The Russian government has compelled Apple and Google to remove an app associated with jailed Kremlin critic Alexei Navalny.
Articles by Andrew Orr
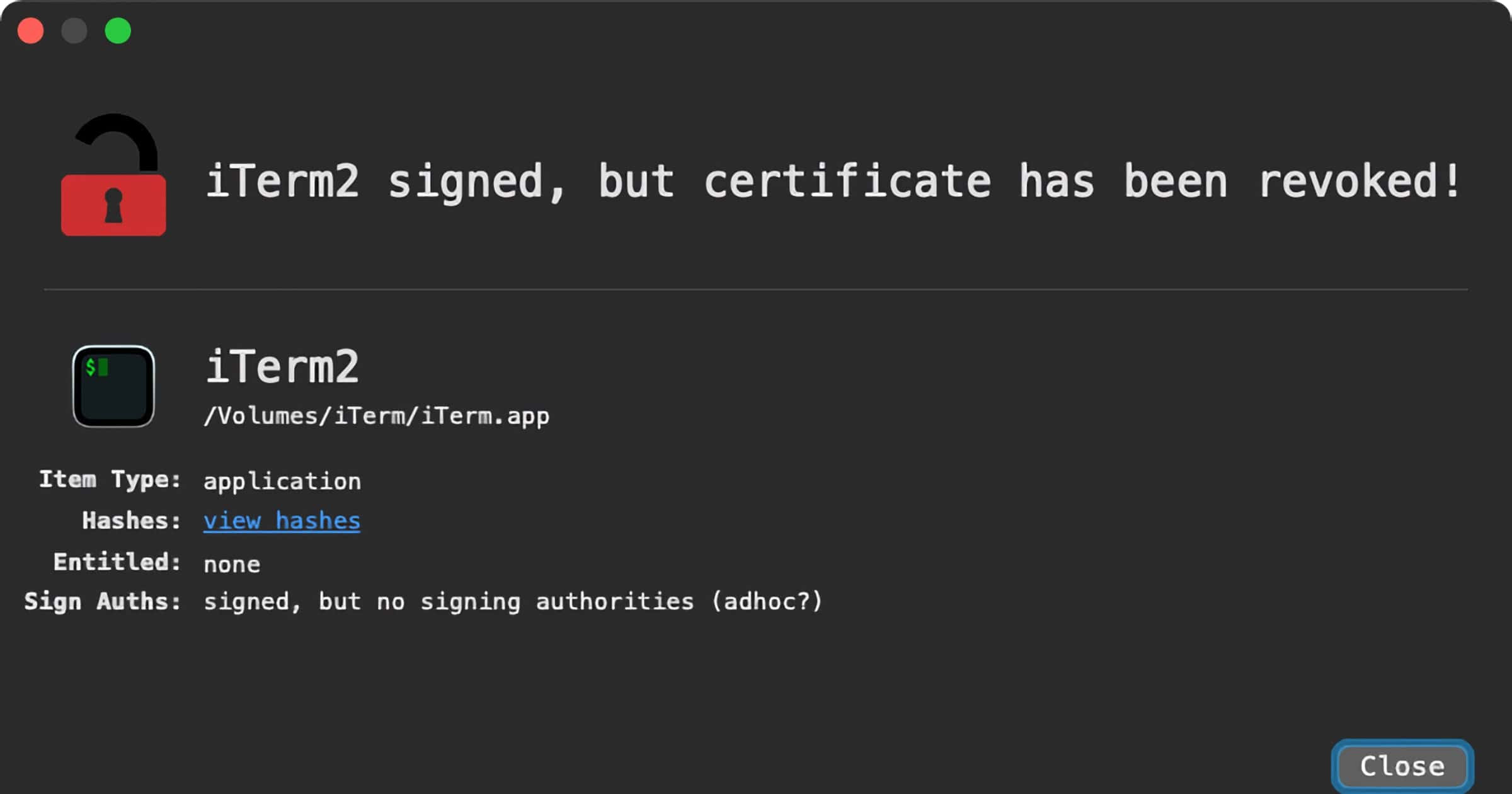
'OSX.ZuRu' Malware Spreads From Trojanized Apps via Sponsored Search Results
The latest Mac malware to be discovered is called OSX.ZuRu. It spreads via infected apps from sponsored search results.
