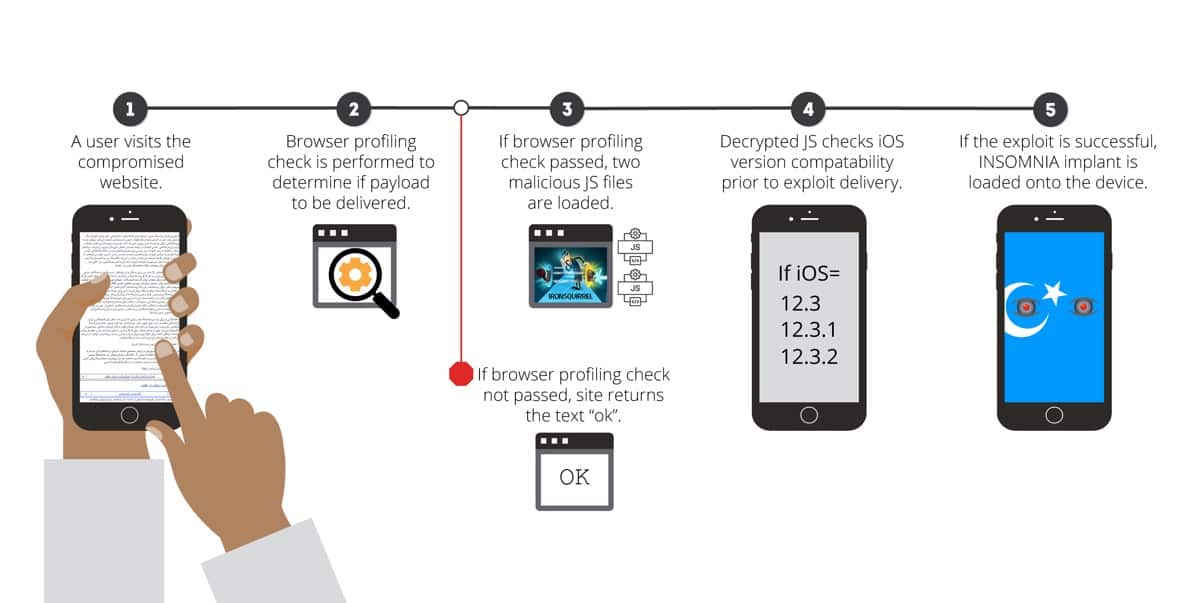
In the first round of attacks, it targeted visitors to the Uyghur Academy website. Another website was the Uyghur Times. Only certain user agents were targeted, meaning if a website visitor was detected as using an Apple device, like this:
Mozilla/5.0 (iPhone; CPU iPhone OS 12_3_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.1.1 EdgiOS/44.5.0.10 Mobile/15E148 Safari/604.1
Mozilla/5.0 (iPad; 12_3_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0 EdgiOS/44.5.2 Mobile/15E148 Safari/605.1.15CPU OS 1
Since all browsers on iOS are required to use Apple’s WebKit engine, it wasn’t specific to Safari users. Safari, Google Chrome, and Microsoft Edge were all successful recipients of the exploit.
The malware had a list of apps that it would steal data from if they were found to be installed on victims’ devices. Two recent additions to the list are Signal, a private messaging app, and ProtonMail, a private email service. Both use end-to-end encryption, and it’s likely China targeted Uyghurs using these apps to hide their communications.
Further details can be found in Volexity’s report.
Further Reading
[iPhone Zero Day Found, Will Be Patched in iOS 13]
[‘Cosmic Frontier: Override’ is a Remake of 1998 Game ‘Escape Velocity’]
