Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates, including data privacy and how to encrypt a pdf on your Mac.
Security
Over 170 Android Cryptocurrency Apps are Scams
A recent report shows that Android has a cryptocurrency scam problem. These apps claim to help you mine Bitcoin “in the cloud.”
The apps work by offering a virtual dashboard that lets you monitor the cryptocurrency mining rate. The same dashboard shows you how much virtual coin has been generated. However, Lookout examined the computer code in the apps along with the network traffic, and found the coin balance displayed was actually fictitious.
Kaspersky’s Password Manager Created Weak Passwords
Kaspersky Password Manager was caught creating weak passwords that were easy to brute force attack.
We will first see an example of a good password generation method, to explain after why the method used by Kaspersky was flawed, and how we exploited it. As we will see, passwords generated by this tool can be bruteforced in seconds.
After a bit less than two years, this vulnerability has been patched on all versions of KPM. Vulnerability has been assigned CVE-2020-27020.
New Ransomware ‘Tsunami’ Destroying Supply Chains
The REvil hacking team is back with new malware. Brand new, still developing, but their ransomware called “Tsunami” is wreaking havoc.
The software in question, Kaseya VSA, is popular among so-called managed service providers, which provide IT infrastructure for companies that would rather outsource that sort of thing than run it themselves. Which means that if you successfully hack an MSP, you suddenly have access to its customers. It’s the difference between cracking safety deposit boxes one at a time and stealing the bank manager’s skeleton key.
Europe Chief Tells Apple Not to Use Privacy to Limit Competition
