Bryan Chaffin and Jeff Gamet talk about CES and the future of in-person events. They also take a look at brain implants, which, believe it or not, are here. And, they talk about efforts to make social media companies accountable and say: be careful what you wish for.
2021: Reviewing a Year of Apple Hardware
Apple unveiled a number of new products in 2021, along with some discontinued items. Let’a check out a year in review of Apple hardware.
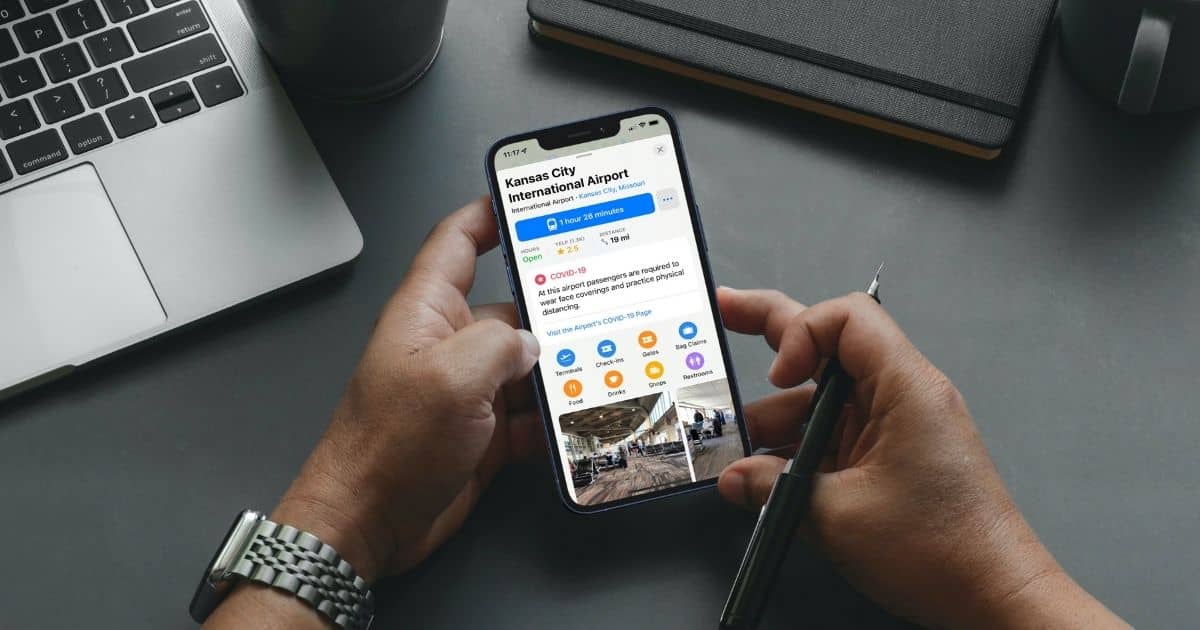
How to Use Apple Maps to Check for COVID-19 Vaccination Requirements
If you want to check for COVID-19 vaccination requirements, Apple Maps is a good start. The app partners with Yelp to display the details.
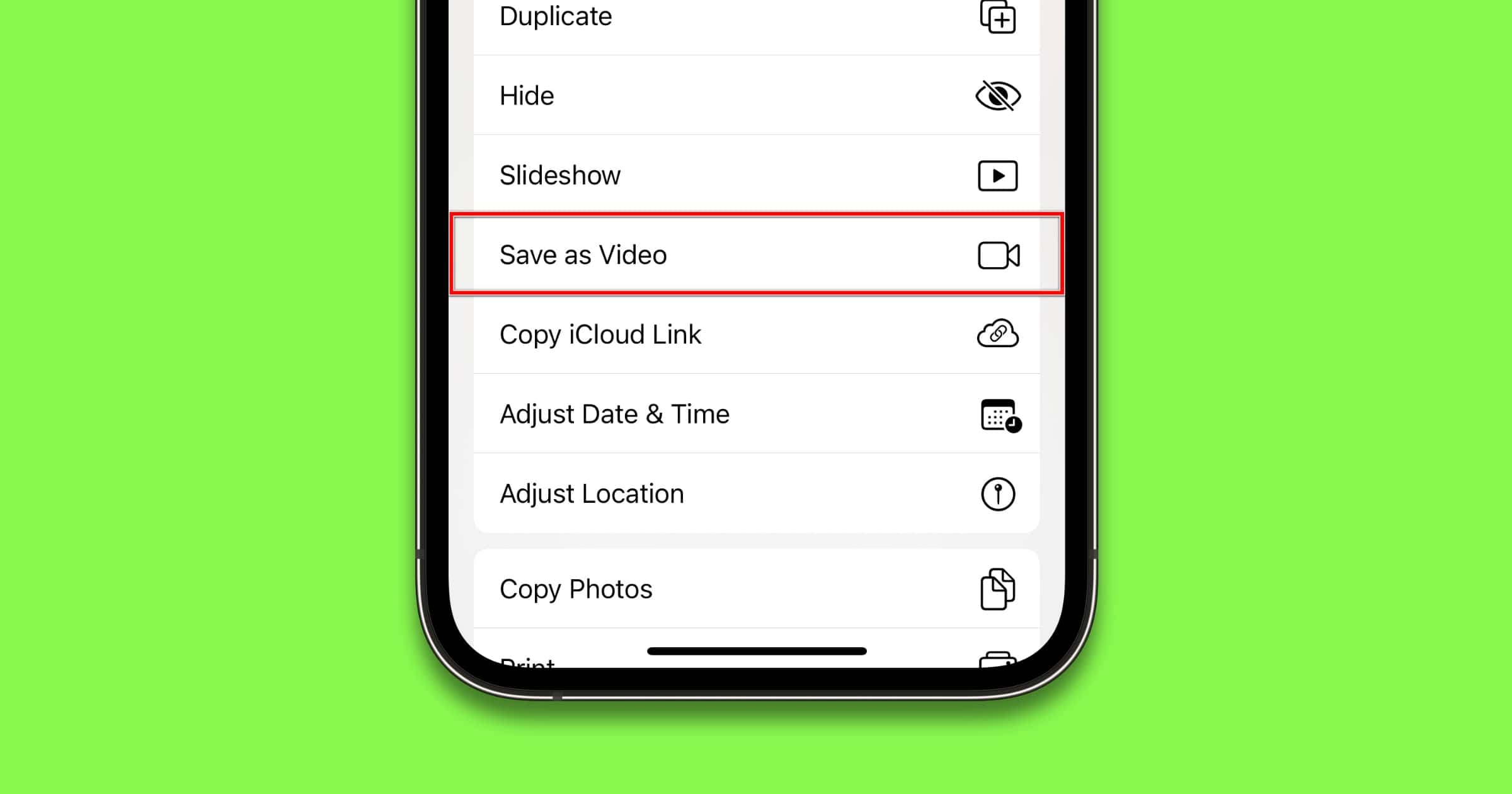
iOS: How to Merge Live Photos Together As a Video
iOS 13 adds a neat feature in Photos that lets you merge Live Photos together and save them as a video. Andrew shows us how.
Thursdays with Bob: Make Mine Monterey – TMO Daily Observations 2021-12-30
Dr Mac joins Kelly to talk about upgrading to Monterey, factors you’ll need to consider, and some general upgrade advice.
Gary Geaves, VP of Acoustics at Apple, Talks AirPods in Interview
Gary Geaves is the Vice President of Acoustics at Apple and his team was largely responsible for the design of AirPods.
Everything You Wanted to Know About How Encrypted Email Works
ProtonMail published a nice blog post explaining how encrypted email works, and the various protocols that companies use.
End-to-end encryption for messages sent between ProtonMail users is automatic, and our integrated OpenPGP support makes it easy to send and receive PGP-encrypted E2EE messages to people that use PGP with other email providers. Proton also informs you when your messages are protected by E2EE with a small blue padlock (for other ProtonMail users) or green padlock (for OpenPGP users).
The Four Products Apple Should Drop in 2022
For me, these are the four products Apple should discontinue from its lineup. I do believe they’re lost in time and any customer that bought one right now would be disappointed with the general experience.
I agree that it’s high time for Apple to discontinue the iPod touch, Watch Series 3, and Beats Solo3 Wireless. These products just aren’t reflective of the best Apple can offer anymore. Some might say the Apple Watch Series 3 is still a good choice. I’d argue most would be better off with the SE model. It’s only $70 more expensive and much more robust. But the Intel-powered Mac mini? I can’t really buy into this idea, simply for the sake of anybody who still needs to dual-boot Windows and macOS.
Polygon Fixes Bug That Endangered $24 Billion Worth of MATIC Token
Polygon, a Layer 2 scaling network for Ethereum, fixed a bug that put its MATIC token at risk. However, a hacker was able to steal tokens.
