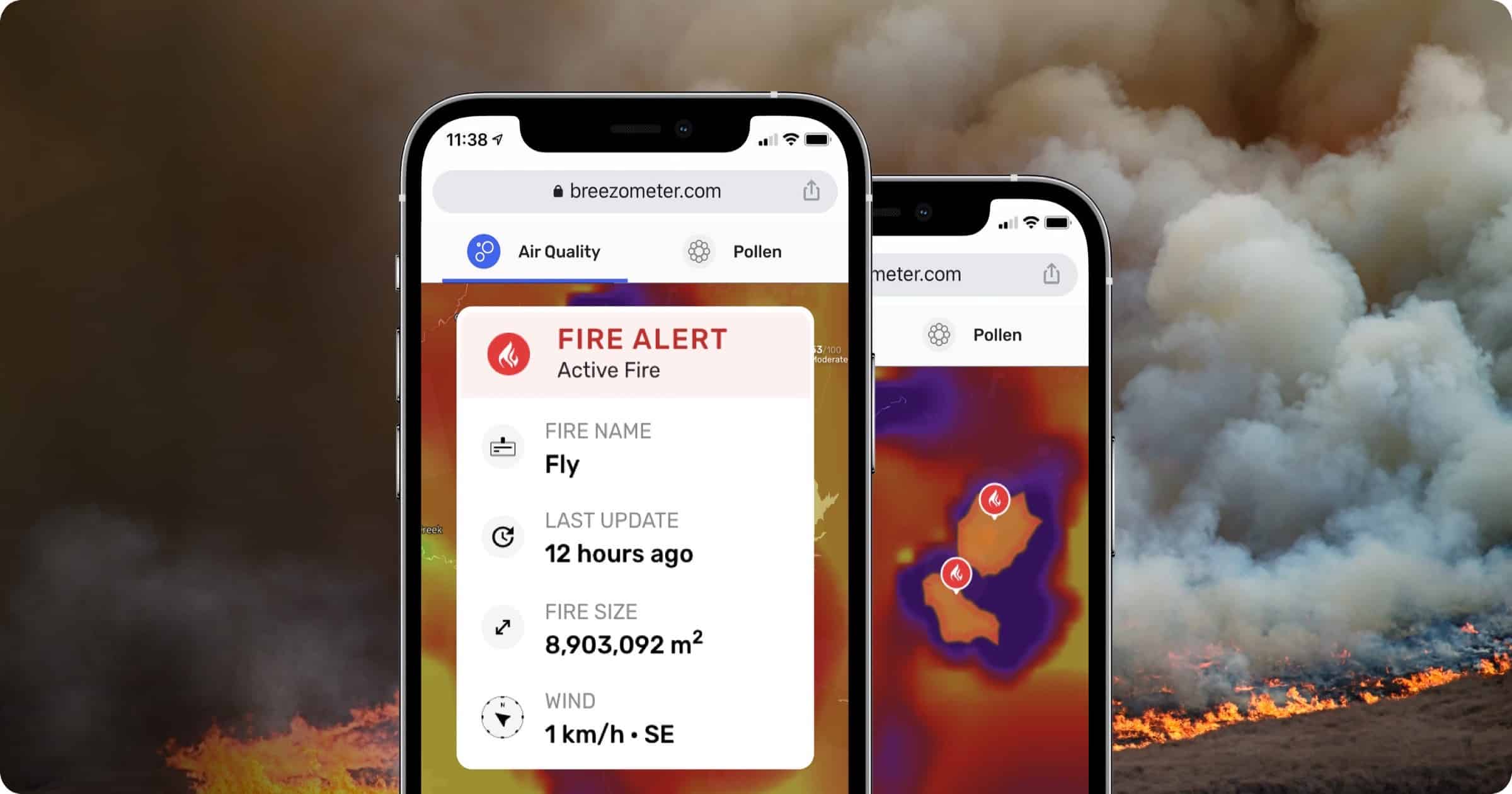
BreezoMeter has launched a Wildfire Tracker that provides real-time detection of wildfire perimeters.