The legitimate and the malicious iTerm2 application bundles contain a massive number of files, including several Mach-O binaries. Moreover, the malicious version appears largely benign (as is the case with most applications that have been surreptitiously trojanized). As such, it takes us a minute to uncover the malicious component.
5 Brands to Consider for iPhone 13 Accessories
Yesterday we published a list of 13 brands to consider when you’re buying iPhone 13 cases. Today we have five brands to list for your iPhone 13 accessories.
Health Apps Must Warn Users of Data Breaches, Says FTC
The Federal Trade Commission issued a policy statement on Thursday. It says that health apps and wearable companies must warn their users of data breaches or face fines.
In a policy statement adopted during an open meeting, the Commission noted that health apps, which can track everything from glucose levels for those with diabetes to heart health to fertility to sleep, increasingly collect sensitive and personal data from consumers These apps have a responsibility to ensure they secure the data they collect, which includes preventing unauthorized access to such information.
Excellent news. Now they should make sure the fines are high enough to deter repeat offenders (cough T-Mobile).
Reminder: Set Up a Shortcut to Preorder Your iPhone 13
Friday, September 17 at 5AM PT/8AM ET is the day that people can officially preorder their iPhone 13. Set up a shortcut to speed up the process.
PrivacyTools Website Rebrands as Privacy Guides (Update)
PrivacyTools.io is a website I’ve long used to learn about different types of private software. The team announced that it will rebrand as Privacy Guides.
Our work maintaining PrivacyTools has been extremely difficult of late without access to key assets such as the domain and without the participation of its founder.
This name change is the first step in this process of regaining our independence as a community. Eventually, we plan on creating a new legal organization designed around the community to ensure our long-term sustainability. This will take some careful planning and time to get right, but we’re confident we can prevent this from ever happening again, and keep us independent of any one team member.
Update: It appears there is some contention or intra-politics. The official PrivacyTools Twitter account said it is a project split, not a rebrand.
GoPro Releases New HERO10 Black Camera With 5.3K Video
GoPro has announced its newest camera, the HERO10 Black that delivers better image quality and twice the speed as previous models.
Cloudflare Supports 'Early Hints' to Speed up Web Browsing
Cloudflare announced it is the first company to add server support for Early Hints. This aims to help speed up websites by as much as 30%.
New Products at Mimeo Photos Include Mounted Prints
Mimeo Photos has recently launched mounted photos and expanded its size options for wall decor and photo prints.
Mimeo Photos users can now transform their favorite photos, designs or artwork into a customized mounted wall print to adorn the walls of their home, office or studio. Mimeo Photos also expanded its wall decor category to include eighteen new sizes and added two new sizes to its photo prints offering. As the No. 1 photo product extension in the Mac App store, Mimeo Photos continues to innovate and expand its product offering, while also being available everywhere its customers’ photos are taken and stored.
Inside Project Raven, a Team of Former NSA Analysts Who Worked for the UAE Government
Project Raven was a team that included more than a dozen former U.S. intelligence operatives recruited to help the United Arab Emirates engage in surveillance of other governments, militants and human rights activists critical of the monarchy. Reuters tells the story.
The operatives utilized an arsenal of cyber tools, including a cutting-edge espionage platform known as Karma, in which Raven operatives say they hacked into the iPhones of hundreds of activists, political leaders and suspected terrorists. Details of the Karma hack were described in a separate Reuters article today.
An interesting story. We know that iOS 14.8 patched a vulnerability used by the Pegasus spyware, but I haven’t heard much about Karma.
Horizen (ZEN) and Braintrust (BTRST) Now Available on Coinbase Pro
Coinbase announced on Wednesday support for Horizen (ZEN) and Braintrust (BTRST). These can be traded on Coinbase Pro.
