Mosyle has officially announced the latest update to its software for Mac admins. It adds a screen sharing tool for the MDM market.
Articles by Andrew Orr
iPadOS 15: How to Create a Quick Note for Apple Notes
One of the new features coming to Apple Notes in iPadOS 15 is the ability to create a “quick note.” Here’s how to create one.
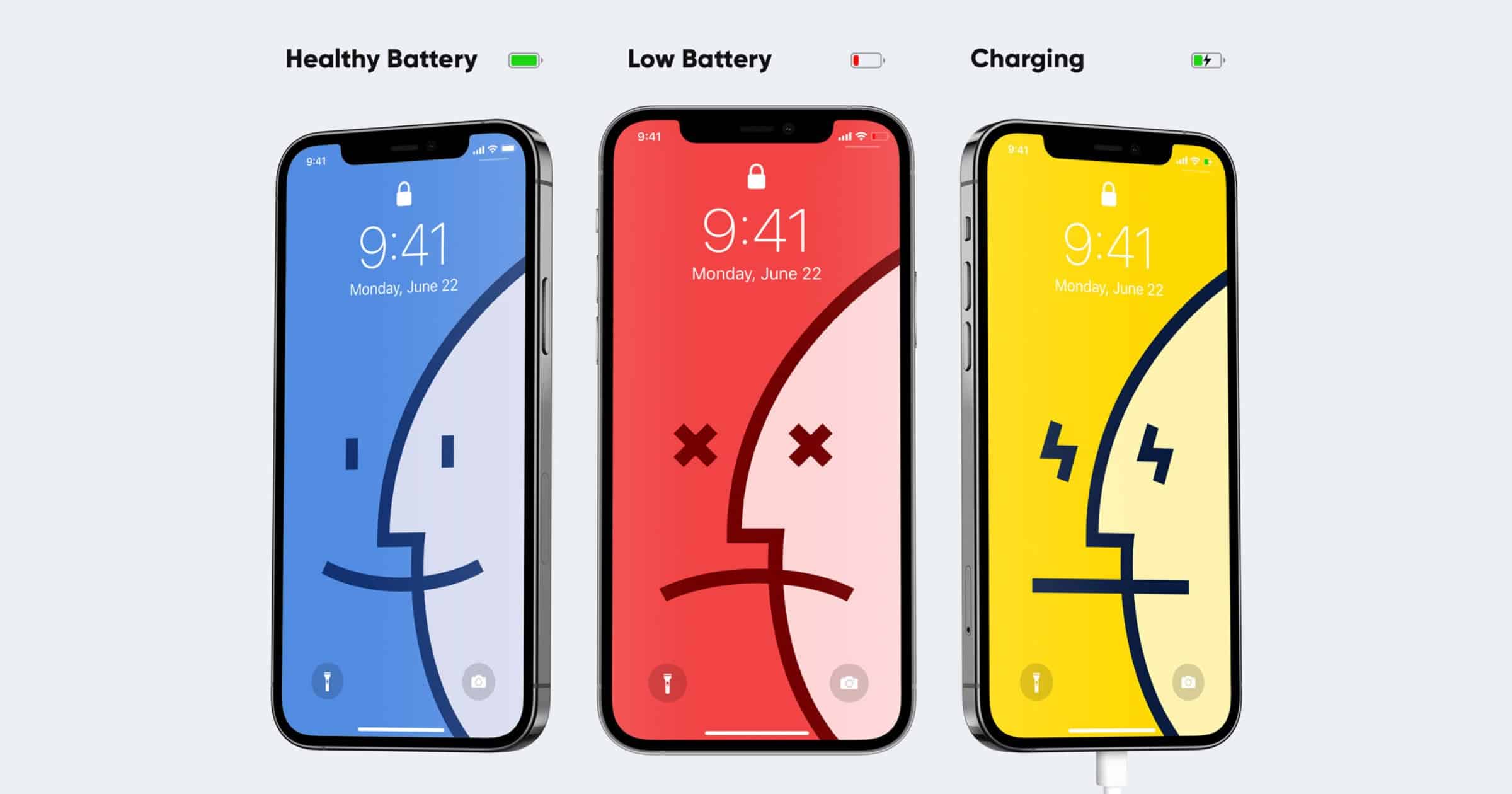
Check Out These New iPhone Battery Wallpapers
Ben Vessey has released some new iPhone battery wallpapers as part of the Dynamo series. These wallpapers use shortcuts automation to automatically change depending on the state of your battery: Full, Low, and Charging. There are two new packs available: an album pack for music fans based on popular music icons; and a Mac-themed pack inspired by the Apple Macintosh. Each pack includes three sets of wallpapers optimized for the iPhone 6s and later. You install them using iCloud and Shortcuts running on iOS 14, with instructions included in the download.
