Enter our new international giveaway for a chance to win the brand new iPhone 16 Pro.
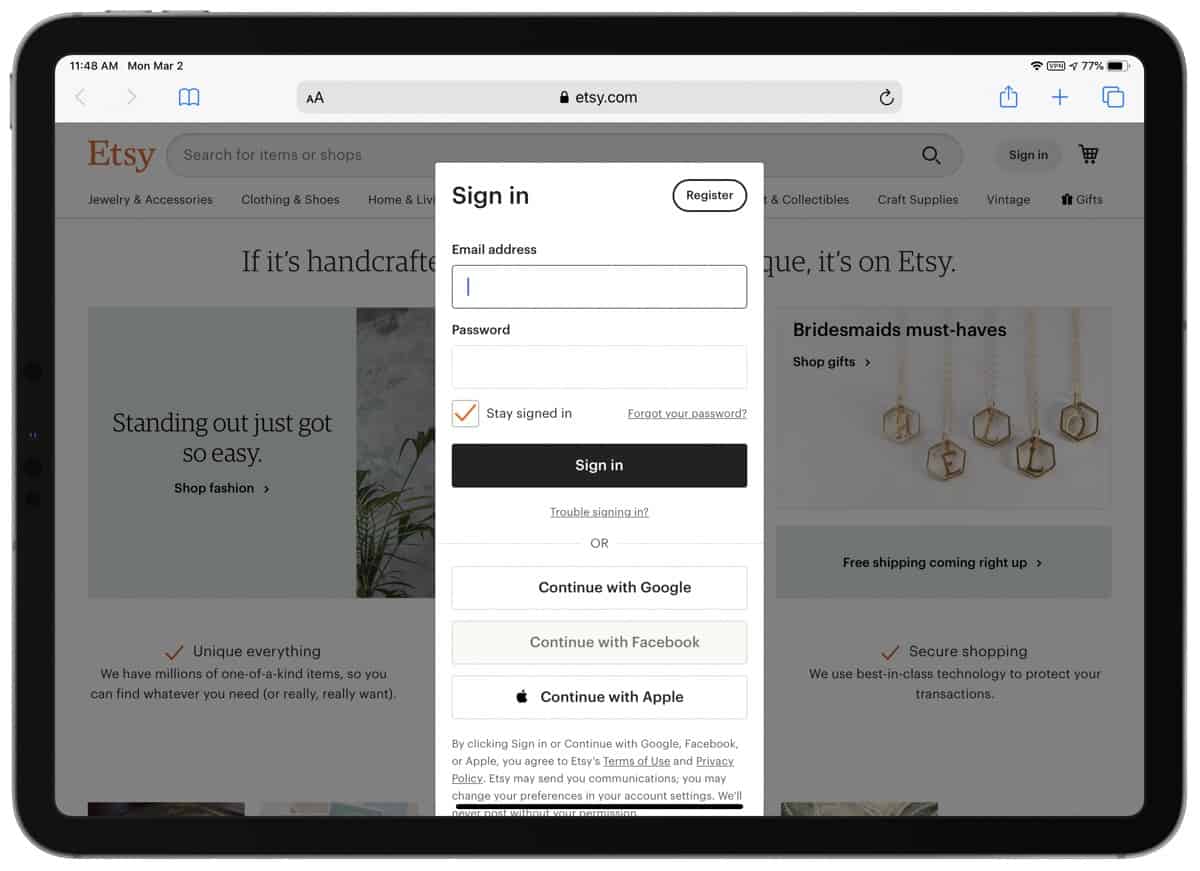
Etsy Gets Updated to Support Sign In with Apple
Etsy didn’t mention it in the app update notes but you can now sign up for an account using Sign In with Apple. So far it looks like this only applies to new accounts, and you won’t be able to convert the account you already have. Reddit maintains a list of all the known apps to support Sign In with Apple.
New Report Outlines Allegations of Abuse Against Uyghur Muslims Working in Apple Supply Chain
Apple Is one of the firms criticised in a damning new report looking at the mistreatment of Uyghur Muslim workers.
