Enter our new international giveaway for a chance to win the brand new iPhone 16 Pro.
Claris Connect Gets New Third-Party App Integrations
Apple subsidiary Claris International has announced an expansion of Claris Connect, with new third-party app integrations.
Apple One Bundles Launching Friday
The various Apple One services bundles will become available on Friday, October 30, 2020, with Fitness+ following later this quarter.
Apple Beats Estimates with Q4 Results of $64.7B in Revenues and $0.73 EPS [Update]
Apple announced fiscal Q4 earnings on Thursday, with September quarter revenues of US$64.7 billion and earnings per share (EPS) of $0.73, both of which beat Wall Street consensus estimates.
Keep Your Space Warm and Cozy with This Heater's 360 Degree Rotation, 2-Speed Fan, and Remote Control: $32.99
We have a deal on the Plug N’ Heat Personal Space Heater. As the name says, it’s a heater designed specifically for your personal space. It features 360° rotation, a 2-speed fan, built-in constant temperature control, a digital readout, a 1 to 12-hour timer, and a remote control. It’s $32.99 through our deal.
Apple Maps in Italy Gets Transit Directions
Apple Maps now includes transportation directions across Italy. MacRumors reported that it works on systems like train, bus and tram in a number of cities now, instead of just Rome where the functionality originally rolled out.
The feature can be accessed by selecting the Transit tab or button in Apple Maps on iPhone, iPad, Mac, or Apple Watch. Supported modes of transportation include trains, buses, trams, and more in and between cities such as Milan, Naples, Turin, Palermo, Genoa, Florence, and Venice. Google Maps has supported transit directions for several years now, but Apple Maps is steadily catching up with detailed routing information.
Apple’s 85/15 Subscription Split Doesn’t Help Developers Much
Unlike Apple’s 70/30 split for in-app purchases, it offers an 85/15 split for subscriptions from customers that stay subscribed for at least a year. But Jacob Eiting writes how that doesn’t really help developers because of subscriber churn.
No matter how great an app is, subscribers are going to churn. Sometimes it’s because of a credit card expiring or some other billing issue. And sometimes it’s more of a pause, and the user comes back after a few months. But the majority of churn comes from subscribers who, for whatever reason, decide that the app just isn’t worth paying for anymore. If a subscriber churns before the 1-year mark, the developer never sees that 85% split. And even if the user resubscribes, Apple and Google reset the clock if a subscription has lapsed for more than 60 days.
FBI Warns of Ransomware Threat to US Healthcare System
The FBI, CISA, and HHS are issuing a joint alert to warn of the threat of ransomware attacks currently affecting U.S. healthcare systems.
MagSafe Fast Charging Won’t Damage Your iPhone 12 Battery
With the right charging brick, Apple’s MagSafe charging pad can quickly charge your iPhone 12 at an estimated 50% battery in 30 minutes. Although it was written last year, Clifford Colby’s article is a helpful investigation into fast charging. The short answer is that fast charging won’t damage your iPhone’s battery.
Damage is rare if everything’s well-managed inside. A battery’s management system closely monitors the two charge phases and drops the charging speed during the second phase to give the battery time to absorb the charge and avoid issues, which is why it can take 10 minutes to get those last few percentage points.
Apple's Search Engine Situation – TMO Daily Observations 2020-10-29
Bryan Chaffin and Andrew Orr join host Kelly Guimont to discuss Apple’s possible search aspirations and what that means for your data.
Apple Releases Unseen 'Long Way Up' Footage
Apple released previously unseen footage from the Apple TV+ series Long Way Up on Thursday. It’s 83 minutes of Ewan McGregor and Charley Boorman on their motorcycles shot from their point of view. The show is available to view now in the TV app.
OverDrive Announces Next Title in Digital Book Club Called ‘Reverie’
Big Library Read is a digital book club from eBook lender OverDrive. “Reverie” is the next book to read available for free through Libby from author Ryan La Sala. “All Kane Montgomery knows for certain is that the police found him half-dead in the river. He can’t remember anything since an accident robbed him of his memories a few weeks ago. And the world feels different—reality itself seems different. So when three of his classmates claim to be his friends and the only people who can tell him what’s truly going on, he doesn’t know what to believe or who he can trust. But as he and the others are dragged into unimaginable worlds that materialize out of nowhere—the gym warps into a subterranean temple, a historical home nearby blooms into a Victorian romance rife with scandal and sorcery—Kane realizes that nothing in his life is an accident, and only he can stop their world from unraveling.”
Simon Says is Bringing AI Transcription to DaVinci Resolve on Mac
Simon Says announced a partnership on Thursday to bring AI transcription to video editor DaVinci Resolve on macOS.