Articles by Andrew Orr
It’s Easy for Minors to Bypass App Store Age Restrictions
On Wednesday, the Campaign for Accountability published a report that shows how easy it is for minors to bypass App Store age restrictions.
Using an Apple ID for a simulated 14-year-old, TTP examined nearly 80 age-restricted apps on the App Store and discovered that the underage user could easily evade the apps’ age restrictions in the vast majority of cases, often with minimal effort.
Your Internet Activity May be Traceable Even Through a VPN
Netflow data refers to IP network traffic that can be collected as it enters or exits an interface. Using this aggregate data, it’s possible to trace network traffic even if a person uses a VPN. Internet service providers sell this information to third parties.
At a high level, netflow data creates a picture of traffic flow and volume across a network. It can show which server communicated with another, information that may ordinarily only be available to the server owner or the ISP carrying the traffic. Crucially, this data can be used for, among other things, tracking traffic through virtual private networks, which are used to mask where someone is connecting to a server from, and by extension, their approximate physical location.
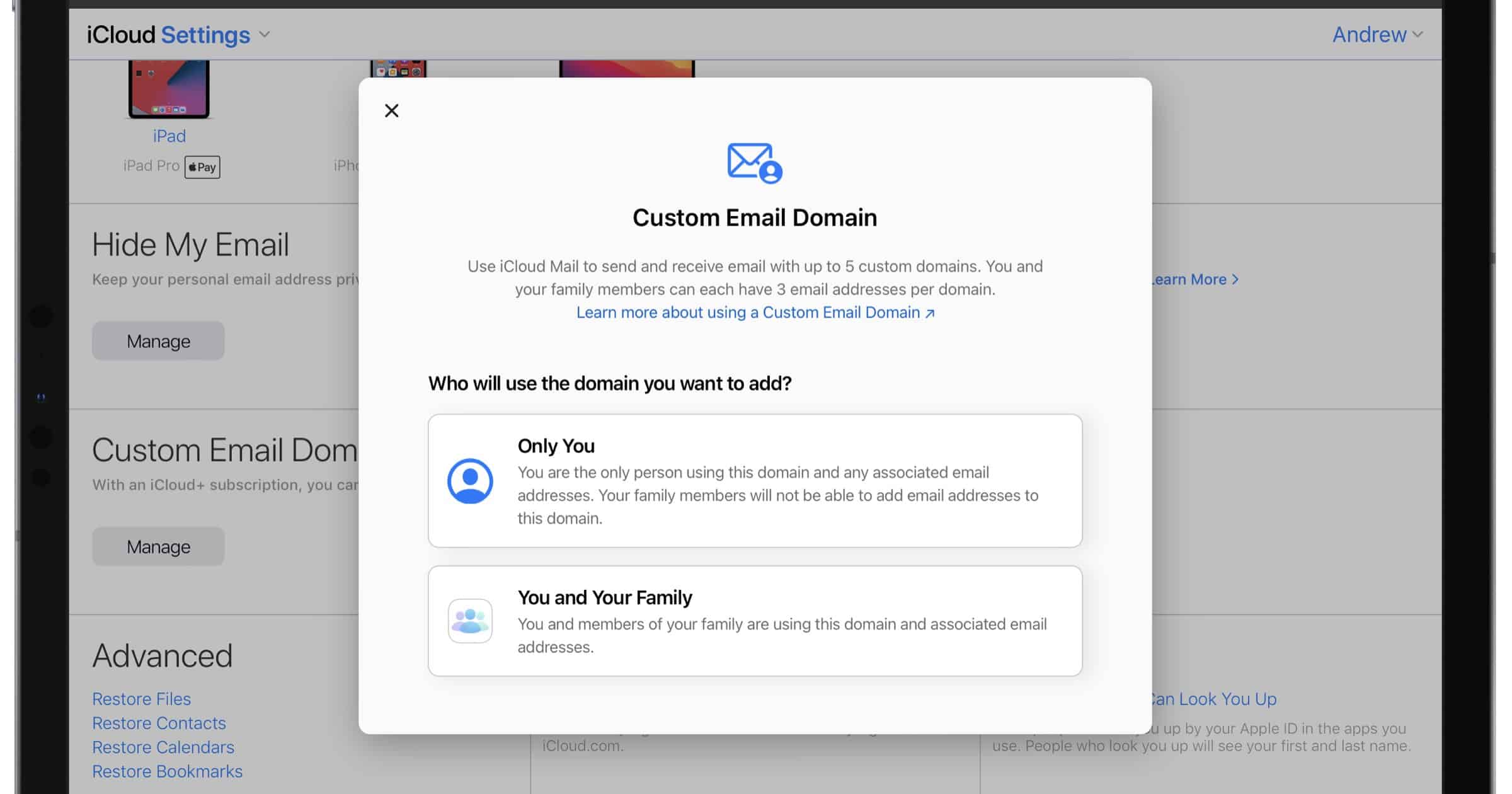
How to Start Using Custom iCloud Domains for Email
Custom iCloud domains have recently become available for subscribers as part of iCloud+. Here’s where to find the setting.
Social Engineering Majority of Business Attacks in 2020
Speaking of social engineering, new data from Atlas VPN shows this kind of attack was responsible for the majority of business breaches in 2020.
According to the data presented by the Atlas VPN team, social engineering cyberattacks were the primary cause of company breaches in 2020 at 14%, followed by advanced persistent threats, unpatched systems and ransomware. As a result, learning to prevent social engineering attacks needs to be a top priority for businesses.
Scammer Stole Over 620,000 iCloud Photos Looking for Nudes
Hao Kuo Chi, 40, of La Puente, has agreed to plead guilty to four felonies, including conspiracy to gain unauthorized access to a computer.
OnlyFans Has ‘Secured Assurances’ and Suspends Porn Ban
