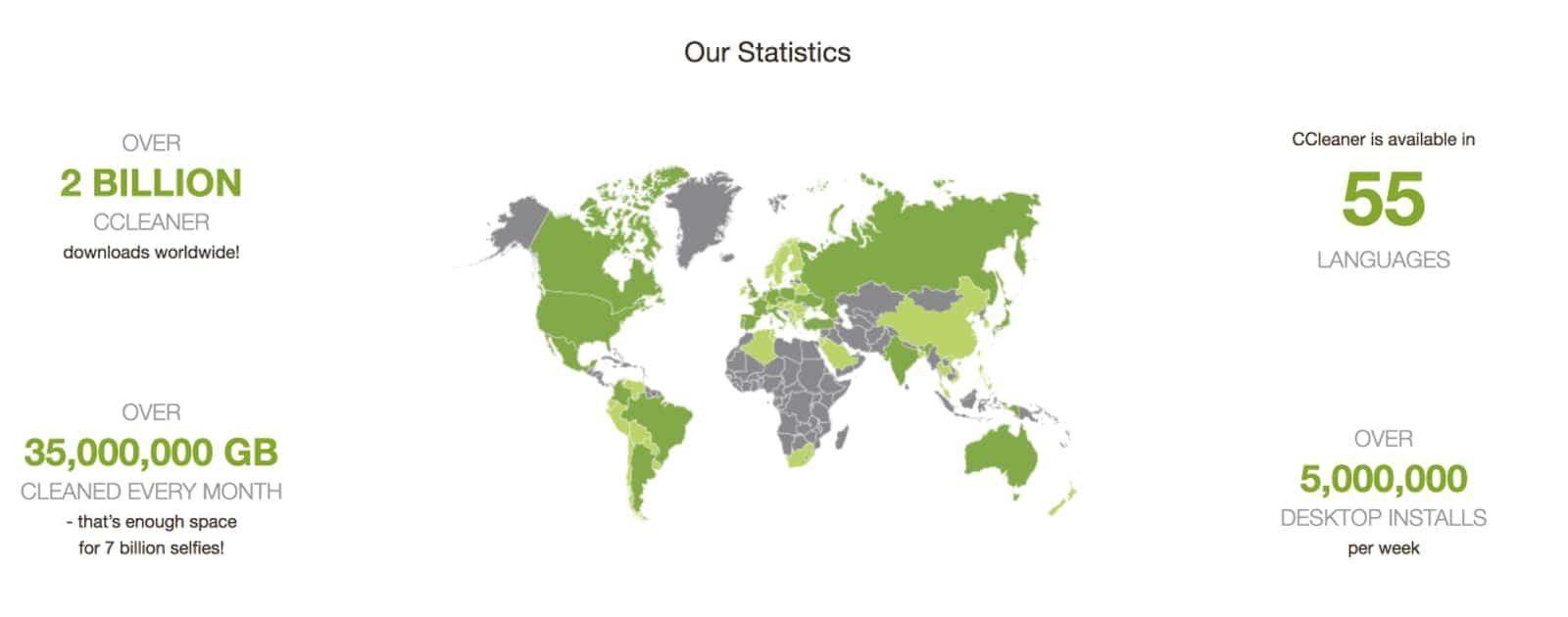
The CCleaner software utility was found to be infected with malware. The malware was inserted by an attacker by compromising the software’s supply chain. CCleaner has been downloaded more than 2 billion times, so the impact could be huge. The most ironic thing about this situation is that CCleaner was bought by antivirus vendor Avast.
The Detection
Cisco’s Talos Intelligence group detected the malware during beta testing of a new exploit-detection technology. The malware was found in a signed CCleaner version 5.3 installer. Talos found that CCleaner Cloud version 1.07.3191 is infected as well. In a blog post, Talos wrote:
On September 13, 2017 while conducting customer beta testing of our new exploit detection technology, Cisco Talos identified a specific executable which was triggering our advanced malware protection systems…it appears that the affected version (5.33) was released on August 15, 2017…It is also important to note that while previous versions of the CCleaner installer are currently still available on the download server, the version containing the malicious payloads has been removed and is no longer available.
