Canopy, a new security project from Ford and ADT, seeks to reduce automobile-related thefts and vandalism
Security
Safari 15 IndexedDB Bug Leaks Your Browsing Activity to Third Parties
On Friday, a report from FingerprintJS revealed a Safari 15 IndexedDB bug that can leak your internet activity to any website.
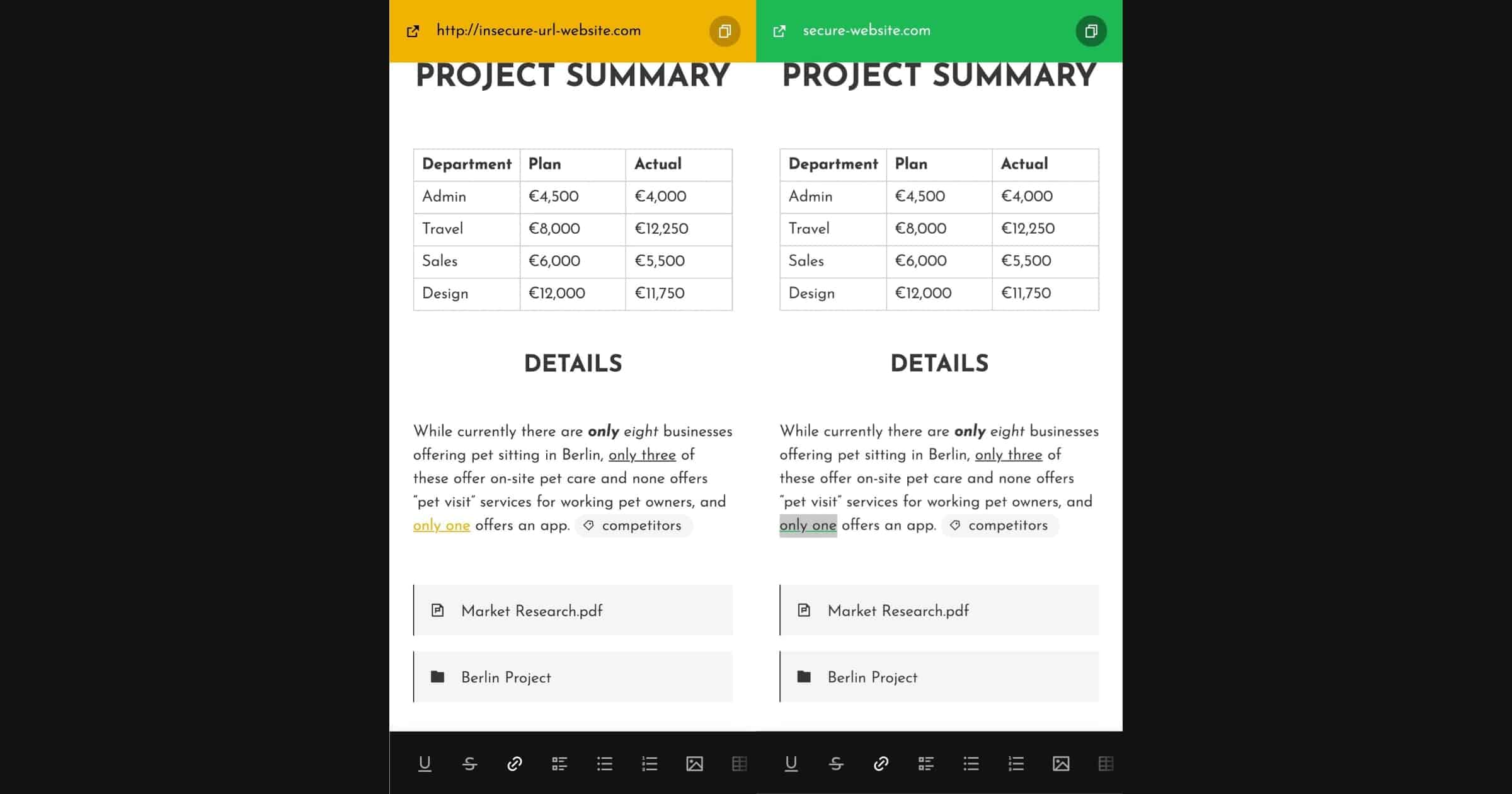
Cloud Platform 'Cryptee' Now Warns You of Insecure URLs
The team behind Cryptee, an end-to-end encrypted platform for documents and photos, announced new features for 2022. One in particular caught my eye.