The iPhone 13 has Five Different 5G and LTE Configurations
The iPhone 13 lineup has five different configuration setups for 5G and LTE. This is the widest array of frequencies of any iPhone thus far.
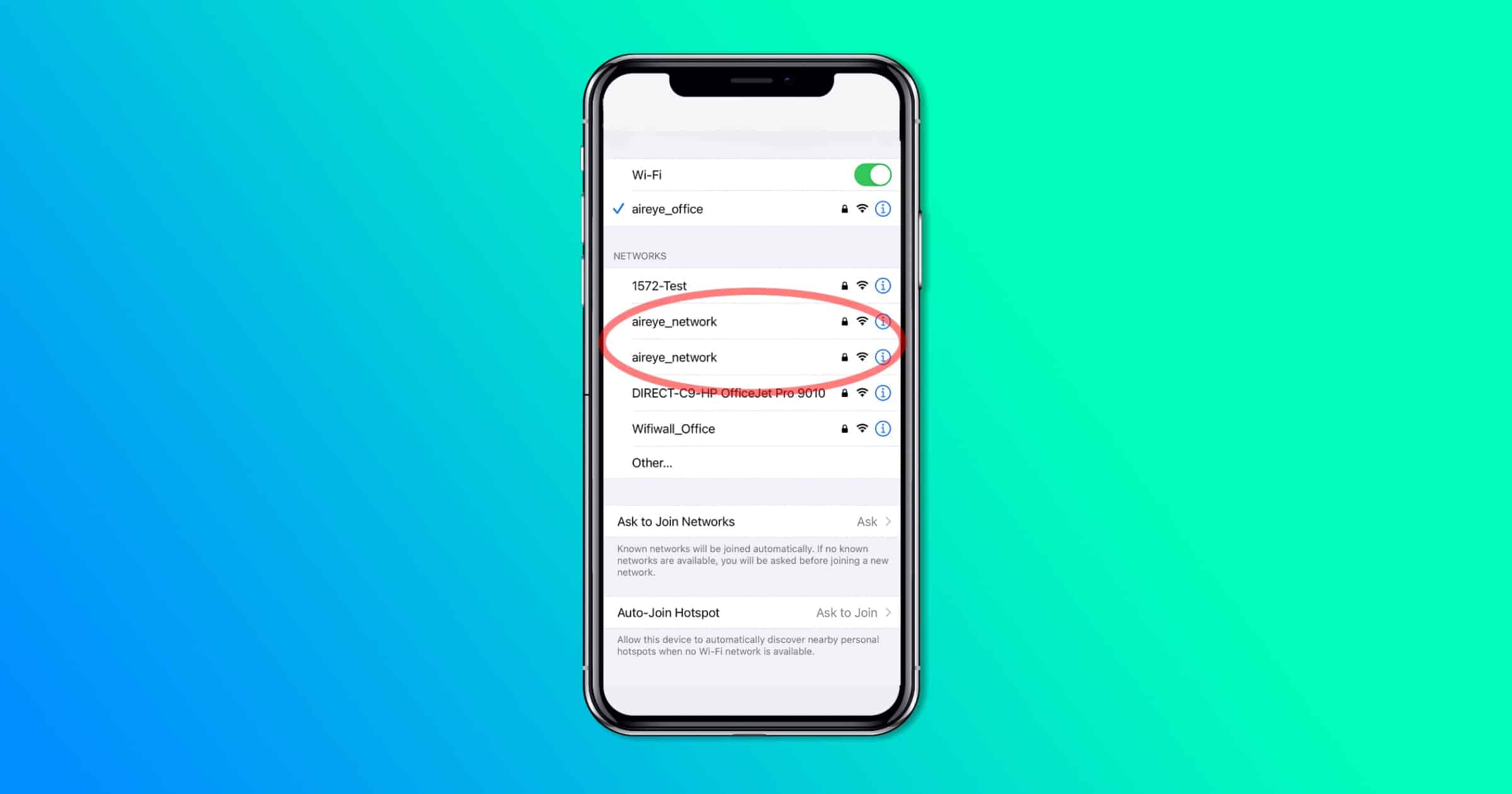
'SSID Stripping' Can Trick You Into Joining a Malicious Wi-Fi Network
Researchers have discovered a new type of network vulnerability dubbed SSID Stripping. It causes a network name to appear differently in a device’s list of networks, thus tricking people into joining a malicious network.
