Yubico is recalling its line of YubiKeys, tools used for two-factor authentication that generate one-time passcodes.
Security
Google Builds HTTPS Directly Into Top Level Domains
More websites have encrypted their traffic than ever, but there is a loophole. Some use a mixture of HTTPS and unsecure HTTP. Google is closing this by building HTTPS protection directly into certain top level domains.
Which means that today, when you register a site through Google that uses “.app,” “.dev,” or “.page,” that page and any others you build off it are automatically added to a list that all mainstream browsers, including Chrome, Safari, Edge, Firefox, and Opera, check when they’re setting up encrypted web connections. It’s called the HTTPS Strict Transport Security preload list, or HSTS, and browsers use it to know which sites should only load as encrypted HTTPS automatically, rather than falling back to unencrypted HTTP in some circumstances. In short, it fully automates what can otherwise be a tricky scheme to set up.
Sign in with Apple, Telegram Attacked – TMO Daily Observations 2019-06-13
Charlotte Henry and Andrew Orr join host Kelly Guimont to discuss Google approving of Sign in with Apple, and China’s attack on Telegram.
Governments Are Terrible at Securing Data
It absolutely infuriates me when agencies like the FBI, and governments like Australia, the U.S., Germany, and more want us to break encryption or circumvent it with a back door. As Mathew Gault writes, they are completely inept at securing data. Even the NSA, which likes to think it’s the “world leader in cryptology” got hacked.
Regular phone and internet users remain vulnerable, forced to take individual protective measures, like a poor wage-worker without health insurance who’s told to secure her nest egg by cutting out morning lattes.
News+: Bad Behavior in the VPN Industry
Max Eddy reviews VPNs for PCMag. Although he believes most vendors have good intentions, he highlights several examples of bad behavior in the VPN industry.
From my experience working with VPNs, I can say with certainty there is a culture of sabotage and paranoia among some vendors. Anonymous dumps of damning information about one VPN vendor get blamed on another VPN vendor. Tips come in suggesting that corporate ownership is tied to the Russian mafia or some other criminal operation. Commentators hold up one VPN review site as an example of rectitude; others say the same site is secretly run by a VPN vendor with an agenda. When there is this much disinformation and counter-disinformation (which may also be disinformation), it’s impossible to tell who is telling the truth.
