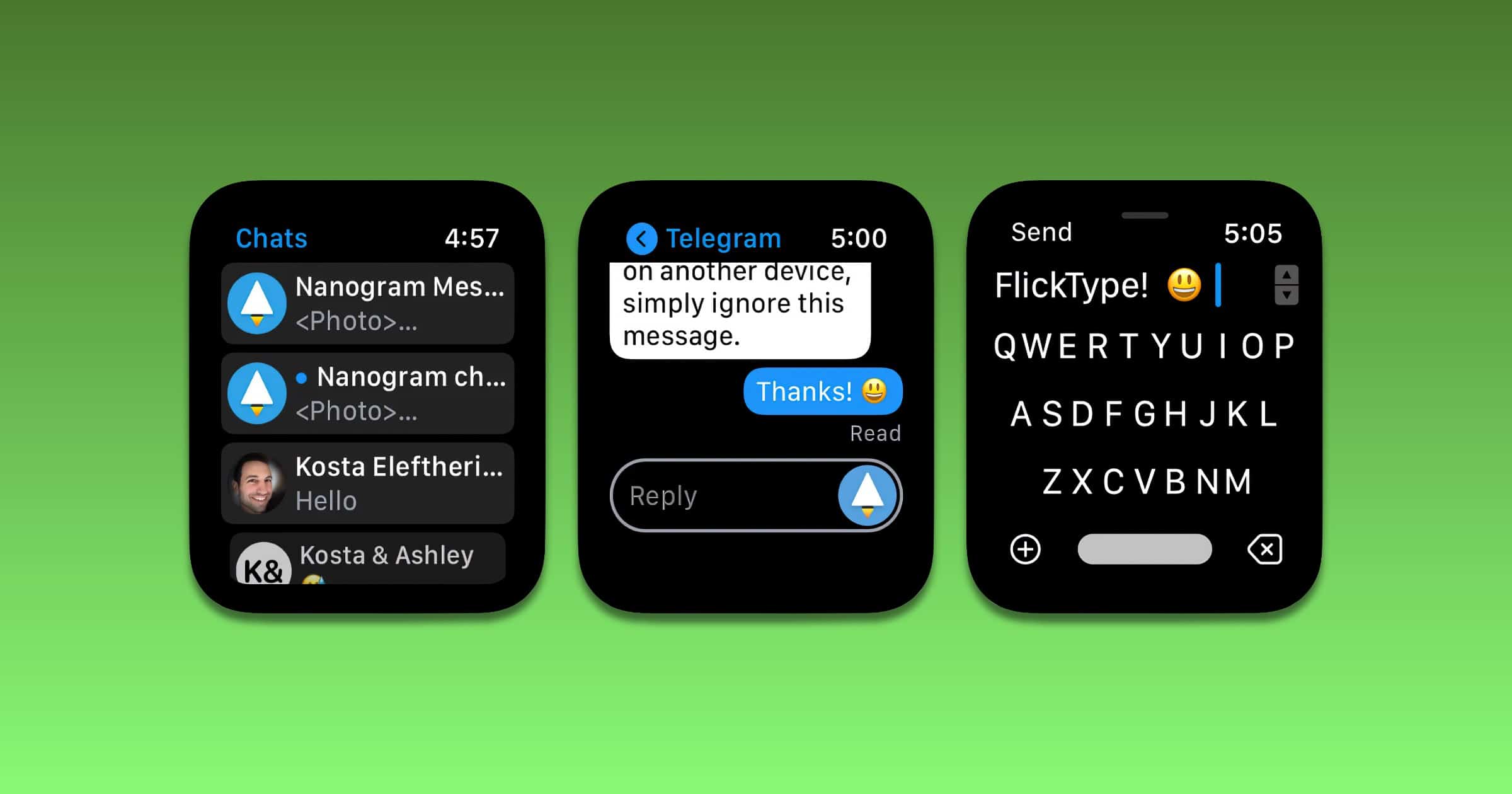
Nanogram is a brand new Apple Watch app that acts as a Telegram client. Features: Send, receive, and see all your messages & notifications right from your wrist – even when you don’t have your phone around. Experience the freedom of going truly phone-less with just your Apple Watch, while staying connected to your friends & family. Also supports FlickType Swipe Keyboard, for faster & more private replies on the go (vs Scribble & Dictation, respectively). Nanogram does not collect any information. Requires Apple Watch Series 3 or later, running watchOS 7 or later.
