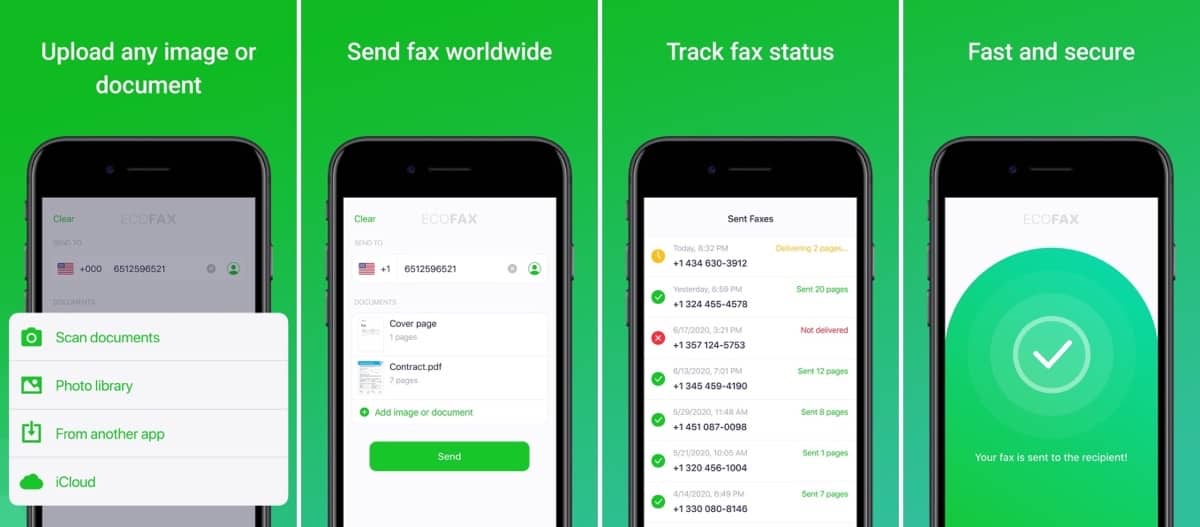
EcoFax is an app that lets you send fax from your iPhone. At the end of the month, the company plants trees to compensate for all the paper used to deliver those faxes. They partnered with Trees for the Future Foundation and aim to increase the number of trees they plant as more people use the app. I checked the privacy policy, and it can access and collect data like: your identity, location data, camera, contacts, storage, photos and/or media, notifications, and mobile data. Camera, contacts, storage, and photos make sense, because that’s how the app functions. If that doesn’t bother you and you need to send faxes, maybe consider EcoFax. App Store: Free (Offers In-App Purchases)
Apple's Head of Diversity And Inclusion Christie Smith Departs Company
Apple’s Vice President, Inclusion and Diversity Christie Smith has left the company after three years there.
New: The macOS Security Compliance Project
The objective of this project is to develop an extensible, modern approach to security guidance that can be used by any organization to adhere to security compliance frameworks and policy. Project outputs include scripts, documentation, and configuration profile payloads
Slack Unveils New Work From Home Emoji Pack
Slack has become essential during this period of working from home. On Monday, the company unveiled a set of remote working emoji to help users communicate with their colleagues. It said in a blog post that the emoji will be rolling out over the coming days.
We’ve created a handy set of custom emoji for using in your status (or in messages or reactions) for those moments when you need to convey more information. This emoji pack for remote work is rolling out now and will be available to everyone in the coming days. You can add this set of emoji by clicking the “add emoji” button within the emoji picker. If you still need help, here’s a link to our help center article on adding custom emoji to Slack.
Gulf States Use COVID-19 Contact Tracing Apps For Mass Surveillance
Some Gulf states are using COVID-19 contact tracing apps as mass surveillance tools. The issue was highlighted in research by Amnesty International, reported on by The Verge.
