We finally have the winner of our iPhone 16 Pro international giveaway! Congratulations to Oliver T., and a huge thank you to everyone who participated.
Chinese Hackers May be Stealing Data to Feed an Artificial Intelligence
Dina Temple-Raston of NPR published a fascinating investigation regarding the Microsoft Exchange attack earlier in 2021.
Officials believe that the breach was in the service of something bigger: China’s artificial intelligence ambitions. The Beijing leadership aims to lead the world in a technology that allows computers to perform tasks that traditionally required human intelligence — such as finding patterns and recognizing speech or faces.
Myst Comes to the Mac App Store with New Art and Sound, More
Cyan releases Myst on the Mac App Store and Steam with updated graphics and sound along with M1 Mac support.
AirTag Firmware Update Rolls Out, Here's How to See if Your Tracker is Up to Date
Apple released a firmware update for its AirTag tracker. Here’s how to see if it’s installed on yours.
45 MM Apple Watch Photo Leak Inspires Our 51 MM Watch Pic
A new photo claims to confirm Apple is making a 45 mm Apple Watch, so we made our own “leaked” pic showing a 51 mm model—which doesn’t really exist.
Most Workers Are Open to Pay Cuts to Stay Home
As folks have gotten accustomed to the freedom and flexibility of remote work, most workers are open to pay cuts to stay home.
US Air Force Contract Aims to Improve Blockchain Security
The United States Air Force will use Constellation’s Hypergraph Network to provide data security with the Department of Defense’s commercial partners.
Constellation said it had been working with Kinnami Software Corporation to develop an end-to-end data security solution using blockchain encryption and distributed data management for the United States Transportation Command, Air Mobility Command’s 618th Air Operations Center, and a Civil Reserve Air Fleet partner. According to the platform, its goal is to securely exchange data with commercial partners on missions involving the operations of aircraft and ships under contract to the Department of Defense, or DoD.
How to Sign Up for Today at Apple Sessions
If you want to learn how to use Apple products, Cupertino has you covered. Let’s walk through how to sign up for Today at Apple sessions.
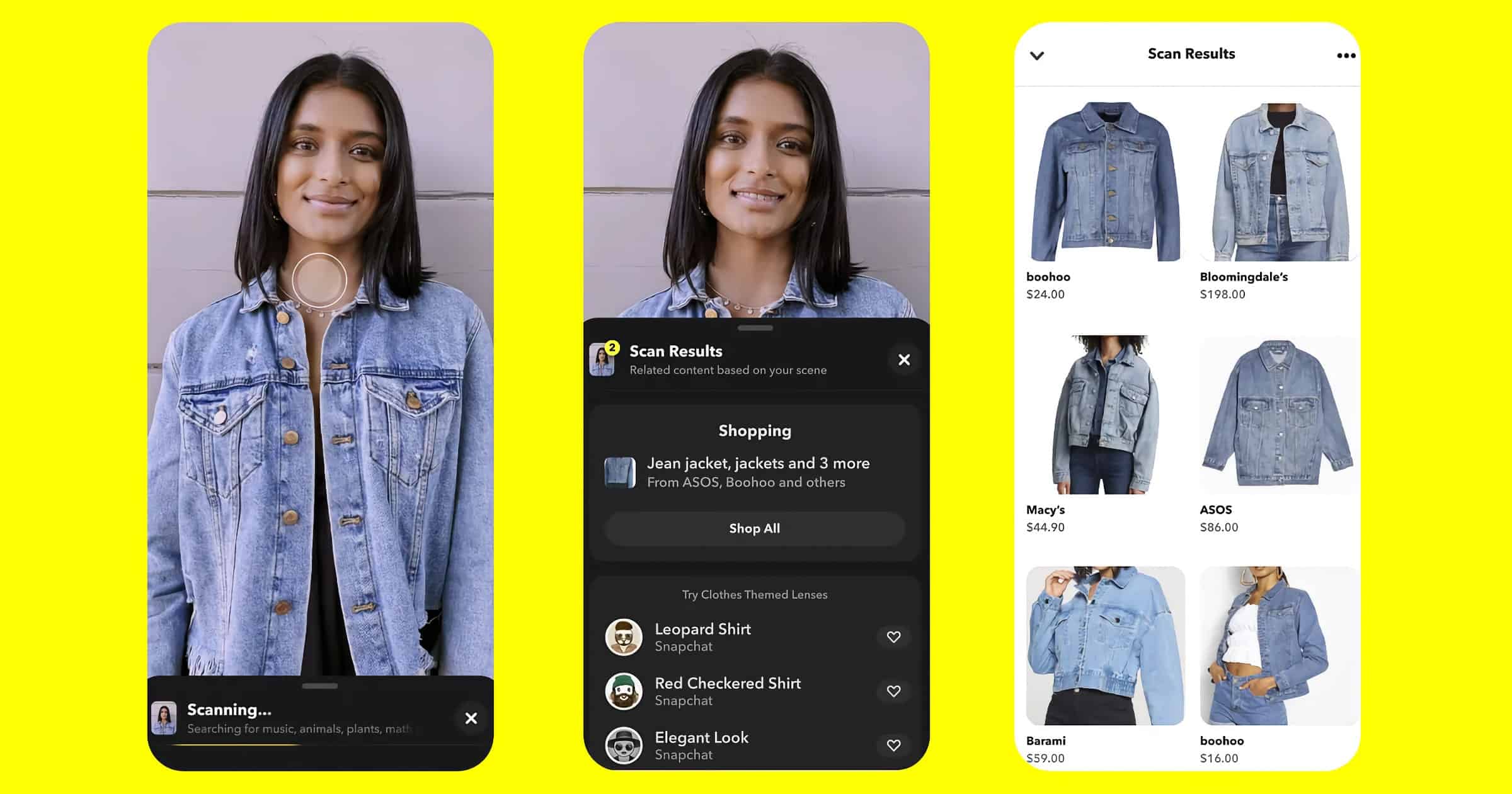
New Snapchat Scan Feature Can Detect Clothes, Plants, Wine, and More
Snap released a new augmented reality feature on Thursday. Called Scan, it can detect objects in the physical world.
