Andrew Orr and Kelly Guimont discuss Security Friday news and updates, including new phishing scams and sketchy wifi networks.
Security
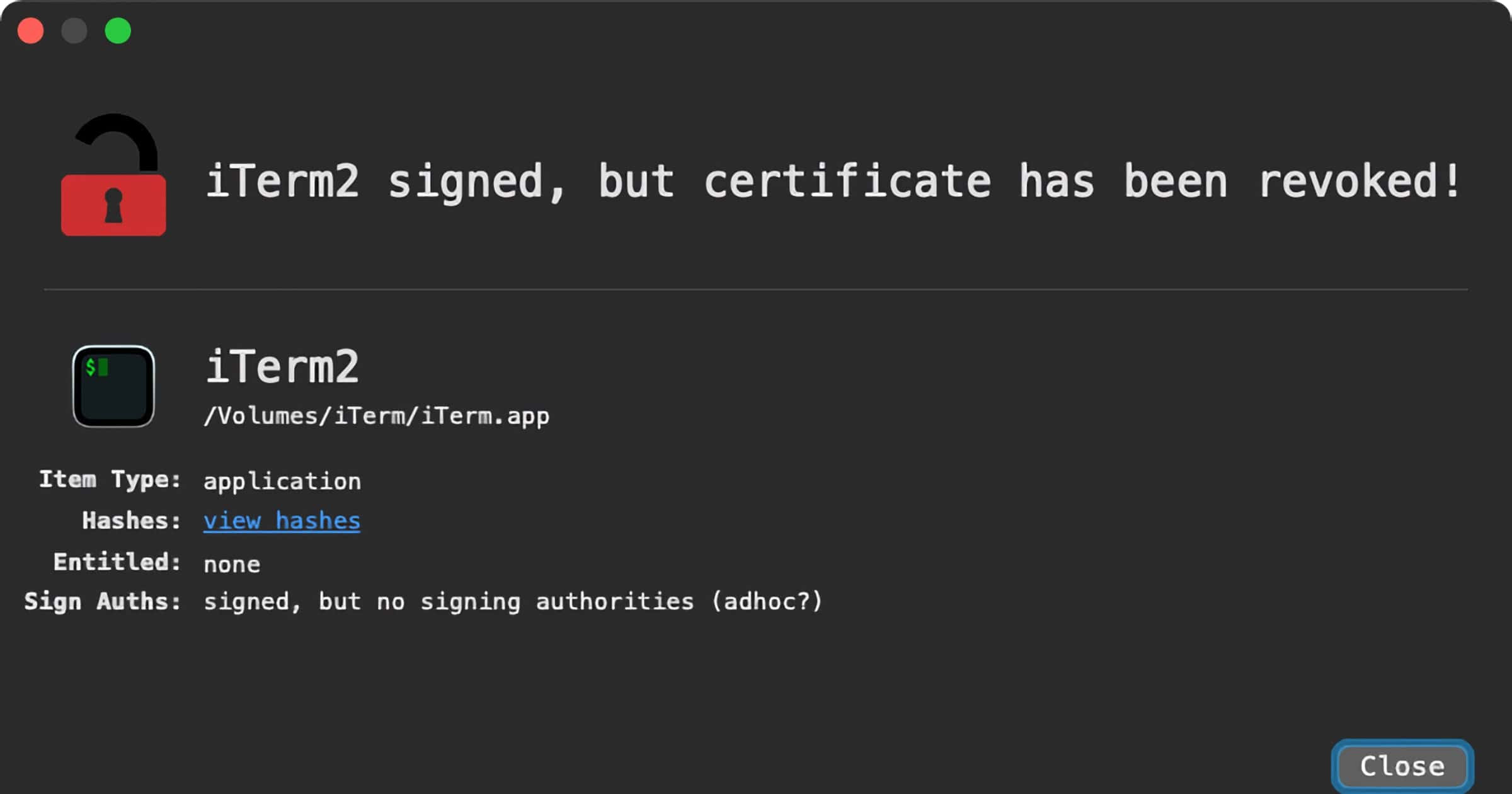
'OSX.ZuRu' Malware Spreads From Trojanized Apps via Sponsored Search Results
The latest Mac malware to be discovered is called OSX.ZuRu. It spreads via infected apps from sponsored search results.