Amnesty International found that the Gulf states’ apps it analyzed were among the most invasive, collecting and storing GPS data and making it easy for the government to identify someone based on their account ID. Norway’s app was also flagged for putting its citizens’ privacy at risk for collecting and storing location data on a central server. But the country on Monday said it would pause the rollout of its the app, called Smittestopp, after Amnesty International shared its findings with the Norwegian government… Apple and Google are still in the process of developing a more privacy-focused system for the US and other countries that would work across both Android and iOS, while some governments have simply made their own apps along separate lines.Gul
Fantastical Adapts to Work From Home Reality
Fantastical has been updated to try and accommodate users working from home more, including adding links to video conference calls.
WWDC 2020 Hopes: Services Bundle, Messages Fixed, Mac Mini Updated
A services/media bundle, Messages fixed, and the Mac mini updated are some of the key things Charlotte would like to see at WWDC 2020.
New Feature ‘Sleep Mode’ Could Arrive on iOS 14
Apple leaker Fudge (@choco_bit) claims that a new feature coming to iOS 14 will be called Sleep Mode.
When Sleep Mode is enabled, the lockscreen will dim, calls and alerts that arrive while locked will be silenced, and notifications will be sent to history. Emergency alerts will break through. Sleep will analyze your sleep patterns based on your iPhone usage at night.
Bedtime in the Clock app can set an alarm and track your time in bed. Do Not Disturb can silence calls and alerts. So if this rumor is true then it sounds Apple is rebranding and combining these disparate features into one Sleep Mode toggle.
Apple Hit With Lawsuit for App Store Loot Boxes
Apple was sued on Friday with a class action lawsuit for allowing apps and games to add loot boxes and profiting off of them.
WWDC Wishlists – TMO Daily Observations 2020-06-16
Andrew Orr and Charlotte Henry join host Kelly Guimont to discuss what they’re looking forward to seeing in the WWDC keynote next week.
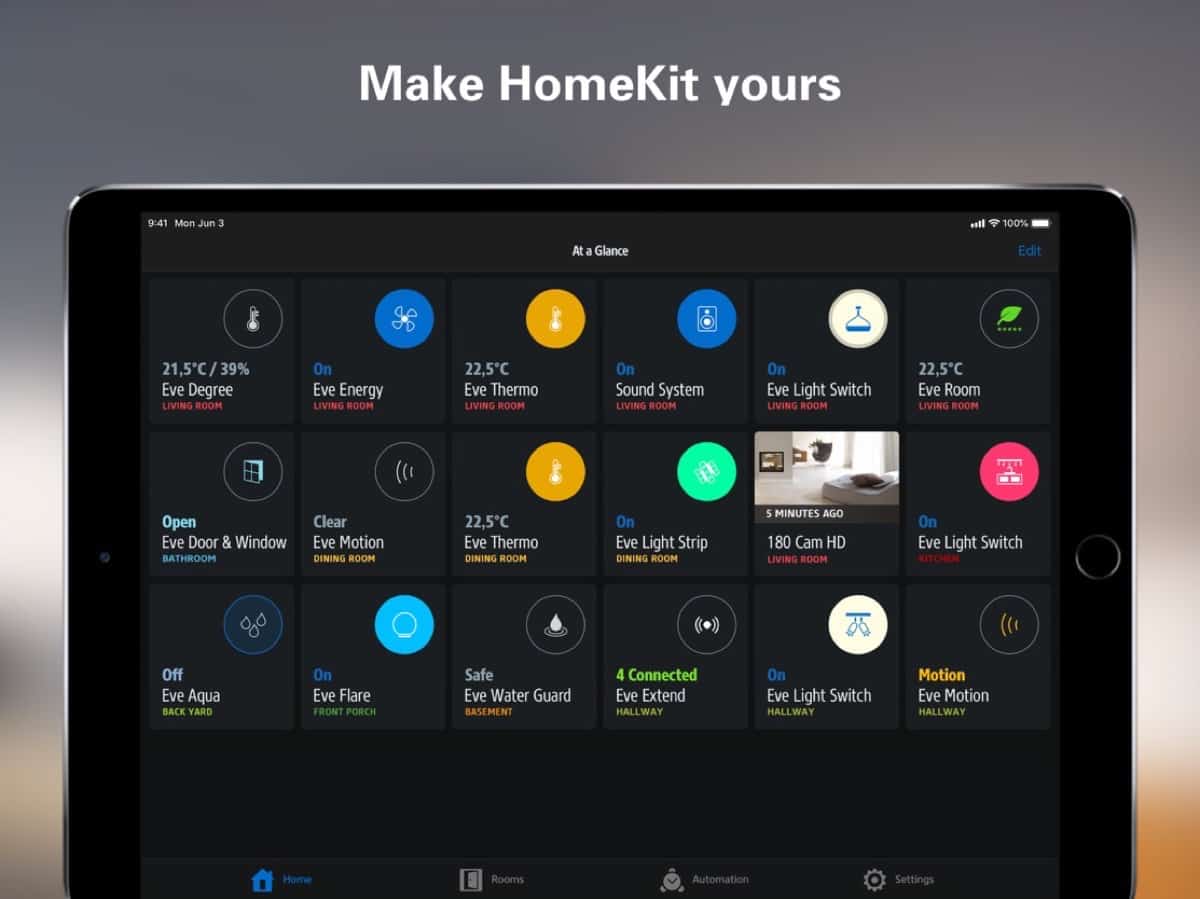
‘Eve’ 4.3 Update Gives You Faster Access to HomeKit Features
