Enter our new international giveaway for a chance to win the brand new iPhone 16 Pro.
Apple Premieres ‘The Banker’ at National Civil Rights Museum
Apple premiered its film The Banker at the National Civil Rights Museum, opening in select theaters March 6 and Apple TV+ on March 20.
YouTube Doesn’t Recommend as Many Conspiracy Videos Anymore
YouTube is working to cut the number of conspiracy video it recommends to users, but that number is slowly increasing again.
Researchers trained an algorithm to judge the likelihood that a video on the site contained conspiracy theories by looking at the description, transcript, and comments. They examined eight million recommendations over 15 months. They found that shortly after YouTube announced it would recommend less conspiracy content in January 2019, the numbers did indeed gradually drop—by about 70% at the lowest point in May 2019. However, the number of conspiracy videos YouTube’s algorithm recommends has steadily risen again since then. These recommendations are now only 40% less common than when YouTube started its crackdown.
'Mythic Quest: Raven’s Banquet' Stars Reveal Their Favorite Games
Apple TV+ series Mythic Quest: Raven’s Banquet tells the story of the team behind a hugely popular multiplayer game. In a video posted Monday, the series’ stars revealed their favorite games. Choices ranged from Pac Man to Skyrim, from Tony Hawks to The Sims.
PCMag Lead Mobile Analyst Sascha Segan - TMO Background Mode Interview
Sascha Segan is PCMag.com’s Lead Mobile Analyst. He has reviewed more than 1,100 smartphones, tablets and other gadgets in more than 15 years with PCMag. Sascha is also a multiple award-winning travel writer.
We chatted about how he got started in computing, and it was a familiar story. “…published the high school newspaper, literary magazine and foreign language magazine on an SE/30.” Along the way, Sascha discovered that he loved helping people and showing them how tech works. We talked about the future of foldable smartphones, how the butterfly MBP keyboard drove him to Windows, a (presumed) Apple iPhone/iPad event on March 31, and what’s in store for the 5G iPhone 12. Sascha understands 5G and phones deeply, and so this was a very informative show.
Trash Can Mac Pro 3.7GHz Quad Core Xeon (Certified Refurbished): $1,599
We have a deal on an Apple Mac Pro 3.7GHz Quad Core Xeon 16GB RAM 512GB SSD – Black (Certified Refurbished). This is the so-called Trash Can Mac Pro designed to look great on your desk. It’s $1,599 through our deal.
Notes and Evernote – TMO Daily Observations 2020-03-02
Bob “Dr Mac” LeVitus chats with host Kelly Guimont about Apple’s Notes app, how it has evolved, and if it’s an alternative to Evernote.
Apple TV+ Exec Michelle Mendelovitz Leaves for 20th Century Fox
Michelle Mendelovitz, Apple’s creative executive involved with Apple TV+, has left the company in favor of 20th Century Fox.
Apple Launches ‘She Creates’ Sessions in its Stores
As noted last week, Apple is launching Today at Apple sessions called “She Creates” to celebrate International Women’s Day 2020.
The Macintosh II Was Launched Today in 1987
Another great ‘Today in Apple History’ from Cult of Mac today. On this day in 1987, the legendary Macintosh II was launched.
Although four Mac models already have been released, the definitive, full-number name of the Macintosh II makes clear that this is a major upgrade for the product line. With a massive hardware boost, optional color display (!) and a new open architecture, it does not disappoint! By far the biggest change with the Mac II? Its open architecture, which allows users to expand the computer. More than just a tech upgrade, this marked a fundamental shift in the way Apple engineers thought about the Macintosh.
Apple Will Pay up to $500 Million to Settle Slow iPhone Class Action
Apple is set to pay up to $500 million to settle a U.S class action related to iPhone slowing allegations, Reuters reported. Claimants said that Apple slowed down devices to encourage users to upgrade to newer ones.