The legitimate and the malicious iTerm2 application bundles contain a massive number of files, including several Mach-O binaries. Moreover, the malicious version appears largely benign (as is the case with most applications that have been surreptitiously trojanized). As such, it takes us a minute to uncover the malicious component.
Health Apps Must Warn Users of Data Breaches, Says FTC
The Federal Trade Commission issued a policy statement on Thursday. It says that health apps and wearable companies must warn their users of data breaches or face fines.
In a policy statement adopted during an open meeting, the Commission noted that health apps, which can track everything from glucose levels for those with diabetes to heart health to fertility to sleep, increasingly collect sensitive and personal data from consumers These apps have a responsibility to ensure they secure the data they collect, which includes preventing unauthorized access to such information.
Excellent news. Now they should make sure the fines are high enough to deter repeat offenders (cough T-Mobile).
PrivacyTools Website Rebrands as Privacy Guides (Update)
PrivacyTools.io is a website I’ve long used to learn about different types of private software. The team announced that it will rebrand as Privacy Guides.
Our work maintaining PrivacyTools has been extremely difficult of late without access to key assets such as the domain and without the participation of its founder.
This name change is the first step in this process of regaining our independence as a community. Eventually, we plan on creating a new legal organization designed around the community to ensure our long-term sustainability. This will take some careful planning and time to get right, but we’re confident we can prevent this from ever happening again, and keep us independent of any one team member.
Update: It appears there is some contention or intra-politics. The official PrivacyTools Twitter account said it is a project split, not a rebrand.
Is Your VPN Leaking Your IP Address?
Learn how to do a DNS Leak Test to find out if your VPN is actually secure with this quick tip from Mac Geek Gab 888.
Then, test For leaks here: https://www.dnsleaktest.com.
Inside Project Raven, a Team of Former NSA Analysts Who Worked for the UAE Government
Project Raven was a team that included more than a dozen former U.S. intelligence operatives recruited to help the United Arab Emirates engage in surveillance of other governments, militants and human rights activists critical of the monarchy. Reuters tells the story.