The SSID Stripping vulnerability affects all major software platforms – Microsoft Windows, Apple iOS and macOS, Android and Ubuntu. With SSID Stripping, it is possible to create a network name in a way that its display only shows a prefix that is similar to a legitimate network name (e.g. the corporate network name) while the actual network name includes the additional specially crafted information.
Phone Carrier 'Visible' Will Sell Apple Watch Series 7 for First Time
Visible, a prepaid carrier that operates on Verizon’s network, will sell the iPhone 13 models and the Apple Watch Series 7 on its website.
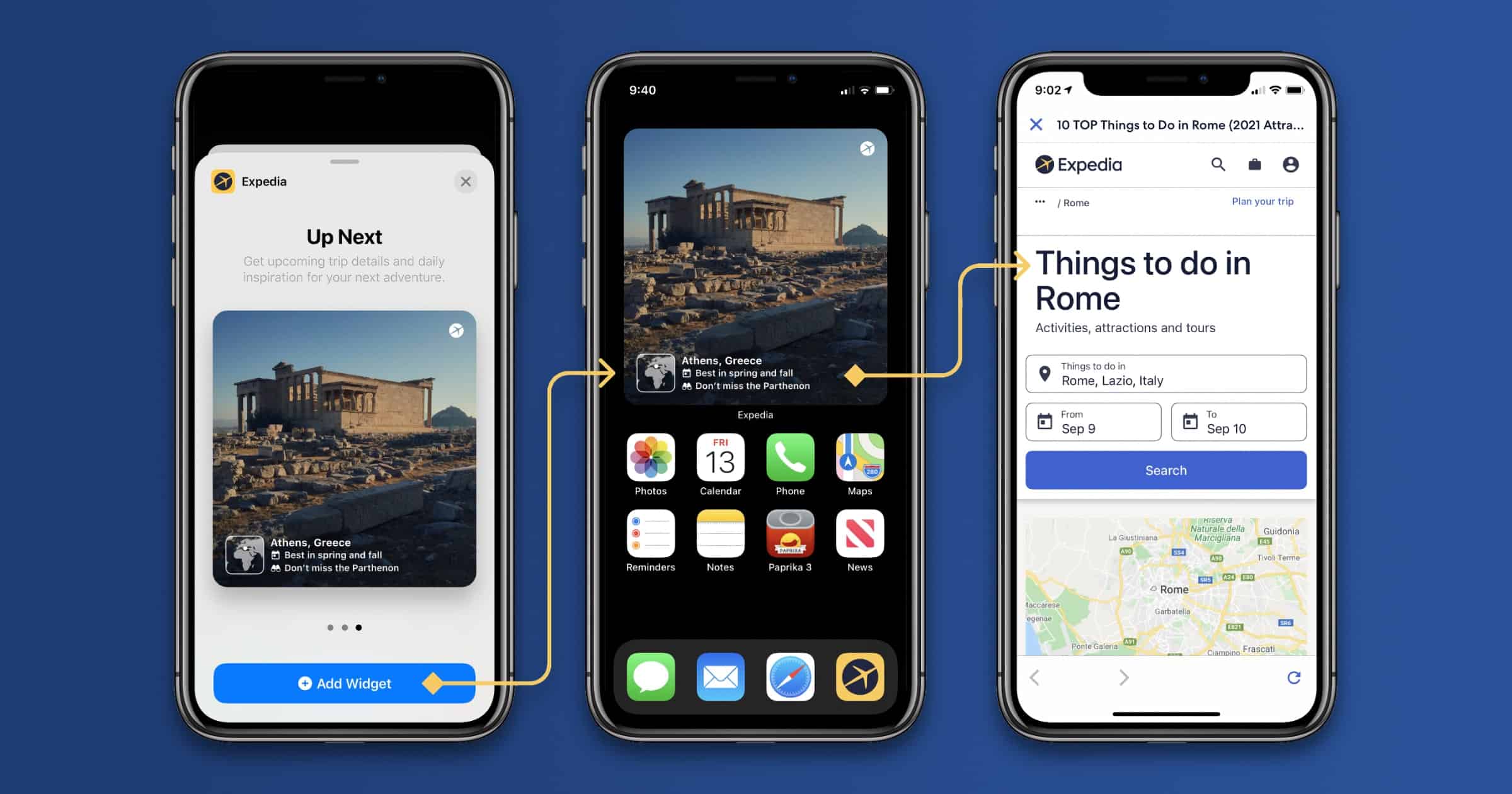
Expedia Group Announces iOS 15 Widgets and Quick Note Integration
On Tuesday Expedia Group announced some new features for its apps: New widgets designed for iOS 15 and an update that takes advantage of iOS 15 Quick Notes.
