Customers of Visible have reported some erroneous account cancellations after taking advantage of the carrier’s recent promotion.
Carriers
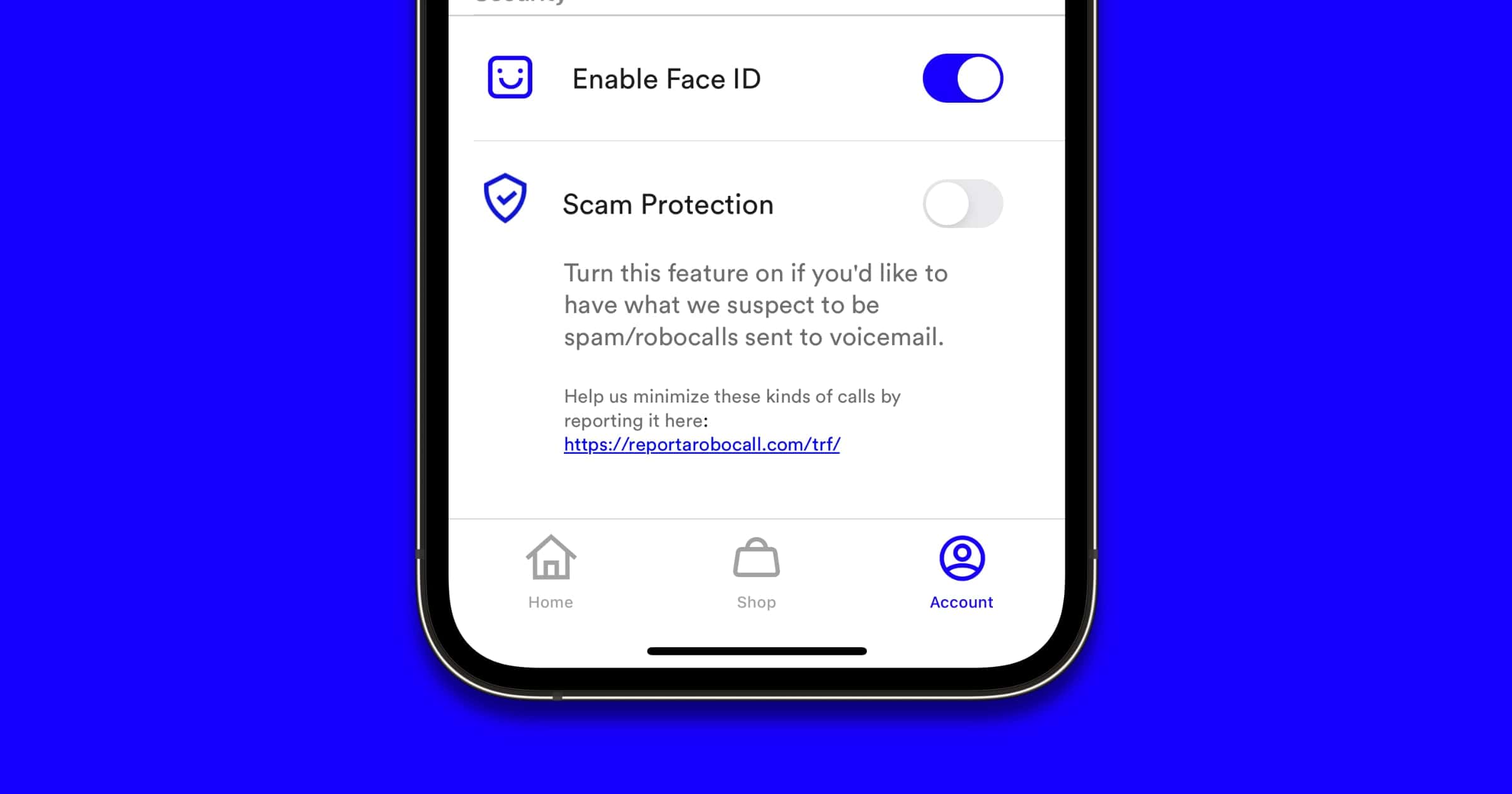
Here's How to Enable Scam Protection on Visible
In an email to customers, prepaid carrier Visible announced that it’s rolling out a Scam Protection feature to fight robocalls.
Visible Deal Gives 2 Months Unlimited Data for $11
Visible is offering a deal that provides two months of unlimited data at US$11.00 for each month. The 2for22 deal starts tomorrow, February 2.