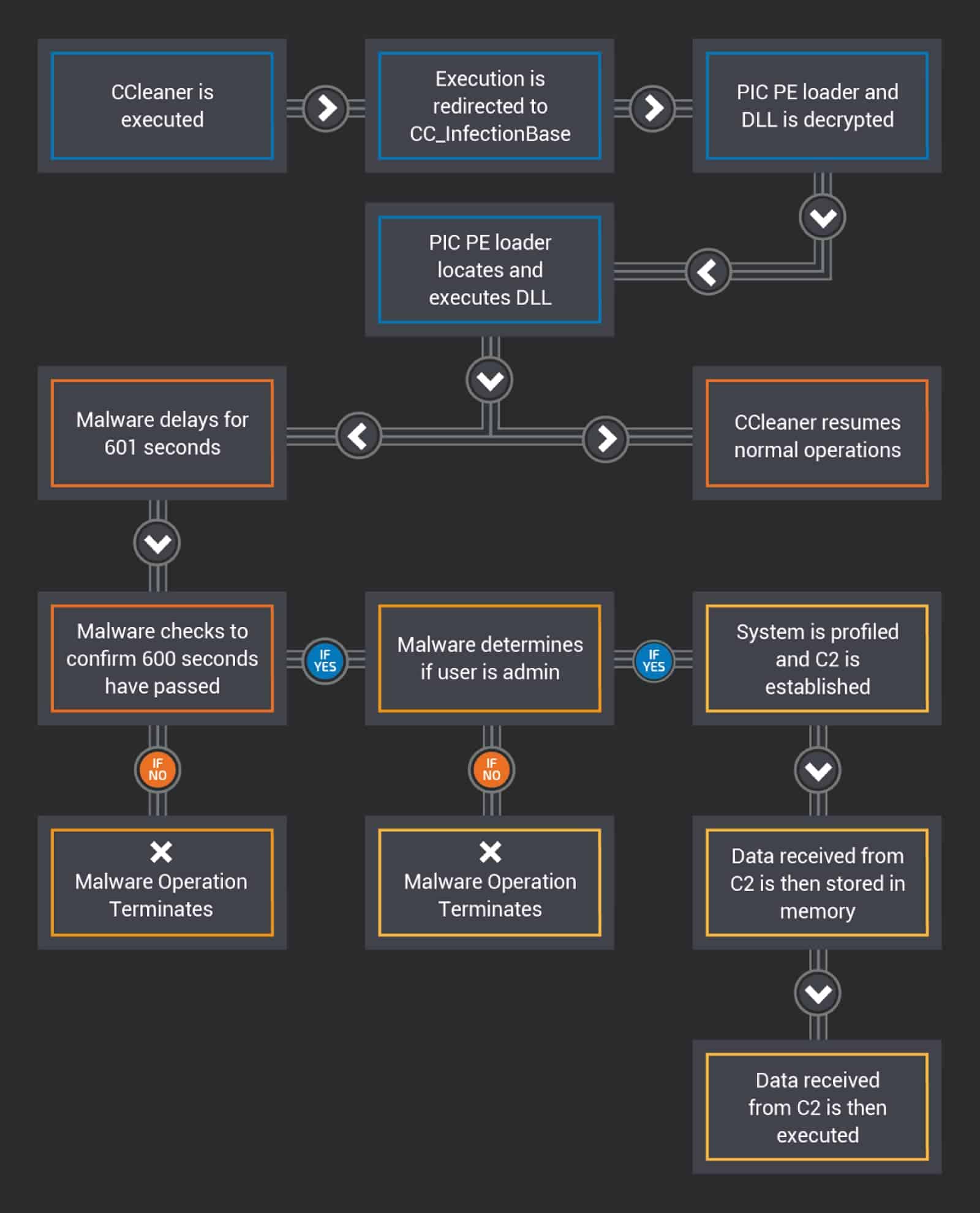
Talos isn’t clear on what exactly the malware was supposed to do. A diagram of the malware process can be seen below.
What You Can Do
First, the free version of CCleaner doesn’t do automated updates. The affected version is 5.3 and right now the latest update is 5.3.4. If you haven’t updated to version 5.3, you’re safe. It also only affects Windows users who have the 32-bit version of CCleaner.
If you have used the infected software, delete the software immediately and run an antivirus scan. To be completely safe you can also do a restore of your computer. Make sure to restore before August 15 which is when version 5.3 rolled out.