The iOS URL Scheme is a way for apps to work around the sandbox limitations of the OS. But it can also be taken advantage of.
URL Scheme
The iOS URL Scheme lets developers launch apps through URLs. In the example that Trend Micro gave, a URL that includes “facetime://” will open a FaceTime call. There are dozens of other schemes. A single URL Scheme can be used by multiple apps, including malicious ones.
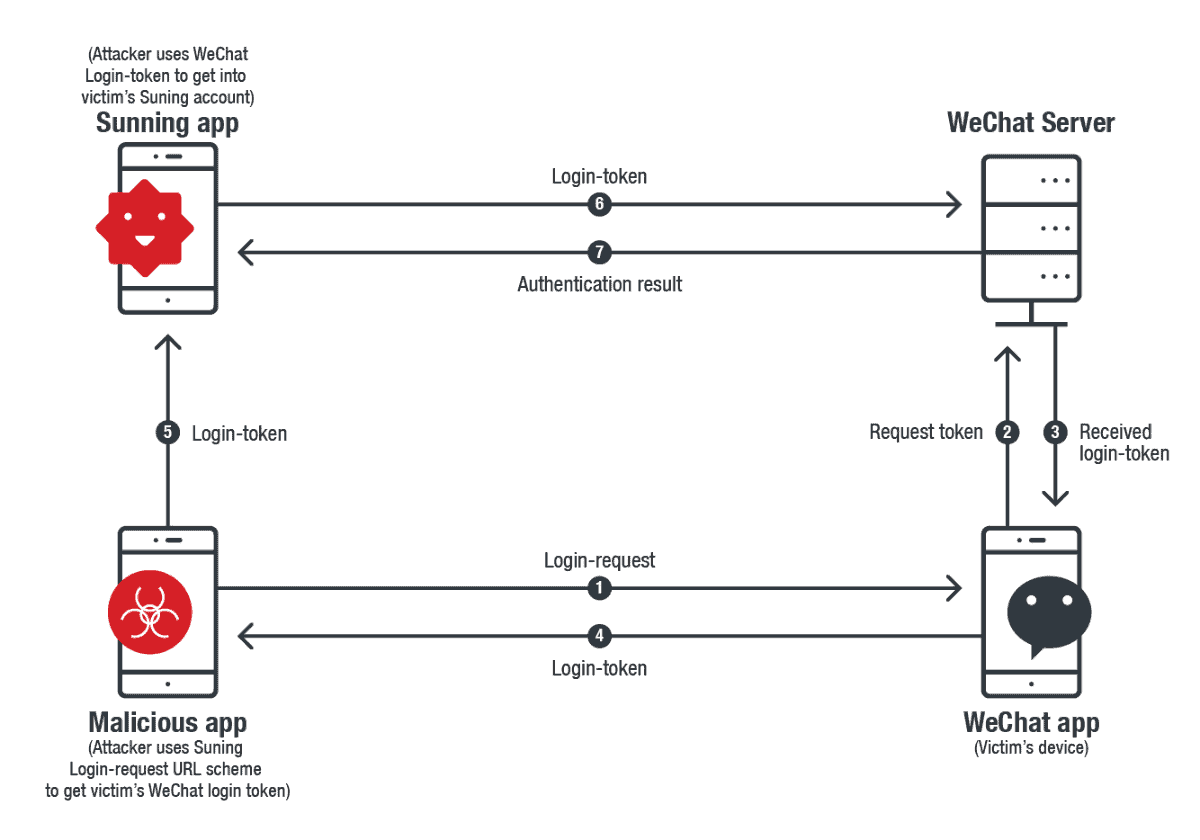
For instance, the Suning app (a retail application) allows a victim to log in using their WeChat account. The normal authentication process (seen below) is that the Suning app generates a URL Scheme query and sends it to WeChat App. When the WeChat app receives the query from the Suning app, it requests a Login-Token from the WeChat server and sends it back to the Suning app for authentication.
Our research found that Suning always uses the same Login-Request URL Scheme query to request the Login-Token, but WeChat does not authenticate the source of the login request. This allows an attacker to use an app’s Login-Request URL Scheme for malicious purposes.
There are also counterfeit URL Schemes. In bill replay phishing, a victim could be tricked into paying someone else’s bill by putting a billing request in the URL. Apps were also shown to have used schemes to make ads appear. Apple is aware of the risks, and told developers to validate all URL parameters and limit actions.
Further Reading:
[Apple Killing AR Glasses and ‘Product Design Troubles’]
[The YouTube Exec Working to Rid the Platform of Hatred and Scandal]