We’ve improved our URL boxes on mobile. Cryptee can now intelligently detect and warn you if your links are insecure. (i.e. using “http” instead of “https”) All insecure links are automatically highlighted yellow, and all secure links are highlighted green.
Information Superhighway...to Hell – TMO Daily Observations 2022-01-14
Andrew Orr and Kelly Guimont discuss the latest security news including a happy headline, a practical tip, and an uplifting sendoff to the weekend.
Hackers Scam Blockchain City Group 'CityDAO' and Stole Funds
CityDAO, a group that bought 40 acres of land in Wyoming to build a blockchain-based city, has gotten hacked this week.
Russian Authorities Arrest Members of REvil Ransomware Group
The Russian Federal Security Service (FSB) announced on Friday that it has arrested 14 members of the REvil ransomware group.
White House Meets With Software Companies Over 'Log4j' Cybersecurity Concerns
Officials at the White House are meeting with companies such as Apple, Apache, and others to talk about cybersecurity in the wake of Log4j.
Apple Releases iOS 15.2.1 Update That Fixes HomeKit Bug
On Wednesday Apple released iOS 15.2.1 and iPadOS 15.2.1 to its customers. It’s a minor update that contains a few bug fixes.
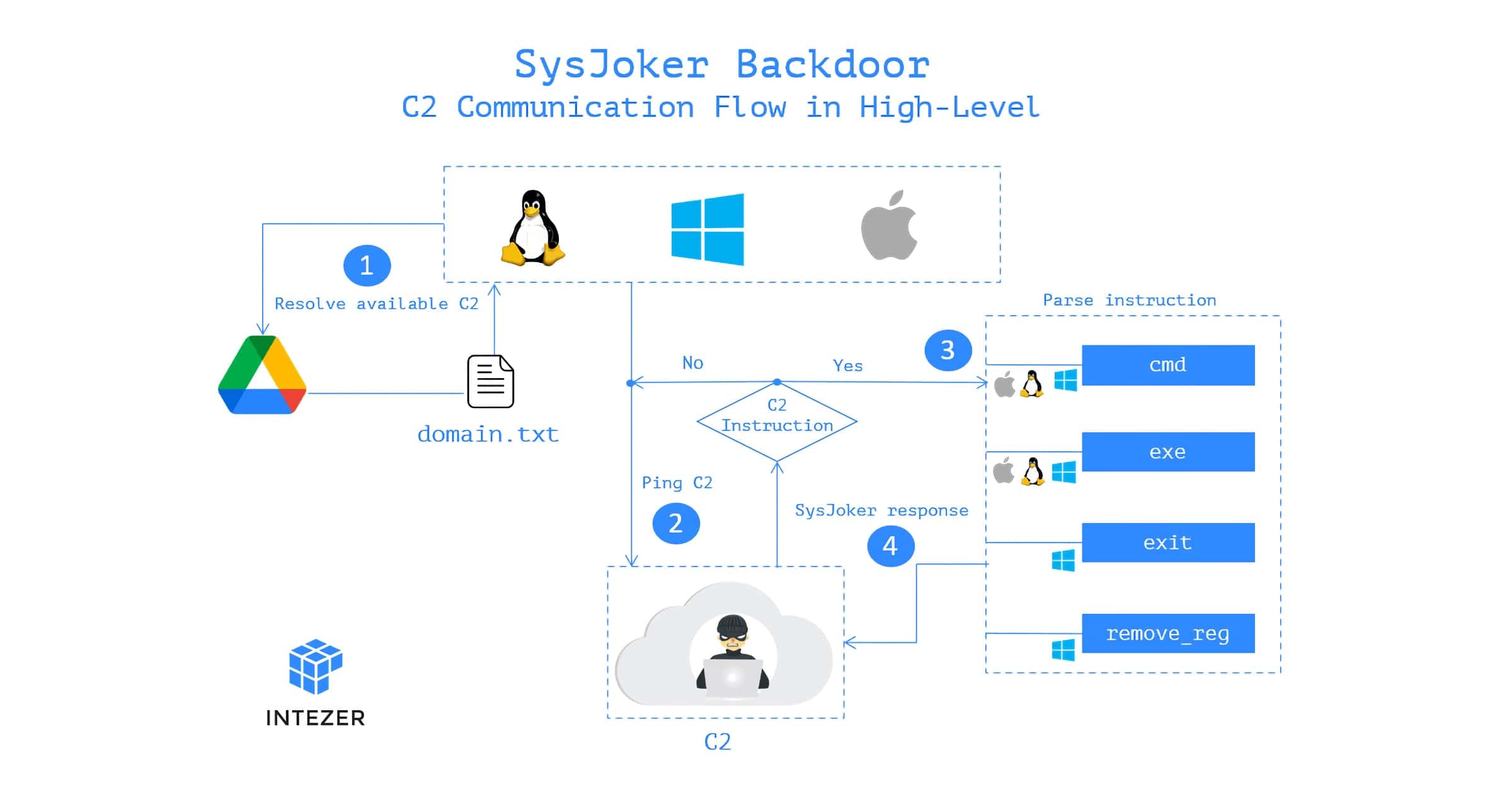
New 'SysJoker' Backdoor is a Multi-Platform Threat for macOS, Windows, Linux
There is a new piece of malware floating around. This SysJoker backdoor was discovered in December 2021 by the Intezer team.