The operatives utilized an arsenal of cyber tools, including a cutting-edge espionage platform known as Karma, in which Raven operatives say they hacked into the iPhones of hundreds of activists, political leaders and suspected terrorists. Details of the Karma hack were described in a separate Reuters article today.
An interesting story. We know that iOS 14.8 patched a vulnerability used by the Pegasus spyware, but I haven’t heard much about Karma.
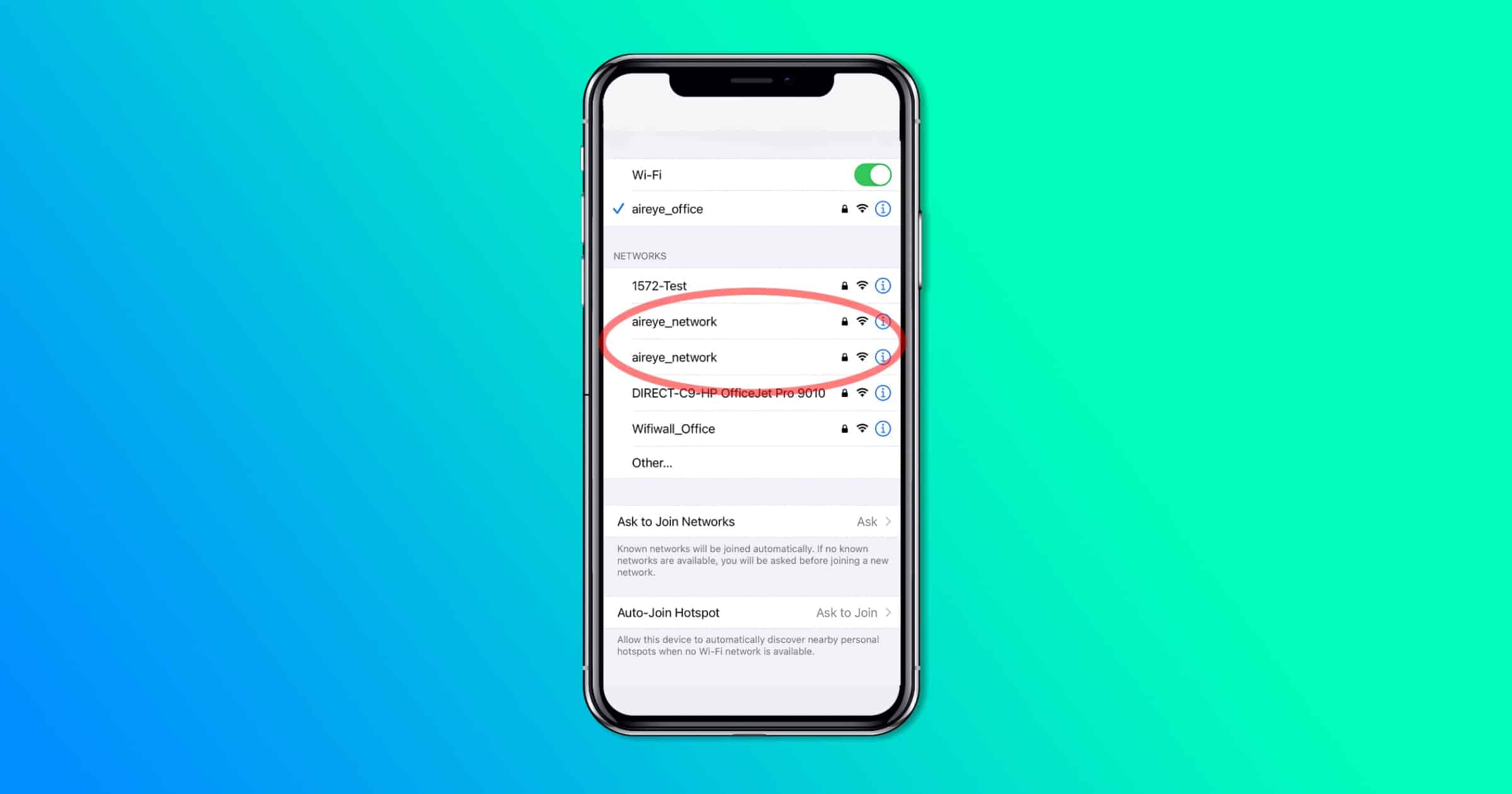
'SSID Stripping' Can Trick You Into Joining a Malicious Wi-Fi Network
Researchers have discovered a new type of network vulnerability dubbed SSID Stripping. It causes a network name to appear differently in a device’s list of networks, thus tricking people into joining a malicious network.
The SSID Stripping vulnerability affects all major software platforms – Microsoft Windows, Apple iOS and macOS, Android and Ubuntu. With SSID Stripping, it is possible to create a network name in a way that its display only shows a prefix that is similar to a legitimate network name (e.g. the corporate network name) while the actual network name includes the additional specially crafted information.
Researchers Uncover a Phishing Kit Used by Two Criminal Gangs
Led by Noam Rotem, vpnMentor’s research team has discovered two separate criminal gangs using slightly altered versions of the same phishing kit to scam people across the globe.
It appears the phishing kit was being used to target people mostly living in Israel and France by two separate criminal gangs. However, we believe these two groups operate phishing websites and SMS operations based on the same phishing kit, possibly obtained from the same source. In addition, at least one of them is potentially affiliated with the OpIsrael political hacking group.
Security Researcher Finds CloudKit Bug That Broke Apple Shortcuts
Security researcher Frans Rosén wrote about a CloudKit bug he accidentally found that affected Apple News, Shortcuts, and iCrowd+.
On the third day, I started to connect the dots, realized how certain assets connected to other assets, and started to understand more how things worked. This is when some of the first bugs popped up, finally restoring my self-esteem a bit, making me more relaxed and focused going forward.
I dug up an old jailbroken iPad I had, which allowed me to proxy all content through my laptop. I downloaded all Apple owned apps and started looking at the traffic.
Apple Releases Security Update for macOS Big Sur, macOS Catalina
Alongside its security updates for watchOS, iOS, and iPadOS, Mac users are receiving a macOS Big Sur 11.6 update and one for macOS Catalina.