This latest version of Scan, which Snap previewed at its developer conference earlier this year, adds detection for dog breeds, plants, wine, cars, and food nutrition info. The majority of Scan’s features are powered by other companies; the app Vivino is behind the wine scanning feature, for example. Soon Allrecipes will power a Scan feature that suggests recipes to make based on a specific food ingredient. Snap plans to keep adding more abilities to Scan over time using a mix of outside partners and what it builds in-house.
Data Leak From Chinese Company 'EskyFun' Affects 1 Million Gamers
The research team at vpnMentor discovered an unsecured server from Chinese mobile gaming company EskyFun. It exposed data for over a million Android gamers.
The resulting records contained a lot of sensitive information, including: IP address, IMEI number, Mobile application package doing the tracking, Device screen size – whether a device is ‘rooted’*, Device model, Phone number (if any), Platform (Android/iOS), NetType (WiFi or cellular), Events (open,login,level_up, etc).
Not so fun anymore.
Tim Cook Receives Final Payout of $750 Million in Apple Stock
As part of a 10-year deal when he took over as Apple CEO, Mr. Cook’s final payout is 5 million shares in Apple worth roughly US$750 million.
Biotech Startup 'SweetBio', VC Firm "VamosVentures, Get Funded by Apple
Two companies have gotten funding from Apple’s Racial Equity and Justice Initiative, a biotech startup called SweetBio and a venture capital firm called VamosVentures.
Thursdays with Bob: BBEdit and You! – TMO Daily Observations 2021-08-26
Dr Mac and Kelly chat about how the new version of BBEdit improves on some of the features both of them use most, and why you might like it too.
How to Join Wi-Fi Networks from Control Center on Your iPhone
You can join Wi-Fi networks from Control Center on your iPhone instead of going to the Wi-Fi options in the Settings app. Watch our video to learn how.
Try BBEdit for Writing
Dr. Mac prefers composing text in a plain-text editor instead of a word processor for myriad reasons he discloses in Dr. Mac’s Rants & Raves Episode #449.
Tesla iOS App Update Brings Widgets and More
The latest version of the Tesla iOS app brings enhanced phone key support and a brand-new set of widgets for your iPhone’s Home Screen.
News Partner Program Aims to Boost Apple News Format in Stories
On Thursday Apple announced the News Partner Program for subscription news publications to publish their content in Apple News Format.
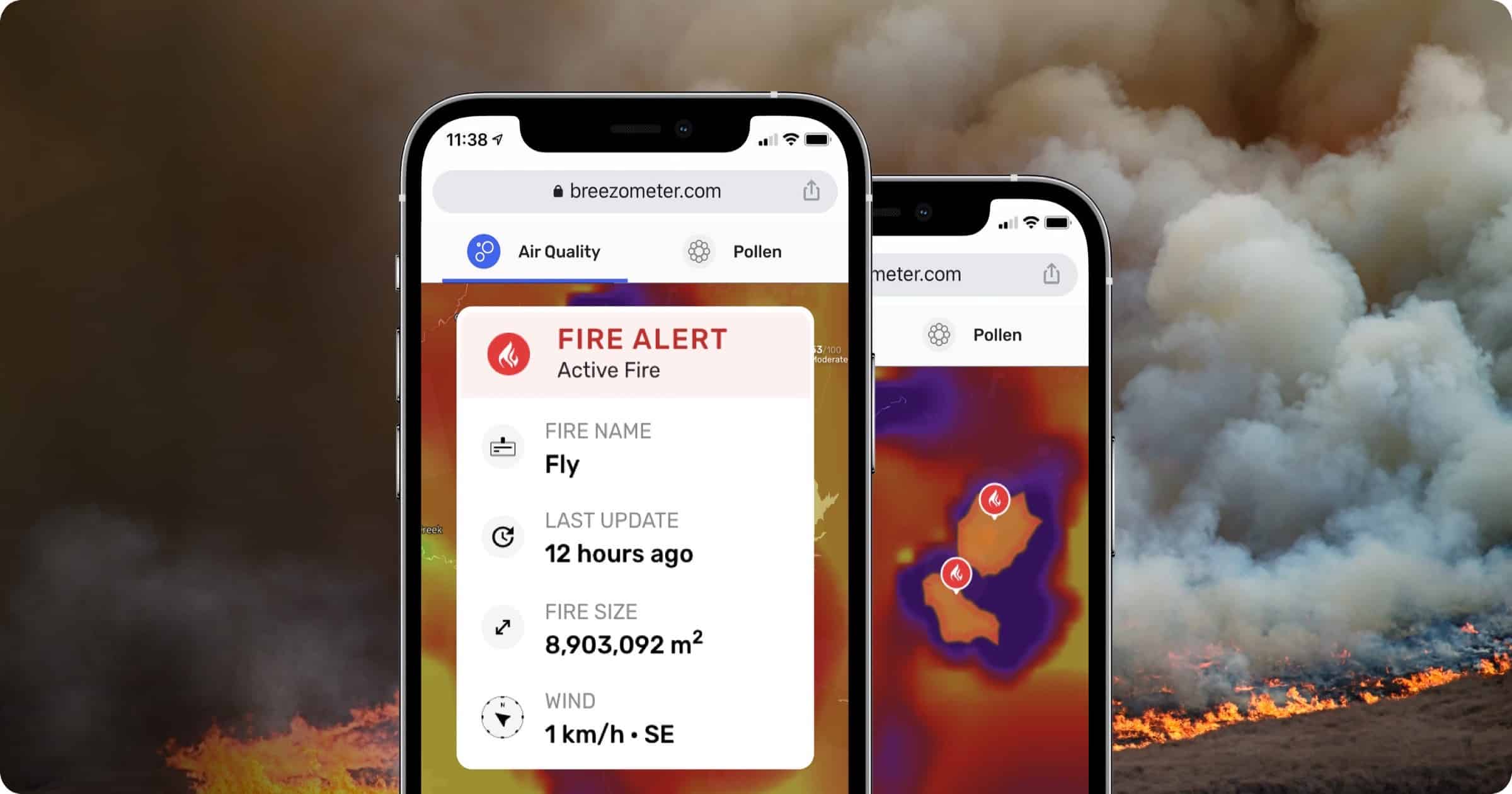
Could BreezoMeter’s New Wildfire Tracker Come to Apple Weather?
BreezoMeter has launched a Wildfire Tracker that provides real-time detection of wildfire perimeters.
Apple TV Hacks You Should Know