TransCredit Data Leak Over 800,000 Records of Credit Reports
Jeremiah Fowler together with the Website Planet research team found an unsecured Transcredit data leak of 822,789 records.
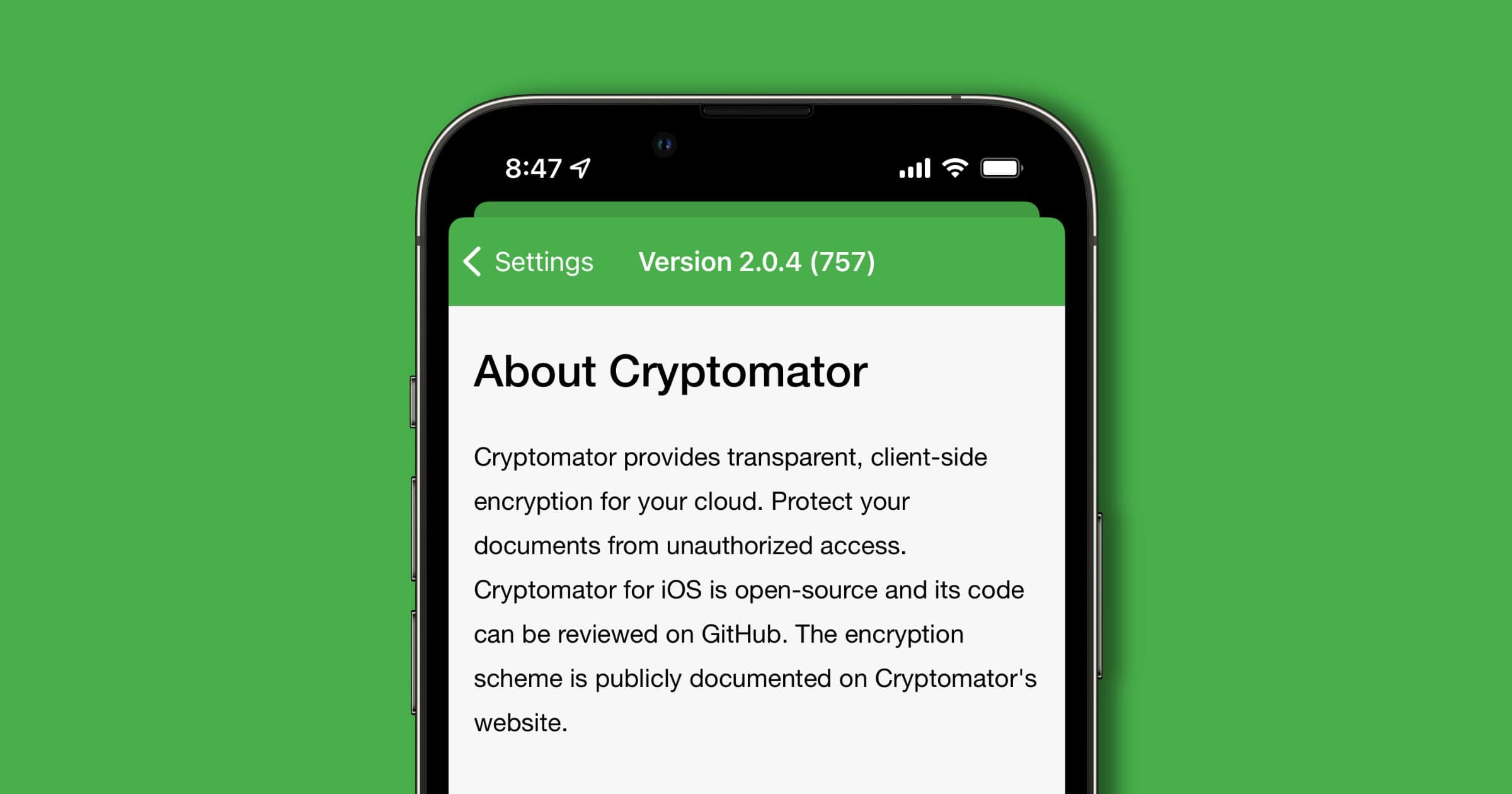
Update Immediately: Bug in 'Cryptomator' Leaks Encrypted File Paths to Apple
A bug in Cryptomator was recently found and reported on for the iOS app. The team wrote about the vulnerability on Tuesday.