Articles by Andrew Orr
Verizon Adds Four New Mobile Hotspot Plans for Customers
Verizon announced on Thursday the addition of four new mobile hotspot plans, perfect for travelers. From 15GB to 150GB per month.
eBay Adds Support for Apple Pay on its Website
eBay has added support for Apple Pay on its website recently. Previously the payment option was only available in its apps.
iOS 15 Public Beta 4 Released for Apple Users
A few days after seeding public beta 4 for developers running iOS 15 | iPadOS 15, public beta testers can now install the release.
Mozilla VPN Expands to Seven More Countries, Increases Price
Mozilla has added seven additional countries to its VPN service, and raises the price for new users.
Mozilla’s virtual private network (VPN) service has arrived in seven more countries, including Austria, Belgium, France, Germany, Italy, Spain and Switzerland.
It will honor the $4.99 a month price for customers from the US, Canada, UK, Singapore, Malaysia, and New Zealand, who signed up already. But from now on that price will only be available for customers who sign up for a year. Otherwise the fee rises to $7.99 a month for a six month deal or $9.99 for a month of access.
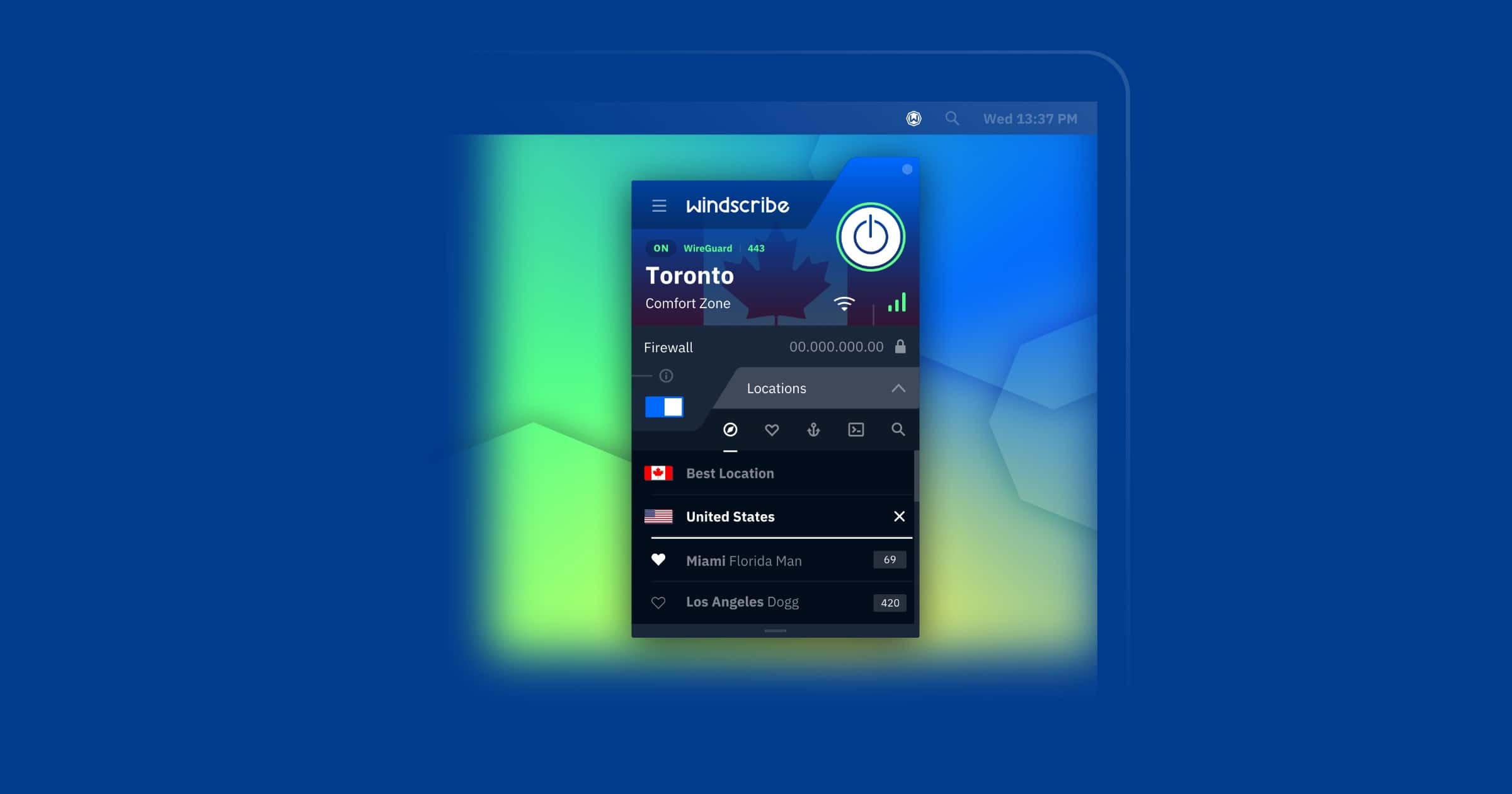
Ukraine Authorities Seize Unencrypted Windscribe VPN Servers
VPN provider Windscribe said its servers were not encrypted, enabling authorities to create decoy servers and snoop on web traffic.