Margrethe Vestager, the European Commission’s VP for technology, says that Apple shouldn’t use privacy and security to limit competitors.
Russian Spies Abuse VPNs to Target Organizations
On Thursday, U.S. and British authorities said that Russia’s military spy agency is using VPNs and Tor to attack governments and private sector targets.
The advisory did not identify any of the targets by name, saying only that they were mainly in the United States and Europe and included government offices, political parties, energy companies, law firms and media organizations.
The Russian Embassy in Washington did not immediately return a message seeking comment. Russian officials routinely reject allegations that they employ hackers to spy on rival nations.
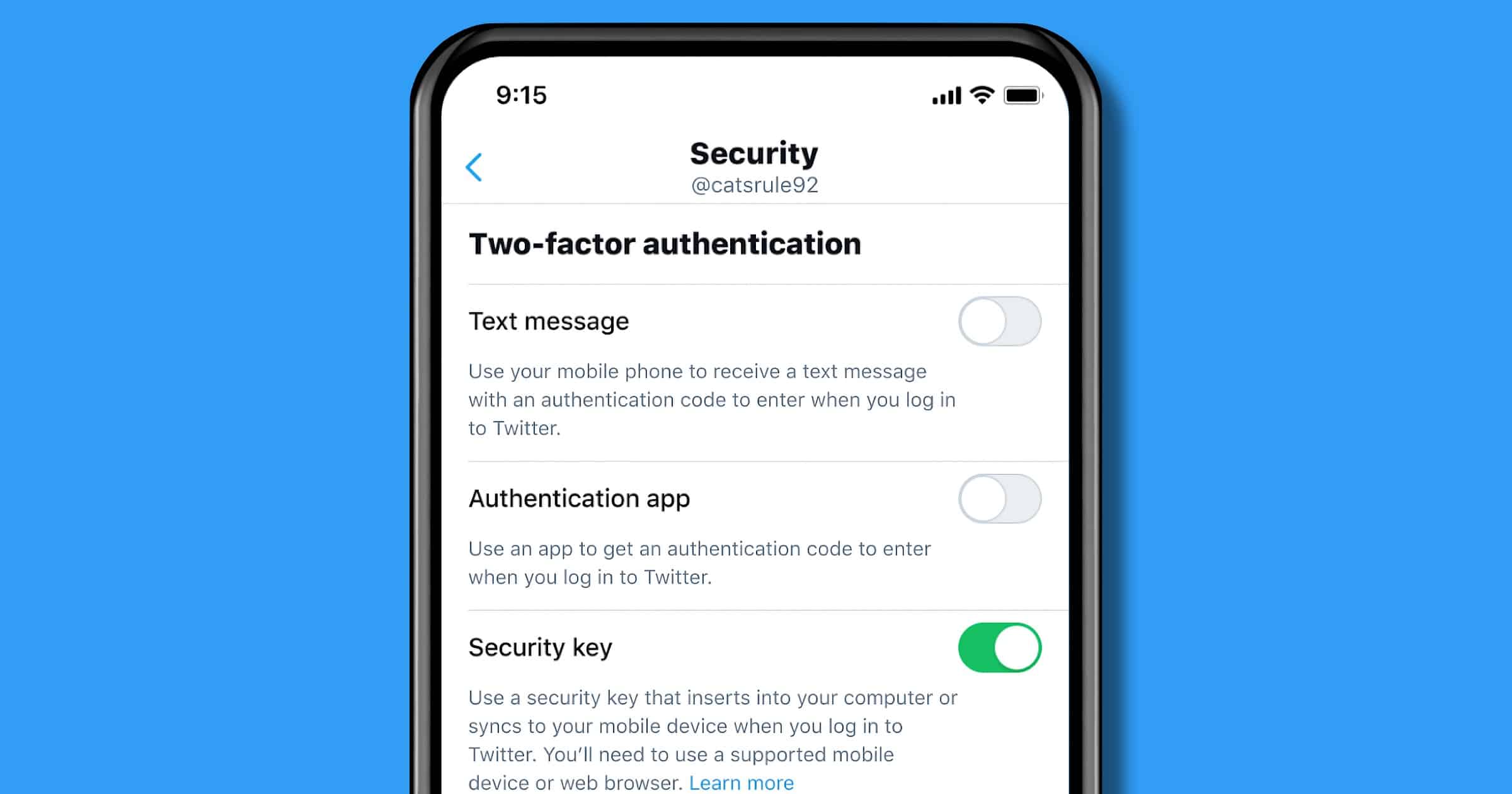
Twitter Lets You Use a Security Key as Only 2FA Option
Twitter announced on Wednesday that it will let people use a security key as their only form of two-factor authentication.
Today, we’re adding the option to use security keys as your sole 2FA method — meaning you can enroll one or more security keys as the only form of 2FA on your Twitter account without a backup 2FA method. We know this is important to people because not everyone is able to have a backup 2FA method or wants to share their phone number with us.
Cryptomator’s Major 2.0 Upgrade is Available in TestFlight, Now Open Source
File encryption app Cryptomator is readying a major 2.0 upgrade and interested users can test the beta within Apple’s TestFlight app on iOS.
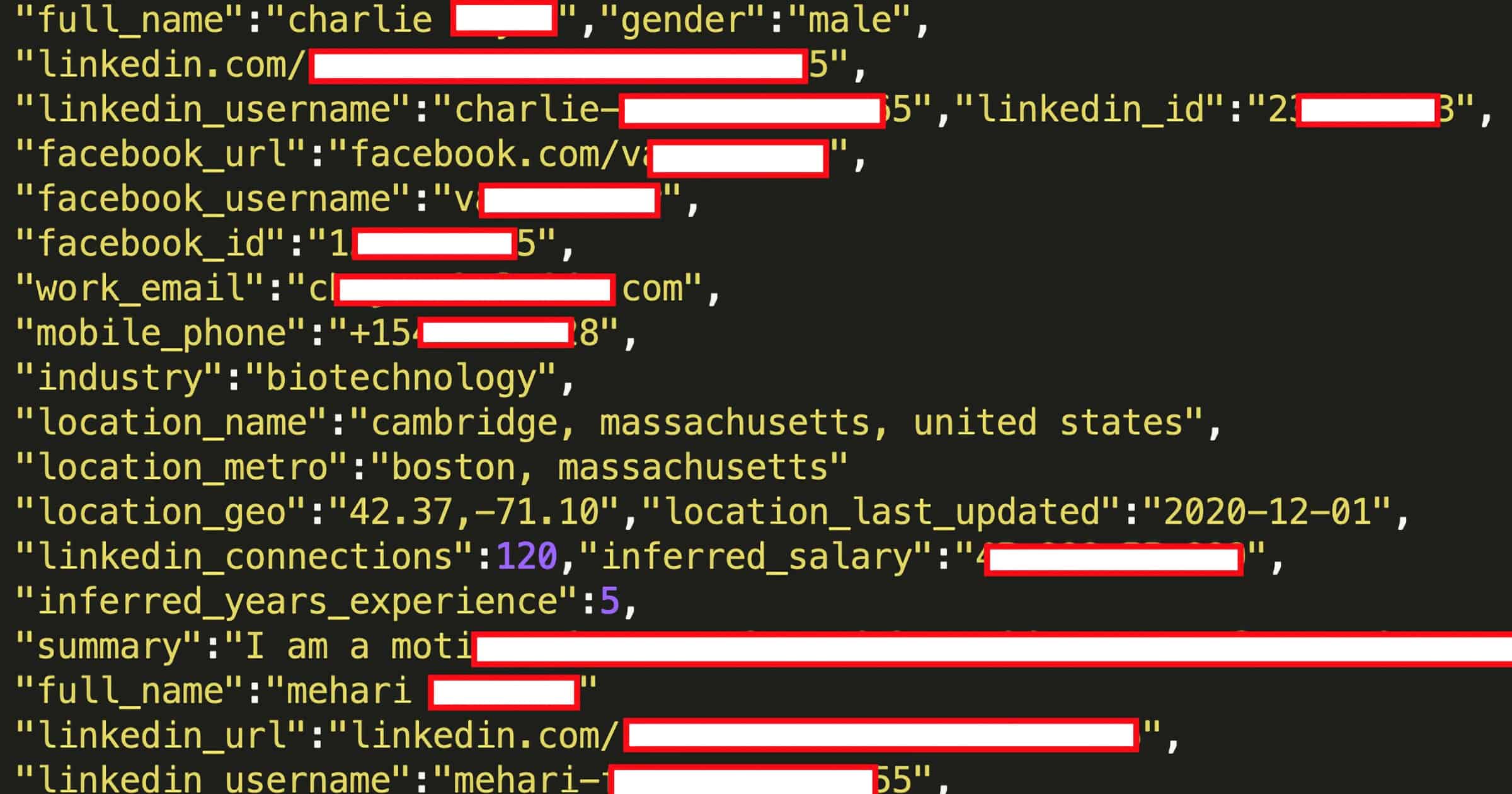
Hackers Sell Personal LinkedIn Data From Leak Affecting 700M Users
Hackers are selling the personal information of over 700 million LinkedIn users. Here are the data types that were leaked:
Email Addresses; Full names; Phone numbers; Physical addresses; Geolocation records; LinkedIn username and profile URL; Personal and professional experience/background; Genders; Other social media accounts and usernames
On June 22nd, a user of a popular hacker forum advertised data from 700 Million LinkedIn users for sale. The user of the forum posted a sample of the data that includes 1 million LinkedIn users.
Security Friday: Data Breaches and Password Migration – TMO Daily Observations 2021-06-25
Andrew Orr joins host Kelly Guimont for Security Friday news and updates, including a massive data breach, and how to import/export passwords.
Web Hosting Service 'DreamHost' Leaked 814 Million Records of Customer Data
A database owned by Dreamhost was found unsecured and publicly accessible online. It contained 814 million entries of exposed usernames, display names, and emails for WordPress accounts.
The exposed log files contained what appears to be 3 years of records that range from 3/24/2018 to 4/16/2021 and each contained information about WordPress accounts hosted or installed on DreamHost’s server and their users. On May 4th a DreamHost representative acknowledged the discovery and informed us that the finding was being passed on to their legal team.
Update: DreamHost reached out to say that none of those records contain data that would have allowed access to DreamHost accounts. They consist entirely of entries that include object update records, error reports, and log entries. Data from just 21 individual websites were involved. More information can be found on its website.
How to Unlock and Extract Data From iPhones Using GrayKey
Instructions for iPhone cracking tool GrayKey have surfaced online and it appears they were written by the San Diego Police Department.