Eve 4.3 adds fast access, improved customization options, and improvements for new products like Eve Cam and Eve Window Guard. You can now long press in almost any area of the app to quickly control an accessory, set a scene, and view its details. Get an overview of a room to instantly toggle all lights and refine room settings. You can also touch, hold, and slide your finger to quickly select a command. Eve 4.3 adds a new way to view and manage automations directly in the accessory’s details view. Long press to toggle Rules and set Scenes, or create new rules and scenes. App Store: Free
Apple Acquires Rights to Israel-Iran Spy Series ‘Tehran’
Apple has acquired rights to stream “Tehran” outside of Israel. It’s distributed by Cineflix Rights and stars Israeli actress Niv Sultan.
Eero Wi-Fi Products Now Available in Apple Retail Stores
Eero recently announced that its eero Wi-Fi products are available in Apple retail stores, after having launched on Apple.com in May.
WWDC 2020 Swift Student Challenge Winners Revealed
In the run-up to WWDC 2020, Apple has revealed the story behind some of if its Swift Student Challenge winners.
EU Launches Investigations Into App Store And Apple Pay
The EU opened two antitrust investigations into Apple that will look into whether App Store violates antitrust rules and also Apple Pay.
App Store Ecosystem Supported $519 Billion Globally in 2019
Apple announced today that in 2019 the App Store supported US$519 billion in billing and sales globally.
TMO UK Associate Editor Charlotte Henry (#6) - TMO BGM Interview
Charlotte is the Mac Observer’s UK Associate editor, based in London. A self described media junkie, she has also written for City A.M. (London’s daily business tabloid,) Computer Business Review, and The Times, amongst others. Her new book is: Not Buying It.
In this episode, Charlotte and I dig deep into Apple TV+. We look at its current market share and growth potential based on a zero sum game, the possible addition of live sports, and a customer satisfaction survey. In passing, Charlotte believes that the naming conventions Apple has used for its Apple TV hardware and software have created a giant mess of customer confusion. We explored some new shows and also examined the character of Apple TV+ content compared to other streaming TV services.
Google Chrome 85 Hides Full URL Addresses
Google wants to follow in Apple’s footsteps by hiding the full URL in Google Chrome 85. Instead, with an optional (for now) toggle, users can choose to have the address bar display only the top level domain.
There’s no public explanation yet for why Google is pressing ahead with these changes, but the company has said in the past that it believes showing the full address can make it harder to tell if the current site is legitimate.