Before I came to The Mac Observer, one of my freelancing gigs was writing for a VPN company. I saw some of the same things as Mr. Eddy. In both privacy and security circles, there is a tint of paranoia and conspiracy thinking, at least with some people.
This is part of Andrew’s News+ series, where he shares a magazine every Friday to help people discover good content in Apple News+.
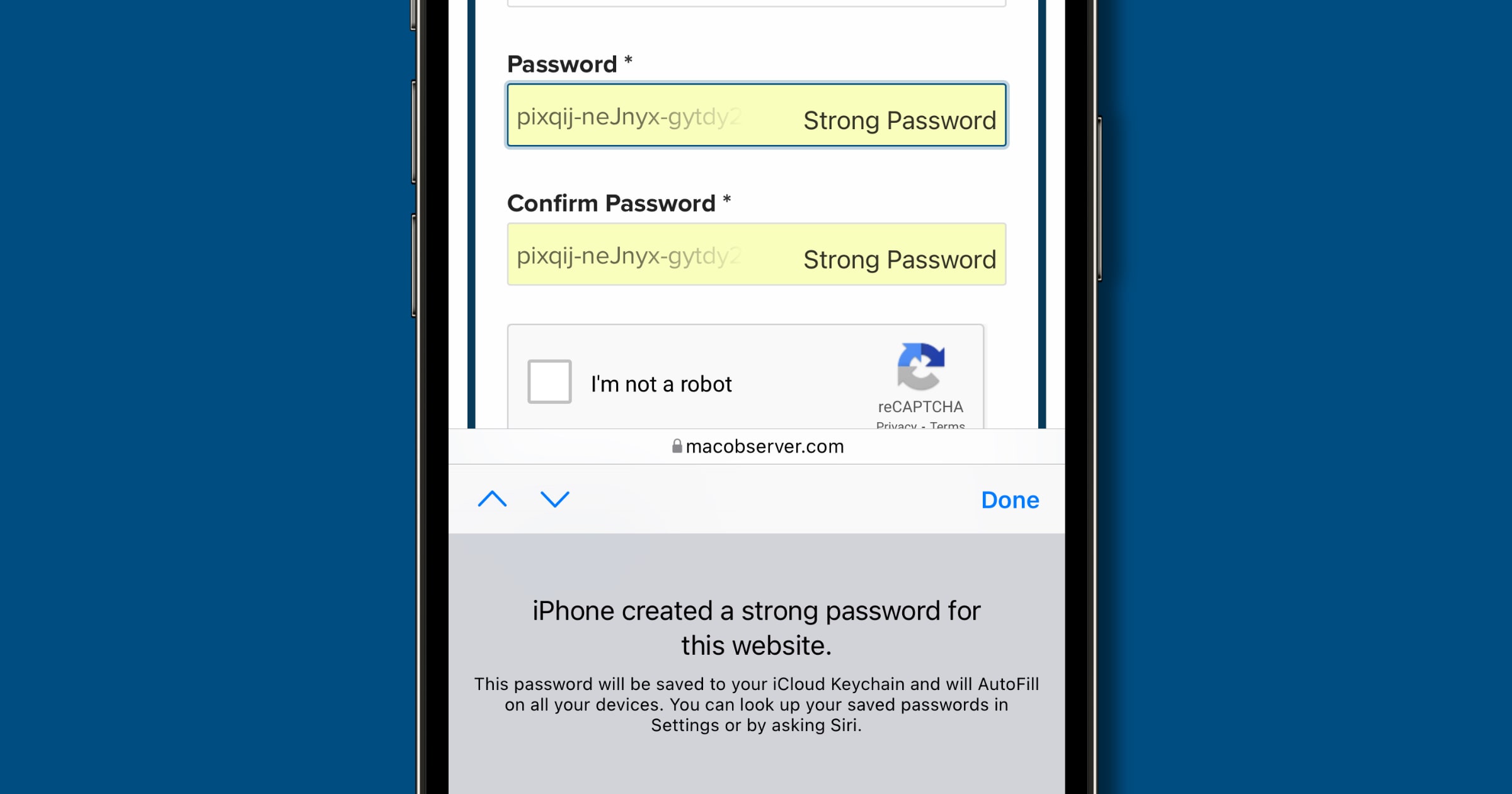
iOS: How to Manually Configure iCloud Keychain
Unlike a traditional password manager, we don’t have a lot of control over iOS password generation. But there is a manual workaround that lets us configure iCloud Keychain a bit.
Apple Deprecates SHA-1 in iOS 13 and macOS Catalina
Apple is deprecating SHA-1, an old security standard, in iOS 13 and macOS Catalina. This is good news since we now have the more secure SHA-2 and SHA-3.
Two Thirds of iOS Apps Disable App Transport Security
Security firm Wandera scanned over 30,000 iOS apps and found that 67.7% of them disable App Transport Security on purpose.
Apple Thwarts Sensor Fingerprinting With iOS 12.2
A study called “SensorID: Sensor Calibration Fingerprinting for Smartphones” examined sensor fingerprinting techniques against smartphones. It found that Micro Electro Mechanical Systems (MEMS) are inaccurate in small ways that make them unique. But Apple thwarted this technique in iOS 12.2 and used the researchers’ suggestion to add random noise to the analog-to-digital converter output and removing default access to motion sensors in Safari.
We demonstrate that our approach is very likely to produce globally unique fingerprints for iOS devices, with an estimated 67 bits of entropy in the fingerprint for iPhone 6S devices. In addition, we find that the accelerometer of Google Pixel 2 and Pixel 3 devices can also be fingerprinted by our approach.
Bypassing macOS Security With Synthetic Clicks
Security researcher Patrick Wardle found he can bypass macOS security by using synthetic clicks built with AppleScript.
Typically apps are signed with a digital certificate to prove that the app is genuine and hasn’t been tampered with. If the app has been modified to include malware, the certificate usually flags an error and the operating system won’t run the app. But a bug in Apple’s code meant that that macOS was only checking if a certificate exists and wasn’t properly verifying the authenticity of the whitelisted app.
Mr. Wardle refers to this as a “second stage” attack, because the hacker or malware needs access to your Mac to exploit this bug.
Here Are The Top 20 Most Common iPhone Passcodes
Security expert Tarah Wheeler recently tweeted a list of the top 20 most common iPhone passcodes. These are all four-digit passcodes.
