Elcomsoft, a company that sells forensics software, announced on Thursday that it has successfully cracked the latest version of Veracrypt.
encryption
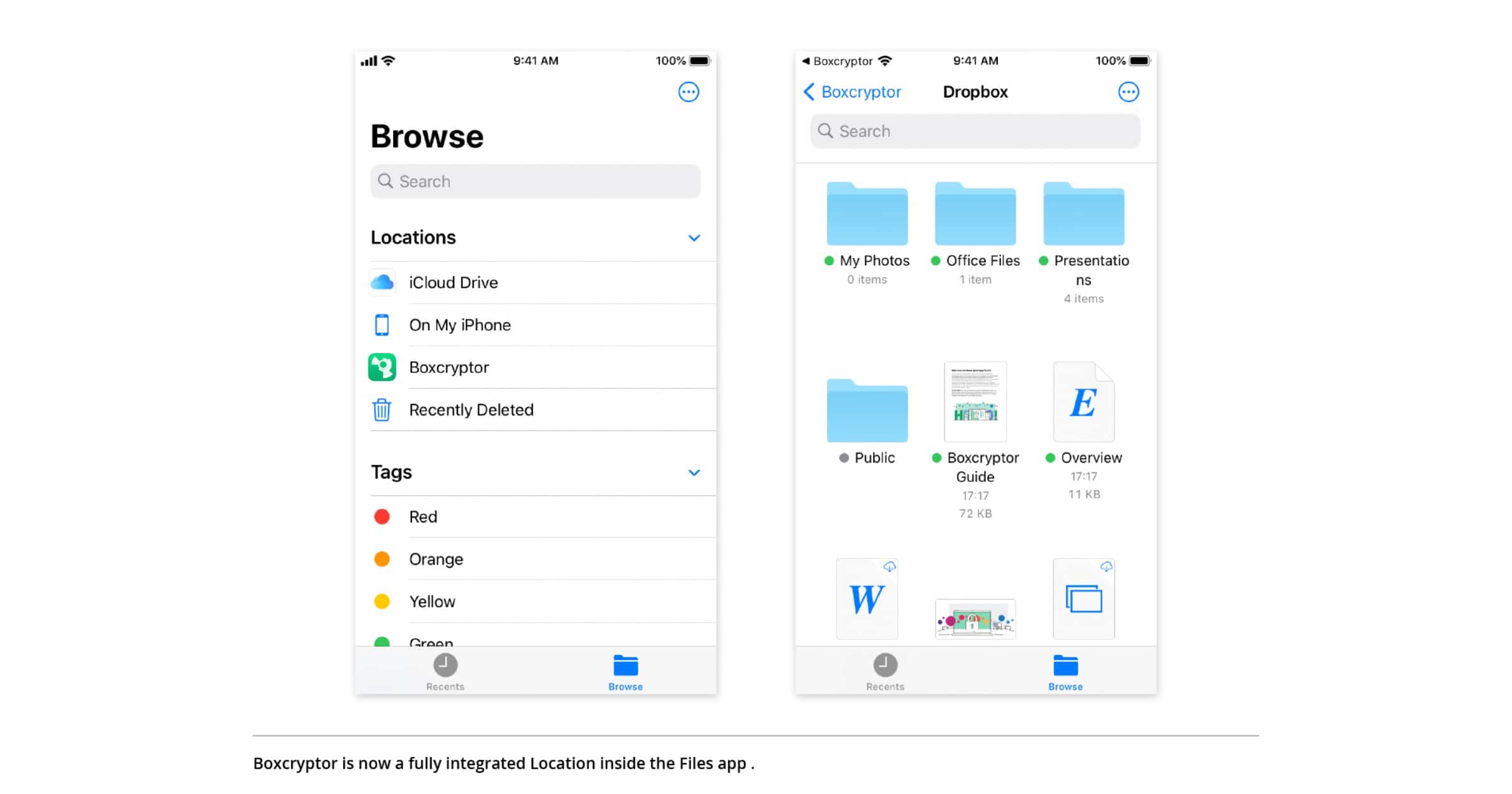
Encrypted Storage App ‘Boxcryptor’ Integrates Better With Files App
Boxcryptor received a major update for iOS and iPadOS that eliminates its own file browser. Instead, you’ll browse through your encrypted files completely within Apple’s Files app. Robert Freudenreich explains the decision: “By taking a ‘Files app first’ approach, we enable the best user experience for working with encrypted files in Apple’s Files app.” The integration with the Files app has been in place since iOS 11. But by eliminating the additional Boxcryptor-owned file browser, the Files app now becomes the exclusive file manager. For users, this primarily means an even simpler workflow.