The Ontario, Canada-based company said earlier this month that two servers hosted in Ukraine were seized as part of an investigation into activity that had occurred a year earlier. The servers, which ran the OpenVPN virtual private network software, were also configured to use a setting that was deprecated in 2018 after security research revealed vulnerabilities that could allow adversaries to decrypt data.
Oh come on, VPN servers that weren’t encrypted?
Totallee Offers Impressive 50% Off Sale for All Smartphone Cases
Starting today and valid until August 8 you can use a special promo code to get 50% off any product with totallee.
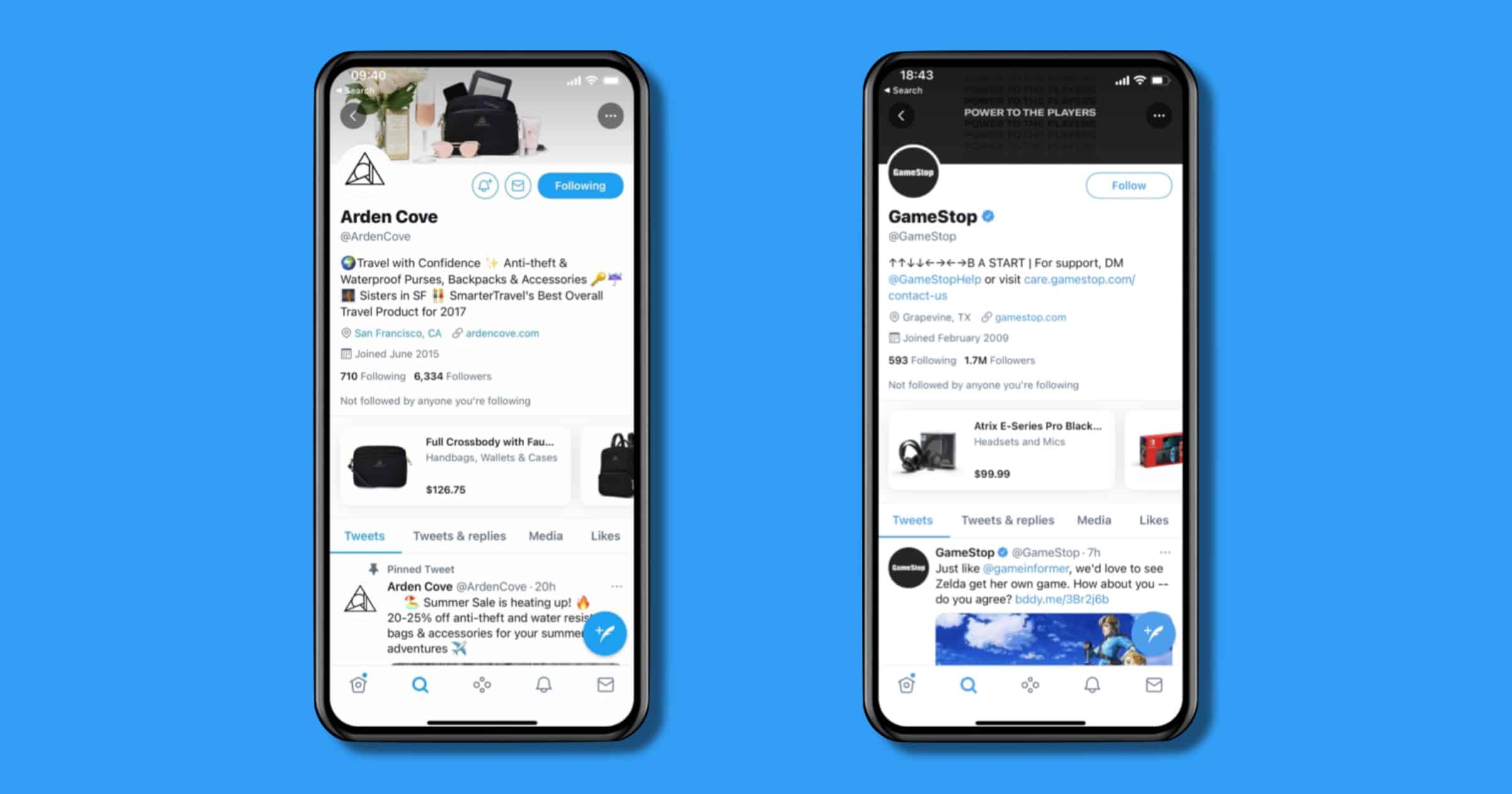
Twitter Tests New ‘Shop Module’ Feature for iOS Users
Twitter is piloting a new feature on Wednesday called Shop Module. It will let brands add a shopping section at the top of their profiles. The pilot is currently limited to iOS devices for people who use the service in English.
