UK regulator the Competition and Markets Authority has launched a market study into both Apple and Google.
'The Daily' Looks at Apple's Bet on China
Monday’s episode of The Daily podcast looked at Apple’s relationship with China and how it has evolved over time. It builds on a recent New York Times investigation into the same subject and raises some uncomfortable questions for the company.
Pixelmator Pro Will Support macOS Monterey Shortcuts
On Monday the team behind Pixelmator Pro announced that its Mac app will integrate with the upcoming Shortcuts app on macOS Monterey.
Why You Should Drill a Hole Into Your iPhone or iPad
Over the weekend, Nikita Mazurov for The Intercept reminds us that a good way to wipe our iDevices is to drill a hole through it.
If you can’t access your device, the most careful approach to wiping it is to destroy the flash memory chip that houses your data. This way you don’t have to lose sleep if you didn’t use a strong passcode, or worry about a forensics vendor being able to recover any of your personal information.
How to Set Up a Ledger Nano X Wallet for Cryptocurrency
Over the weekend Andrew received his Ledger Nano X hardware wallet for cryptocurrency, and he set it up on Saturday.
Apple Design Awards, Monterey Missteps – TMO Daily Observations 2021-06-14
Bryan Chaffin and Charlotte Henry join host Kelly Guimont to chat about Apple Design Award winners, and Apple’s puzzling Monterey preview.
Beware of Malicious PDFs When Using Web Search
The team behind the SolarMarker malware have been loading it into PDFs and using web search to trick people into downloading them.
Apple Celebrating Black Music Month with Special Today at Apple Sessions From Willie Jones and Valerie June
Apple is celebrating Black Music Month with special online Today at Apple Sessions from Willie Jones and Valerie June.
'The Morning Show' Season Two Premieres September 17 on Apple TV+
The Morning Show is set to return to Apple TV+ on September 17, 2021, with old stars returning and new characters entering the story.
Apple Stores to Drop Mask Requirement for Vaccinated Customers
Apple Stores will no longer require vaccinated customers in the U.S. to wear a mask where local restrictions allow for this.
Download the M1 iPad Pro Wallpapers Here
The folks at OSXDaily found all eight M1 iPad Pro wallpapers. Four of them are light mode and four of them are dark mode. “This time around, Apple has made sure the new wallpapers show off the new Liquid Retina XDR display in all its glory. But, if you already have an older iPad Pro, you can replicate the look with these new wallpapers, as we’ve sourced them for you in full resolution.“
HaaS: Hay as a Service – Mac Geek Gab 876
Listen as John and Dave share your Quick Tips about Safari Picture-in-Picture, the caveats of Finder’s Drag and Drop, Apple Remotes, and more. Lots of suggestions and ideas about note-taking and idea capturing on-the-go in the episode, many of them from y’all! Then your two favorite geeks even have time to answer a few questions, including a clever workaround for blocking SMS spam. Plus… HaaS folks! It’s gonna be big! Or at least amusing. Press play and enjoy learning at least five new things!
Apple TV+: 'Lisey's Story' Made Pablo Larraín Rethink Filmmaking
In a new clip, Lisey’s Story director Pablo Larraín explained how working on the adaptation of the Stephen King novel demanded he rethink his approach to filmmaking. Stars Julianne Moore and Clive Owen also discussed the working process. The first three episodes of season one are available to Apple TV+ subscribers now, with new episodes released each Friday.