Cryptee's Cloud Document Editor Gets Mobile Interface
Cryptee announced version 3.1 to the document editor for its encrypted cloud platform. The UI has been redesigned for mobile users.
Encrypted Email Service ‘Tutanota’ Desktop Apps Exit Beta
Tutanota is an end-to-end encrypted email service and its desktop clients exit beta after two-and-a-half years.
Security Friday: Data Leaks and Drilling – TMO Daily Observations 2021-06-18
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates, including a way to obliterate that iPhone data once and for all.
New Malware Infects Software Pirates and Blocks The Pirate Bay
Andrew Brandt reports on a new malware campaign that isn’t like your typical malware. This one blocks people from accessing many popular pirating websites.
We weren’t able to discern a provenance for this malware, but its motivation seemed pretty clear: It prevents people from visiting software piracy websites (if only temporarily), and sends the name of the pirated software the user was hoping to use to a website, which also delivers a secondary payload.
Looks like this is aimed more towards Windows users. The malware takes the form of .EXE executables, and may display a message saying the victim is missing an important .DLL file.
The Story of BonziBuddy and its Company’s Demise
In the third episode of Kernel Panic, Mashable tells the story of one of the first virtual assistants known as BonziBuddy.
Behind the facade of that friendly gorilla, Bonzi Software, the company responsible for BonziBuddy, was collecting private information and contacts from the unsuspecting internet users who downloaded it — and bombarding them with ads and pop-ups that Bonzi would profit from.
Harry Potter and the Curse of Bonzi. If you ever downloaded this purple ape and noticed strange things start to happen, let us know in the comments. Maybe your browser was full of ads, or maybe he whispered into your ear at night, encouraging you to commit securities fraud.
Data Leak Exposes Customer Records With CVS Health
CVS Health recently leaked approximately one billion user records that include email addresses, user IDs, and metadata. The information was discovered in a non-password protected database.
CVS Health acted fast and professionally to secure the data and a member of their Information Security Team contacted me the following day and confirmed my findings and that the data was indeed theirs. I was informed that this was a contractor or vendor who managed this dataset on behalf of CVS Health, but it was confidential as to who the vendor was.
Why You Should Drill a Hole Into Your iPhone or iPad
Over the weekend, Nikita Mazurov for The Intercept reminds us that a good way to wipe our iDevices is to drill a hole through it.
If you can’t access your device, the most careful approach to wiping it is to destroy the flash memory chip that houses your data. This way you don’t have to lose sleep if you didn’t use a strong passcode, or worry about a forensics vendor being able to recover any of your personal information.
Beware of Malicious PDFs When Using Web Search
The team behind the SolarMarker malware have been loading it into PDFs and using web search to trick people into downloading them.
Gaming Company ‘EA’ Suffers Data Breach of Game Code
Electronic Arts is the latest company to have information stolen in a data breach. It includes the source code for FIFA 21, the Frostbite engine, and proprietary frameworks and SDKs.
We are investigating a recent incident of intrusion into our network where a limited amount of game source code and related tools were stolen. No player data was accessed, and we have no reason to believe there is any risk to player privacy.
Following the incident, we’ve already made security improvements and do not expect an impact on our games or our business. We are actively working with law enforcement officials and other experts as part of this ongoing criminal investigation.
Hackers Stole McDonald’s Customer Information in Data Breach
On Friday, McDonald’s revealed it was the victim of a recent data breach, in which some customer information was stolen.
JBS USA Pays $11 Million in Ransom After Cyberattack
On Thursday, meat supplier JBS said it paid US$11 million after ransomware attack stopped its operations.
In consultation with internal IT professionals and third-party cybersecurity experts, the company made the decision to mitigate any unforeseen issues related to the attack and ensure no data was exfiltrated.
I wonder if the FBI will recover this ransom as well, like the Colonial Pipeline money.
iCloud Keychain Gets Time Based One Time Passwords
In one of Apple’s videos dedicated to developers, the company revealed a new feature that wasn’t mentioned in the WWDC 2021 keynote.