However, it’s also worth considering that making the web address less important, as this feature does, benefits Google as a company. Google’s goal with Accelerated Mobile Pages (AMP) and similar technologies is to keep users on Google-hosted content as much as possible, and Chrome for Android already modifies the address bar on AMP pages to hide that the pages are hosted by Google.
In other words, Google doesn’t want people to be able to tell the difference between Google and the internet.
WWDC 2020 'Full Stream Ahead' Keynote Invites Arrive
Invites to the online-only WWDC 2020 keynote have arrived in inboxes, emblazoned with the title ‘Full Stream Ahead.’
How Nianitic is Working to Follow the Success of Pokémon Go
Following a hit is always hard. Gamesmaker Niantic has found this after the mega-success of Pokémon Go. The company’s boss John Hanke told Bloomberg News on how it is trying to create the next big thing.
“We’re hard at work on our games pipeline with a multiyear product road map made up of games and other forms of AR experiences,” John Hanke, chief executive officer of the San Francisco-based studio, told a group of reporters last week. “We are extending the concept of what constitutes a Niantic game in a variety of ways,” he added, without elaborating. AR technology, which blends digital elements with real-world environments, is seen as one of the next big leaps in mobile tech and many firms are gearing up to seize the opportunity. That includes Apple Inc., which Bloomberg News has reported will build 3-D cameras into this year’s iPhone generation like it’s done for the latest iPad Pro. Formerly a part of Alphabet Inc.’s Google — which has its own AR ambitions — Niantic is in charge of the most popular AR app in history with Pokémon Go.
Notability 9.4 Update Improves the Audio System, Plus 8 new Languages
The newest update to Notability—9.4—adds improvements to audio recordings. These recordings can now be renamed, reordered, trimmed, merged, and split. The sound equalizer has been improved in which frequencies can be adjusted for optimal listening. The recording UI has been updated, too. Next, eight new languages have been added for handwriting recognition: Danish, Filipino, Indonesian, Malay, Polish, Swedish, Ukrainian, and Vietnamese. Finally, a mix of smaller updates include support for iPadOS mouse pointers, themed popovers with Dark Mode, and fixes an issue where the tool switching in the top toolbar could sometimes become unresponsive. App Store: US$8.99
2020 Apple Back to School Promotion Offers Free AirPods With Mac or iPad
The 2020 Apple ‘Back to School’ promotion has been announced. Students can get a free pair of AirPods with the purchase of a Mac or iPad.
WWDC 2020: How Developers Plan to 'Attend' Apple's Event
While the fact that WWDC 2020 is going to be virtual even means developers and other attendees will save on hotels and flights, they will miss out on some of the benefits in-person attendance means. A number of them told CNBC how they intend to make the most out of next week.
Adrian Eves, an iOS developer based in Alabama, said he plans to take all of WWDC week off work so he can follow along with the videos and announcements. He’s created a Slack group called WWDC Lobby to discuss the announcements in real-time with other fans, including Apple employees. “Since everything’s remote, we need a way to adapt ourselves to this experience. I’ve been to different conferences, and the best thing is, besides the subject matter, the networking,” Eves said… For independent developers and companies that send several people, the savings could be substantial. “WWDC moving online is terrific for smaller developers, particularly those based abroad. Even for us, WWDC being online will save us upwards of $100,000 on event sponsorships, travel, and accommodation, since most of our team is based in Europe,” said Oleksandr Kosovan, CEO of MacPaw, a software developer focused on Apple products.
Apple Developer Mac App Updated With New UI
Today Apple released a developer app on macOS called Apple Developer, which matches the iOS app of the same name. In fact, this could very well be the Catalyst version of the iOS app. The reason I think so is because I noticed my “Get App Icon” gave me the iOS icon, even though I used the Mac link. Or, that could mean nothing. The app is meant to be your one-stop guide to developer news, and also a great place to watch WWDC 2020. Stay up to date on the latest technical and community information; browse news, features, developer stories, and informative videos; catch up on videos from past Apple events and download them to watch offline. There’s also an in-app purchase to sign up for the Apple Developer Program.