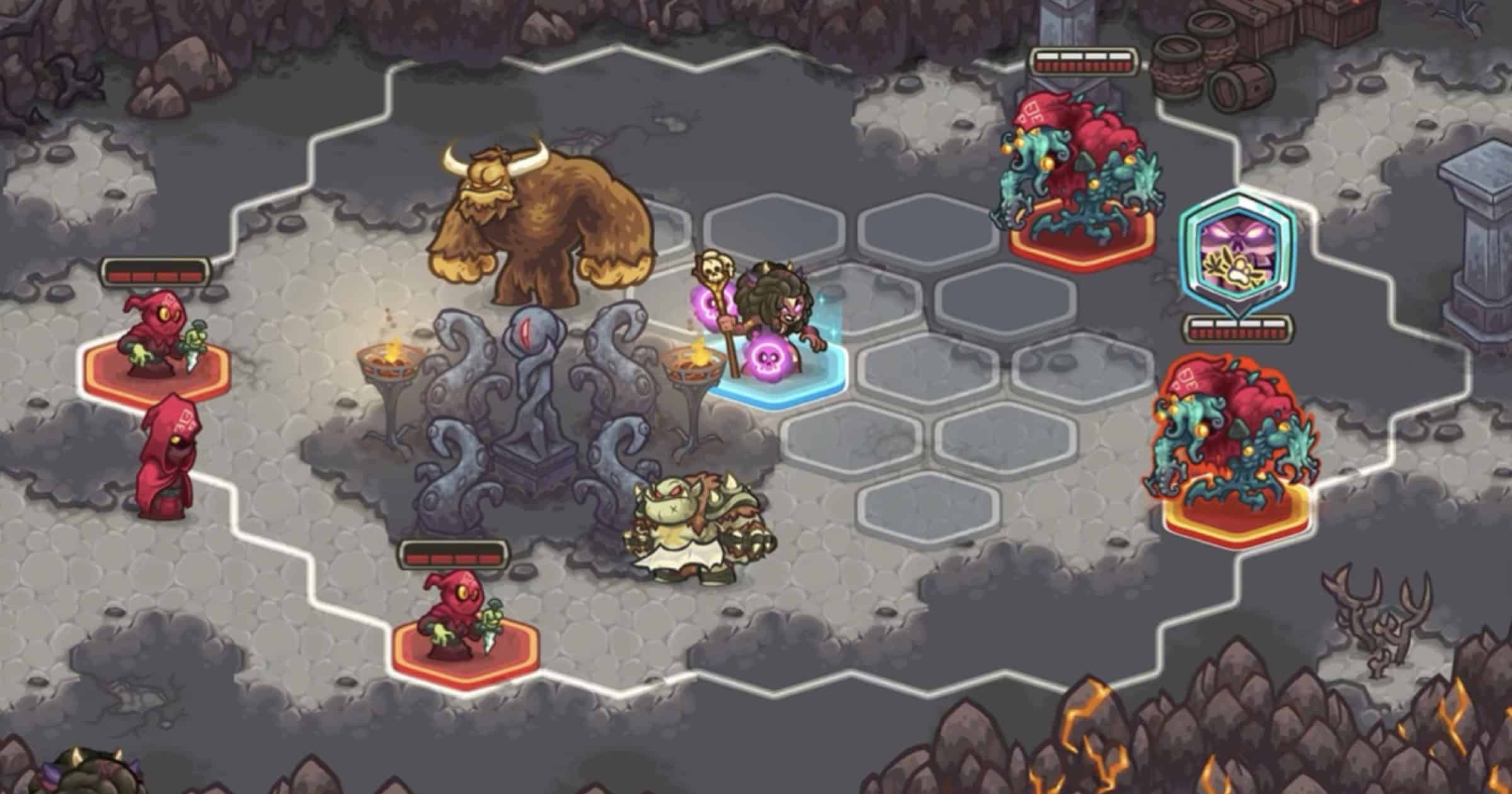
‘Legends of Kingdom Rush’ Now on Apple Arcade
Apple announced on Friday that Legends of Kingdom Rush is now on Apple Arcade. It’s a turn-based combat game.
WWDC Developer Spotlight: Jay Miller – TMO Daily Observations 2021-06-11
Today Kelly chats with Jay Miller about the announcements out of WWDC and envisions a world where Apple has some competition.
Gaming Company ‘EA’ Suffers Data Breach of Game Code
Electronic Arts is the latest company to have information stolen in a data breach. It includes the source code for FIFA 21, the Frostbite engine, and proprietary frameworks and SDKs.
We are investigating a recent incident of intrusion into our network where a limited amount of game source code and related tools were stolen. No player data was accessed, and we have no reason to believe there is any risk to player privacy.
Following the incident, we’ve already made security improvements and do not expect an impact on our games or our business. We are actively working with law enforcement officials and other experts as part of this ongoing criminal investigation.
Two Adobe Apps Will Disappear From the App Store on June 21
Adobe revealed in a support forum that it will remove Photoshop Mix and Photoshop Fix from the App Store on June 21.
Apple Should Have Been Clear About macOS Monterey and M1 Macs
As we have now learned, users will require an M1 Mac to get all of the features coming in macOS Monterey. Oliver Haslam at iMore thinks that by allowing users and journalists to work this out, instead of properly announcing itself, Apple missed a big opportunity to talk up its own silicon. I rather agree.
What if Apple had made a point out of the M1 Macs getting the full feature set? What if Apple had someone stand on its virtual stage and say “because M1 is so powerful, and thanks to its Neural Engine, we were able to take macOS Monterey a step further on new Macs.” What if someone had rolled out the red carpet, shown the new features off on a bright orange M1 iMac, and pointed out just why the M1 is so great? The whole message would be different. Then, the M1 would be the hero of the piece, flexing its muscle to go above and beyond. Now, it’s the villain as it rips features from Intel’s cold, dead hands.
