A highly-targeted attack via MDM (mobile device management) software installed malicious apps onto 13 iPhones. Cisco’s Talos Intelligence Group discovered the MDM hack.
[Apple is Making iPhone Hacking A Lot More Difficult for Law Enforcement with iOS 11.4]
MDM Hack
The attack appears to be in India, and involved the attackers getting 13 iPhones registered with rogue MDM servers. It then pushed out malicious apps that let the attackers track the location of the phones and read SMS messages.
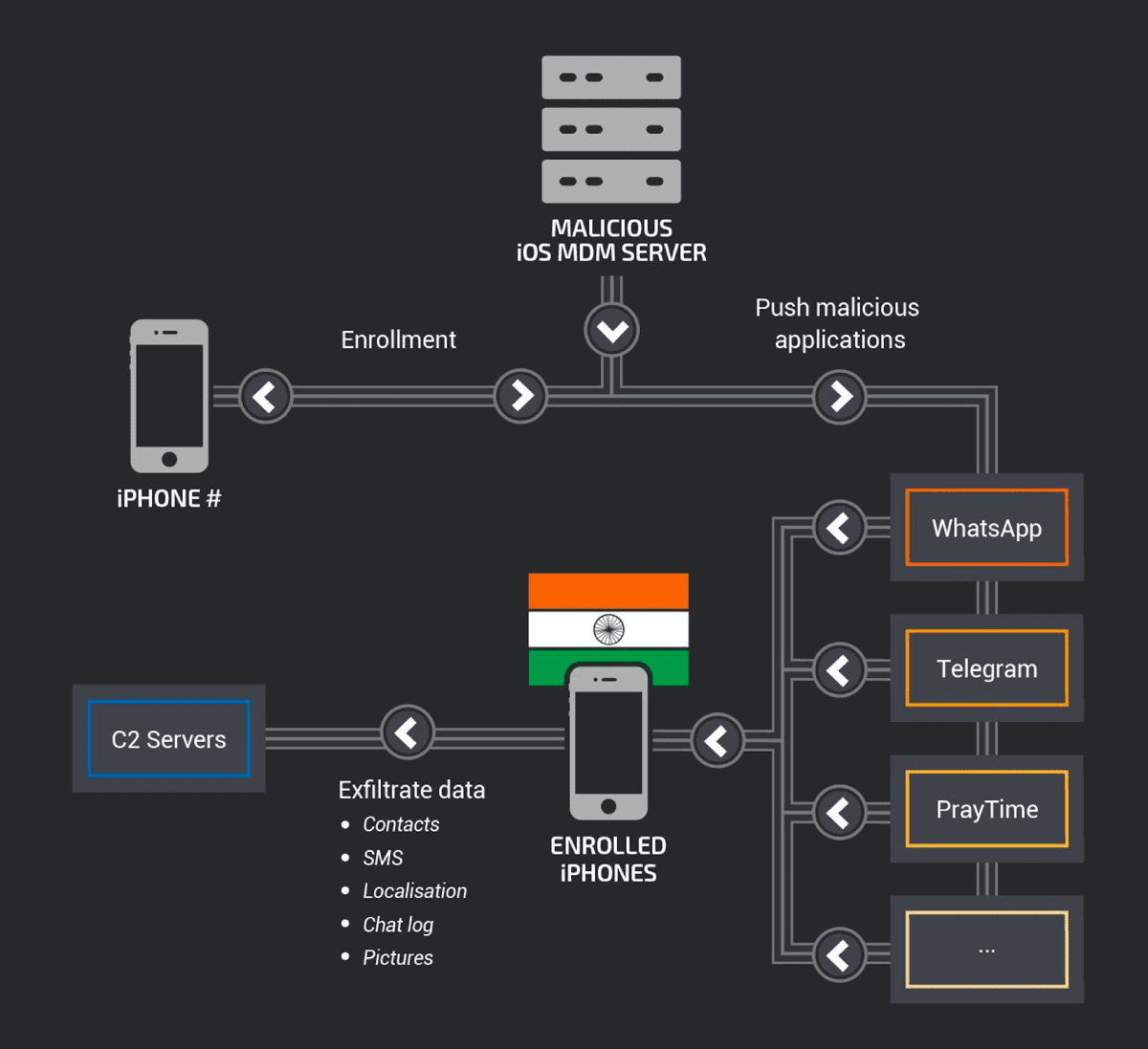
It used a “BOptions” sideloading technique to modify versions of apps like WhatsApp and Telegram. Talos researchers Warren Mercer, Paul Rascagneres, and Andrew Williams wrote a blog post:
The malicious code inserted into these apps is capable of collecting and exfiltrating information from the device, such as the phone number, serial number, location, contacts, user’s photos, SMS, and Telegram and WhatsApp chat messages. Such information can be used to manipulate a victim or even use it for blackmail or bribery.
Two servers identified were:
- hxxp://ios-certificate-update[.]com
- hxxp://www[.]wpitcher[.]com
MDM software lets an administrator manage multiple iDevices to install/remove apps, install/revoke certificates, lock devices, change password requirements, etc. The servers were registered with mail.ru addresses.
Okay, is there any threat from this to the average iPhone user?
These iPhone users were targeted. If you’re in an organization that uses MDM software, knowledgeable people might be able to perform this hack, but otherwise it’s not something most people need to worry about.