Enter our new international giveaway for a chance to win the brand new iPhone 16 Pro.
New Products at Mimeo Photos Include Mounted Prints
Mimeo Photos has recently launched mounted photos and expanded its size options for wall decor and photo prints.
Mimeo Photos users can now transform their favorite photos, designs or artwork into a customized mounted wall print to adorn the walls of their home, office or studio. Mimeo Photos also expanded its wall decor category to include eighteen new sizes and added two new sizes to its photo prints offering. As the No. 1 photo product extension in the Mac App store, Mimeo Photos continues to innovate and expand its product offering, while also being available everywhere its customers’ photos are taken and stored.
TMO Staff Preorders – TMO Daily Observations 2021-09-15
Dave Hamilton and Andrew Orr join host Kelly Guimont to discuss what they are (and aren’t) ordering from yesterday’s announcements.
Inside Project Raven, a Team of Former NSA Analysts Who Worked for the UAE Government
Project Raven was a team that included more than a dozen former U.S. intelligence operatives recruited to help the United Arab Emirates engage in surveillance of other governments, militants and human rights activists critical of the monarchy. Reuters tells the story.
The operatives utilized an arsenal of cyber tools, including a cutting-edge espionage platform known as Karma, in which Raven operatives say they hacked into the iPhones of hundreds of activists, political leaders and suspected terrorists. Details of the Karma hack were described in a separate Reuters article today.
An interesting story. We know that iOS 14.8 patched a vulnerability used by the Pegasus spyware, but I haven’t heard much about Karma.
Horizen (ZEN) and Braintrust (BTRST) Now Available on Coinbase Pro