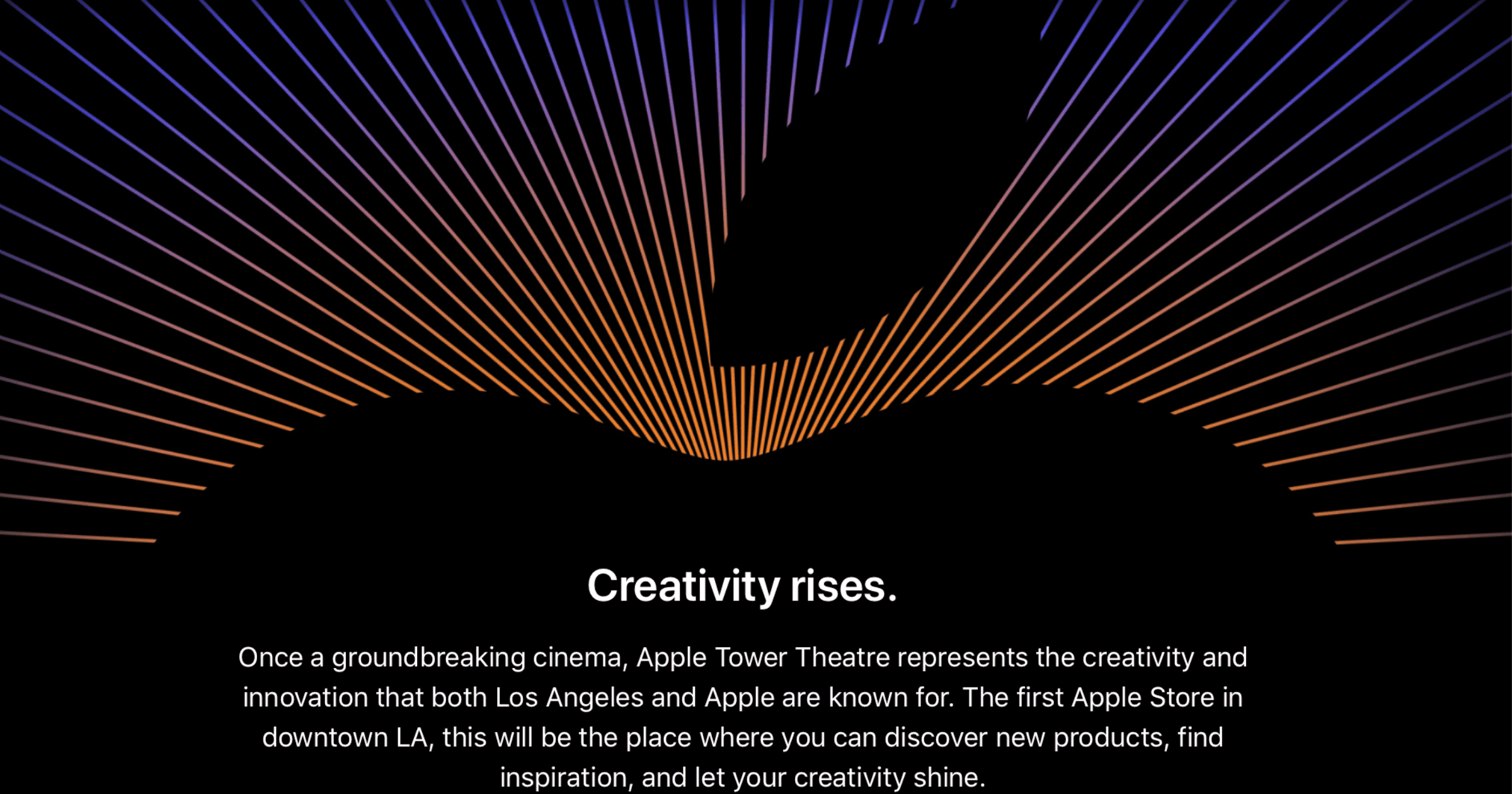
Apple Tower Theatre in Downtown LA to Open on June 24
The Apple Store at the Tower Theatre in LA will finally open its doors on June 24, in the heart of the city’s Broadway Theater District.