Get Free AirPods When You Sign Up For Visible for Black Friday 2021
Starting November 18, Visible is offering new customers a free pair of earbuds when they buy select phones and port their number.
Verizon Names Manon Brouillette as CEO and Executive Vice President
Verizon Communications announced Manon Brouillette as Executive Vice President and CEO of Verizon Consumer Group effective January 1, 2022
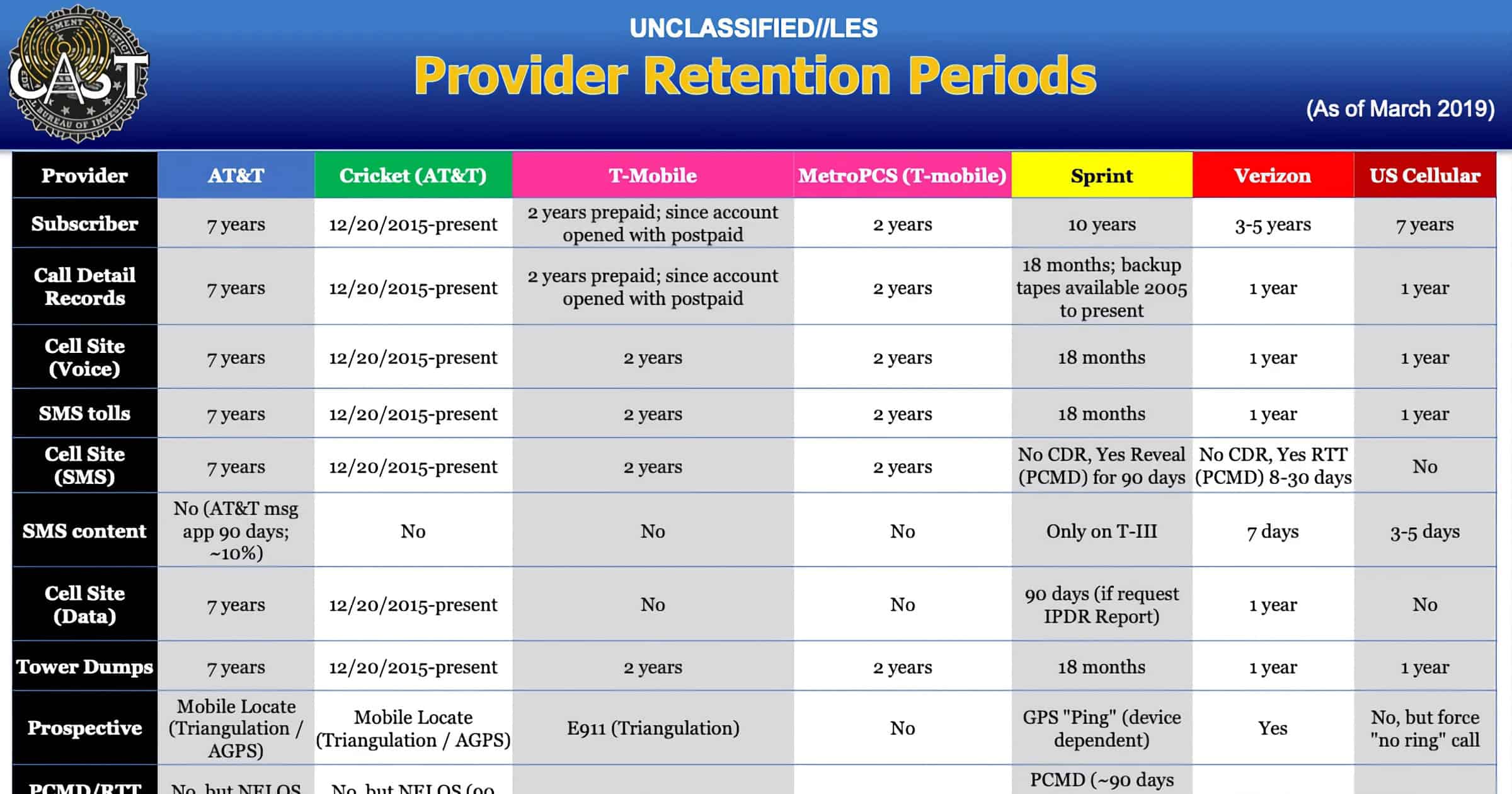
FBI Document Reveals Guide to Get Location Data From Carriers
An internal document for the FBI reveals how the agency obtains phone location data from carriers like AT&T, Verizon, and others.
