Apple has blocked GrayKey, an iPhone hacking device used by law enforcement. The company designed iOS 12 with protection against it, but no one knows how (via Forbes).
[How to Enable and Disable iPhone and iPad USB Restricted Mode]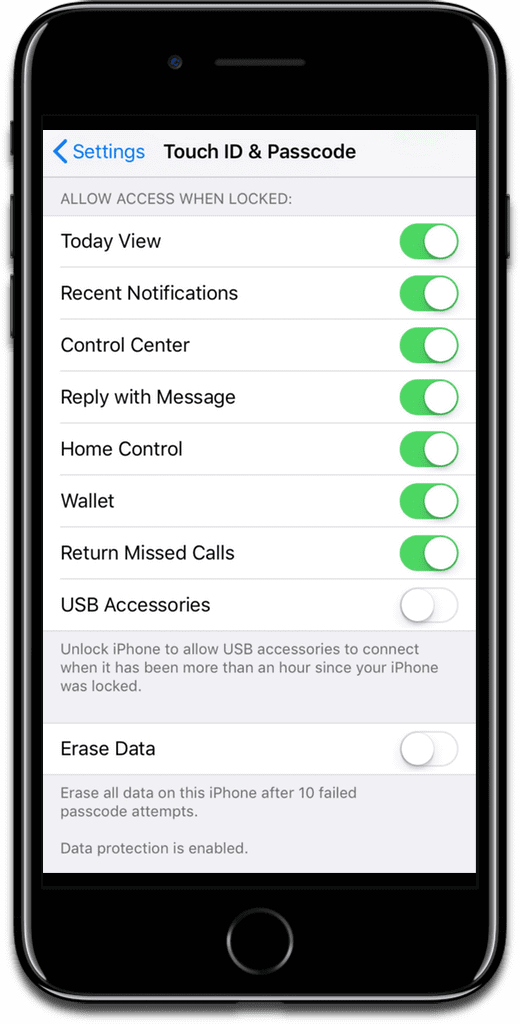
Achy, GrayKey Heart
We first learned of the GrayKey device back in March. Created by a company called Grayshift, and founded in part by a former Apple security engineer, it promised to break into iPhones as new as the iPhone X.
Grayshift is a secretive company, and got contracts with Immigration and Customs Enforcement (ICE) as well as the Secret Service. Certain U.S. law enforcement agencies had also started using the device.
It worked by using a hacking method called brute forcing, by guessing different combinations of passcodes swiftly. But eventually Apple was able to prevent GrayKey from working on devices running iOS 12.
No one is exactly sure how, although my guess is that Apple somehow obtained a device and reverse engineered it. Vladimir Katalov, chief of forensic tech provider Elcomsoft, told Forbes he was stumped: “No idea. It could be everything from better kernel protection to stronger configuration-profile installation restrictions.”
iOS 12 does have a new security feature that prevents USB accessories from accessing your device if your iPhone hasn’t been unlocked for over an hour. You can find the toggle in Settings > Touch ID & Passcode.
[Grayshift Customer Leaves iPhone Cracking Box Exposed, Data Breach Ensues]
I’m guessing reverse engineering as well. When this first came out six months ago I speculated that Apple was doing whatever they had to to get heir hands on one.