Developer of 'FlickType' Sues Apple Over Apple Watch Keyboards
Kosta Eleftheriou, developer of the FlickType keyboard for Apple Watch, has filed a lawsuit against Apple for fraud.
iPhone 13 Pro Camera Features Include All-New Macro Photography
Apple announced its powerful iPhone 13 Pro lineup on Tuesday and here are the camera features that users will get.
Apple Announces Apple Watch Series 7 With Exciting New Features
The Apple Watch Series 7 didn’t get the flat design that rumors claimed, but it’s still a notable update with a big screen.
How to Use Regular Expressions, or Regex, in Shortcuts
Regular expressions, or regex for short, are certain characters used as search functions. They are powerful, confusing tools. Justin Meredith wrote a guide on how to get started.
In case you don’t know, a piece of text within another piece of text is called a “string” in programming. For instance, the word ‘green’ is a string of characters from the text “I wore green pants today.”
So put another way, regex is a way to locate a string of text in a larger body of text. And because regex is written in code, you can use it to perform some pretty complex operations.
Researchers Uncover a Phishing Kit Used by Two Criminal Gangs
Led by Noam Rotem, vpnMentor’s research team has discovered two separate criminal gangs using slightly altered versions of the same phishing kit to scam people across the globe.
It appears the phishing kit was being used to target people mostly living in Israel and France by two separate criminal gangs. However, we believe these two groups operate phishing websites and SMS operations based on the same phishing kit, possibly obtained from the same source. In addition, at least one of them is potentially affiliated with the OpIsrael political hacking group.
Keep Your iPhone 13 Secure With This Stylish Leather Holster
WaterField Designs is out today with a Latigo iPhone Holster for the new iPhone13, iPhone 13 Pro, iPhone 13 Pro Max, and iPhone 13 mini.
Revenue From Streaming Music Totaled $4.6 Billion in First Half of 2021
A mid-year report from the RIAA showed streaming music services have bounced back in 2021.
Within the overall streaming landscape, paid streaming subscription revenue totaled $4.6 billion — growing at the same 26% clip — and accounted for 78% of overall revenues in the first half of the year. Limited tier subscription revenue jumped to $452 million, accounting for 10% of streaming dollars, while ad-supported revenues — which took a large pandemic-related hit last year — grew 54% to $741 million. Digital and customized radio, including SoundExchange distributions, increased 3% to $585 million.
Security Researcher Finds CloudKit Bug That Broke Apple Shortcuts
Security researcher Frans Rosén wrote about a CloudKit bug he accidentally found that affected Apple News, Shortcuts, and iCrowd+.
On the third day, I started to connect the dots, realized how certain assets connected to other assets, and started to understand more how things worked. This is when some of the first bugs popped up, finally restoring my self-esteem a bit, making me more relaxed and focused going forward.
I dug up an old jailbroken iPad I had, which allowed me to proxy all content through my laptop. I downloaded all Apple owned apps and started looking at the traffic.