The Shop Module is a dedicated space at the top of a profile where businesses can showcase their products. When people visit a profile with the Shop Module enabled, they can scroll through the carousel of products and tap through on a single product to learn more and purchase — seamlessly in an in-app browser, without having to leave Twitter.
Apple Threatens iPhone Prototype Seller With Police Involvement
Apple has sent a cease-and-desist letter to a Chinese citizen who advertised stolen iPhone prototypes on social media.
Apple to Limit Siri Interactions With Third-Party Apps in iOS 15
According to a support article for developers, Apple is deprecating some SiriKit intents and commands for third-party apps.
Former eBay Security Chief Sentenced to 18 Months in Prison Over Cyber-Stalking
Philip Cooke is the last of seven former eBay employees to be charged for involvement in a harassment campaign against two bloggers.
Hackers Increasingly Using Discord to Spread Malware
Researchers found that hackers are turning to Discord to spread malware, such as password-hijacking and Discord chat bot APIs.
But the greatest percentage of the malware we found have a focus on credential and personal information theft, a wide variety of stealer malware as well as more versatile RATs. The threat actors behind these operations employed social engineering to spread credential-stealing malware, then use the victims’ harvested Discord credentials to target additional Discord users.
Oil Producer ‘Wesco’ Uses Excess Natural Gas to Mine Bitcoin
Utah-based oil company Wesco Operating Co. is using excess gas (natural, not Ethereum) to power a Bitcoin mining operation.
Rather than being “flared,” or burned, to eliminate it, the natural gas is burned to run electrical generators, which in turn power two mobile data centers that process Bitcoin transactions, Wesco representative Steve Degenfelder explained.
The company has connected with a Chicago-based firm, EZ Blockchain, to acquire the two Bitcoin “miners,” portable data processors tied to the Internet.
macOS: Here’s How to Reset an M1 Mac SMC
The System Management Controller manages many low-level functions on your Mac. Here’s how to reset an M1 Mac SMC for troubleshooting.
Apple News Offers Exclusive 2020 Olympics Content With NBCUniversal
Apple is partnering with NBCUniversal to offer exclusive Olympics content in Apple News with daily recaps, audio briefings, event schedules, and more.
Samsung Reveals Mini-LED Ultrawide Gaming Monitor Dubbed ‘Odyssey Neo G9’
Samsung has unveiled what it says is the world’s first Mini-LED gaming monitor. It’s a curved, ultrawide display available for preorder on July 29.
‘Unseen Empire’ is a Game Based on a Real-Life Wildlife Study
Based on the biggest wildlife camera trap study ever, Unseen Empire takes you through the research process.
In playing the game, users can re-enact the research process as they place camera traps across eight countries and collected and identify hundreds of never-before-seen photos of rare animal species.
Apple Releases Updates for Macs, iPhones, and iPads
Apple has released updates on Monday with macOS 11.5.1 and iPhone 14.7.1 with bug fixes and security updates.
Apple Museum in Poland Will House World’s Biggest Collection of Products
This fall a museum dedicated to Apple products will open in Poland in the Norblin Factory complex with 1,500 exhibits.
Phil Schiller Talks Tech Innovation in New Interview
In an interview with Automobili Lamborghini, Apple Fellow Phil Schiller talks about technology, innovation, and cars in a recent interview.
Amazon Posts Job Listing for ‘Digital Currency and Blockchain’
On Thursday Amazon published a job listing for a Digital Currency and Blockchain Product Lead with the Payments Acceptance & Experience team.
Apple Device Owners Can Play Facebook Games in a Web App
Facebook is bringing its cloud gaming services to Apple devices via a web app that can be added to the Home Screen
New Bill Would Remove Section 230 Protections for Social Media
Introduced on Thursday, a bill called the Health Misinformation Act would hold social media companies responsible for spreading health misinformation.
Researchers Hid Malware Inside an AI’s Brain
This is straight out of a sci-fi novel. Researchers created a proof-of-concept technique that let them hide malware inside of an AI’s neurons to avoid detection.
According to the paper, in this approach the malware is “disassembled” when embedded into the network’s neurons, and assembled into functioning malware by a malicious receiver program that can also be used to download the poisoned model via an update. The malware can still be stopped if the target device verifies the model before launching it, according to the paper. It can also be detected using “traditional methods” like static and dynamic analysis.