Coinbase Adds Option for Two-Factor Authentication Security Keys
Cryptocurrency exchange Coinbase announced an important update to its mobile app. Users can now secure their accounts with a two-factor authentication security key.
Hardware security keys are encrypted USB devices that you can register with your Coinbase account as a strong form of physical 2FA. Once registered, you’ll be prompted for your security key when logging in. You then plug in the key, or tap via near field communication (NFC), to your mobile device to securely access your account.
Apple Releases Security Updates With iOS 14.8 Out Today
Apple released iOS | iPadOS 14.8 on Monday with security fixes, along with watchOS 7.6.2 for the Apple Watch Series 3 and later.
'GetHealth' Leaks Apple HealthKit Data With 61 Million Records
GetHealth, a health and wellness company in New York City, leaked data from a non-password protected database with over 61 million records.
Security Friday and Epic Updates – TMO Daily Observations 2021-09-10
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and the latest in the Apple v Epic lawsuit.
Security Researchers are Fed Up With Apple's Bug Bounty Program
For five years Apple has invited ethical hackers to break into its products to look for flaws. But these security experts are tired of the program.
The best programs support open conversations between the hackers and the company. Apple, already known for being tight-lipped, limits communication and feedback on why it chooses to pay or not pay for a bug, according to security researchers who have submitted bugs to the bounty program and a former employee who spoke on the condition of anonymity because of a nondisclosure agreement.
Microsoft President Brad Smith Says Government Agencies Need to Share Data
Microsoft President Brad Smith says intelligence agencies need to share information to better protect the nation against cyberattacks.
