Special prototype iPhones called dev-fused iPhones help security researchers examine Apple’s code.
Security
Apple Security Tool Unveiled at RSA Conference 2019
The RSA Conference is a series of computer security conferences. This year, security researcher Patrick Wardle announced a new tool for Macs called GamePlan.
…GamePlan, a tool that watches for potentially suspicious events on Macs and flags them for humans to investigate. The general concept sounds similar to other defense platforms, and it hooks into detection mechanisms—has a USB stick been inserted into a machine? has someone generated a screen capture? is a program accessing a webcam?—Apple already offers in macOS. But GamePlan, cleverly written with Apple’s GameplayKit framework, collects all of this data in a centralized stream and uses the videogame logic engine to process it.
I use a couple of Mr. Wardle’s security tools. I look forward to downloading GamePlan.
GitHub Code Ring Promotes Over 300 Apps With Backdoors
Researchers uncovered a GitHub code ring made up of 89 accounts promoting 73 repos that contain over 300 apps with backdoors.
Google Finds Severe macOS Kernel Flaw
The flaw lets a hacker make changes to a file without informing the operating system.
Huawei Suing U.S. Government Over Ban
Huawei is suing the U.S. government because its products were banned from being used by federal agencies.
According to one of the people familiar with the matter, Huawei’s lawsuit is likely to argue that the provision is a “bill of attainder,” or a legislative act that singles out a person or group for punishment without trial. The Constitution forbids Congress from passing such bills.
Thunderbolt Vulnerability, Warrant Canaries – TMO Daily Observations 2019-02-27
Andrew Orr and Charlotte Henry join host Kelly Guimont to discuss the new Thunderbolt vulnerability and the latest in warrant canaries.
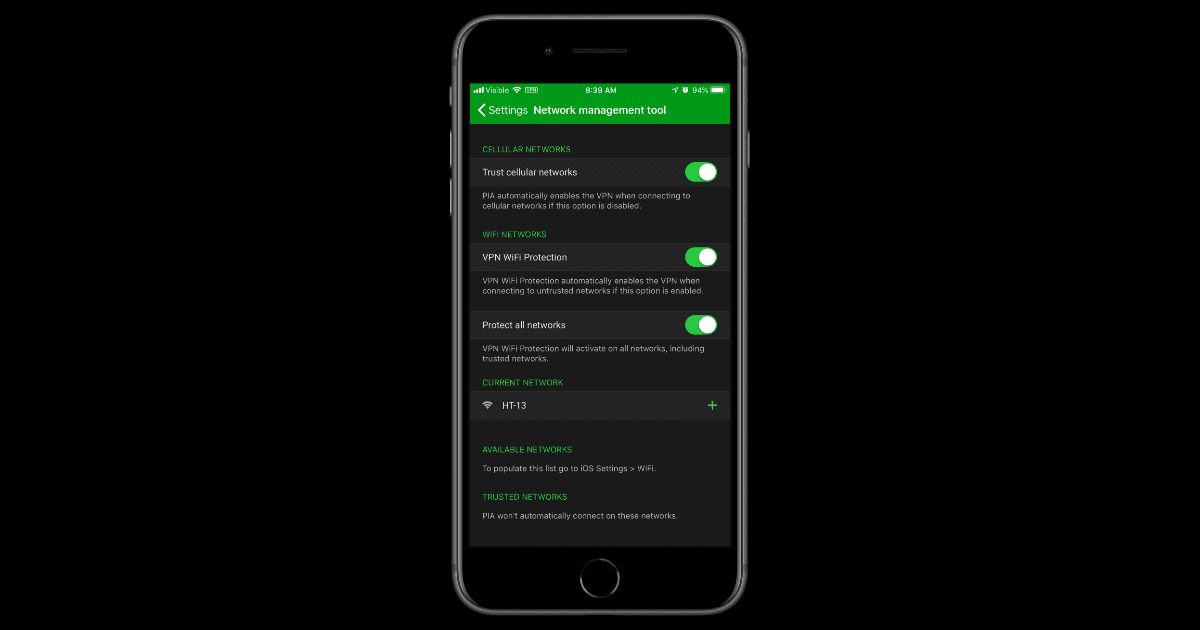
Private Internet Access 2.8.0 Brings Network Whitelisting
The Private Internet Access 2.8.0 update brings a network management tool. When you enable the feature PIA will automatically turn itself on when you connect to untrusted Wi-Fi networks. You can add networks you do trust to a whitelist, including your cellular network. If you set it not to trust cellular networks and you turn on the option to protect all networks, it means that the VPN will automatically turn itself on all the time.
The update also adds support for IKEv2. Internet Key Exchange (IKE) is part of the IPsec protocol suite, and it’s used to set up a security association. Jargon aside, IKEv2 is responsible for making a secure connection between you and the VPN server. It does this by authenticating you both and establishing which encryption methods will be used.
U.S. Cyber Command Thwarted Russia During Midterms
During the 2018 midterm elections U.S. Cyber Command blocked internet access to Russians seeking to interfere.