New Ransomware ‘Tsunami’ Destroying Supply Chains
The REvil hacking team is back with new malware. Brand new, still developing, but their ransomware called “Tsunami” is wreaking havoc.
The software in question, Kaseya VSA, is popular among so-called managed service providers, which provide IT infrastructure for companies that would rather outsource that sort of thing than run it themselves. Which means that if you successfully hack an MSP, you suddenly have access to its customers. It’s the difference between cracking safety deposit boxes one at a time and stealing the bank manager’s skeleton key.
iOS 15: A First Look at Automating With Shortcuts
Shortcuts is getting some new features with iOS 15 as well as appearing on macOS Monterey this fall. Here are some of the new changes.
Europe Chief Tells Apple Not to Use Privacy to Limit Competition
Margrethe Vestager, the European Commission’s VP for technology, says that Apple shouldn’t use privacy and security to limit competitors.
Brydge 11 MAX+ Supports iPad Pro, iPad Air
After releasing the 12.9-inch MAX+ keyboard case Brydge is following up with the 11-inch MAX+ for iPad Pro and iPad Air.
Russian Spies Abuse VPNs to Target Organizations
On Thursday, U.S. and British authorities said that Russia’s military spy agency is using VPNs and Tor to attack governments and private sector targets.
The advisory did not identify any of the targets by name, saying only that they were mainly in the United States and Europe and included government offices, political parties, energy companies, law firms and media organizations.
The Russian Embassy in Washington did not immediately return a message seeking comment. Russian officials routinely reject allegations that they employ hackers to spy on rival nations.
This Man Wants to Decipher the Languages of Animals
Aza Raskin was the person who invented the “infinite scroll” feature we see often on social media. Now he wants to use machine learning to decipher animal language.
A library of all the different animal communication data sets that were machine learning ready. Everyone was working in their own silos, and we saw an opportunity to create a kind of perspective-changing machine: to look at the difference between humpback communication and elephant communication and sperm whale communication and bat communication.
Apple Seeds macOS Monterey Public Beta 1
Apple has released macOS Monterrey public beta 1 on Thursday, a day after seeding betas for iOS 15 | iPadOS 15 and watchOS 8.
New Russian Law Requires Some Companies to Have Offices in Country
Russian President Vladimir Putin signed a law that requires foreign social media companies to open offices in the country.
Israeli Wallet Company Says Apple Pay Is Killing Physical Wallet Industry
Israeli wallet brand Emmanuel Wallets is boycotting digital wallets like Apple Pay, saying it’s harming the physical wallet industry.
Classic wallets have accompanied the human race for centuries and serve as a practical means of maintaining a means of payment and a fashionable accessory. A wallet is the type of item one holds, such as a phone… so it’s part of its unique style and personal branding. No technological gimmick, not even one promoted by the world’s largest tech company, will succeed in reducing the popularity of a physical wallet.
“No digital wallet will succeed in reducing the popularity of a physical wallet.” Well then, what’s all the fuss about?