How to Steal and Repurpose Mac Malware
A former NSA hacker argued that stealing and then repurposing Mac malware can be more powerful than creating it from scratch. Patrick Wardle demonstrated one example of how he went about it at RSA Conference, ArsTechnica reported.
Patrick Wardle, who is now a security researcher at the macOS and iOS enterprise management firm Jamf, showed how reusing old Mac malware can be a smarter and less resource-intensive approach for deploying ransomware, remote access spy tools, and other types of malicious code. Where the approach really pays dividends, he said, is with the repurposing of advanced code written by government-sponsored hackers. “There are incredibly well-funded, well-resourced, very motivated hacker groups in three-letter agencies that are creating amazing malware that’s fully featured and also fully tested,” Wardle said during a talk titled “Repurposed Malware: A Dark Side of Recycling.” “The idea is: why not let these groups in these agencies create malware and if you’re a hacker just repurpose it for your own mission?” he said.
Apple Sees iPhone Market Share Fall in Latin America in 2019
Apple’s market share in the increasingly important Latin American (LATAM) market dropped in 2019, according to new analysis.
What's Different About Mexican Power? – Mac Geek Gab 804
Dave’s back from Mexico where the power is definitely the same. Yep, certianly. Or is it? He and John talk that through. Mostly, though, the show focuses on you: your questions, your tips, your thoughts, and your answers! Learn how to “right-size” Finder columns, use the keyboard to navigate System Preferences, re-enable your Mac’s startup chime, manage Photos backups, boot a new Mac from an old one, and more! Press play to learn at least five new things!
Laurene Powell Jobs Talks Philanthropy, Dreamers, and Steve
Laurene Powell Jobs gave a revealing interview to The New York Times in which she discussed a number of issues, including her late husband, Steve Jobs.
A Better Way to Type on an iPhone?
Dr. Mac is fascinated by Typewise, the first keyboard app designed from the ground up for the iPhone (or other smart phone) and its claim that it can reduce typos up to 80%.
Apple Notes May Be Better Than Ever(note)
Dr. Mac’s been playing with Apple Notes lately and he thinks it might finally be mature enough to replace Evernote Premium in his workflow (which will save him $70 next year).
How Apple Might Introduce ARM CPUs in Future Macs
There is a renewed indicator that Apple will use its own ARM CPU in future Macs.
But there may be a catch.
Programmers Create Every Possible Melody to Stop Lawsuits
Two programmers have created every possible melody in MIDI to help creators stifled by lawsuits.
Two programmer-musicians wrote every possible MIDI melody in existence to a hard drive, copyrighted the whole thing, and then released it all to the public in an attempt to stop musicians from getting sued.
Often in copyright cases for song melodies, if the artist being sued for infringement could have possibly had access to the music they’re accused of copying—even if it was something they listened to once—they can be accused of “subconsciously” infringing on the original content.
Sounds like a clever attempt to hack the system. I’m not sure if that will actually hold up in court but it’s creative.
RIOT HiFi Over-Ear Headphones: $59.99
We have a deal on a pair of RIOT HiFi Over-Ear Headphones. RIOT connects to your portable devices via Bluetooth, or with a headphone jack using a mini-plug wired connection. they also come with a carrying case, and they’re priced at $59.99 through our deal.
Apple Blocks Clearview AI iPhone App
Apple has blocked Clearview AI’s iPhone app, saying it violated the terms of its enterprise program because the app wasn’t for internal use.
Major Tech Events Being Canceled Due to Coronavirus
A number of major technology firms, including Microsoft and Facebook, are canceling events and conference appearances due to coronavirus.
Use Sign in With Apple to Access Your WordPress.com Account
You can easily login to your WordPress.com account using Sign in With Apple, making access simpler and a bit more secure.
Tim Cook: Apple ‘Fundamentally Strong’ in Wake of Coronavirus
In an interview with Fox Business Network, Tim Cook said that Apple is “fundamentally strong” in the face of COVID-19.