Coinbase announced on Wednesday support for Horizen (ZEN) and Braintrust (BTRST). These can be traded on Coinbase Pro.
The iPhone 13 has Five Different 5G and LTE Configurations
The iPhone 13 lineup has five different configuration setups for 5G and LTE. This is the widest array of frequencies of any iPhone thus far.
Apple Care+ With Theft and Loss Expanded to UK and Australia
Apple Care+ with Theft and Loss coverage has been expanded and is now available in both the UK and Australia.
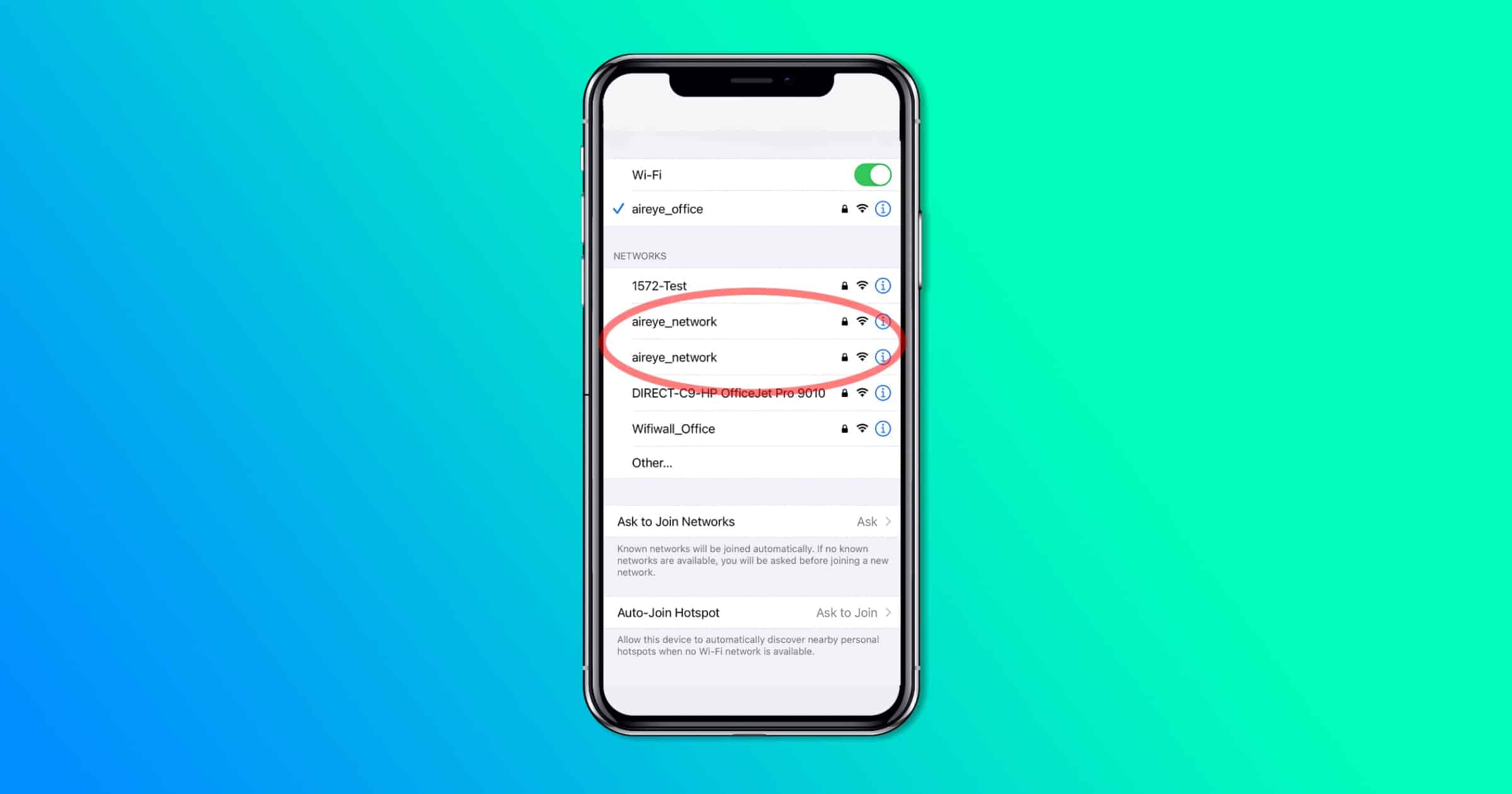
'SSID Stripping' Can Trick You Into Joining a Malicious Wi-Fi Network
Researchers have discovered a new type of network vulnerability dubbed SSID Stripping. It causes a network name to appear differently in a device’s list of networks, thus tricking people into joining a malicious network.
The SSID Stripping vulnerability affects all major software platforms – Microsoft Windows, Apple iOS and macOS, Android and Ubuntu. With SSID Stripping, it is possible to create a network name in a way that its display only shows a prefix that is similar to a legitimate network name (e.g. the corporate network name) while the actual network name includes the additional specially crafted information.
Phone Carrier 'Visible' Will Sell Apple Watch Series 7 for First Time
Visible, a prepaid carrier that operates on Verizon’s network, will sell the iPhone 13 models and the Apple Watch Series 7 on its website.
The Ultimate Guide To Surge Protecting
Here’s a guide to surge protecting your network from Mac Geek Gab 887.
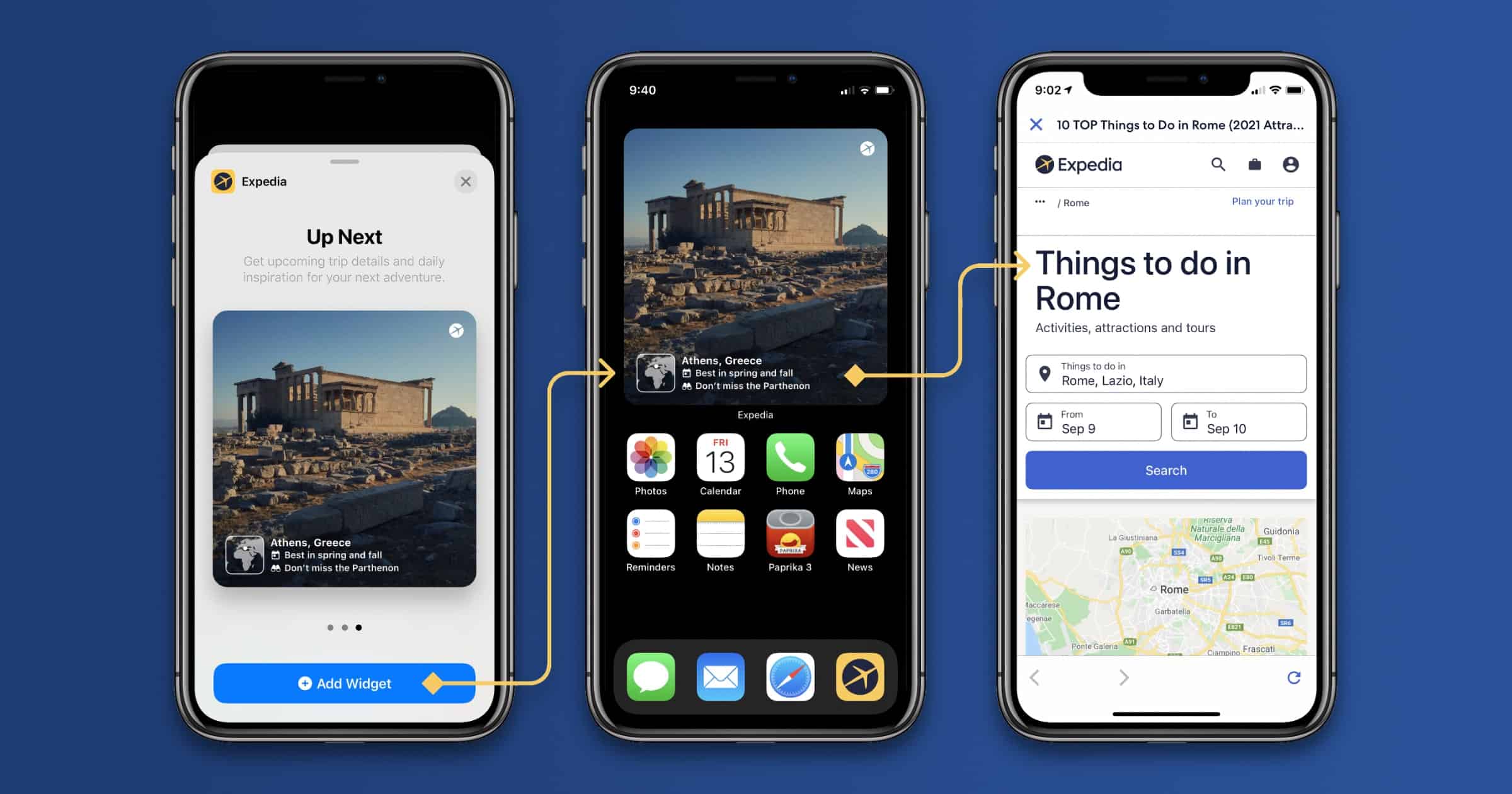
Expedia Group Announces iOS 15 Widgets and Quick Note Integration
On Tuesday Expedia Group announced some new features for its apps: New widgets designed for iOS 15 and an update that takes advantage of iOS 15 Quick Notes.
Geeks Scheming about Apple's California Streaming — Mac Geek Gab 890