AirPort Updates, WWDC Plans – TMO Daily Observations 2019-05-31
Dave Hamilton and Andrew Orr join host Kelly Guimont to discuss AirPort Base Station updates, and look ahead to WWDC plans and coverage.
AirPort Base Stations Get 7.9.1 Firmware Update
Although Apple discontinued its line of AirPort base stations (routers), it recently released a firmware update, version 7.9.1. It fixes several security issues, one of which seems especially bad.
Impact: A base station factory reset may not delete all user information
Description: The issue was addressed with improved data deletion.
CVE-2019-8575: joshua stein
GCHQ Officials' Encryption-Bypassing Idea Criticised in Letter Signed by Apple
Apple, Google, Microsoft, and WhatsApp signed an open letter criticizing proposals to bypass encryption made by GCHQ officials.
Sneak Peek of Cloudflare Warp VPN Shows Split Tunneling
Cloudflare Warp VPN is a new service the company announced back in April. Currently there is a waiting list, but Andrew got his hands on some screenshots.
Flipboard Suffers Data Breach, Emails All 145M Users
Flipboard revealed that an “unauthorized party” accessed its database between June 2, 2018 and March 23, 2019, as well as between April 21-22, 2019.
1Password 7.3 Updates the Mini Menu Bar Tool
1Password 7.3 for macOS brings a new “filling brain” as well as an updated 1Password mini that lives in the menu bar.
Inside Apple’s Secure Enclave Stress Testing Efforts
The Independent recently published an interview with Craig Federighi, talking about privacy and Apple chips.
Those chips are here to see whether they can withstand whatever assault anyone might try on them when they make their way out into the world. If they succeed here, then they should succeed anywhere; that’s important, because if they fail out in the world then so would Apple. These chips are the great line of defence in a battle that Apple never stops fighting as it tries to keep users’ data private.
I don’t think the article was written well, but to me the most interesting part was Secure Enclave stress testing, which involves temperature. I assume Apple is trying to prevent hacks like this.
In The Persistence of Chaos, Buy Six Notorious Computer Viruses For $1 Million
A computer infested with six of the word’s most infamous viruses is being sold as an art piece called ‘The Persistence of Chaos.’ The auction has topped US$1 million.
Bidding for a laptop infected with six of the world’s most famous computer viruses—WannaCry, BlackEnergy, ILOVEYOU, MyDoom, SoBig and DarkTequila—has topped more than $1.1 million at auction. The art project, titled “The Persistence of Chaos,” is a collaboration between Chinese internet artist Guo O Dong, and Deep Instinct, a cybersecurity firm based in New York. Those six viruses have caused billions of dollars in damage worldwide.
How to Use macOS Keychain Access to Beef up iCloud Keychain
Did you know that iCloud Keychain is synced with macOS’s Keychain Access utility? You can add website logins directly to Keychain Access, and have it synced to your iOS devices.
DHS Warns of Chinese Drone Spying
The U.S. Department of Homeland Security warns of Chinese drone spying, specifically Chinese-made consumer drones.
New ProtonMail Anti-Phishing Feature Makes You Confirm
For the past several days I’ve seen a new dialog box whenever I tap on a link in ProtonMail for iOS. It turns out that it’s a new ProtonMail anti-phishing feature.
Another security improvement is our new link confirmation modal, which is now enabled by default on all our apps. This anti-phishing feature helps you avoid opening a link by mistake or going to a different page than you intended.
A Fix For That Scary WhatsApp Exploit is Live
An Israeli firm called NSO Group used a WhatsApp exploit to inject spyware on target devices. A fix for the exploit is live.
Given the stealthy way the attack was attempted, it’s impressive that WhatsApp caught it as quickly as they did. Engineers at Facebook have been busy sorting this one out over the weekend…Named CVE-2019-3568…affected versions include…WhatsApp for iOS prior to v2.19.51, WhatsApp Business for iOS prior to v2.19.51.
Apple Releases Patch for ZombieLoad Flaw in Intel Chips
ZombieLoad is a serious flaw affecting almost every Intel chip since 2011. Apple, Amazon, Google, and Microsoft have issue patches for it.
The tech giant said in an advisory that any system running macOS Mojave 10.14.5, released Monday, is patched. This will prevent an attack from being run through Safari and other apps. Most users won’t experience any decline in performance. But some Macs could face up to a 40 percent performance hit for those who opt-in to the full set of mitigations.
Crazy that Intel chips have had this since 2011. This is the first time I’ve heard of ZombieLoad.