Learn about auto-play, minimizing credits, fast-fast forward, and more in this mini-segment from Mac Geek Gab 885. This Apple Discussion has even more details.
4 More Must-have Mac Menu Bar Add-ons
We have four more great Mac menu bar add-ons to follow up from last week’s list. They’ll all help do even more with your Mac, so read on to see our list.
A Virtual Keyboard Could Be Coming to Your Mac
An Apple filing just approved by the United States Patent Office could point to Cupertino offering virtual keyboard technology on the Mac.
Smash Hit Asphalt 8: Airborne Racing to Apple Arcade
Apple Arcade might have been launched to help new and exclusive games, but Cupertino has been adding some really hot titles to the subscription gaming service. On August 27, 2021, you’ll be able to download the popular racing game Asphalt 8: Airborne through Apple Arcade. Sure, the franchise is up to Asphalt 9, but this version won’t tempt you with in-app purchases.
One interesting aspect of having Asphalt 8 available on Apple Arcade is the change in the gameplay model. Current Asphalt games (including Asphalt 8) are free-to-play, meaning that anyone can download them without paying, but the game offers multiple items that can only be obtained through in-app purchases.
Apple Maps Updates for Better (or Worse) – TMO Daily Observations 2021-08-25
Andrew Orr and Jeff Gamet join host Kelly Guimont to discuss the new revisions to Apple Maps after Jeff pointed out some places it is lacking.
It’s Easy for Minors to Bypass App Store Age Restrictions
On Wednesday, the Campaign for Accountability published a report that shows how easy it is for minors to bypass App Store age restrictions.
Using an Apple ID for a simulated 14-year-old, TTP examined nearly 80 age-restricted apps on the App Store and discovered that the underage user could easily evade the apps’ age restrictions in the vast majority of cases, often with minimal effort.
Your Internet Activity May be Traceable Even Through a VPN
Netflow data refers to IP network traffic that can be collected as it enters or exits an interface. Using this aggregate data, it’s possible to trace network traffic even if a person uses a VPN. Internet service providers sell this information to third parties.
At a high level, netflow data creates a picture of traffic flow and volume across a network. It can show which server communicated with another, information that may ordinarily only be available to the server owner or the ISP carrying the traffic. Crucially, this data can be used for, among other things, tracking traffic through virtual private networks, which are used to mask where someone is connecting to a server from, and by extension, their approximate physical location.