Repeatedly in late 2020 we found people in federal agencies asking us about information in other parts of the government, because it was easier to get it from us than directly from other federal employees. A culture of holding information tightly is so ingrained in the government that even its contracts with us forbid us from letting one part of the government know that another part has been attacked.
Germany Secretly Purchased NSO Group Spyware 'Pegasus'
A report reveals that Germany’s Federal Criminal Police Office (BKA) had purchased the Pegasus spyware to monitor suspects.
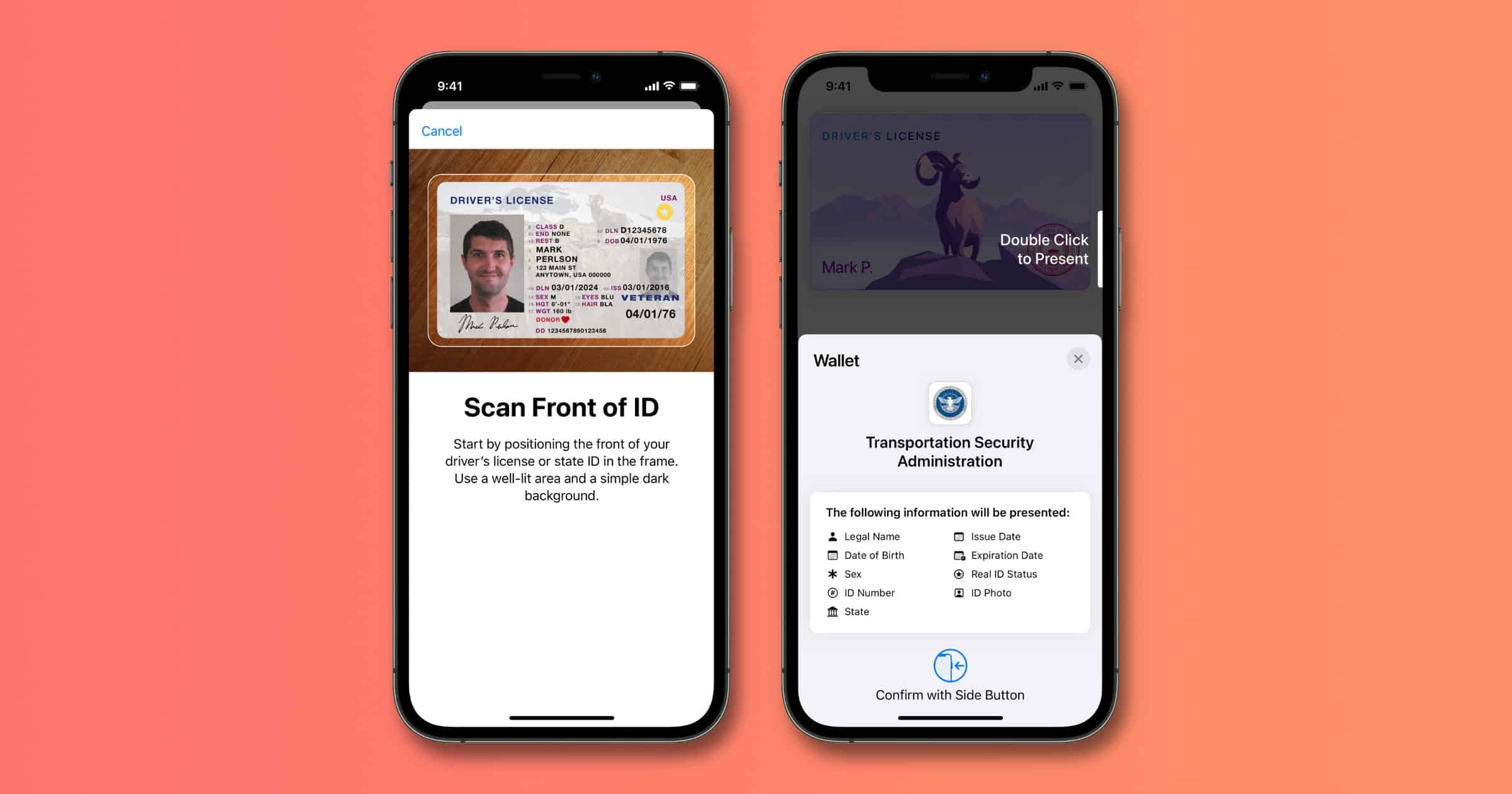
Here are the First States to Support iOS 15 Digital IDs
On Wednesday Apple revealed which U.S. states are the first to support storage of IDs within Apple Wallet in iOS 15 and watchOS 8.
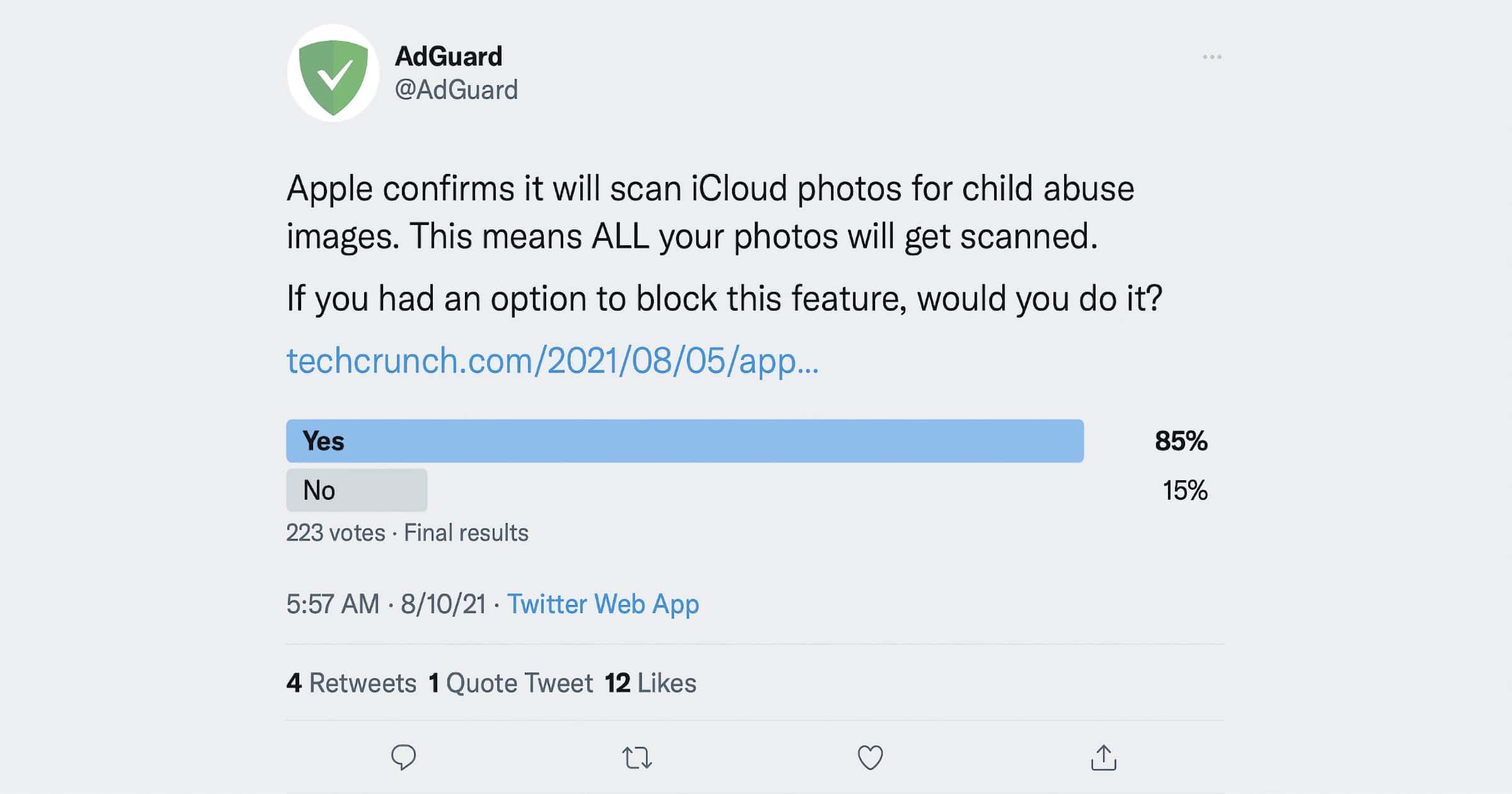
AdGuard: 'People Should be Worried About Apple CSAM Detection'
Adblocking company AdGuard is the latest to offer commentary on Apple’s controversial decision to detect CSAM in iCloud Photos. The team ponders ways to block it using their AdGuard DNS technology.
We consider preventing uploading the safety voucher to iCloud and blocking CSAM detection within AdGuard DNS. How can it be done? It depends on the way CSAM detection is implemented, and before we understand it in details, we can promise nothing particular.
Who knows what this base can turn into if Apple starts cooperating with some third parties? The base goes in, the voucher goes out. Each of the processes can be obstructed, but right now we are not ready to claim which solution is better and whether it can be easily incorporated into AdGuard DNS. Research and testing are required.
Security Friday: News, Leaks vs Breaches, Metadata – TMO Daily Observations 2021-08-27