Days after it announced that it will ban sexually explicit content on its platform, OnlyFans has reversed its decision. The pressure for this ban came from “banking partners and payout providers.” But as TechCrunch notes, the decision has been “suspended” which could mean the ban may not fully be canceled.
In response to the planned policy change, some creators had already deleted their OnlyFans accounts and moved to alternate services. With this recent reversal, creators will have to decide between returning to the platform or leaving it altogether for a rival service.
Also, not to be that guy but banks exerting financial pressure in cases like this is exactly what cryptocurrency can help with.
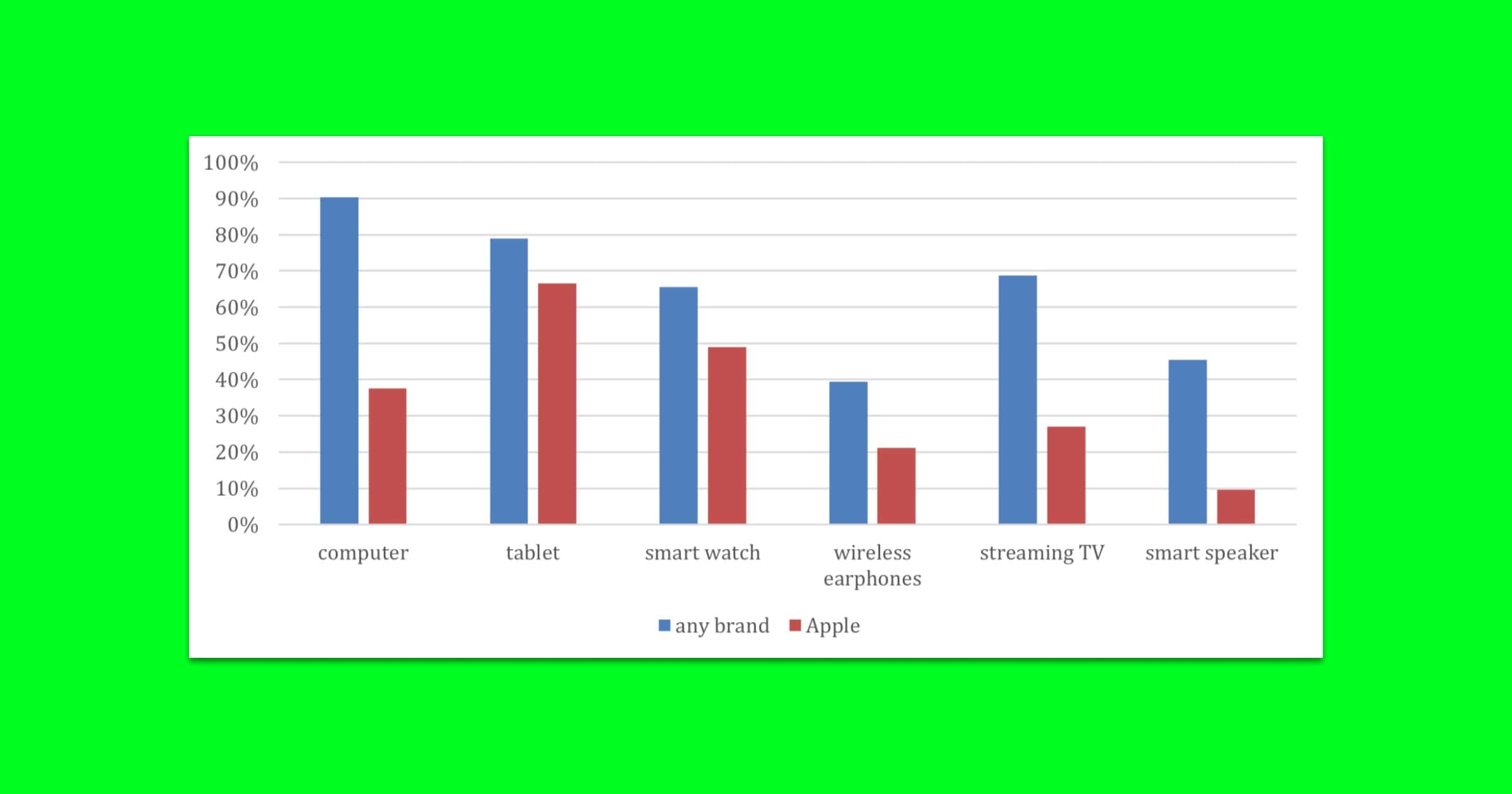
What Other Products do iPhone Owners Have?
The latest analysis from Consumer Intelligence Research Partners examined some of the common products that iPhone owners own.
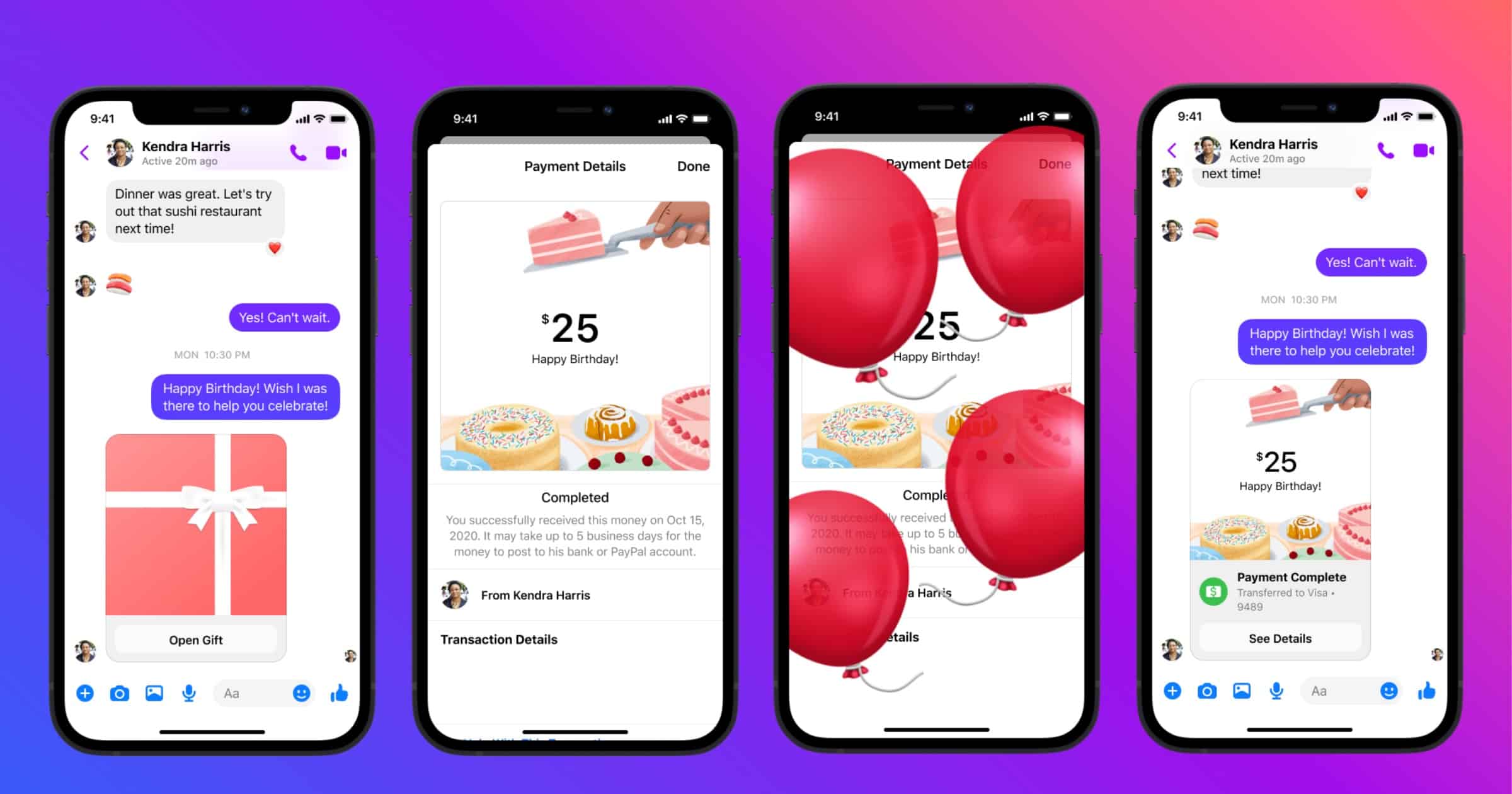
Facebook Messenger Celebrates 10th Birthday With New Features
Facebook’s Messenger app is celebrating its 10th anniversary in August, and it will release a bundle of 10 product features.
What Does Apple’s M1 Chip do Differently Than Other Chips?
In his latest blog post, Howard Oakley has examined the M1 chip to find out what features set it apart from other chips.
The M1 doesn’t integrate main memory, though, which is contained within the package. It’s also unusual in incorporating many coprocessors in addition to the GPU, which provide state-of-the-art facilities for features such as deep learning using neural networks.
Incase Launches ‘Reform’ Hardshell MacBook Pro Case
Incase has launched a hardshell case for the 13-inch MacBook Pro. It gives customers up to four feet up drop protection.
IBM’s AI-Powered Chip Can Help Detect Fraud
IBM revealed its new Telum processor at the Hot Chips semiconductor conference. It claims it can detect fraud in real time.
IBM says this could lead to “a potentially new era of prevention of fraud at scale.” Although credit card fraud is the most direct application, Telum’s onboard A.I. accelerator can handle other workloads as well. Using machine learning, it can conduct risk analysis, detect money laundering, and handle loan processing, among other things.