Apple announced new iPhones, iPads, Fitness+ features, Watches, and more on Tuesday, and your two favorite geeks are here to share their reactions. On top of that, listen for Dave’s pre-review of iOS 15 for you and John, as well as advice on how to approach next week’s upgrade. Press play and enjoy learning five new things!
Developer of 'FlickType' Sues Apple Over Apple Watch Keyboards
Kosta Eleftheriou, developer of the FlickType keyboard for Apple Watch, has filed a lawsuit against Apple for fraud.
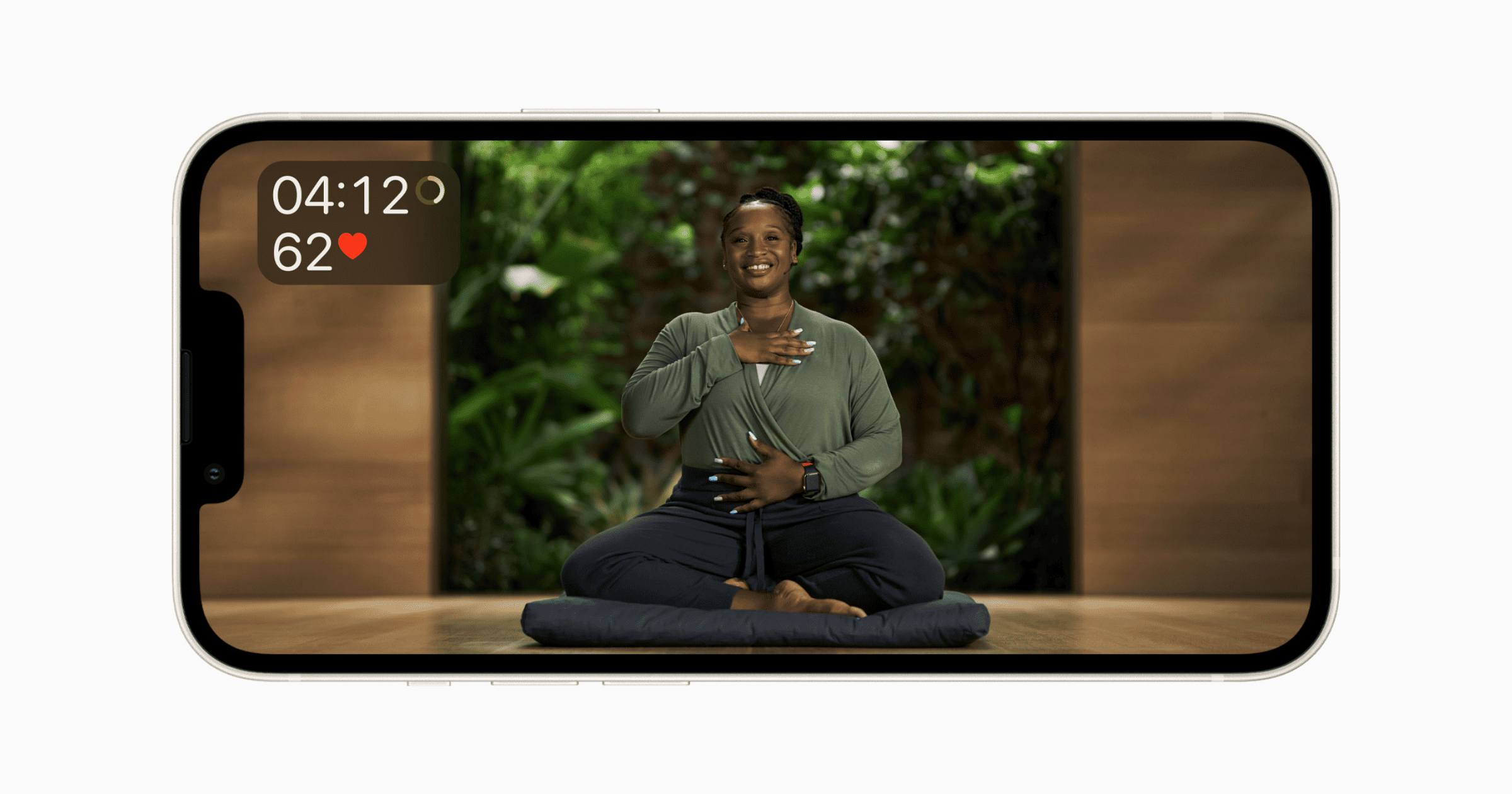
Apple Fitness+ is Coming For Calm, Headspace
Apple Fitness+ is introducing guided Meditation, letting users practice mindfulness through the service, a challenge to Calm and Headspace.
iPhone 13 Pro Camera Features Include All-New Macro Photography
Apple announced its powerful iPhone 13 Pro lineup on Tuesday and here are the camera features that users will get.
California Streaming Reactions – TMO Daily Observations 2021-09-14
Charlotte Henry and Bryan Chaffin join host Kelly Guimont to discuss Apple’s ‘California Streaming’ event and the announced (or not) products.
Apple Announces the iPhone 13 Lineup
At its “California Streaming” event, Apple introduced the latest model of its smartphone lineup, the iPhone 13.
Surprise! There's a New iPad mini!
Apple unveiled a new iPad mini, with an 8.3-inch Liquid Retina display, the A15 Bionic chip, and upgrade cameras.
Apple Unveils Ninth-Generation iPad at 'California Streaming' Event
Apple announced a new iPad with the A13 Bionic chip, a 10.2-inch Retina display with True Tone, and a 12MP Ultra Wide front camera.
Apple Announces Apple Watch Series 7 With Exciting New Features
The Apple Watch Series 7 didn’t get the flat design that rumors claimed, but it’s still a notable update with a big screen.
Do AirTags Interfere With Planes?