Andrew Orr joins host Kelly Guimont to discuss data leads vs data breaches, security news, and what metadata actually entails.
Chinese Hackers May be Stealing Data to Feed an Artificial Intelligence
Dina Temple-Raston of NPR published a fascinating investigation regarding the Microsoft Exchange attack earlier in 2021.
Officials believe that the breach was in the service of something bigger: China’s artificial intelligence ambitions. The Beijing leadership aims to lead the world in a technology that allows computers to perform tasks that traditionally required human intelligence — such as finding patterns and recognizing speech or faces.
US Air Force Contract Aims to Improve Blockchain Security
The United States Air Force will use Constellation’s Hypergraph Network to provide data security with the Department of Defense’s commercial partners.
Constellation said it had been working with Kinnami Software Corporation to develop an end-to-end data security solution using blockchain encryption and distributed data management for the United States Transportation Command, Air Mobility Command’s 618th Air Operations Center, and a Civil Reserve Air Fleet partner. According to the platform, its goal is to securely exchange data with commercial partners on missions involving the operations of aircraft and ships under contract to the Department of Defense, or DoD.
Data Leak From Chinese Company 'EskyFun' Affects 1 Million Gamers
The research team at vpnMentor discovered an unsecured server from Chinese mobile gaming company EskyFun. It exposed data for over a million Android gamers.
The resulting records contained a lot of sensitive information, including: IP address, IMEI number, Mobile application package doing the tracking, Device screen size – whether a device is ‘rooted’*, Device model, Phone number (if any), Platform (Android/iOS), NetType (WiFi or cellular), Events (open,login,level_up, etc).
Not so fun anymore.