Mac Security Tools Company 'Objective-See' Goes Non-Profit
Instead of antivirus or antimalware software, I use several tools from Objective-See. They’re free and open source. Company founder Patrick Wardle is making the business a non-profit.
I see a lot of people who take VC money and almost always your business model has to change or you have to put profits first and can’t do the community focus and public service activities you want. Going the nonprofit route is a really good approach and illustrates that you can support your company on donations without having to change that business model.
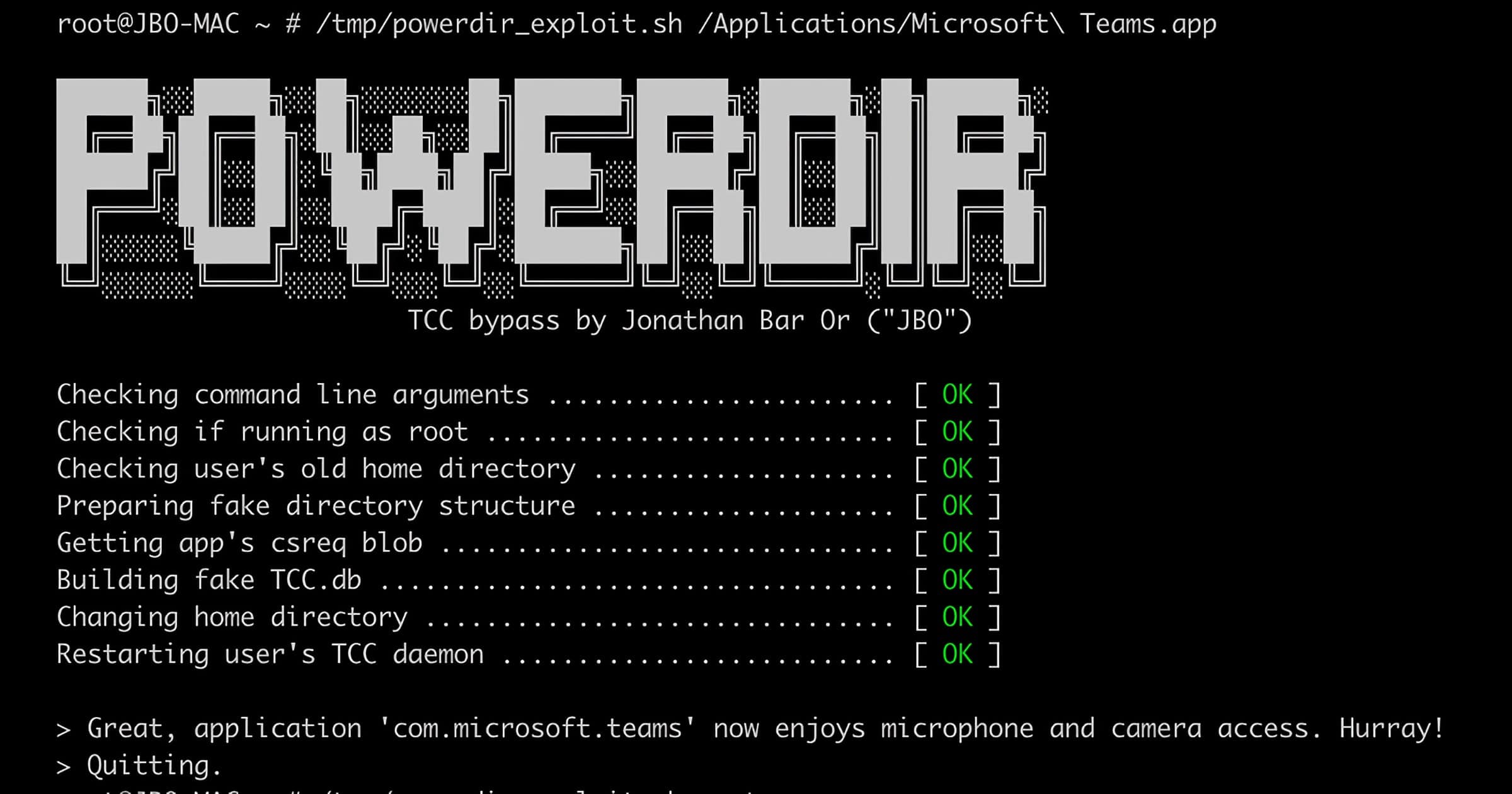
macOS Bug 'Powerdir' Could Let Attacker Access User Data
Microsoft’s security team has published an analysis of “powerdir” a vulnerability in macOS that could let an attacker access a person’s data.