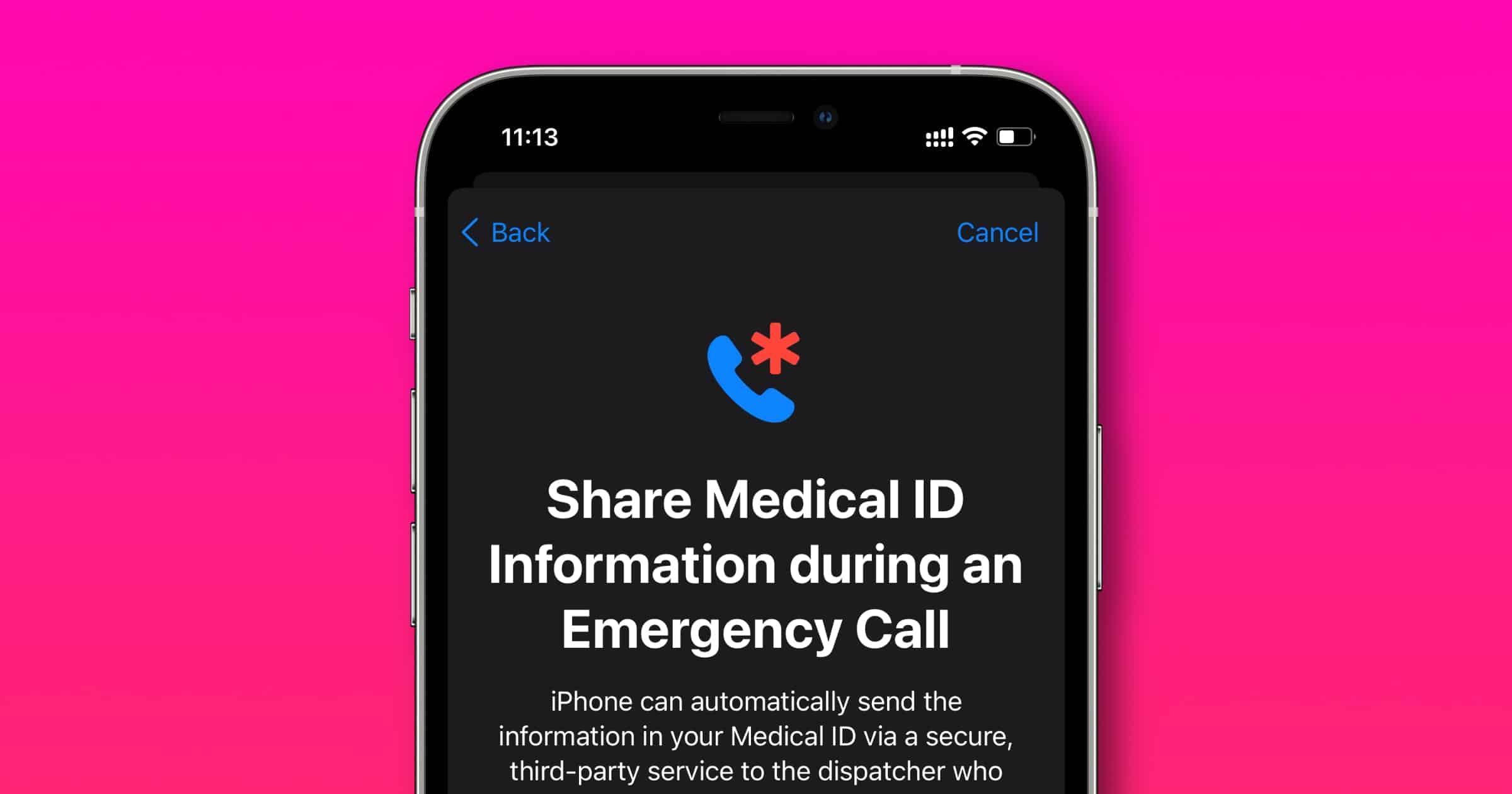
iOS 15: How to Share Your Medical ID During an Emergency Call
iOS 15 brings a new feature in the Health app that lets you automatically share your medical ID during an emergency call.
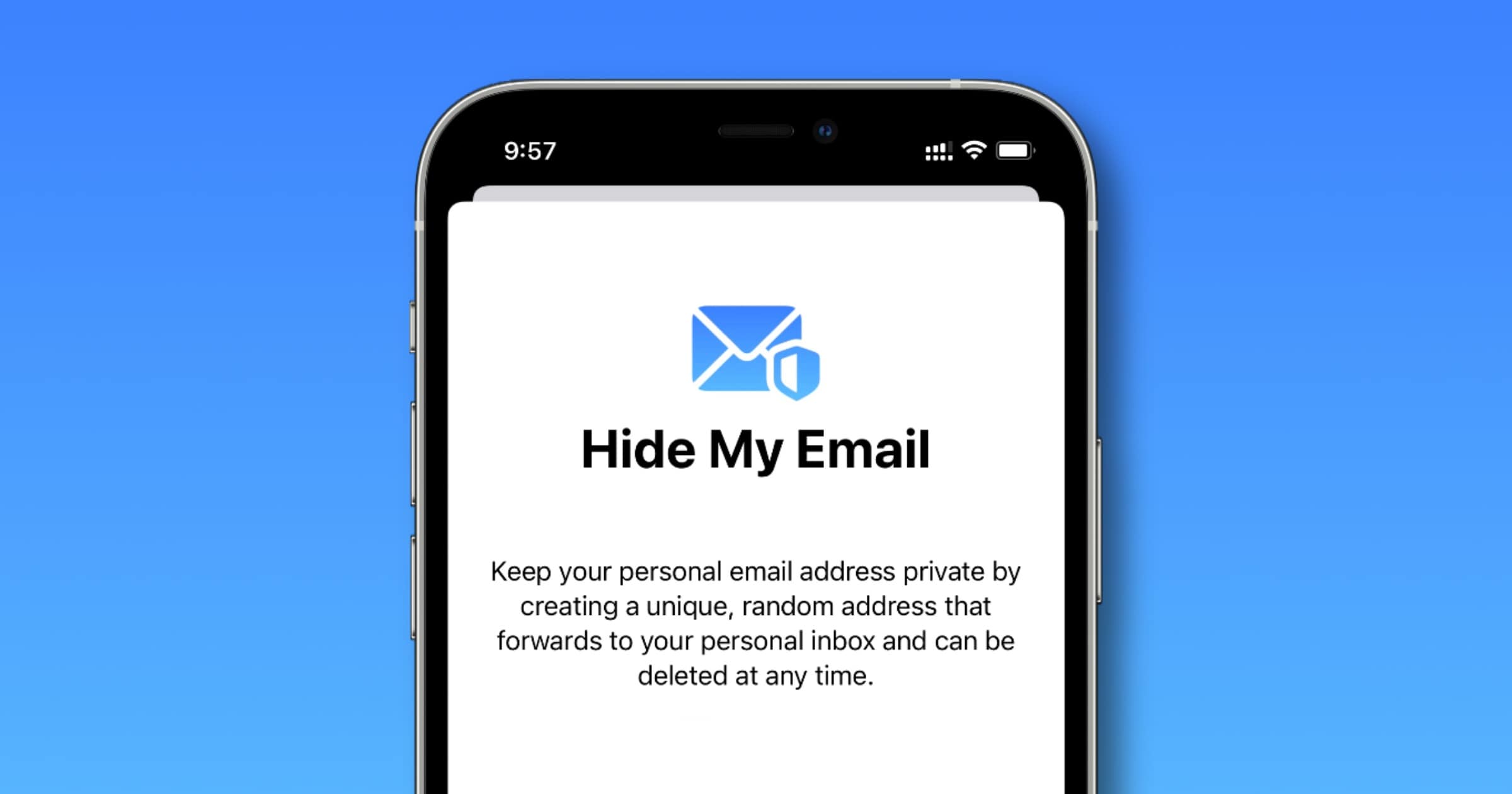
iOS 15: How to Generate Email Aliases With ‘Hide My Email’
One of the privacy features coming with iOS 15 is called Hide My Email. It‘s part of iCloud+ and lets you use random email aliases.
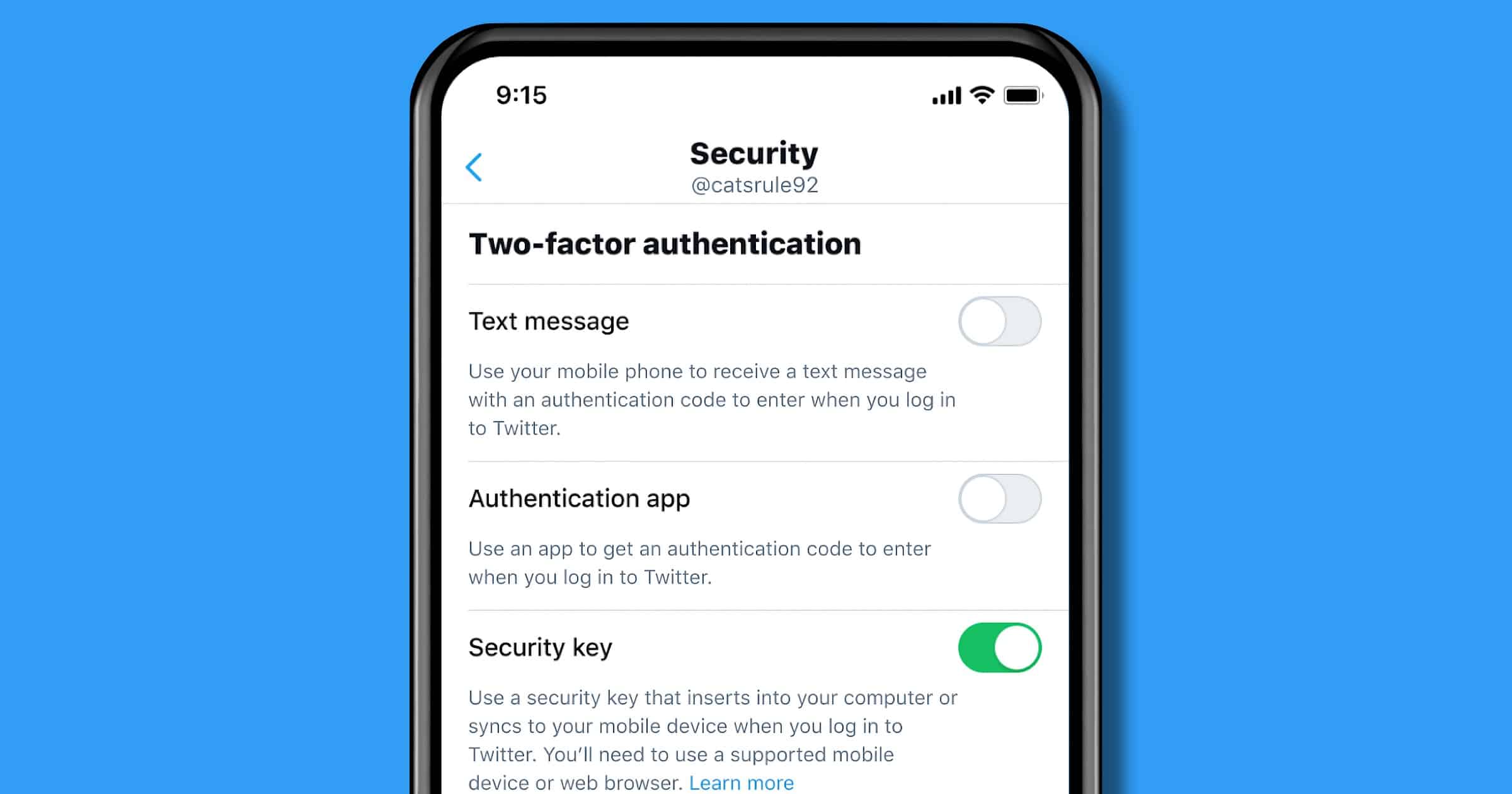
Twitter Lets You Use a Security Key as Only 2FA Option
Twitter announced on Wednesday that it will let people use a security key as their only form of two-factor authentication.
Today, we’re adding the option to use security keys as your sole 2FA method — meaning you can enroll one or more security keys as the only form of 2FA on your Twitter account without a