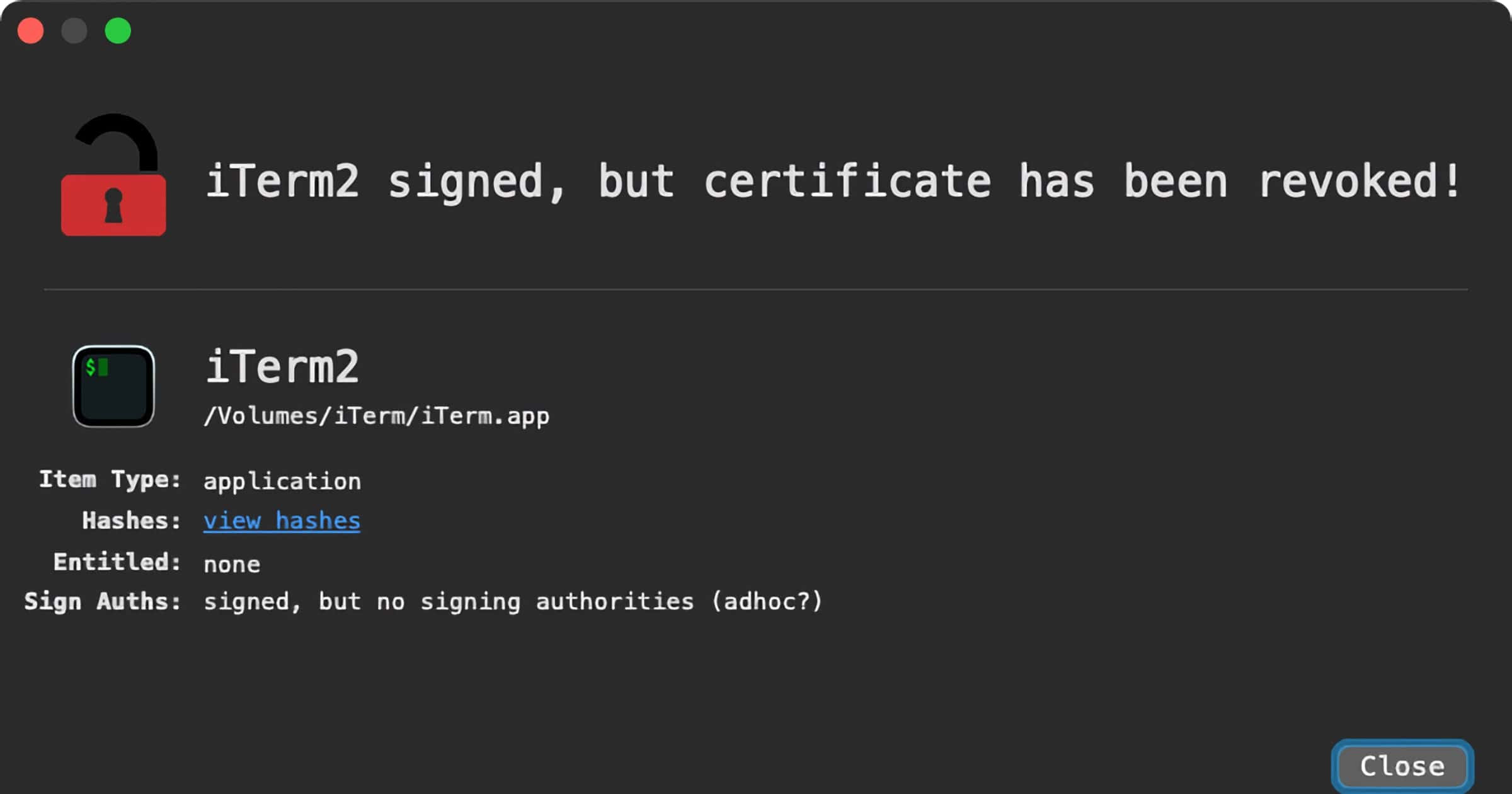
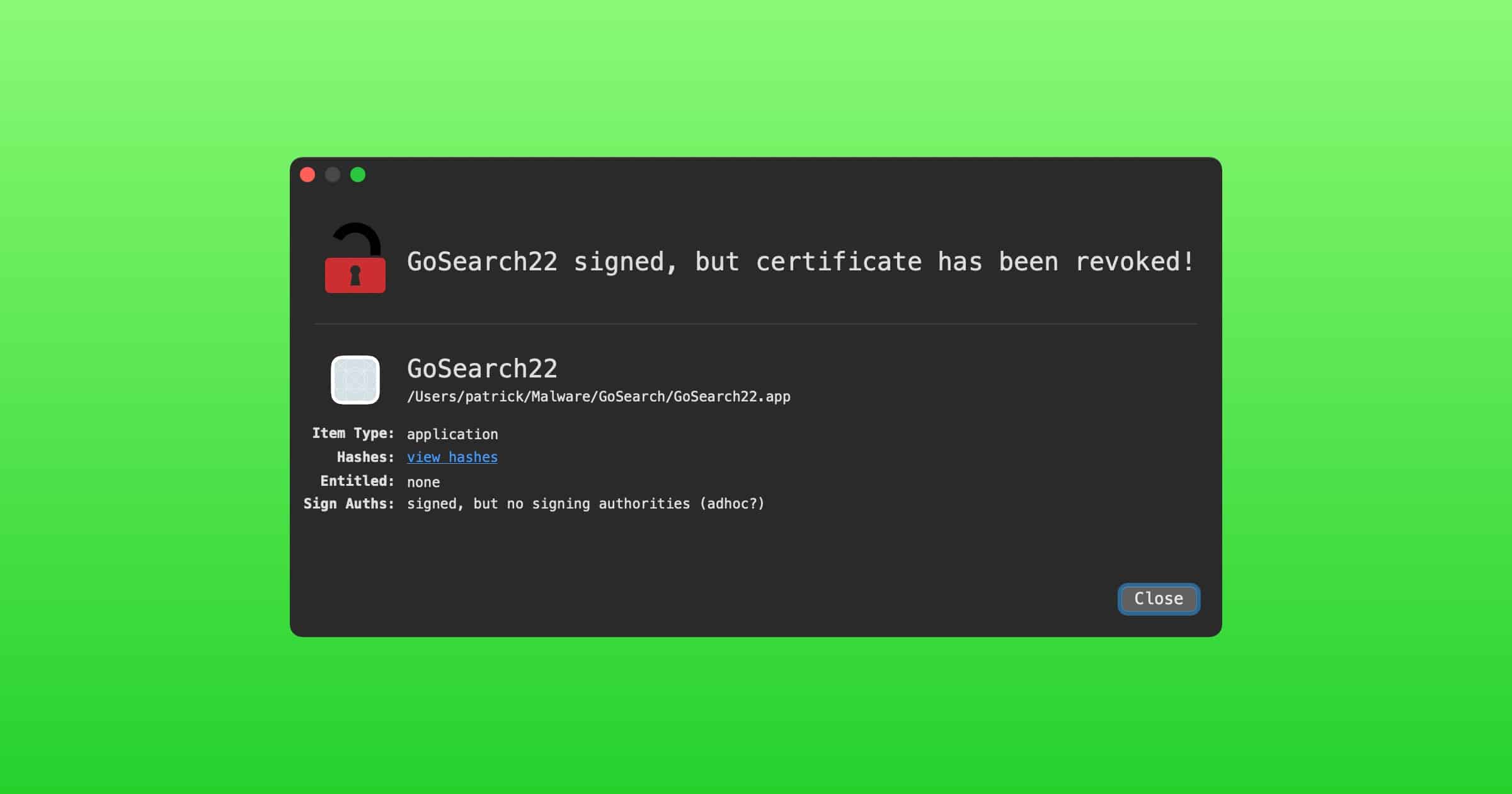
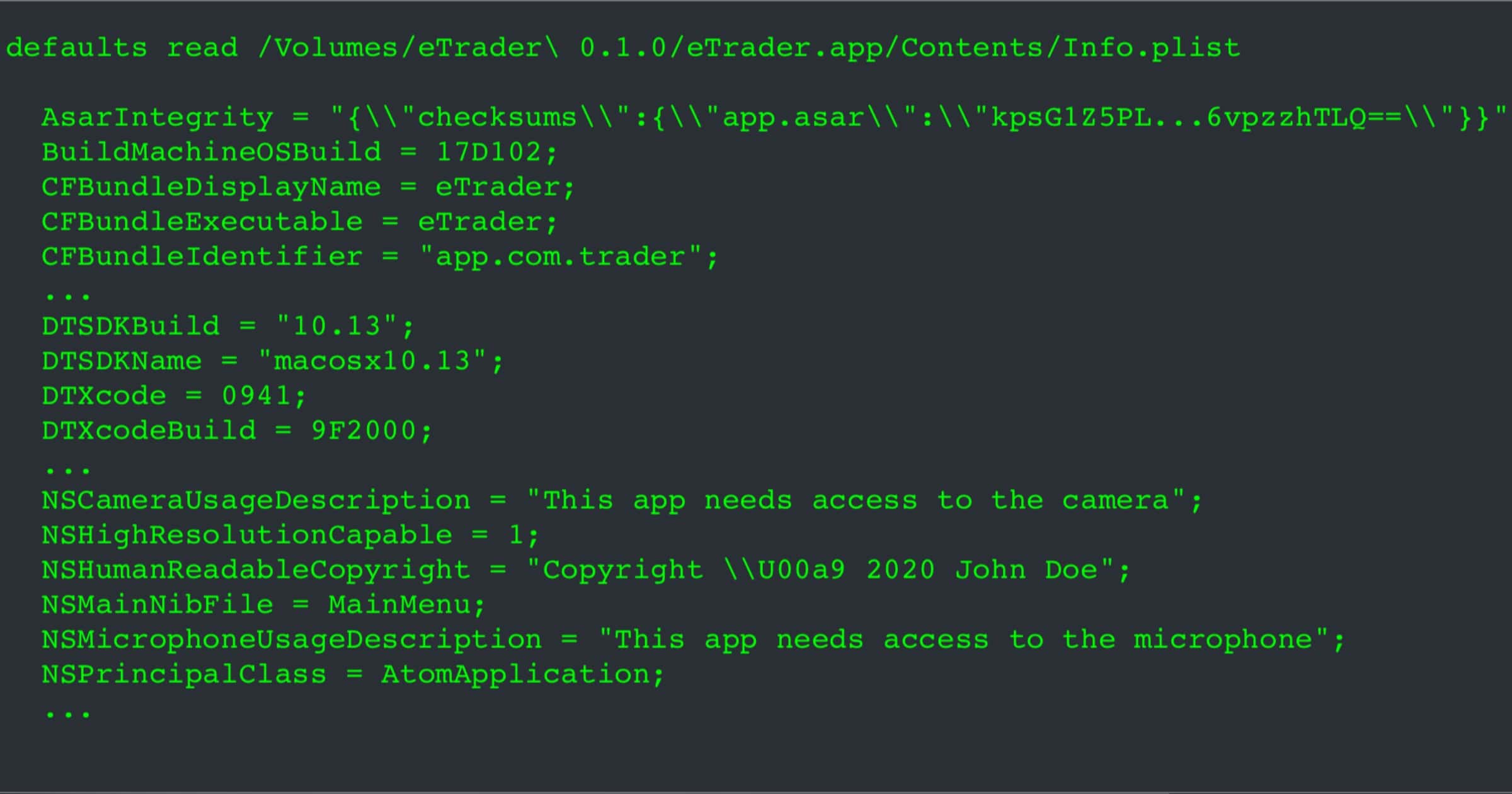
Security researcher Patrick Wardle made a list of the Mac malware we saw in 2021. It’s a timeline with information on each.
While the specimens may have been reported on before (i.e. by the AV company that discovered them), this blog aims to cumulatively and comprehensively cover all the new Mac malware of 2021 – in one place …yes, with samples of each malware available for download!
After reading this blog post, you should have a thorough understanding of recent threats targeting macOS. This is especially important as Apple continues to make significant inroads into the enterprise.