How to Stop the In-App Review Annoyance
If you’re annoyed with being bombarded with in-app review requests, you aren’t alone. Here’s how to turn those prompts off completely.
FCC Ruling Opens up to 1,200MHz of Spectrum for Wi-Fi 6E
A ruling by the U.S. Court of Appeals for the District of Columbia Circuit backs an FCC decision to open up to 1,200MHz of spectrum for Wi-Fi 6E.
While Wi-Fi 6 connections make more reliable and efficient use of the same spectrum that’s been in use for the last couple of decades, especially when multiple devices are connected, Wi-Fi 6E routers will work at 2.4GHz and 5GHz plus the new 6GHz band. That has enough room for up to seven maximum capacity Wi-Fi streams to broadcast in the same area at once without interfering with each other or using any existing spectrum.
TwelveSouth’s Happy New Gear Sale Could Save You a Bundle
Looking for a case for that new iPhone? Maybe a stand for your MacBook Pro? Take a look at the Happy New Gear Sale at TwelveSouth for terrific savings on elegant accessories for every Apple device.
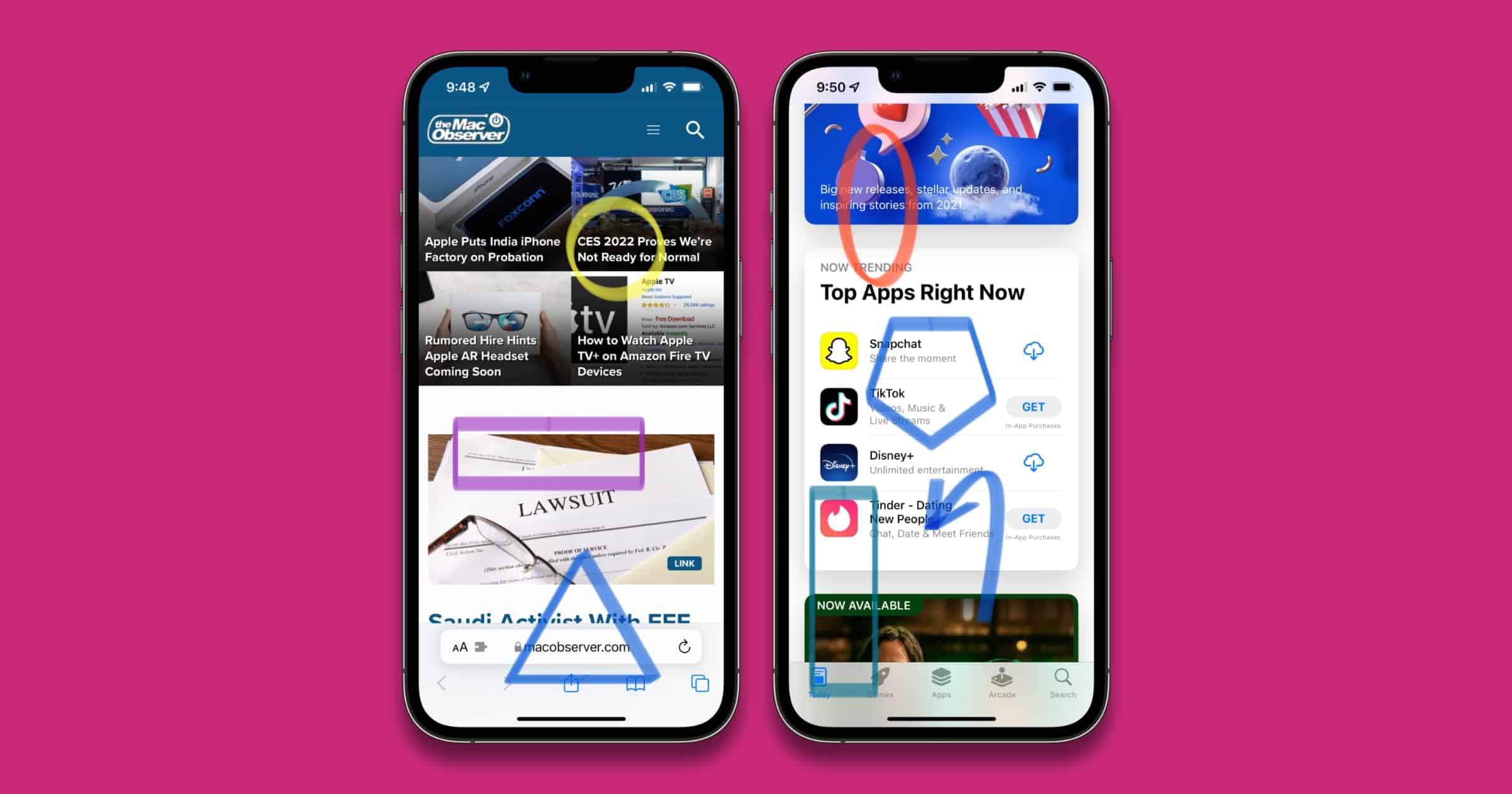
iOS: Here's How to Draw Perfect Shapes in Markup
Did you know you can draw perfect shapes with Markup? Markup lets you edit screenshots and photos to draw or add text.