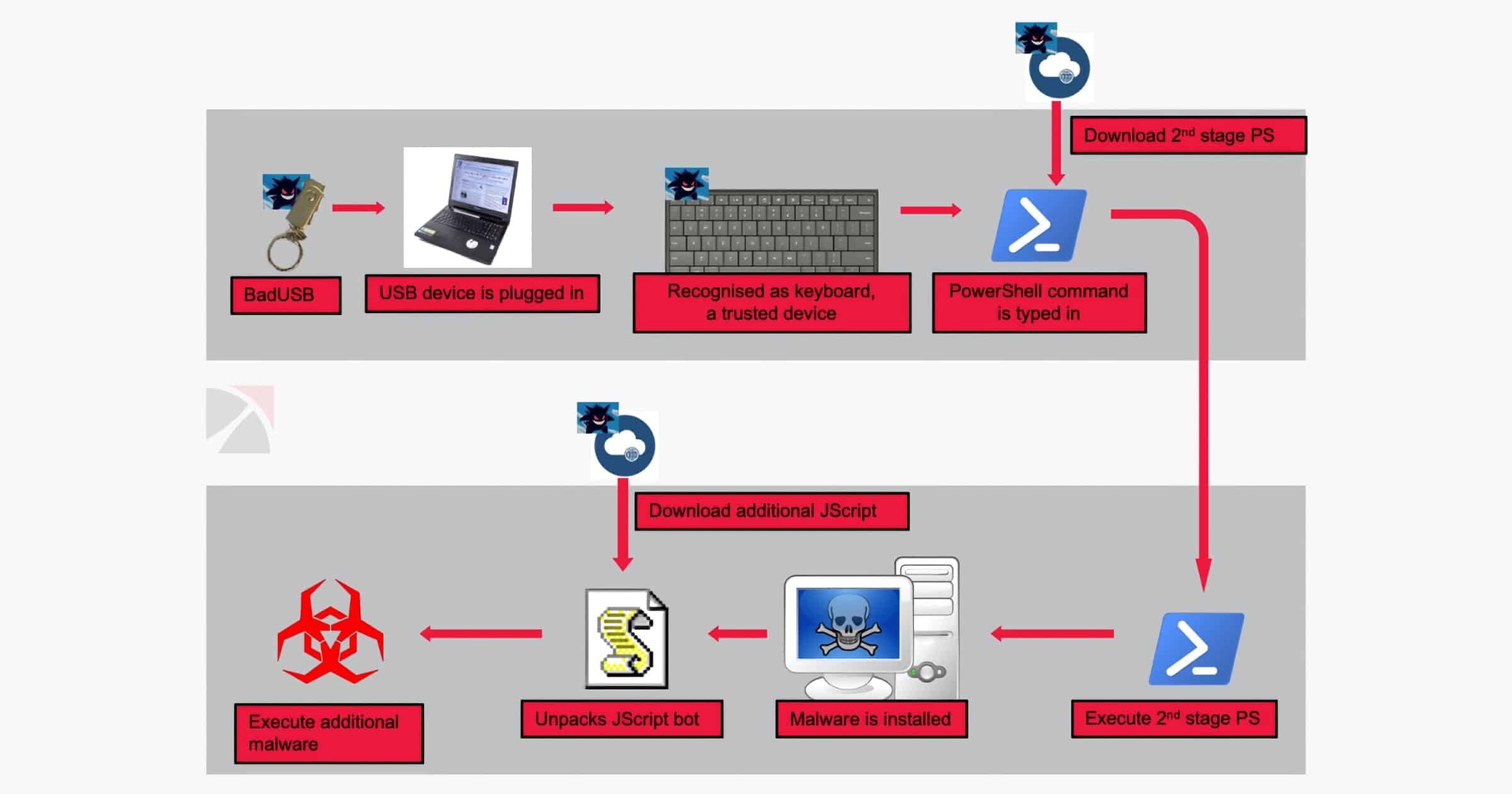
People are Mailing USB Drives With 'BadUSB' Malware to Companies
The FBI is warning that an Eastern European cybercriminal group is mailing USB drives filled with BadUSB malware to various companies.