No, You Probably Don't Take Privacy and Security Seriously
Zach Whittaker is tired of the same old line companies use, like when they suffer a data breach: “We take your privacy and security seriously.”
The truth is, most companies don’t care about the privacy or security of your data. They care about having to explain to their customers that their data was stolen…About one-third of all 285 data breach notifications had some variation of the line. It doesn’t show that companies care about your data. It shows that they don’t know what to do next.
I’m betting there’s a template that public relations employees have that they copy and paste into official emails sent out in the wake of security stuff like this.
Webcams and Post-Its, Scary AI – TMO Daily Observations 2019-02-14
John Martellaro and Andrew Orr join Kelly Guimont to discuss webcams and security measures, as well as AI that freaks out even Elon Musk.
Happy Valentine's Day, This Dating App got Hacked
Dating app Coffee Meets Bagel announced today that it suffered a data breach on Monday.
Developers Required to Enable Two-Factor Authentication
Apple is requiring developers to secure their Apple ID with two-factor authentication.
Comparing Android Security Versus iOS Security
Keiran Dennie tweeted an interesting chart that compares the security of various smartphone operating systems.
Wondering about Android and Apple phone security? Here’s an objective chart to help you decide.
It’s a well known fact of Android that people have to rely on their carrier to push out security updates. This can take weeks, months, and sometimes they don’t get released at all.
macOS Flaw Exposes Safari Browsing History
A flaw in macOS Mojave can expose your Safari browsing history. Developer Jeff Johnson discovered this on February 8.
Russia Prepares for Cyber War With Disconnect Test
Russia prepares for cyber war with an internet disconnect test. Russia will temporarily disconnect itself from the internet.
Department of Homeland Security to Investigate Foreign VPNs
Senators Ron Wyden and Marco Rubio are worried about the possibility of foreign VPNs used to spy on U.S. government employees.
This Data Breach is Equal to 469,000 War and Peace Books
Last month we heard of the Collection #1 data breach, which contained 773 million email addresses and 21 million passwords. Now, Collections #2-#5 are here.
Despite its unthinkable size, which was first reported by the German news site Heise.de, most of the stolen data appears to come from previous thefts, like the breaches of Yahoo, LinkedIn, and Dropbox. WIRED examined a sample of the data and confirmed that the credentials are indeed valid, but mostly represent passwords from years-old leaks.
As with any data breach you can find out if your details have been leaked by visiting HaveIBeenPwned.com. My eBook copy of War and Peace is 1.8MB. The total size of the new breaches is 845GB, which equals 469,000 of those books.
Be Safe on the Internet With This Security Checklist
The Security Checklist is an open source list of resources designed to improve your online privacy and security. Check things off to keep track as you go.
This website provides a beginner’s checklist for staying safe on the internet. This website is the result of a conversation started during a recent episode of the Design Details Podcast and a subsequent tweet by Michael Knepprath.
This is a great website that Kelly Guimont pointed my way. Even if you’re a techie and have a handle on your online privacy, you should check this out too.
Screen Recording Your Activity, RIP Do Not Track – TMO Daily Observations 2019-02-07
Dave Hamilton and Andrew Orr discuss iOS apps recording your screen and bid farewell to Safari’s Do Not Track option, with host Kelly Guimont.
Security Researcher Won't Share macOS Keychain Bug
Security researcher Linuz Henze found a macOS Keychain bug but won’t share it with Apple out of protest.
Henze has publicly shared legitimate iOS vulnerabilities in the past, so he has a track record of credibility. However, Henze is frustrated that Apple’s bug bounty program only applies to iOS, not macOS, and has decided not to release more information about his latest Keychain invasion.
It is odd that there isn’t a macOS bug bounty but I think withholding security information isn’t the way to go.
U.S. Navy Needs to Destroy 2 Tons of Hard Drives
The U.S. Navy has issued a solicitation asking for an appropriate service to turn 4,000 pounds of storage devices into ash.
The information stored on these devices is highly sensitive, as evidenced by the physical security requirements set forth in the solicitation. The incineration facility must have “at the minimum, secure entry, 24-hour armed guards and 24/7 camera surveillance with recordable date and time capabilities.”
Any interested destruction service has to be located within 10 driving hours of the White Sands Missile Range.
GCHQ Wants Apple to add it to iMessage, FaceTime Chats
The GCHQ wants Apple to secretly add the agency to iMessage chats and FaceTime calls, effectively creating a backdoor into encryption.
Silicon Valley Needs Abusability Testing
Andy Greenberg writes that security isn’t enough for Silicon Valley. Companies should also adopt abusability testing.
It’s time for Silicon Valley companies to take the potential for unintended, malicious use of a product as seriously as they take its security. From Russian disinformation on Facebook, Twitter, and Instagram to YouTube extremism to drones grounding air traffic, Soltani argues that tech companies need to think not just in terms of protecting their own users, but what Soltani calls abusability: the possibility that users could exploit their tech to harm others, or the world.
In my cynical opinion, companies don’t care about whether their products could cause social harm. It’s all about money.