Saudi Activist With EFF Sues DarkMatter Group for Hacking iPhone
Saudi human rights activist Loujain AlHathloul, along with the Electronic Frontier Foundation, is suing DarkMatter for hacking her iPhone. DarkMatter Group was created and run by former U.S. intelligence operatives.
Reuters broke the news about the hacking program called Project Raven in 2019, reporting that when UAE transferred the surveillance work to Emirati firm DarkMatter, the U.S. operatives, who learned spycraft working for the National Security Agency and other U.S. intelligence agencies, went along and ran DarkMatter’s hacking program, which targeted human rights activists like AlHathloul, political dissenters, and even Americans residing in the U.S.
Upgrade the Old, Troubleshoot the New – TMO Daily Observations 2021-12-29
Jeff Butts and Dave Hamilton join host Kelly Guimont to chat about tips for upgrading old hardware and getting new gear finely tuned.
Brace Yourselves: New HDMI 2.1a Standard to Debut at CES 2022
CES 2022 will see the introduction of yet another HDMI standard: 2.1a. What will it do? Both good and bad things.
Let’s start with the good: HDMI 2.1a is an upcoming revision to the HDMI 2.1 stack and adds a major new feature, Source-Based Tone Mapping, or SBTM. SBTM is a new HDR feature that offloads some of the HDR tone mapping to the content source (like your computer or set-top box) alongside the tone mapping that your TV or monitor is doing.
More HDMwhy, am I right?
Apple's Policies Force Tumblr to Ban Certain Tags for iOS Users
Tumblr has been banning a host of tags from its iOS app in an effort to comply with Apple’s app review policies.
Some of the banned tags make sense for a platform trying to scrub itself of sensitive content — “porn,” “drugs” and “sex” are banned, for instance. Others are incomprehensible (or troubling if you think about them for too long), like the aforementioned “Tony the Tiger” and “Eugene Levy.” Even tags with the numbers 69 and 420 are banned.
How to Measure Someone’s Height Using iPhone 13 Pro
In Apple’s latest iPhone user guide it tells people that iPhone 12 Pro/Pro Max can measure someone’s height using the LiDAR sensor.
iOS 13: Where to Find Sign in With Apple Logins
Sign in With Apple lets you sign into apps and websites with your Apple ID. Here’s where you find Sign in With Apple logins.