Tim Cook, Satya Nadella, Andy Jassy to Visit White House for Cybersecurity
The CEOs of Apple, Microsoft, and Amazon will attend a meeting at the White House to discuss cybersecurity.
Speed Tests Reveal the Fastest Mobile Network in the United States
In its twelfth annual network test, PCMag traveled over 10,000 miles across the U.S. to test the speeds of mobile networks AT&T, T-Mobile, and Verizon.
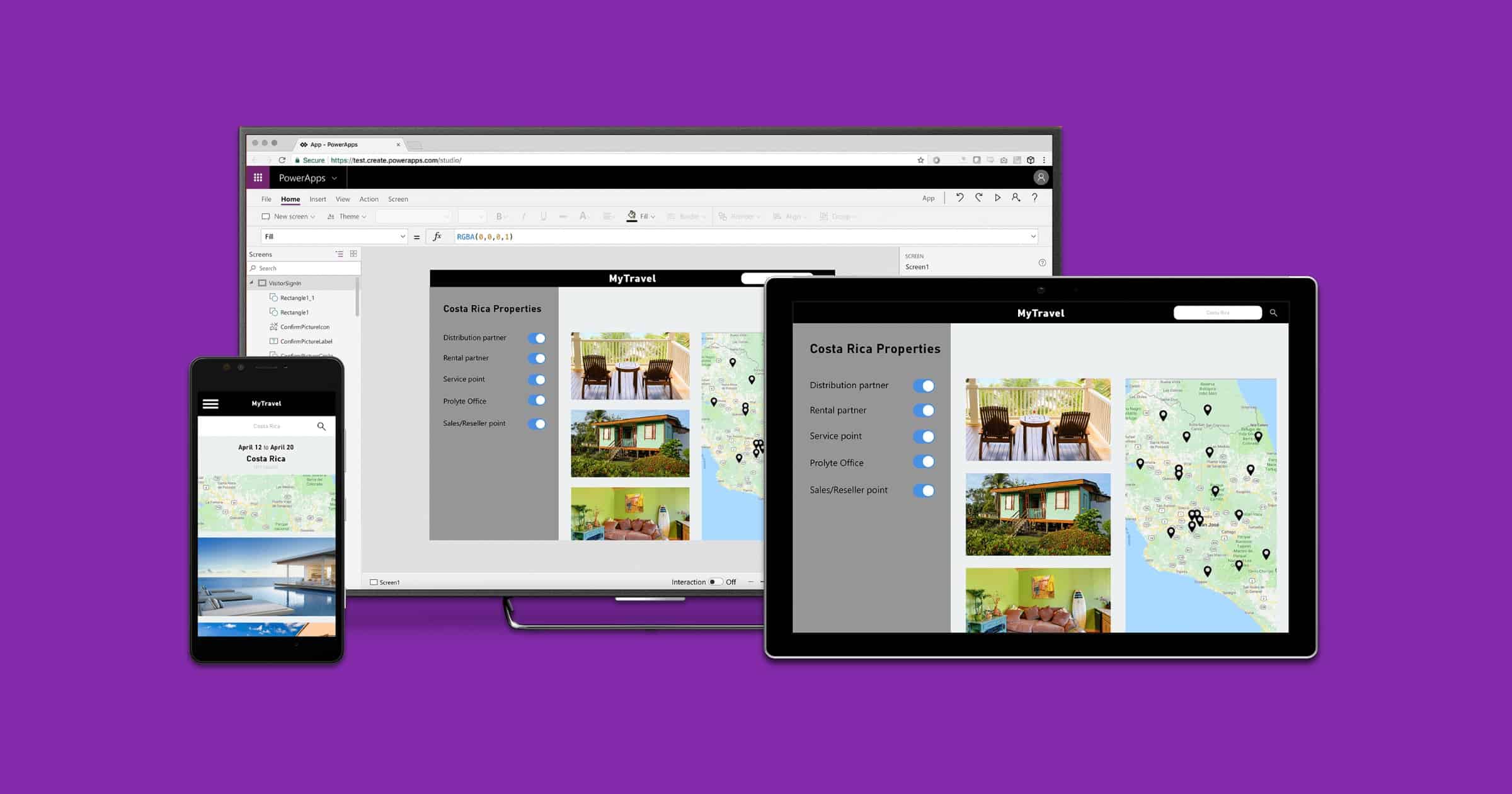
Misconfigured Microsoft Power Apps Leaked 38 Million Database Records
Over a thousand web apps from Microsoft’s Power Apps platform have leaked 38 million records. This data includes COVID-19 contact tracing.
