Antivirus company Trend Micro has uncovered a new macOS backdoor, and it’s linked to OceanLotus. OceanLotus, also known as APT32 is a hacking group that started being active in 2017. They launched attacks against human rights organizations, media organizations, research institutes, and maritime construction firms.
macOS Backdoor
Trend Micro identified this backdoor as OSX_OCEANLOTUS.D. It targets Mac that have the Perl programming language installed. It was first found in a malicious Word document, and it most likely spread through email.
The document has the filename “2018-PHIẾU GHI DANH THAM DỰ TĨNH HỘI HMDC 2018.doc,” and this translates to “2018-REGISTRATION FORM OF HMDC ASSEMBLY.” It claims to be a registration form for an HDMC event. HDMC is a Vietnam organization that advertises national independence and democracy.
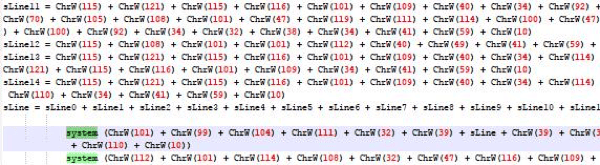
When a person receives the document, it will advise you to turn on Word macros, which is a type of script that can automate certain tasks in Microsoft Word. The code is obfuscated using decimal ASCII.
When Trend Micro de-obfuscated the code, it found that the payload was written in Perl. It extracts theme0.xml, which is a Mach-O 32-bit executable file extracted to /tmp/system/word/theme/syslogd.
Can You Do Anything?
First, it seems that macOS has a version of Perl seemingly installed by default. I know I didn’t download it, but when I ran this Terminal command:
perl -v
It told me which version of Perl I have. Even so, it doesn’t seem likely that most people will get an email like this. However, The Mac Observer has some best practices to make sure you’re safe from phishing attacks:
- Don’t open emails from senders you don’t know.
- If you do open one, don’t click on any URL or download any attachment.
- Back up your Mac regularly.
- Use antivirus software. Two that we recommend are Bitdefender and Avira.
If you do receive a Word document in the email, and it looks like something you want/need, you could open it via Pages on iCloud.com. Then, copy and paste it into a new document, or export it as a Word document from there. Keep macros turned off in Word, because that is a big vector for malware.

Perl is fundamentally built in to all versions of macOS, and Mac OS X before it. It cannot and should not be deleted. (Macs also ship with other scripting languages like Python, Ruby, Swift, etc. These shouldn’t be removed either.)
A quick check of the /usr/bin directory on a Mac running High Sierra turns up 150+ built-in system programs that use Perl; a broader search would turn up many more, but you get the idea.
The fix isn’t to rip fundamental tools out of your computer. The fix is the other recommendations — like don’t open weird attachments from unknown senders, etc.
Question: Is there any reason for the average user to keep Perl installed on their Mac? And if not, how do you uninstall it?