Germany Investigates Amazon, Apple Over ‘Brandgating’
Germany’s Federal Cartel Office is investing Amazon and Apple over “brandgating”, an Amazon policy that interferes with independent vendors.
NHS COVID-19 App to Send More Isolate Alerts After Google-Apple API Update
The UK’s NHS COVID-19 app, built using the Apple-Google framework, is set for an update that will send out more self-isolation alerts.
ExxonMobil Adds App Clips for Mobile iPhone Payments
ExxonMobil has added App Clips for mobile payments on iPhones, as well as QR codes for Google Pay users.
NSA Avoids Discussing Back Doors in Commercial Products
The U.S. National Security agency is dodging questions about back doors in commercial products and whether it’s continuing this practice. The article mentions Dual EC, a type of encryption algorithm the NSA tried to get ratified as a global standard. Why? Because they could easily crack it.
Juniper Networks got into hot water over Dual EC two years later. At the end of 2015, the maker of internet switches disclosed that it had detected malicious code in some firewall products. Researchers later determined that hackers had turned the firewalls into their own spy tool here by altering Juniper’s version of Dual EC.
And that’s the reason we oppose these kinds of back doors or “weaknesses on purpose” on Security Friday. If one group can easily crack it, so eventually will other groups.
Researchers Extract Intel CPU Encryption Key
Security researchers have successfully extracted the Intel CPU encryption key used to secure updates to the chip.
The key makes it possible to decrypt the microcode updates Intel provides to fix security vulnerabilities and other types of bugs. Having a decrypted copy of an update may allow hackers to reverse engineer it and learn precisely how to exploit the hole it’s patching. The key may also allow parties other than Intel—say a malicious hacker or a hobbyist—to update chips with their own microcode, although that customized version wouldn’t survive a reboot.
Of course, it’s the “other parties” to worry about. The key can be extracted from any chip that uses Intel’s Goldmont architecture. This is used for low-power chips like the Atom, Celeron, and Pentium brands.
Connecting COVID-19 Contact Tracing Apps Across Europe is Starting to Work
The first stage in making COVID-19 contact tracing apps work across different European countries has been achieved. The Scottish contact tracing app, which was built using the Apple/Google API, now also works in both Northern Ireland and Jersey.
The shared code is what also enables interoperability between apps used in New York, New Jersey, Pennsylvania and Delaware … The Scottish app should also work in England and Wales within the next few weeks, and then across Europe. This is all part of a wider European interoperability project intended to ensure that all contact tracing apps work across the continent. The app was developed by NearForm, which first created the Irish contact tracing app before rolling out versions for Scotland, Jersey, and the four US states. All the apps share the same core code.
iPad Air Might Make the Pro Obsolete
The reviews of the new iPad Air are starting to appear. Wired UK‘sis very positive, with author Jeremy White saying that it might make the Pro redundant for many users.
The inclusion of Apple’s A14 Bionic means you get the company’s latest chip that is in some respects even better than the one in the current iPad Pro. While to say this results in better performance than the Pro would be outright wrong, you do get a big bump in power – a 40 per cent increase in performance over the previous iPad Air, Apple says, and a 30 per cent uptick in graphics performance. Much like the new iPhone 12 series that also carries the A14, the Air is noticeably faster than its previous iteration. Battery life is of the usual iPad standard – top drawer. You will not need to charge the Air for days with light use, and if you do employ it as a PC replacement (which is certainly possible, especially with the keyboard) you will get many more hours out of it than a standard laptop. The faster 20W charger that comes in the box will help top things up if you do run low. It’s not all good news, though. Despite stealing so much from the Pro there is no LiDAR and no ultrawide camera.
Hints of an Apple Search Engine Resurface
A report in the Financial Times (which is paywalled so I’m linking to TechCrunch) claims that Apple could be creating an Apple search engine. Or, maybe the company is instead improving search for Siri or Spotlight.
Apple is now showing its own search results and linking directly to websites when users type queries from its home screen in iOS 14. For context, this is a behavior that has been known for a while as people have seen the feature pop up in beta versions of iOS. And the search volume being up on Apple’s crawler is something that Jon Henshaw of Coywolf had noted back in August.
I’m going with the “improving Siri and Spotlight” take. Apple isn’t known for creating products outside its ecosystem (Music on Android and Apple TV on other devices notwithstanding).
Apple Releases First Developer Beta of macOS Big Sur 11.0.1
The first beta of macOS Big Sur 11.0.1 has been released to developers, two weeks after the 11.0 beta 10 updates.
Confirmed: 'Ted Lasso' Will Return for Third Season
Apple has confirmed that Ted Lasso, the comedy starring Jason Sudeikis, will get a third season on Apple TV+.