backup 2FA method. We know this is important to people because not everyone is able to have a backup 2FA method or wants to share their phone number with us.
Apple Offers Free Downloads of OS X Lion, OS X Mountain Lion
Until now Apple charged US$19.99 to download codes for OS X Lion and OS X Mountain Lion. But now they’re free from Apple’s website.
Lion runs on Macs that came prior to the launch of Mountain Lion in 2012. Mountain Lion runs on the Macs below, but you may not be able to downgrade to it unless you completely reformat the drive. You can’t install an old OS on top of a newer one. Also, the oldest OS an M1 Mac can run is Big Sur.
iOS 15 Public Beta is Now Available for Everyone
At WWDC21 Apple said that the iOS 15 public beta would be released in July, so it’s possible this early release means that the OS is fairly stable.
Parts of AT&T’s 5G Network Will Run on Microsoft Azure Cloud
Microsoft and AT&T announced a joint venture on Wednesday that will have the carrier run core parts of its 5G network using Microsoft’s Azure cloud.
The newer generation of networks, which AT&T began rolling out in 2018, is designed to rely more heavily on software and data centers for routing traffic rather than telecommunications specific gear.
Microsoft intends to use the newly acquired technology – plus the experience gained helping AT&T run the network – to build out a product it calls Azure for Operators, which it will use to go after core network business from telecommunications companies in the 60 regions of the world where it operates.
That sounds really cool to me that some phone traffic can run through data centers. I wonder if this move would make it easier for harder for government surveillance.