Ever wonder why you can’t use your phone on a plane, and if AirTags in your luggage could have the same effect? Watch this segment from Mac Geek Gab 888 to find out the answer.
Want To Know More? Check Out this article from Civil Beat.
How to Use Regular Expressions, or Regex, in Shortcuts
Regular expressions, or regex for short, are certain characters used as search functions. They are powerful, confusing tools. Justin Meredith wrote a guide on how to get started.
In case you don’t know, a piece of text within another piece of text is called a “string” in programming. For instance, the word ‘green’ is a string of characters from the text “I wore green pants today.”
So put another way, regex is a way to locate a string of text in a larger body of text. And because regex is written in code, you can use it to perform some pretty complex operations.
Facebook Glasses - Creepy or Great for Content Creation and Consumption? — Media+
Adrian Weckler joins Charlotte Henry to discuss his experience using Ray-Ban Stories/Facebook glasses. They are creepy but are they also useful for content creation and consumption.
The Rotor Riot Game Controller
Want to turn your iPhone into a game controller? Check out Rotor Riot’s game controller where you can do just that in this Cool Stuff Found from Mac Geek Gab 887.
Researchers Uncover a Phishing Kit Used by Two Criminal Gangs
Led by Noam Rotem, vpnMentor’s research team has discovered two separate criminal gangs using slightly altered versions of the same phishing kit to scam people across the globe.
It appears the phishing kit was being used to target people mostly living in Israel and France by two separate criminal gangs. However, we believe these two groups operate phishing websites and SMS operations based on the same phishing kit, possibly obtained from the same source. In addition, at least one of them is potentially affiliated with the OpIsrael political hacking group.