Microsoft’s security team has published an analysis of “powerdir” a vulnerability in macOS that could let an attacker access a person’s data. Apple patched the bug, tracked as CVE-2021-30970, in an update on December 13, 2021 (macOS Monterey 12.1 and macOS Big Sur 11.6.2).
Powerdir macOS Bug
Since 2012’s OS X Mountain Lion, the operating system has included something called Transparency, Consent, and Control (TCC). It let’s users control the privacy settings for apps, such as access to the Mac camera, microphone, calendar, and more. It’s found in System Preferences > Security & Privacy > Privacy. Apple included a feature to stop unauthorized code execution and restrict TCC to apps with full disk access.
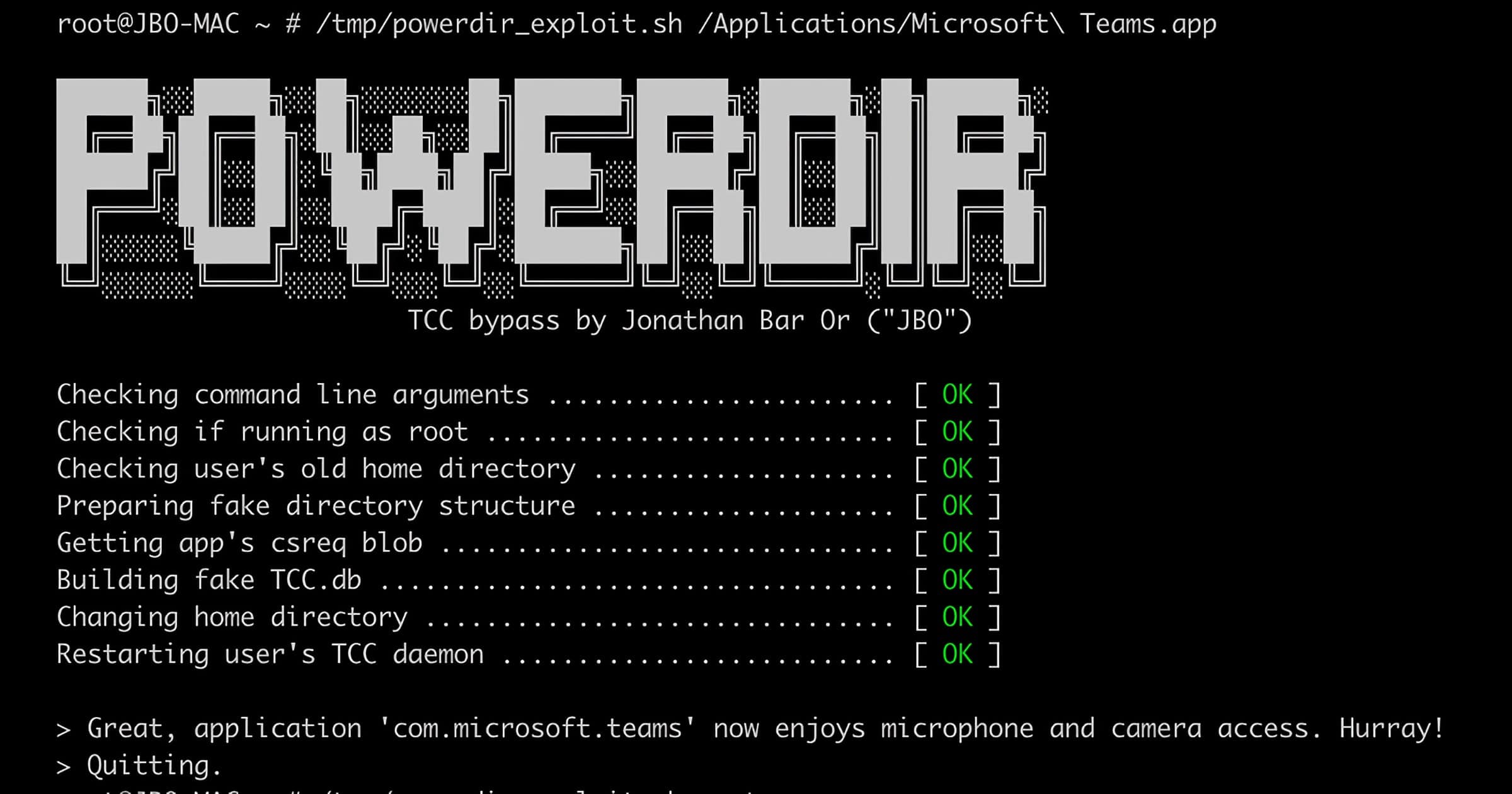
Powerdir makes it possible to change a victim’s home directory or insert a fake TCC database. If exploited, the attacker could access features such as the microphone, hijack an installed app, or install their own malicious app. Screenshots could also be taken of the contents of the display, such as sensitive information.
TCC’s database stores the consent history for apps so that users don’t have to repeatedly grant/deny access to a system feature. Microsoft says there are two types of TCC databases:
- User-specific database contains stored permission types that only apply to the specific user profile; it is saved under ~/Library/Application Support/com.apple.TCC/TCC.db and can be accessed by the user who owns the said profile
- System-wide database contains stored permission types that apply on a system level; it is saved under /Library/Application Support/com.apple.TCC/TCC.db and can be accessed by users with root or full disk access
The attacker could modify the TCC database to edit these permissions to any app, including their own malicious app. The user wouldn’t be prompted to grant/deny access. Microsoft’s security team made a proof-of-concept exploit to test the powerdir vulnerability. The full write-up is worth a read and it’s not too technical.