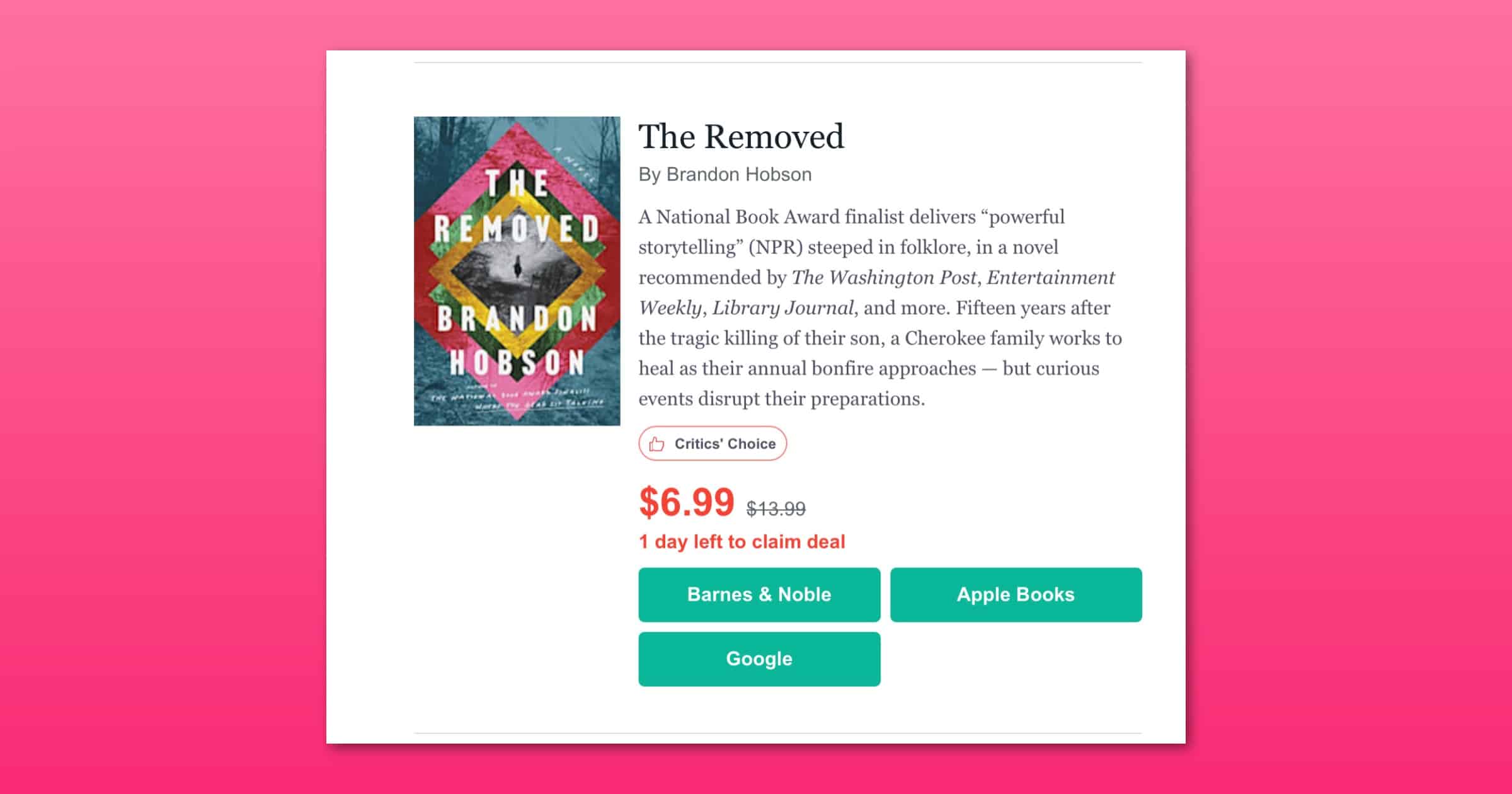
eBook Platform ‘BookBub’ Introduces The Short List for More Discounts
In an email sent to users, Bookbub has announced The Short List, a way to get discounts on new eBooks.
