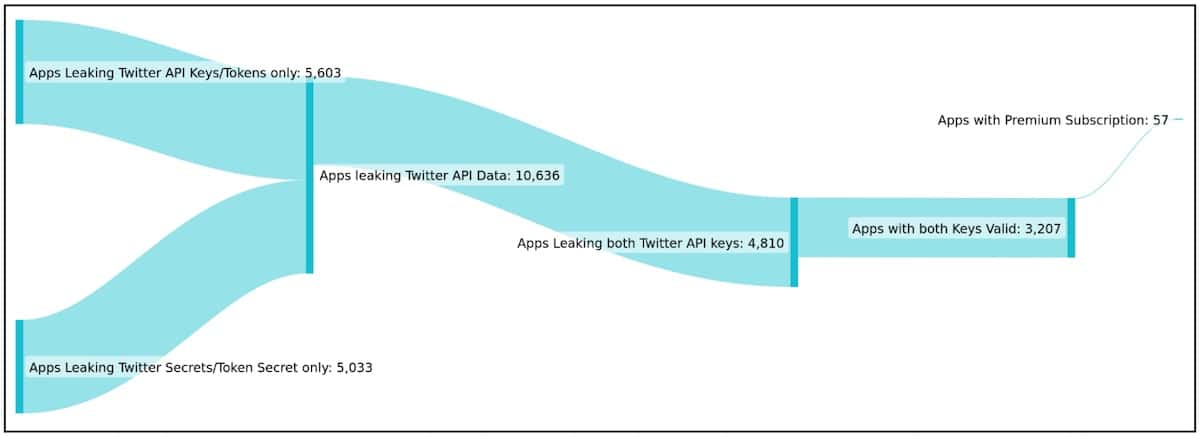
Cybersecurity researchers have uncovered a set of 3,207 mobiles apps that expose Twitter API keys to the public. This can potentially enable a threat actor to overtake a users’ Twitter accounts that may have association with the app.
According to BleepingComputer, Cybersecurity firm CloudSEK is responsible for the discovery. After implementing BeVigil, a security search engine for mobile apps, the firm also scrutinized large app sets for data leaks and discovered 3,207 apps leaking a valid Consumer Key and Consumers Secret for the Twitter API.
Of the 3,207 apps, 230 of them were leaking all four Auth Cred to fully take over a Twitter account.
Cybersecurity Firm Finds Developers Leak Twitter API Keys
Essentially, when developers integrate mobile apps with Twitter, they receive authentication keys, or tokens, allowing mobile apps to interact with Twitter API. When a user links their Twitter account with the mobile app, the keys also enable the app to act on behalf of the user. Thus, the app can log them into Twitter, create tweets, send DMs and more.
Since authentication keys can allow anyone to perform actions as an associated Twitter user, this is why keys should never be stored directly within the mobile app. According to CloudSEK, leaks of API keys are typically due to mistakes by app developers. If developers forget to remove authentication keys in the Twitter API, the app becomes compromised and exposed to threat actors.
According to the report from CloudSEK, the most prominent situation for abuse is for threat actors to use the exposed tokens in order to create a Twitter army of trustworthy accounts featuring a large number of followers. These accounts could then promote fake news, malware campaigns, cryptocurrency scams and more.
Starting a Bot War
So while individual users accounts are likely okay, the real concern is that big name accounts may start peddling crypto or conspiracy theories.
In a report from CloudSEK, they stated,
The Twitter bot army that we will try to create can fight any war for you. But perhaps the most dangerous one is the misinformation war, on the internet, powered by bots. Time Berners-Lee, the founding father of the internet said that it is too easy for misinformation to propagate because most people get their news from a small set of social media sites and search engines that make money from people clicking on links. These sites’ algorithms often prioritize content based on what people are likely to engage with, which means fake news can “spread like wildfire”
Additionally, CloudSEK recommends that developers implement API key rotation in order to protect authentication keys. CloudSEK also suggests developers start ensuring the accuracy of its versioning and hiding or disguising keys.
To complicate matters, CloudSEK did share the list of impacted applications with BleepingComputer. However, neither BleepingComputer nor CloudSEK is releasing the list publicly. Currently, many of the apps are still vulnerable to exploitation and account takeover.
Unfortunately, most applications that are currently exposing their API keys publicly have yet to acknowledge CloudSEK’s notices. This is despite the firm notifying them over a month ago. The only exception was Ford Motors which fixed their ‘Ford Events’ app after discovering it was leaking Twitter API keys.
Furthermore, last month, a hacker was selling a database allegedly consisting of 5.4 million users. The breach came after an exploit was found in January. Twitter has since patched the exploit.
You can read the full report from CloudSEK here.