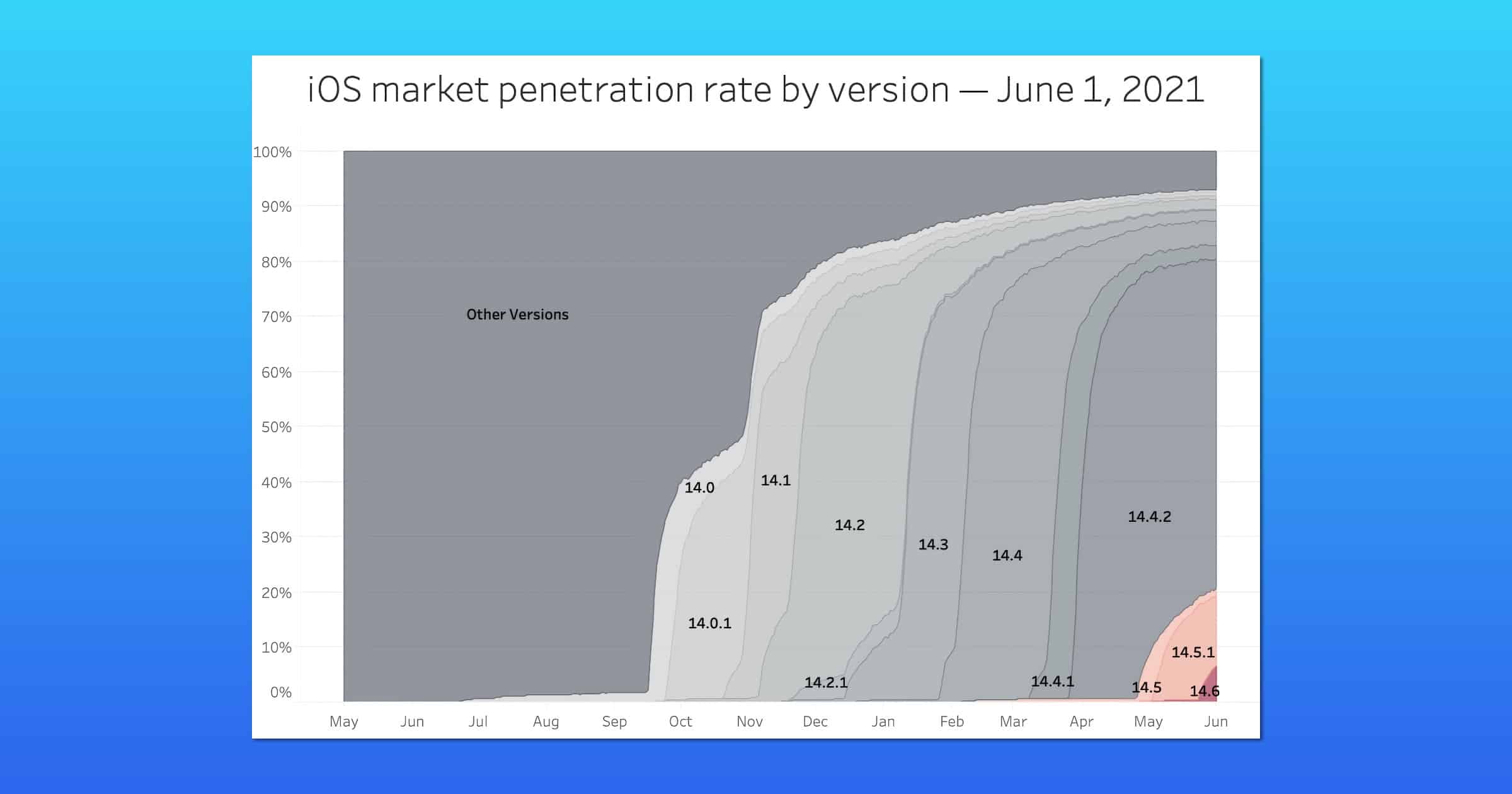
Only 35% of App Store Apps Use iOS 14 Privacy Labels
A new report examines the adoption rate of iOS 14.5 App Tracking Transparency and App Store privacy labels.
Whoopi Goldberg Added to Voice Cast of Apple TV+ Animated Feature 'Luck'
Whoopi Goldberg is to voice a leader role in Luck, an animated feature heading to Apple TV+, in which she will play The Captain.
Hackers Stole McDonald’s Customer Information in Data Breach
On Friday, McDonald’s revealed it was the victim of a recent data breach, in which some customer information was stolen.
Bitcoin is Now Legal Tender in El Salvador
El Salvador recently become the first country to adopt Bitcoin as legal tender, other other counties in Latin America may follow suit.
By contrast, cryptocurrencies like bitcoin allow anyone with a mobile phone to send or receive funds, regardless of location. A software app known as a “wallet” manages the cryptocurrency as needed. Such wallets are safeguarded on phones and protected by passwords or biometric mechanisms like fingerprints.
This is what people mean when they talk about cryptocurrency’s decentralization. We don’t notice much in developed countries because we have no shortage of banks to choose from. But banks may be scarce in developing countries, with 70% of people in El Salvador being unbanked. With crypto, you no longer need a bank.
'See' Season Two Premieres August 27 on Apple TV+, Gets Season Three Renewal
Season two of ‘See’ will premiere on Apple TV+ on August 27, and the show has also been renewed for a third season.
![[Updated] UK Regulator Taking Closer Look at Apple and Google](https://www.macobserver.com/wp-content/uploads/2020/04/workheader-apple-google-logo.jpeg)