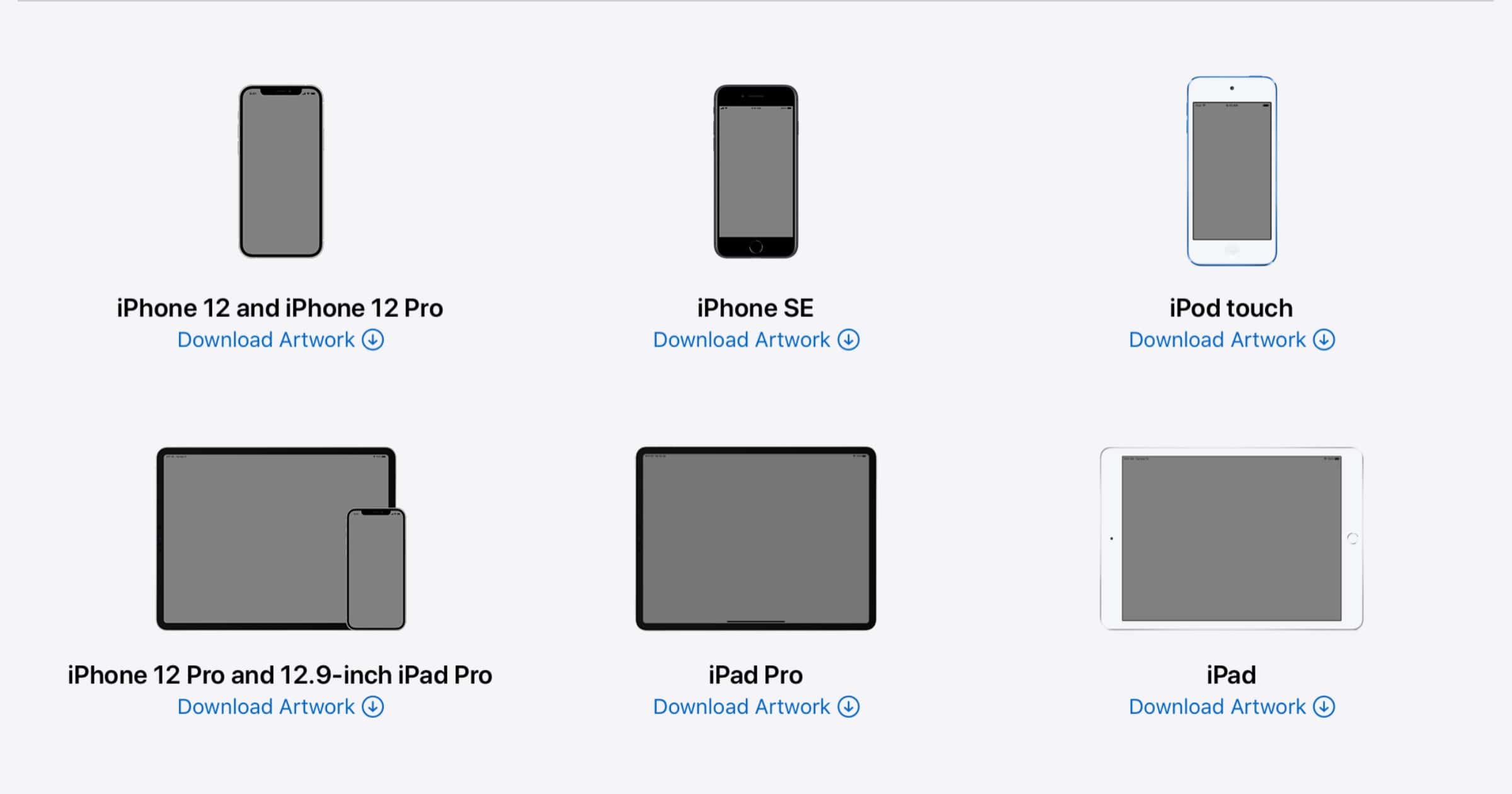
iPhone 12, iPhone 12 Pro Device Frames Now Available
You can now download iPhone 12 and iPhone 12 Pro device frames from Apple’s design resources website.
Instagram’s “Unlink Account” Feature is Deceiving
Instagram’s Unlink Account feature is deceiving, at least when it comes to Facebook. Since Instagram is a Facebook company your two accounts will forever be connected.
That’s because the wealth of data that Facebook collects through its multiple services is more than enough to properly identify users’ various accounts and link them to one another. Even in cases where a different name, email address, or device was used to create each account—be it a throwaway WhatsApp profile, stalker Instagram account, or joke Facebook profile—Facebook often is able to suss out who is actually behind the account and whether they have accounts on other Facebook-owned apps.


![Apple Beats Estimates with Q4 Results of $64.7B in Revenues and $0.73 EPS [Update]](https://www.macobserver.com/wp-content/uploads/2016/07/aapl-stock-graph-wide.jpg)