WeWork Series Coming to Apple TV+
An Apple TV+ series on the rise and fall of WeWork, based on the WeCrashed podcast from Wondery, is in development.
iPads, Trackpads, China, and Censorship – TMO Daily Observations 2020-02-28
This week we saw rumors of Apple releasing an iPad keyboard with a trackpad, and news that Apple will be requiring paid game developers to comply with Chinese censorship laws. Charlotte Henry and Bryan Chaffin join Dave Hamilton to sift through it all for you before the weekend. Press play and enjoy!
Stars of Apple TV+'s 'Visible - Out on Television' Ask: How Much Longer?
In the latest Apple TV+ clip, some of the stars featured in the series Visible – Out On Television, share moments when they nearly gave up. The likes of Ellen DeGeneres, Laverne Cox, and Adam Lambert all appear in the series and explain the difficult times they went through. The series is available now with an Apple TV+ subscription.
First Apple Store to Launch in India in 2021, Online Store Will Launch This Year
CUPERTINO – Apple CEO Tim Cook announced his company would open its first physical Apple Store in India in 2021, and that the company would launch its own online store later in 2020.
How to Create a Honeypot URL With URL Canary
A service I recently discovered is URL Canary. It creates a honeypot URL that you can then put in a location such as your cloud storage. It alerts you if that URL has been accessed.
URL Canary will catch automated robots and crawlers, as well as manual human attackers. The only time it won’t catch an attacker is if they don’t see the canary, or they don’t find it sufficiently-compelling and opt not to visit it. Since you have control of the URL and the domain name, you can make your canaries as compelling as possible for your specific use case.
There’s a similar service I know of called CanaryTokens.
Carriers Could be Fined $200M For Selling Location Data
The FCC is preparing to fine four major cellular carriers roughly US$200 million for selling location data of customers.
MI5 Chief Wants ‘Exceptional Access’ to Encrypted Messages
Sir Andrew Parker is the head of MI5, the UK’s domestic security service. He wants tech firms to provide “exceptional access” to encrypted messages.
In an ITV interview to be broadcast on Thursday, Sir Andrew Parker says he has found it “increasingly mystifying” that intelligence agencies like his are not able to easily read secret messages of terror suspects they are monitoring.
Bah, this is smoke and mirrors. As the head of a security agency he knows that restricting backdoors to the good guys is impossible.
Tim Cook Thinks China is Getting Coronavirus 'Under Control'
Tim Cook appears to be more optimistic than most about China’s response to the coronavirus outbreak. In an interview with Fox Business, the Apple CEO said he felt China was getting the illness “under control.”
Apple CEO Tim Cook told FOX Business’ Susan Li Thursday that he is “optimistic” about China managing the coronavirus outbreak, which has slowed production at the tech giant’s suppliers. “It feels to me that China is getting the coronavirus under control,” Cook said. “You look at the numbers, they’re coming down day by day by day. And so I’m very optimistic there.” He stressed that iPhone gets parts from “everywhere in the world,” including China, which has seen 2,744 deaths among 78,497 cases, mostly in the central province of Hubei.
What Impact Does Watching Netflix Have Climate Change?
Despite what mainstream media wants you to think, the outcome is mostly still unclear when it comes to Netflix binging.
On one hand, the paper reports, strides in data center efficiency have mostly kept pace with growing demand for data, meaning that in the last decade the total amount of energy consumed by the centers has not changed much—around 1% of global energy use. That’s about the same as 18 million US homes.
On the other hand, it’s clear that we’re approaching a limit to squeezing out more efficiency—especially given the rise of data-ravenous artificial intelligence.
What I find annoying about the debates around climate change is how a lot of mainstream media are trying to blame people. Like blaming their Netflix binging instead of reporting the facts like 100 corporations are responsible for 71% of emissions. Sure, Netflix wouldn’t exist without its users, but I think it’s important to focus on how much more damage a corporation does than an individual.