Ransomware Attack on Finalsite Shuts Down 5,000 School Websites
Finalsite is a company that helps schools with websites. In a statement, it says it was hit by a ransomware attack on Tuesday, January 4.
Proton Shares Year in Review With Product Plans for 2022
Proton, makers of ProtonMail and ProtonVPN, has shared its 2021 Year in Review. The company has also shared its plans for the year ahead.
'NoReboot' is an iOS Bug That Can Fake a Shutdown to Trick You
ZecOps writes about “NoReboot,” the ultimate persistence bug that can trick the user into thinking the device has been shut down.
Pepcom 2022: Wemo Announces a Smart Video Doorbell for HomeKit
Wemo’s new smart video doorbell announced at Pepcom 2022 will support Apple’s HomeKit. Videos will be stored in a person’s iCloud+ account.
Recap: Here is the Mac Malware List for 2021
Security researcher Patrick Wardle made a list of the Mac malware we saw in 2021. It’s a timeline with information on each.
While the specimens may have been reported on before (i.e. by the AV company that discovered them), this blog aims to cumulatively and comprehensively cover all the new Mac malware of 2021 – in one place …yes, with samples of each malware available for download!
After reading this blog post, you should have a thorough understanding of recent threats targeting macOS. This is especially important as Apple continues to make significant inroads into the enterprise.
Everything You Wanted to Know About How Encrypted Email Works
ProtonMail published a nice blog post explaining how encrypted email works, and the various protocols that companies use.
End-to-end encryption for messages sent between ProtonMail users is automatic, and our integrated OpenPGP support makes it easy to send and receive PGP-encrypted E2EE messages to people that use PGP with other email providers. Proton also informs you when your messages are protected by E2EE with a small blue padlock (for other ProtonMail users) or green padlock (for OpenPGP users).
Polygon Fixes Bug That Endangered $24 Billion Worth of MATIC Token
Polygon, a Layer 2 scaling network for Ethereum, fixed a bug that put its MATIC token at risk. However, a hacker was able to steal tokens.
Saudi Activist With EFF Sues DarkMatter Group for Hacking iPhone
Saudi human rights activist Loujain AlHathloul, along with the Electronic Frontier Foundation, is suing DarkMatter for hacking her iPhone. DarkMatter Group was created and run by former U.S. intelligence operatives.
Reuters broke the news about the hacking program called Project Raven in 2019, reporting that when UAE transferred the surveillance work to Emirati firm DarkMatter, the U.S. operatives, who learned spycraft working for the National Security Agency and other U.S. intelligence agencies, went along and ran DarkMatter’s hacking program, which targeted human rights activists like AlHathloul, political dissenters, and even Americans residing in the U.S.
President Biden Signs 'National Defense Authorization Act' Into Law for Cybersecurity
The National Defense Authorization Act of 2022 lays out voluntary cybersecurity practices for private companies that handle critical infrastructure in the U.S.
But provisions all rely on the voluntary participation by industry, which owns and operates the vast majority of the nation’s critical infrastructure. Despite bipartisan calls after massive breaches at SolarWinds, Microsoft Exchange, Colonial Pipeline and other hacks, the NDAA made it through the House without mandatory incident reporting requirements for the private sector.
I disagree on the “voluntary” part. Make it mandatory, otherwise we end up with T-Mobile’s half-dozen breaches in the span of four years.
T-Mobile Data Breach Leaves Customers Vulnerable to SIM Swapping
T-Mobile has had another data breach, although a report suggests this one is less severe than the one in August. Only a small set of customers have been affected, but they could be vulnerable to a SIM swapping attack.
This is where a malicious actor will change the physical SIM card associated with a phone number in order to obtain control of said number. This can, and often does, lead to the victim’s other online accounts being accessed via two-factor authentication codes sent to their phone number. The document says that customers affected by a SIM swap have now had that action reversed.