Switch to T-Mobile and Your Phone Will be Paid Off Up to $1,000
T-Mobile announced that it will pay off your remaining smartphone payments up to US$1,000 if you switch to its network.
Customer Accounts of 'Visible' Phone Carrier Hacked, Unauthorized Purchases Made
Visible, a carrier owned by Verizon, suffered what some believed was a data breach on Wednesday, with some customer accounts hacked.
SMS Routing Company 'Syniverse' Admits it was Hacked in 2016
Syniverse provides backbone services to wireless carriers like AT&T, Verizon, T-Mobile, and several other carriers. It discovered the breach in May 2021 but it began in May of 2016.
Syniverse repeatedly declined to answer specific questions from Motherboard about the scale of the breach and what specific data was affected, but according to a person who works at a telephone carrier, whoever hacked Syniverse could have had access to metadata such as length and cost, caller and receiver’s numbers, the location of the parties in the call, as well as the content of SMS text messages.
Phone Companies Must Block Carriers That Don't Follow FCC Rules
Phone companies must now block traffic from voice service providers that don’t comply with new FCC robocall rules.
Specifically, phone companies must block traffic from other “voice service providers that have neither certified to implementation of STIR/SHAKEN caller ID authentication standards nor filed a detailed robocall mitigation plan with the FCC.”
What You Can Do If Your Verizon iPhone 13 Doesn't Get 5G
Some iPhone 13 owners are reporting that they’re unable to get 5G Ultra Wideband. PCMag found three solutions that may help.
The iPhone 13 has Five Different 5G and LTE Configurations
The iPhone 13 lineup has five different configuration setups for 5G and LTE. This is the widest array of frequencies of any iPhone thus far.
Phone Carrier 'Visible' Will Sell Apple Watch Series 7 for First Time
Visible, a prepaid carrier that operates on Verizon’s network, will sell the iPhone 13 models and the Apple Watch Series 7 on its website.
Verizon Brings 5G Ultra Wideband to 25 NFL Stadiums
Verizon and the NFL announced a 10-year partnership on Thursday to bring 5G Ultra Wideband to 25 NFL stadiums over the next decade.
Speed Tests Reveal the Fastest Mobile Network in the United States
In its twelfth annual network test, PCMag traveled over 10,000 miles across the U.S. to test the speeds of mobile networks AT&T, T-Mobile, and Verizon.
Researchers Propose New Way to Limit Location Tracking With ‘Pretty Good Phone Privacy’
Researchers have proposed a way to limit smartphone tracking from carriers. It’s called Pretty Good Phone Privacy.
‘Non-Standalone’ 5G Exposes Phones to Stingray Police Surveillance
5G that uses “non-standalone architecture” is rife with security issues and doesn’t protect people from Stingray police surveillance.
Borgaonkar and fellow researcher Altaf Shaik, a senior research scientist at TU Berlin, found that major carriers in Norway and Germany are still putting out 5G in non-standalone mode, which means that those connections are still susceptible to stingrays. The two presented at the Black Hat security conference in Las Vegas last week.
Verizon Adds Four New Mobile Hotspot Plans for Customers
Verizon announced on Thursday the addition of four new mobile hotspot plans, perfect for travelers. From 15GB to 150GB per month.
Visible Introduces ‘Bring a Friend’ Program for Cellular Service
Visible has launched a program called Bring a Friend that aims to reduce customers’ phone bills while bringing new people to the service.
Visible to Offer Early Smartphone Upgrade Program for Members
Starting May 3, Visible will offer an early smartphone upgrade program for Apple, Samsung, and Google phones.
Phone Carrier ‘Visible’ Offers Special Tax day 2021 Deals
Visible is a mobile-first prepaid phone carrier that uses Verizon’s network and it has a new deal for Tax Day 2021 for new customers.
T-Mobile Completes Rollout of Anti-Spam ‘STIR/SHAKEN’ Technology
T-Mobile announced on Thursday that it completed the rollout of its anti-spam STIR/SHAKEN technology.
FCC Readies Next 5G Auction so Service Reaches More Americans
The FCC is preparing a 5G auction that will begin in October. It will offer frequencies that will cover millions of more Americans.
Here’s What Phone Carrier ‘Visible’ Has Been Up To Lately
On Tuesday, prepaid carrier Visible shared details about the features it has added lately to its service in an email to customers.