The data included a range of sensitive information, from people’s phone numbers and home addresses to social security numbers and COVID-19 vaccination status.
The incident affected major companies and organizations, including American Airlines, Ford, the transportation and logistics company J.B. Hunt, the Maryland Department of Health, the New York City Municipal Transportation Authority, and New York City public schools.
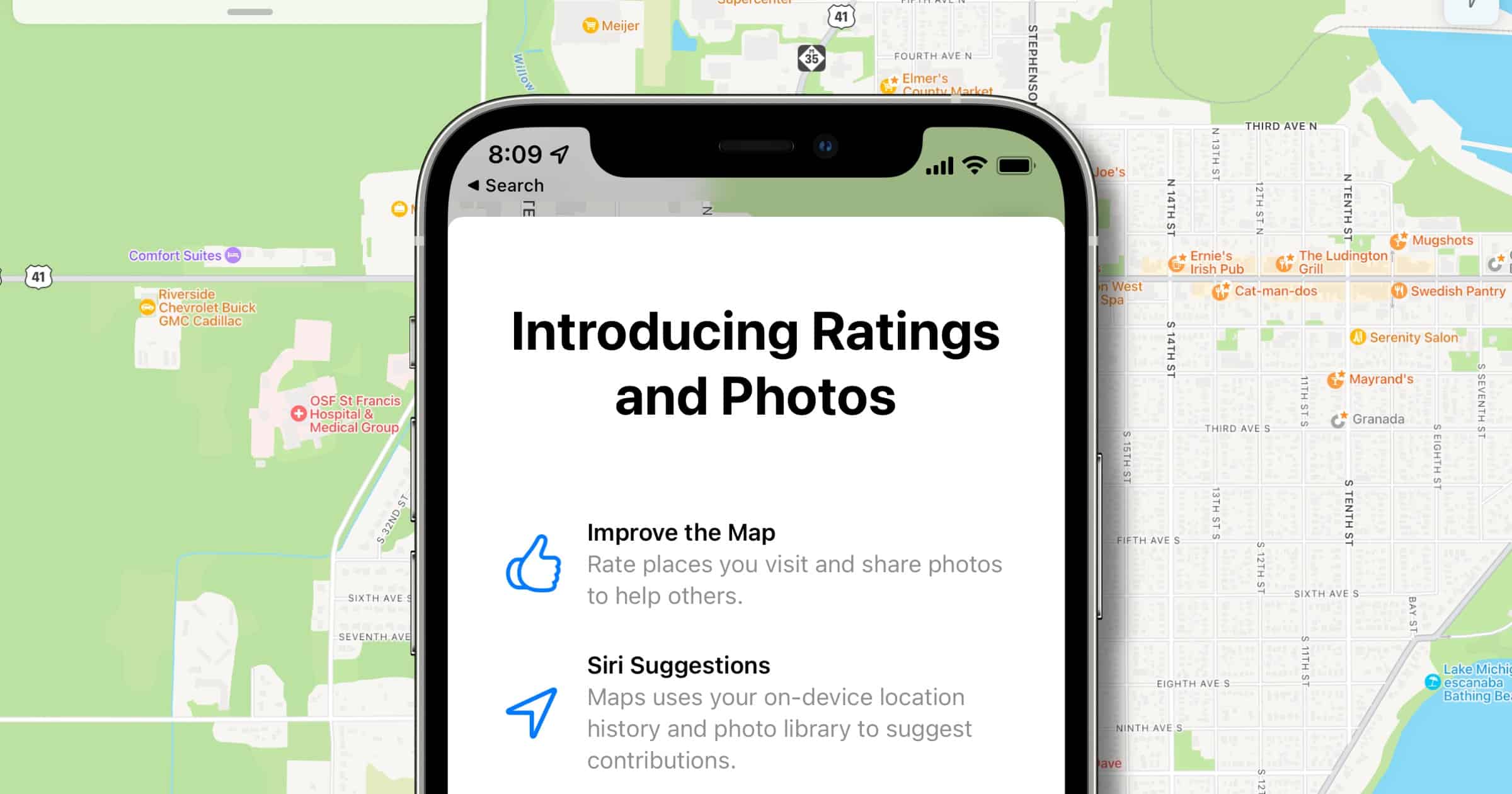
Apple Moves to Replace Yelp With its Now-Available Rating System in Maps
The rating system in Apple Maps is now available for people to rate their local businesses. You can give a thumbs up or a thumbs down.