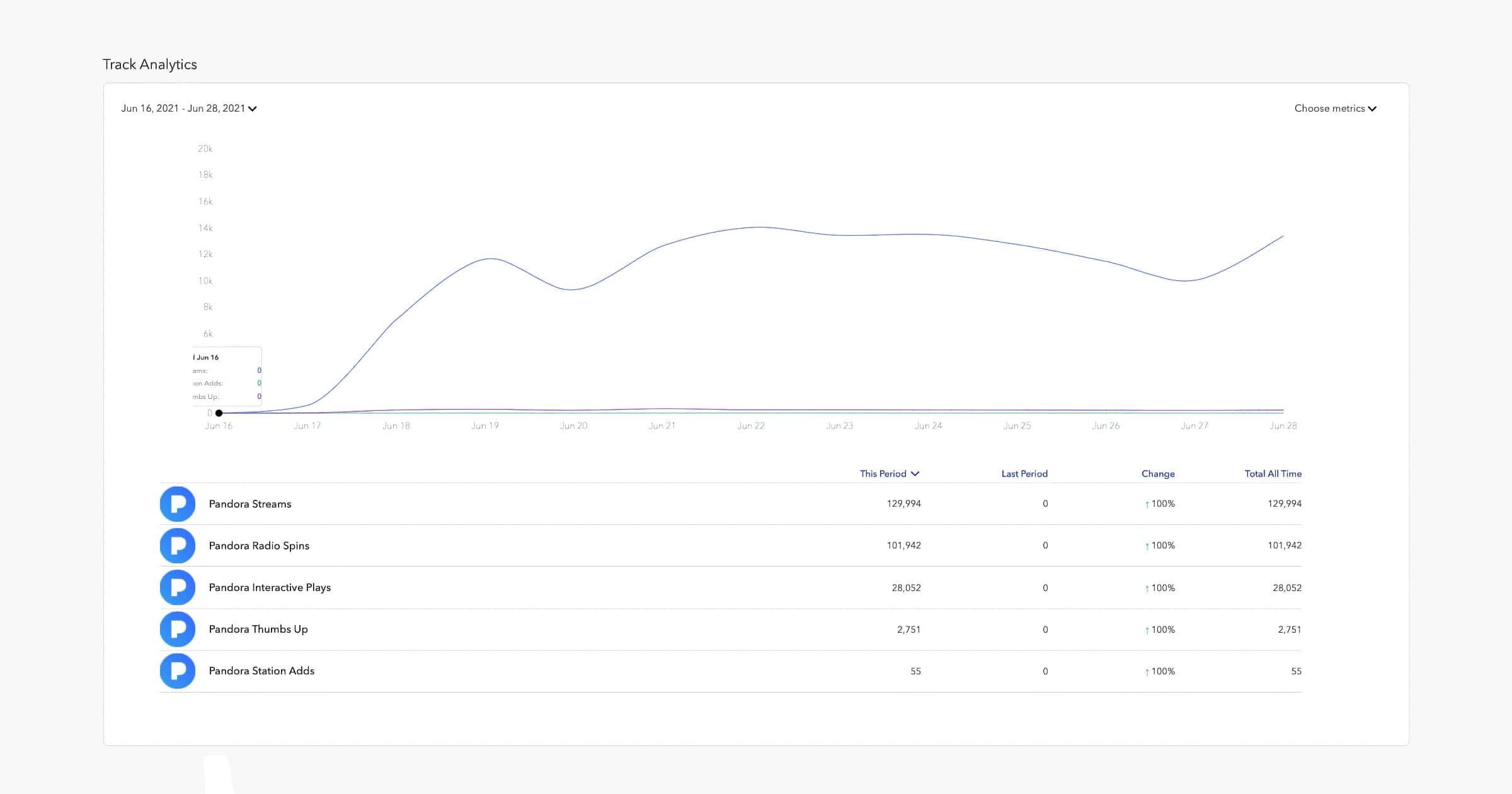
Pandora’s Artist Platform Adds Track Reporting for Listening Stats
Pandora’s Artist Marketing Platform (AMP) has added a new feature for creators called Track Reporting to provide listening statistics.
How Apple Arcade Shows an OS Merger Isn’t Wise
Alex Blake of Digital Trends writes how the nature of Apple Arcade shows the pitfalls of merging iOS and macOS.
You see, Apple Arcade is a showcase for all that’s wrong with taking two very different operating systems and mashing them together into a mixed-up medley where no one wins. Because developers have to make games that work on the tiniest iPhone and the largest iMac, they are forced into compromises that weaken the games on both platforms.
I see his point and I think I agree with him. No one wins except maybe the lowest common denominator. Maybe the more powerful M1 chip would change that, but probably not. iPadOS apps haven’t yet taken full advantage of the chip, as one example.
Satechi Releases Mac mini Stand and Hub with SSD Enclosure
Satechi’s newest product is a stand + hub combo for the Mac mini that includes an SSD enclosure. It’s available to purchase for US$99.99.
Cryptomator’s Major 2.0 Upgrade is Available in TestFlight, Now Open Source
File encryption app Cryptomator is readying a major 2.0 upgrade and interested users can test the beta within Apple’s TestFlight app on iOS.
