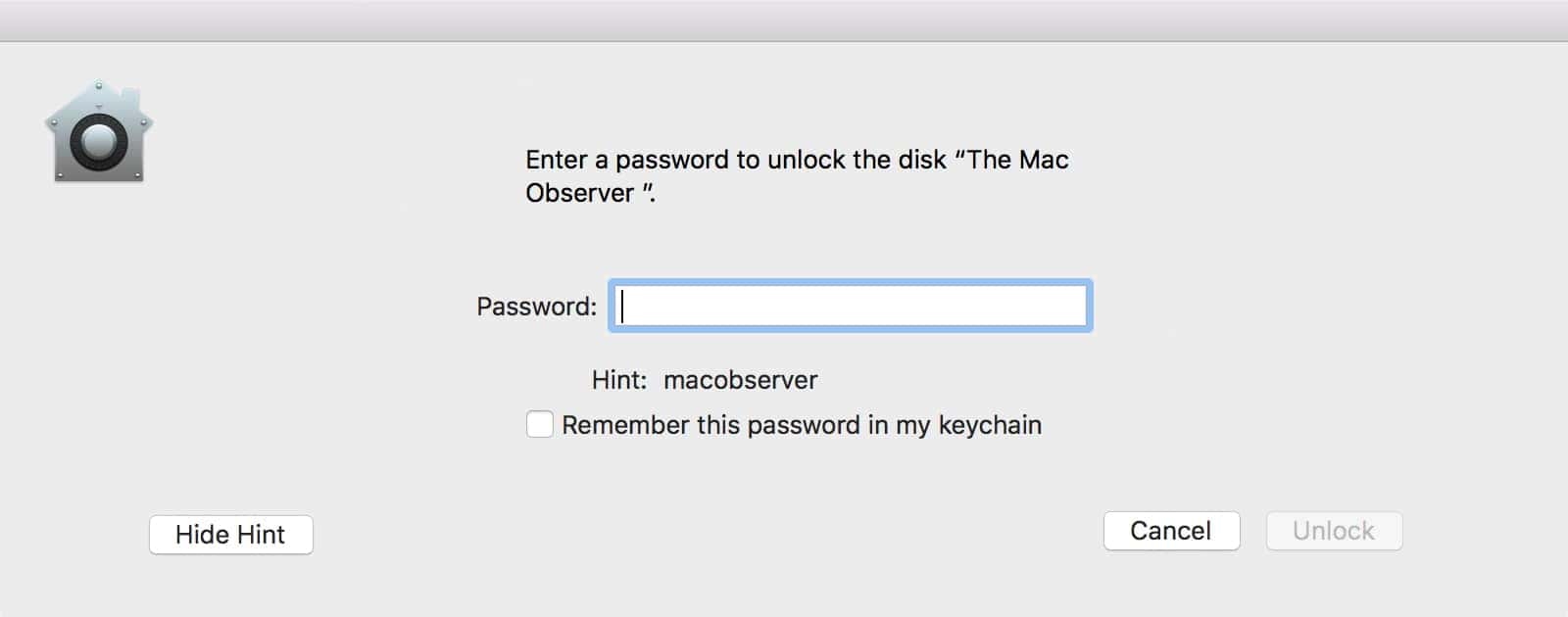
An APFS password vulnerability has been found in Apple’s latest release of macOS. It happens when you create an encrypted APFS container through Disk Utility. Software developer Matheus Mariano first discovered this, and it’s troubling that Apple missed this. When you create the encrypted container, your password ends up being displayed in plain text.
APFS Password
Matheus posted a video on YouTube where he shows what happens. I tested it by creating my own encrypted APFS container. You have to choose a password, and then a password hint. After you unmount and remount the container, click the button “Show Hint.” Your password will be displayed, even though the password hint you chose was completely different.
Matheus tested this on a 2016 MacBook Pro running macOS High Sierra, including versions 10.13 and 10.13.1 beta. He already reported it to Apple, so we can expect a fix in the next update or so. Still, it’s weird that a vulnerability like this slipped through the cracks.
Be aware that this only affects Macs with SSDs. This is because Apple’s new APFS file system only works with SSDs, although support for Fusion Drives is coming. The password vulnerability seems to be an issue with Disk Utility itself, rather than a bug in the whole OS. If you create an encrypted APFS volume in Terminal using diskutil, it displays the actual password hint, instead of the password.
Update – 10/4/2017
Apple has released a supplemental update for macOS that fixed this vulnerability, as well as the keychain exploit that was previously found.