The preliminary proposed class-action settlement was disclosed on Friday night and requires approval by U.S. District Judge Edward Davila in San Jose, California. It calls for Apple to pay consumers $25 per iPhone, which may be adjusted up or down depending on how many iPhones are eligible, with a minimum total payout of $310 million. Apple denied wrongdoing and settled the nationwide case to avoid the burdens and costs of litigation, court papers show.
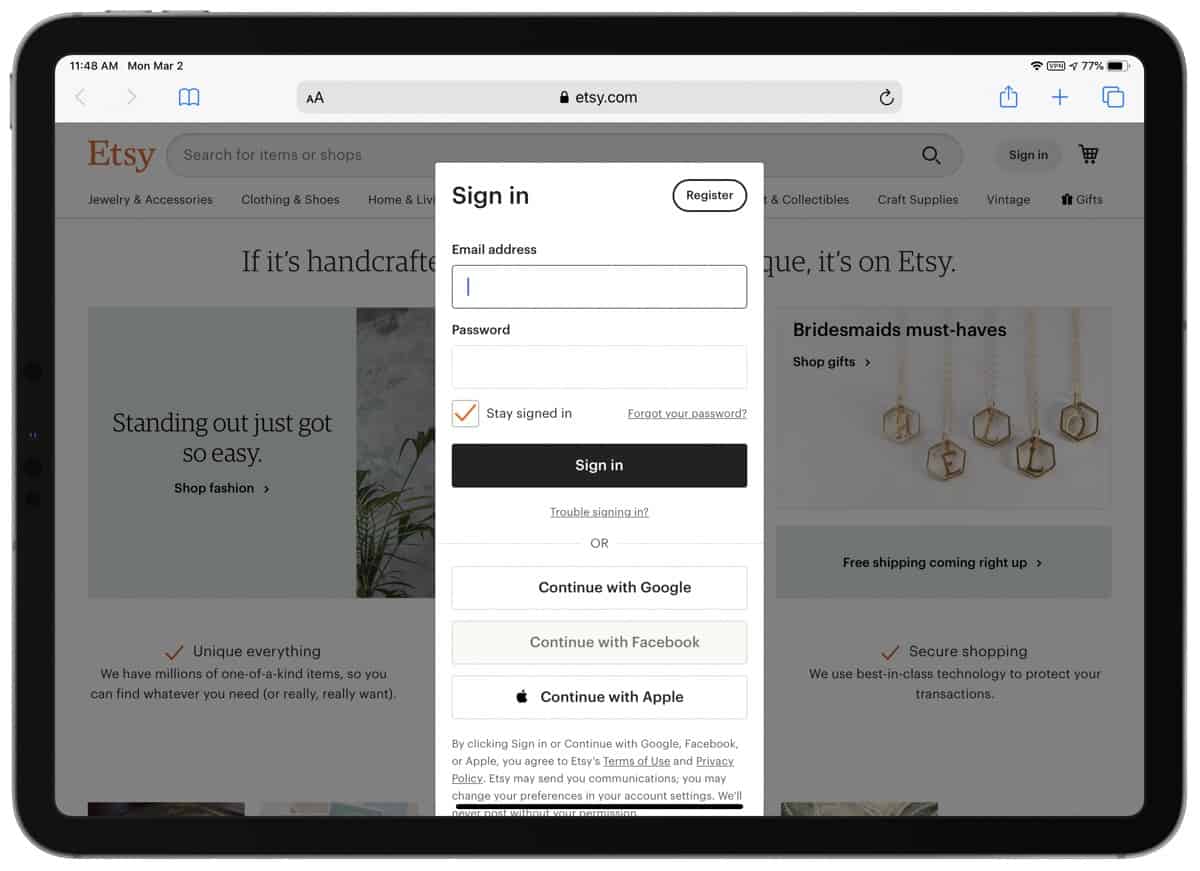
Etsy Gets Updated to Support Sign In with Apple
Etsy didn’t mention it in the app update notes but you can now sign up for an account using Sign In with Apple. So far it looks like this only applies to new accounts, and you won’t be able to convert the account you already have. Reddit maintains a list of all the known apps to support Sign In with Apple.