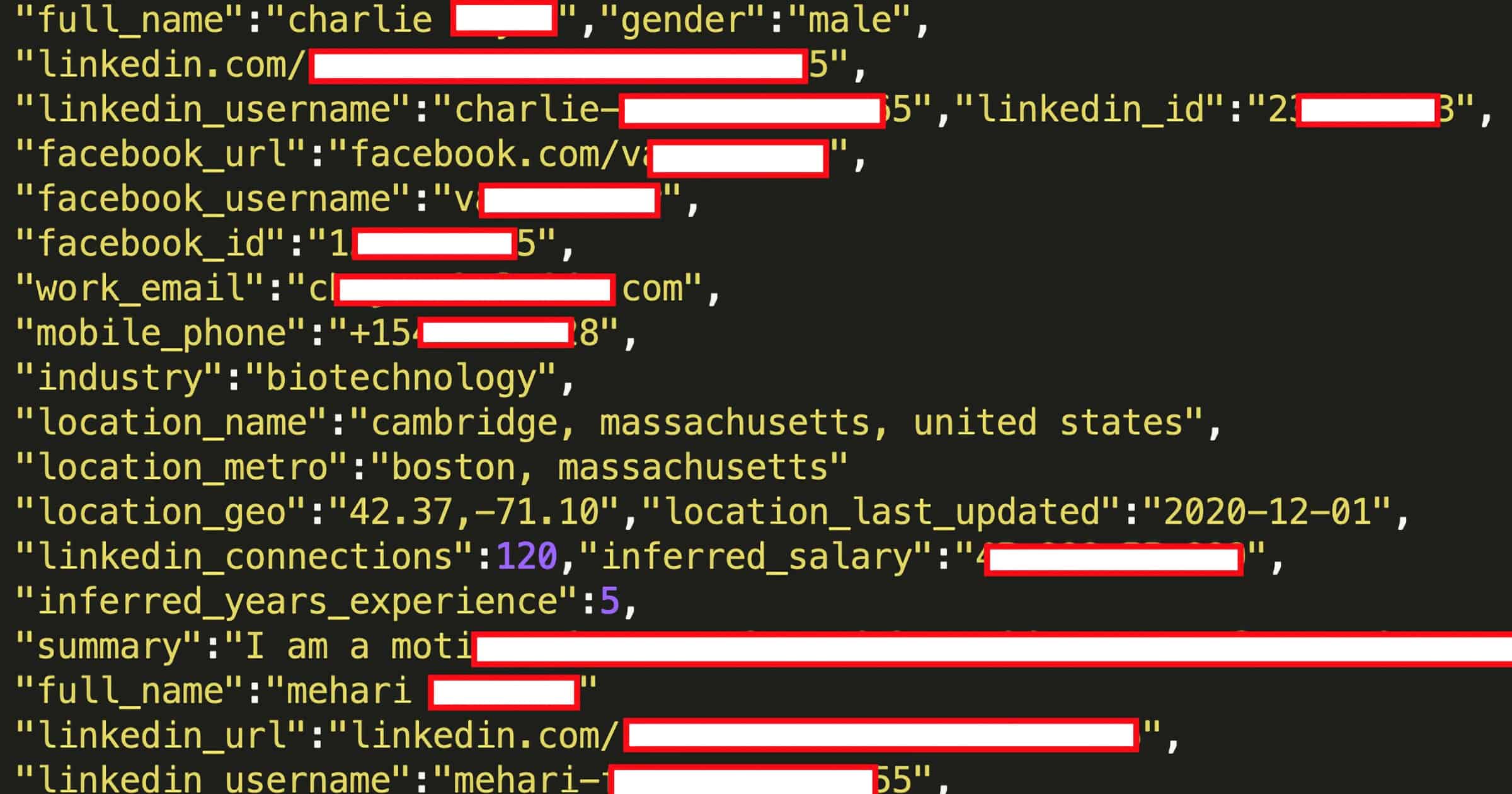
Hackers Sell Personal LinkedIn Data From Leak Affecting 700M Users
Hackers are selling the personal information of over 700 million LinkedIn users. Here are the data types that were leaked:
Email Addresses; Full names; Phone numbers; Physical addresses; Geolocation records; LinkedIn username and profile URL; Personal and professional experience/background; Genders; Other social media accounts and usernames
On June 22nd, a user of a popular hacker forum advertised data from 700 Million LinkedIn users for sale. The user of the forum posted a sample of the data that includes 1 million LinkedIn users.