UpdateAgent is the name of a Mac trojan that Microsoft has been tracking since October, although the company says it first appeared in September 2020.
UpdateAgent
UpdateAgent started as a basic piece of malware that stole information. But it has evolved to distribute secondary payloads onto a machine, such as Adload adware. There are two variants of this trojan and Microsoft believes it’s still in the development stage. Updates are likely to arrive in the future that could add more capabilities to it.
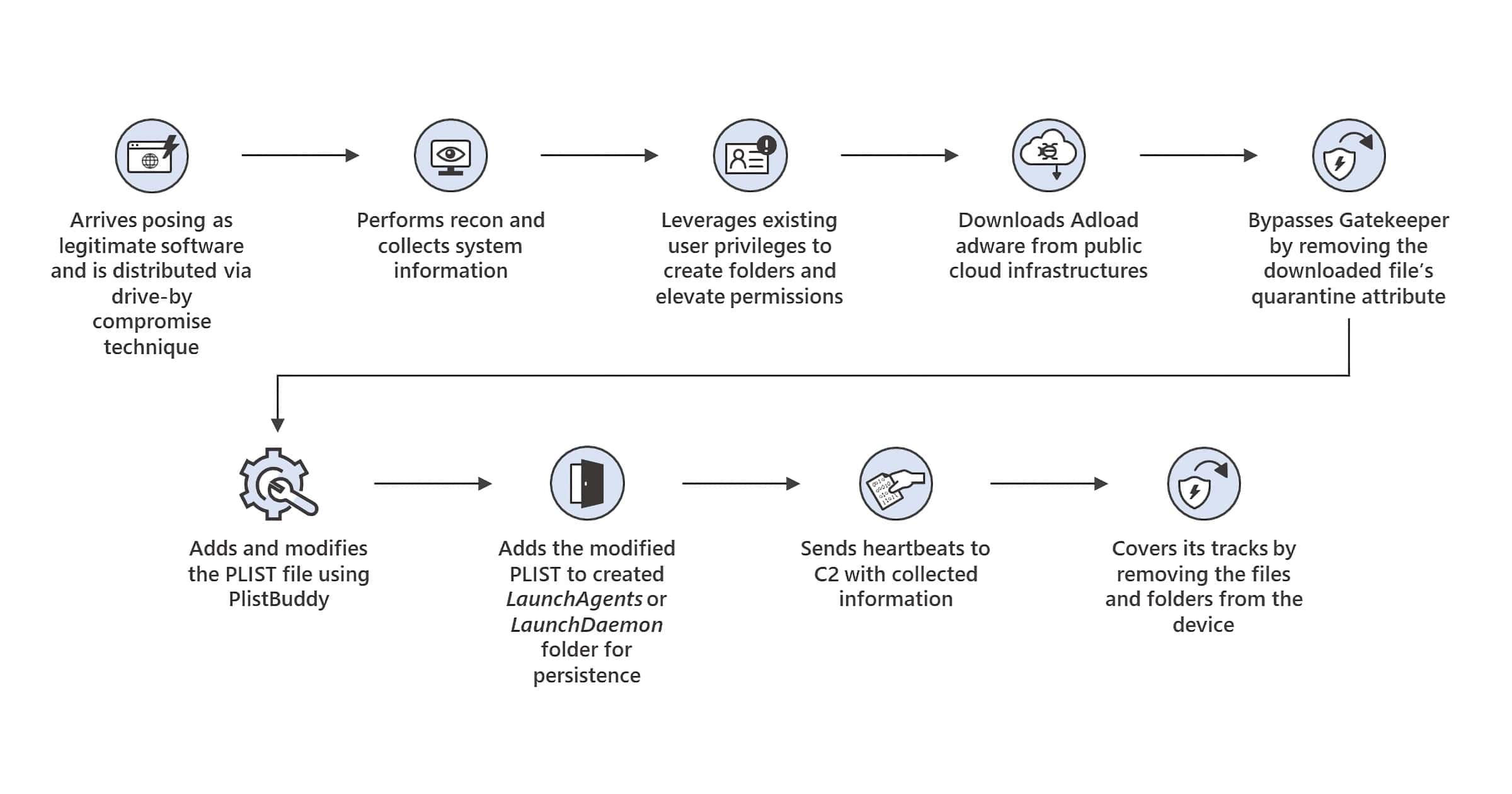
UpdateAgent can impersonate legitimate software and can use various Mac device functionalities. It can bypass Gatekeeper which Apple created to make sure only trusted apps can run on Macs. The malware can make use of existing user permissions to perform activities in the background and delete the evidence afterward. UpdateAgent can also use public cloud services such as Amazon S3 and CloudFront to host its malicious payloads. Microsoft alerted Amazon, which removed the malicious URLs on its platform.
Because of its mimicking capabilities, people are likely to be infected via “drive-by downloads” or ad popups. Once installed, UpdateAgent starts to collect system information that is then sent to its command-and-control (C2) server.
Timeline
Microsoft has shared a timeline of UpdateAgent;
- September–December 2020: The initial version of UpdateAgent was considered to be a fairly basic information-stealer. At the time, the malware was only capable of performing reconnaissance to scan and collect system information such as product names and versions.
- January–February 2021: Approximately two months later, UpdateAgent maintained its original capabilities and added a new one: the ability to fetch secondary payloads as .dmg files from public cloud infrastructure.
- March 2021: Upon its third update, the malware altered one of its prior functions to fetch secondary payloads as .zip files instead of .dmg files. The malware’s developer also included two new capabilities: the ability to bypass Gatekeeper by removing the downloaded file’s quarantine attribute and the ability to create a PLIST file that is added to the LaunchAgent folder.
- August 2021: The malware’s fourth update further altered some of its prior capabilities. For one, it expanded its reconnaissance function to scan and collect System_profile and SPHardwaretype information.
- October 2021: UpdateAgent included the ability to enumerate LSQuarantineDataURLString using SQLite in order to validate whether the malware’s downloaded app is within the Quarantine Events database where it would be assigned a quarantine attribute. The upgrade also allowed the malware to leverage existing user profiles to run commands requiring sudo access in addition to the ability to add arguments using PlistBuddy to create and edit PLIST files more easily. Lastly, the trojan included the ability to modify sudoers list.
Microsoft’s blog post has additional information. The company says its Defender Antivirus can detect UpdateAgent.