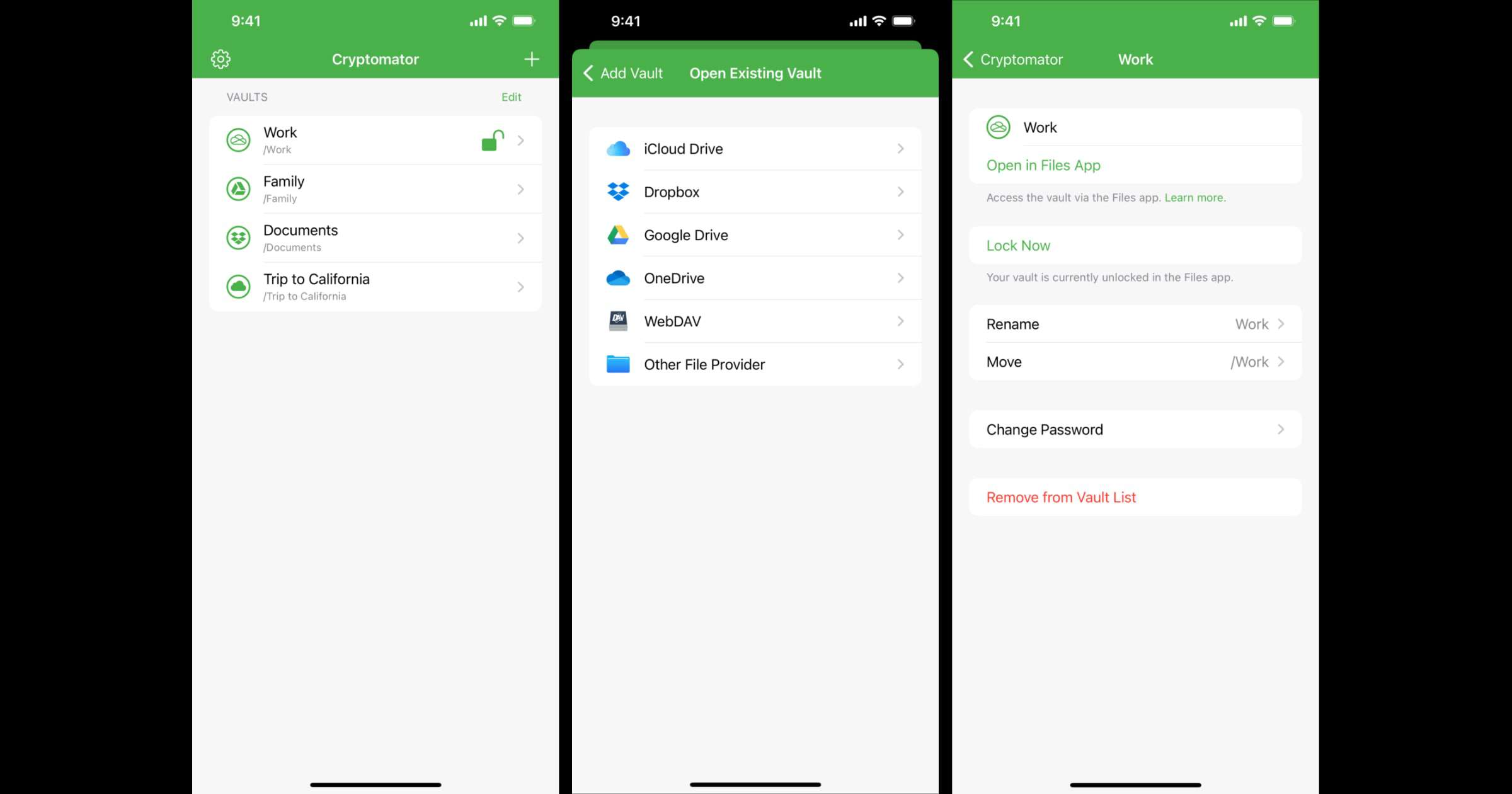
A Bluetooth bug found with Fisher-Price’s Chatter phone could let others eavesdrop on your conversation.
With just the online instruction manual to go on, the researchers feared that a design flaw could allow someone to use the Chatter to eavesdrop.
Ken Munro, founder of the cybersecurity company Pen Test Partners, told TechCrunch that chief among the concerns are that the Chatter does not have a secure pairing process to stop unauthorized phones in Bluetooth range from connecting to it.