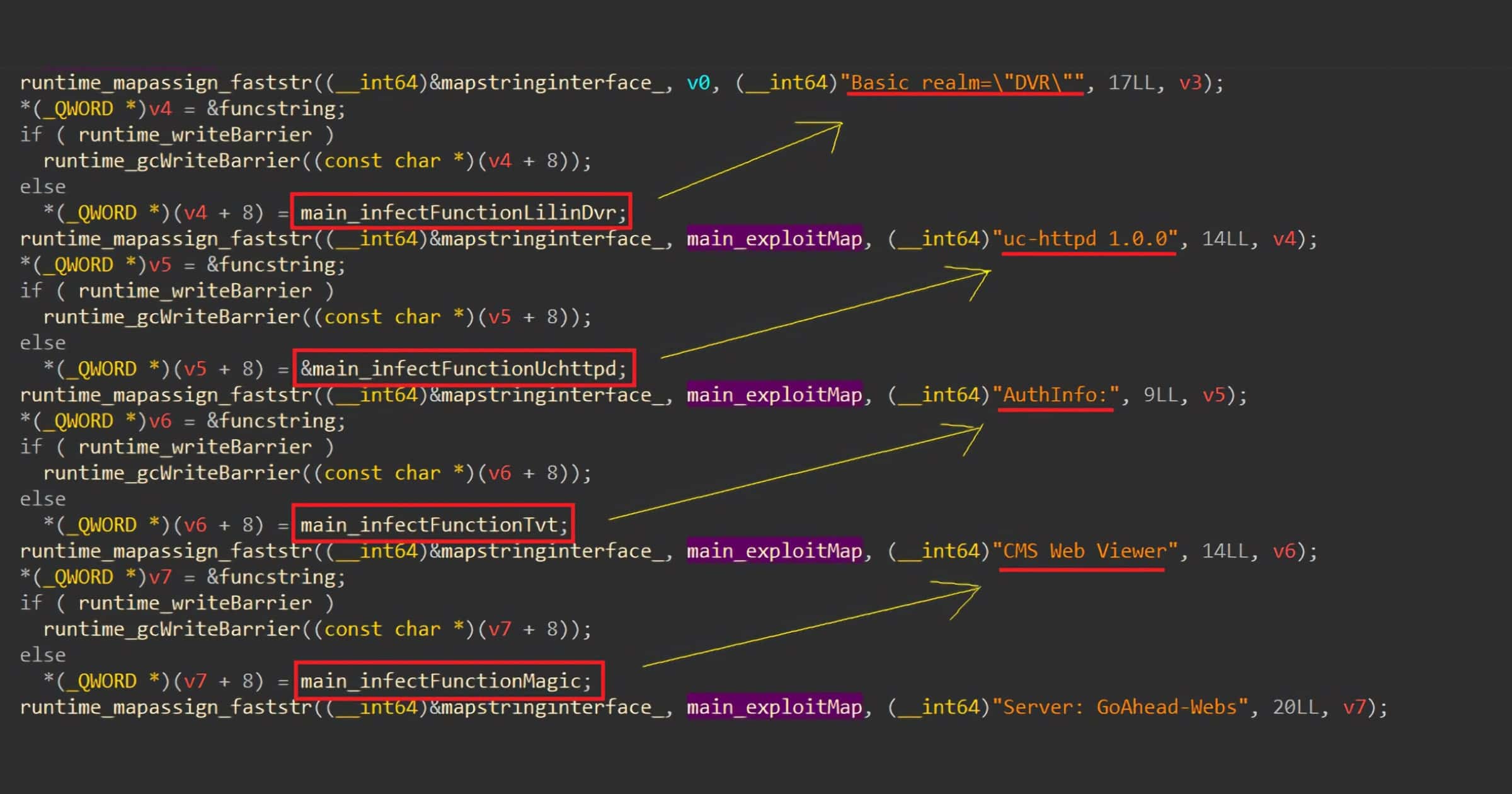
Hackers are exploiting a bug from 2017 to attack the EdgeMarc Enterprise Session Border Controller. This device is used by businesses to manage phone calls and video calls.
The vulnerability being exploited to infect the devices is tracked as CVE-2017-6079, a command-injection flaw that penetration tester Spencer Davis reported in 2017 after using it to successfully hack a customer’s network. The vulnerability stemmed from an account in the device that, as Davis learned from this document, had the username and password of “root” and “default.”