There is a new piece of malware floating around the interwebs. This SysJoker backdoor, as it was called, was discovered in December 2021 by the Intezer team.
SysJoker Backdoor
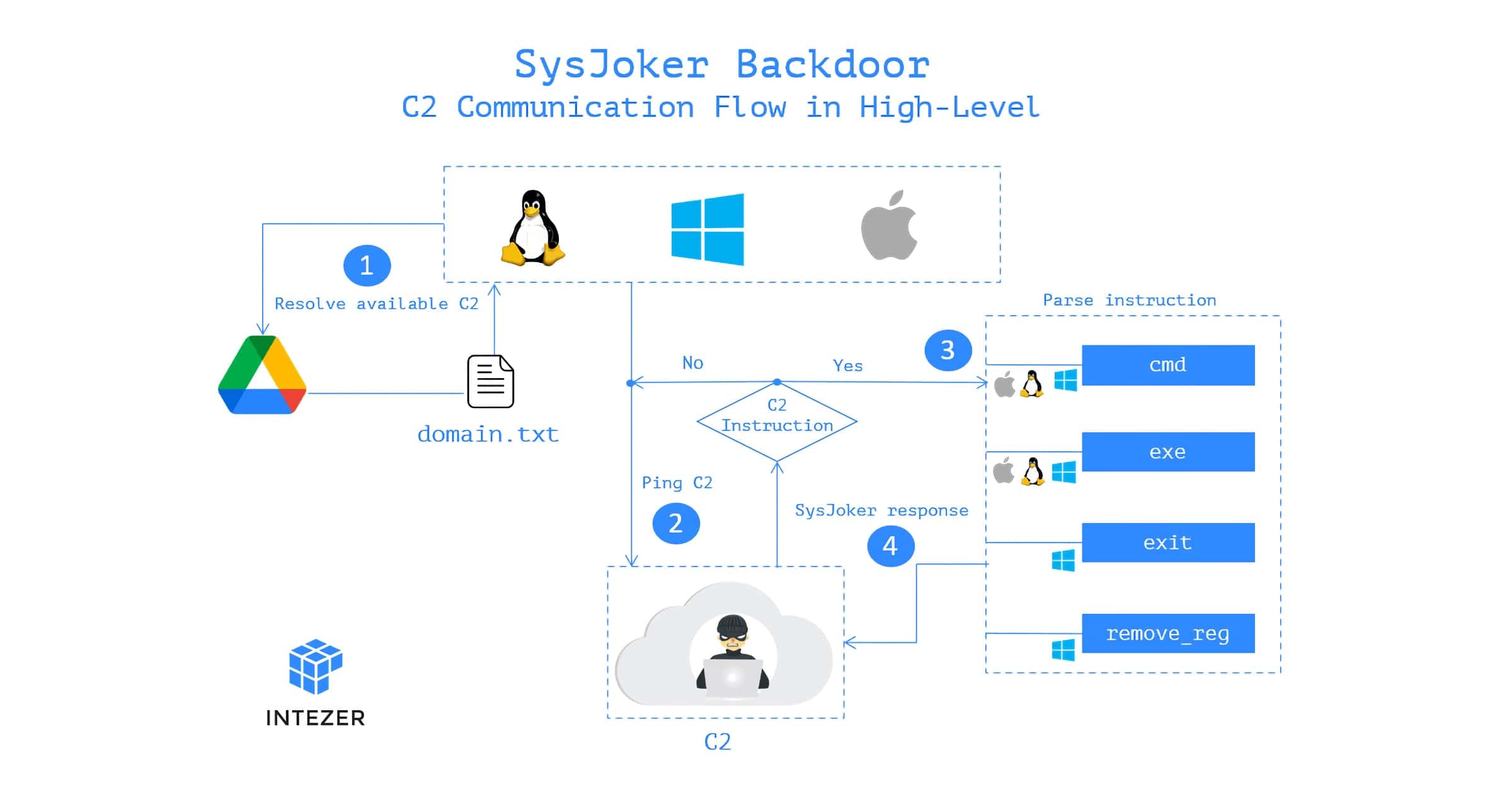
The SysJoker backdoor can infect macOS, Windows, and Linux machines. It was first dissevered while it was actively attacking a Linux web server of “a leading educational institution.” Based on its Command and Control (C&C or C2) domain registration and samples, Intezer believes the attack started sometime during the second half of 2021.
SysJoker pretends to be a system update and generates the C2 domain by decoding a string from a text file hosted in Google Drive. The team says that during its analysis the malware’s C2 changed three times. This suggests the attack is actively monitoring for machines to infect. The SysJoker backdoor also seems to target specific victims.
A sample of the malware was uploaded to VirusTotal, a website for security researchers that analyzes uploaded files and URLs for malware. The SysJoker backdoor is written in C++ and can be tailored for each operating system. So far, VirusTotal doesn’t flag the macOS and Linux variants as being malware.
Detection
Intezer’s report is a technical analysis of the SysJoker backdoor, but it shares a way to detect the malware.
Use memory scanners to detect SysJoker payload in memory:
- For Linux machines, use Intezer Protect to gain full runtime visibility over the code in your Linux-based systems and get alerted on any malicious or unauthorized code. We have a free community edition.
- For Windows machines, use Intezer’s Endpoint Scanner. The Endpoint Scanner will provide you with visibility into the type and origin of all binary code that resides in your machine’s memory.
There doesn’t appear to be a method of detection for Macs.
A final interesting point is that Intezer believes SysJoker is from an “advanced threat actor.” The code was written from scratch, at least four C2 domains were registered, and the malware targets specific victims. “Based on the malware’s capabilities we assess that the goal of the attack is espionage together with lateral movement which might also lead to a Ransomware attack as one of the next stages.”