New Report Outlines Allegations of Abuse Against Uyghur Muslims Working in Apple Supply Chain
Apple Is one of the firms criticised in a damning new report looking at the mistreatment of Uyghur Muslim workers.
How to Steal and Repurpose Mac Malware
A former NSA hacker argued that stealing and then repurposing Mac malware can be more powerful than creating it from scratch. Patrick Wardle demonstrated one example of how he went about it at RSA Conference, ArsTechnica reported.
Patrick Wardle, who is now a security researcher at the macOS and iOS enterprise management firm Jamf, showed how reusing old Mac malware can be a smarter and less resource-intensive approach for deploying ransomware, remote access spy tools, and other types of malicious code. Where the approach really pays dividends, he said, is with the repurposing of advanced code written by government-sponsored hackers. “There are incredibly well-funded, well-resourced, very motivated hacker groups in three-letter agencies that are creating amazing malware that’s fully featured and also fully tested,” Wardle said during a talk titled “Repurposed Malware: A Dark Side of Recycling.” “The idea is: why not let these groups in these agencies create malware and if you’re a hacker just repurpose it for your own mission?” he said.
Apple Sees iPhone Market Share Fall in Latin America in 2019
Apple’s market share in the increasingly important Latin American (LATAM) market dropped in 2019, according to new analysis.
What's Different About Mexican Power? – Mac Geek Gab 804
Dave’s back from Mexico where the power is definitely the same. Yep, certianly. Or is it? He and John talk that through. Mostly, though, the show focuses on you: your questions, your tips, your thoughts, and your answers! Learn how to “right-size” Finder columns, use the keyboard to navigate System Preferences, re-enable your Mac’s startup chime, manage Photos backups, boot a new Mac from an old one, and more! Press play to learn at least five new things!
Laurene Powell Jobs Talks Philanthropy, Dreamers, and Steve
Laurene Powell Jobs gave a revealing interview to The New York Times in which she discussed a number of issues, including her late husband, Steve Jobs.
A Better Way to Type on an iPhone?
Dr. Mac is fascinated by Typewise, the first keyboard app designed from the ground up for the iPhone (or other smart phone) and its claim that it can reduce typos up to 80%.
Apple Notes May Be Better Than Ever(note)
Dr. Mac’s been playing with Apple Notes lately and he thinks it might finally be mature enough to replace Evernote Premium in his workflow (which will save him $70 next year).
How Apple Might Introduce ARM CPUs in Future Macs
There is a renewed indicator that Apple will use its own ARM CPU in future Macs.
But there may be a catch.
Programmers Create Every Possible Melody to Stop Lawsuits
Two programmers have created every possible melody in MIDI to help creators stifled by lawsuits.
Two programmer-musicians wrote every possible MIDI melody in existence to a hard drive, copyrighted the whole thing, and then released it all to the public in an attempt to stop musicians from getting sued.
Often in copyright cases for song melodies, if the artist being sued for infringement could have possibly had access to the music they’re accused of copying—even if it was something they listened to once—they can be accused of “subconsciously” infringing on the original content.
Sounds like a clever attempt to hack the system. I’m not sure if that will actually hold up in court but it’s creative.
RIOT HiFi Over-Ear Headphones: $59.99
We have a deal on a pair of RIOT HiFi Over-Ear Headphones. RIOT connects to your portable devices via Bluetooth, or with a headphone jack using a mini-plug wired connection. they also come with a carrying case, and they’re priced at $59.99 through our deal.
Apple Blocks Clearview AI iPhone App
Apple has blocked Clearview AI’s iPhone app, saying it violated the terms of its enterprise program because the app wasn’t for internal use.
Major Tech Events Being Canceled Due to Coronavirus
A number of major technology firms, including Microsoft and Facebook, are canceling events and conference appearances due to coronavirus.
Use Sign in With Apple to Access Your WordPress.com Account
You can easily login to your WordPress.com account using Sign in With Apple, making access simpler and a bit more secure.