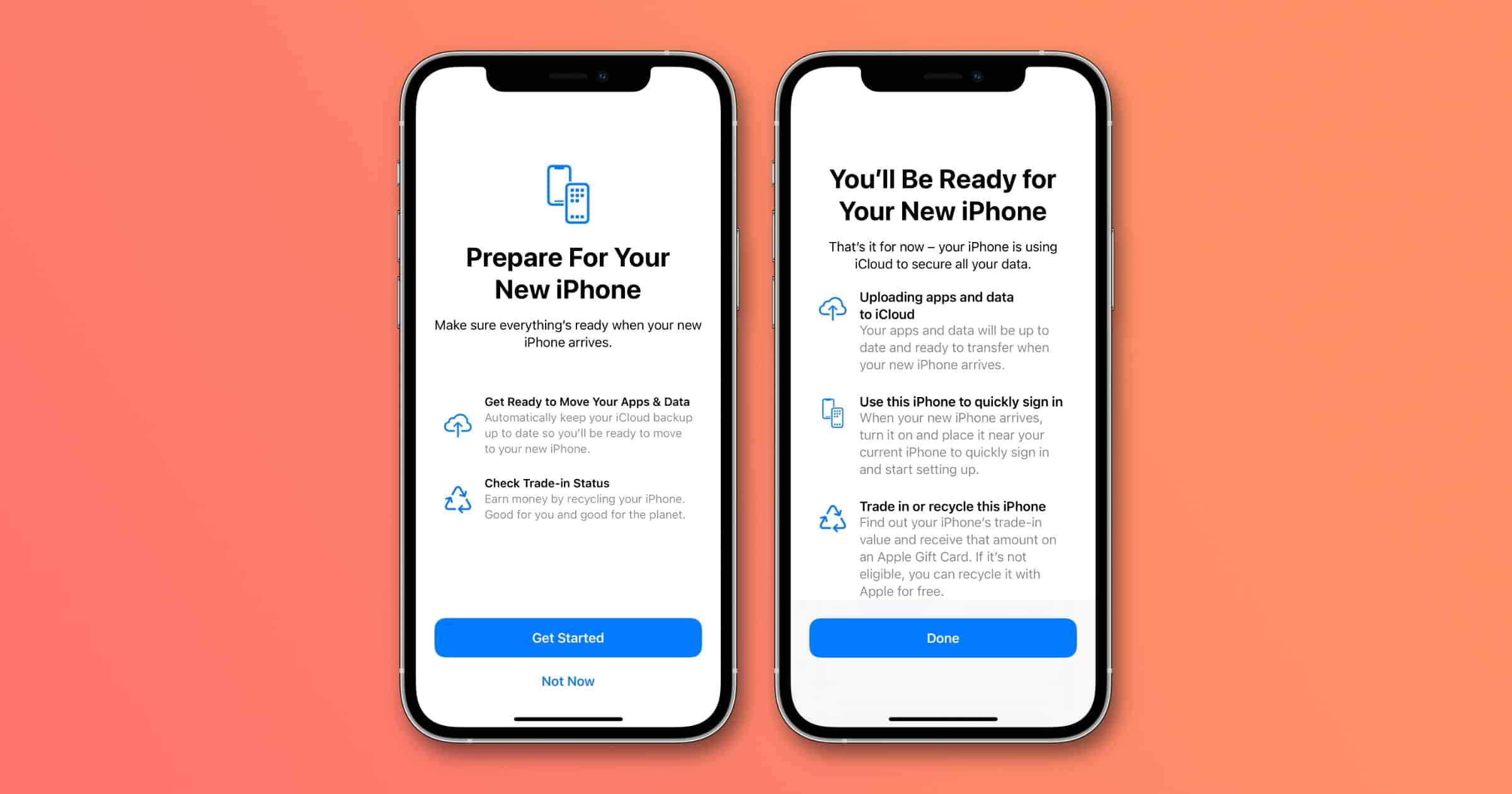
How to Prepare Your Apple Account For Your New iPhone
If you recently purchased a new iPhone or received one as a gift, this is the guide for you. These steps will help make your transition to the new device easy.
President Biden Signs 'National Defense Authorization Act' Into Law for Cybersecurity
The National Defense Authorization Act of 2022 lays out voluntary cybersecurity practices for private companies that handle critical infrastructure in the U.S.
But provisions all rely on the voluntary participation by industry, which owns and operates the vast majority of the nation’s critical infrastructure. Despite bipartisan calls after massive breaches at SolarWinds, Microsoft Exchange, Colonial Pipeline and other hacks, the NDAA made it through the House without mandatory incident reporting requirements for the private sector.
I disagree on the “voluntary” part. Make it mandatory, otherwise we end up with T-Mobile’s half-dozen breaches in the span of four years.
Geo-Fence Your Robot Vacuum
Learn how you can use a Geo-fence to run your vacuum while you’re out of the house in this mini-segment from Mac Geek Gab 906.
Totallee Ends 2021 With 50% Off Sitewide Clearance Sale
Totallee is ending the year with a big 50% clearance sale on all products. You can get the discount by using a special code.
T-Mobile Data Breach Leaves Customers Vulnerable to SIM Swapping
T-Mobile has had another data breach, although a report suggests this one is less severe than the one in August. Only a small set of customers have been affected, but they could be vulnerable to a SIM swapping attack.
This is where a malicious actor will change the physical SIM card associated with a phone number in order to obtain control of said number. This can, and often does, lead to the victim’s other online accounts being accessed via two-factor authentication codes sent to their phone number. The document says that customers affected by a SIM swap have now had that action reversed.