USD Coin Will Be Backed By Pure Cash and US Treasury Bonds
As a stablecoin, USD Coin (USDC) is pegged to the value of the U.S. dollar. The reserves of currency upholding this value will only be cash and bonds going forward.
Circle reserves expanded beyond cash and cash equivalents in May, 2021, and the company provided a more detailed breakdown of reserve composition in July, adding clarity and insight into the funds backing USDC. Mindful of community sentiment, our commitment to trust and transparency, and an evolving regulatory landscape, Circle, with the support of Centre and Coinbase, has announced that it will now hold the USDC reserve entirely in cash and short duration US Treasuries.
Indie Publishing Platform ‘Substack’ to Accept Bitcoin Payments
Bitcoin payment processor OpenNode announced on Monday its integration with Substack, an online publishing platform. OpenNode will power both on-chain and Lightning Network Bitcoin payments.
Working together, OpenNode and Substack are starting by making instant, low cost payments available to a select group of crypto-focused publications. Readers will be able to use Bitcoin to pay for subscriptions to these select publications, and the publications will retain earnings in Bitcoin.
‘The Morning Show’ Season 2 Trailer Shows a Heartwarming Comeback
On Monday Apple uploaded the trailer for season two of The Morning Show and it reveals some aspects of the show that fans have been waiting for.
T-Mobile Offers 12 Months Free Apple TV+ After Serious Data Breach
T-Mobile has an offer for Magenta and Magenta Max subscribers. They can get a free year of Apple TV+ just days after the carrier revealed its latest data breach.
Here’s a List of Open Source Alternative Front-Ends to YouTube, Twitter, and Others
Someone on GitHub posted a project of a list that shares alternative, open source front-ends to proprietary services.
This AI Text Generator Shortcut Will Replace Our Blogger Jobs
Over the weekend, u/ryandeanrocks shared an AI text generator via the r/Shortcuts subreddit. It’s an open source version of GPT-3. Of course, how good the output it produces depends upon the input, but I’ve seen it spit out some decent things. Here’s an example; I pasted the first sentence of this piece, and here is part of the output: “You’ll notice that if you type something and then choose to send it to someone, that the chat box in the corner will turn green. In theory, that’s the easiest way to see if someone is typing something out and waiting to send it, but it can take awhile to see the difference. With real-time chatting, it’s almost instantaneous.“
How Google Search Works: An Insider Reveals All
Google has launched a web page that aims to help people understand how Google Search works and how the team improves and designs this service.
The Secret Security Features in macOS Big Sur
There are security features that Apple tells us about on stage at keynotes, and then there are hidden improvements it doesn’t mention.
macOS has gradually made the UNIX security model irrelevant. For example, even the superuser is only allowed to access the private documents of a regular user with the user’s permission—permission that is given on a per-application basis, through that protector of users and bane of developers known as the Transparency, Consent & Control (TCC) framework.