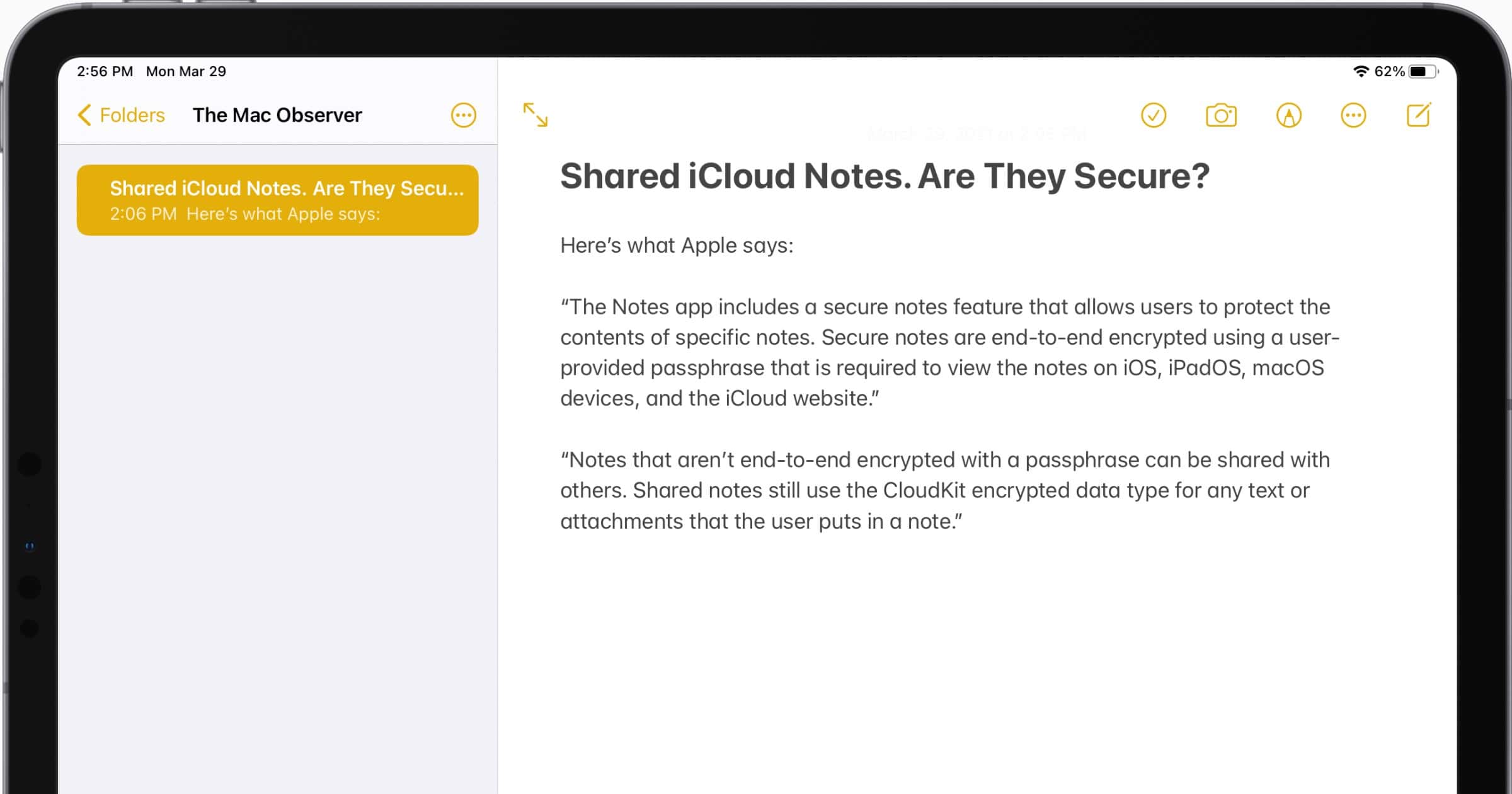
iCloud Security and Using Apple Notes as a Secret Messenger
Shared Apple Notes can be used to send secret messages to people. But how secure are they? Andrew finds out.
Encrypted Cloud Storage Service ‘Cryptee’ Announces Massive Update
Cryptee is an end-to-end encrypted cloud storage service and announced a huge update on Sunday.
We’ve re-designed the entire platform, re-engineered everything from ground up, added hundreds of new features, and created an entirely new Cryptee experience for you. Along the way we’ve realized it’s going to be a massive leap forward, so we thought we should get a new logo too.
I think Cryptee is a great service and one that I’ve recommended in the past.
Security Friday: Encryption Updates, Reviewing Permissions – TMO Daily Observations 2021-01-15
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and how January is a good time to review all those Sign In With… buttons.
iOS Encryption Isn’t as Secure as it Could be, Researchers Discover
Security researchers at John Hopkins University studied the security measures of Android and iOS, specifically encryption.
Security Friday, Secret Messages – TMO Daily Observations 2021-01-08
Andrew Orr joins host Kelly Guimont to discuss Security Friday news, including what’s up with WhatsApp (sorry) and some things to know about encryption.
Cellebrite Has Not Broken Signal’s Encryption
On Tuesday, security company Cellebrite claimed to have broken the encryption that Signal uses to keep user communication safe. The blog post has since been removed, but the BBC has an archived version here. But Signal says that claim isn’t true.
It is important to understand that any story about Cellebrite Physical Analyzer starts with someone other than you physically holding your device, with the screen unlocked, in their hands. Cellebrite does not even try to intercept messages, voice/video, or live communication, much less “break the encryption” of that communication. They don’t do live surveillance of any kind.
File Encryption App ‘Boxcryptor’ Announces macOS Big Sur Support
File encryption app Boxcryptor has been updated to support macOS Big Sur and M1 Macs to keep your documents safe in the cloud.
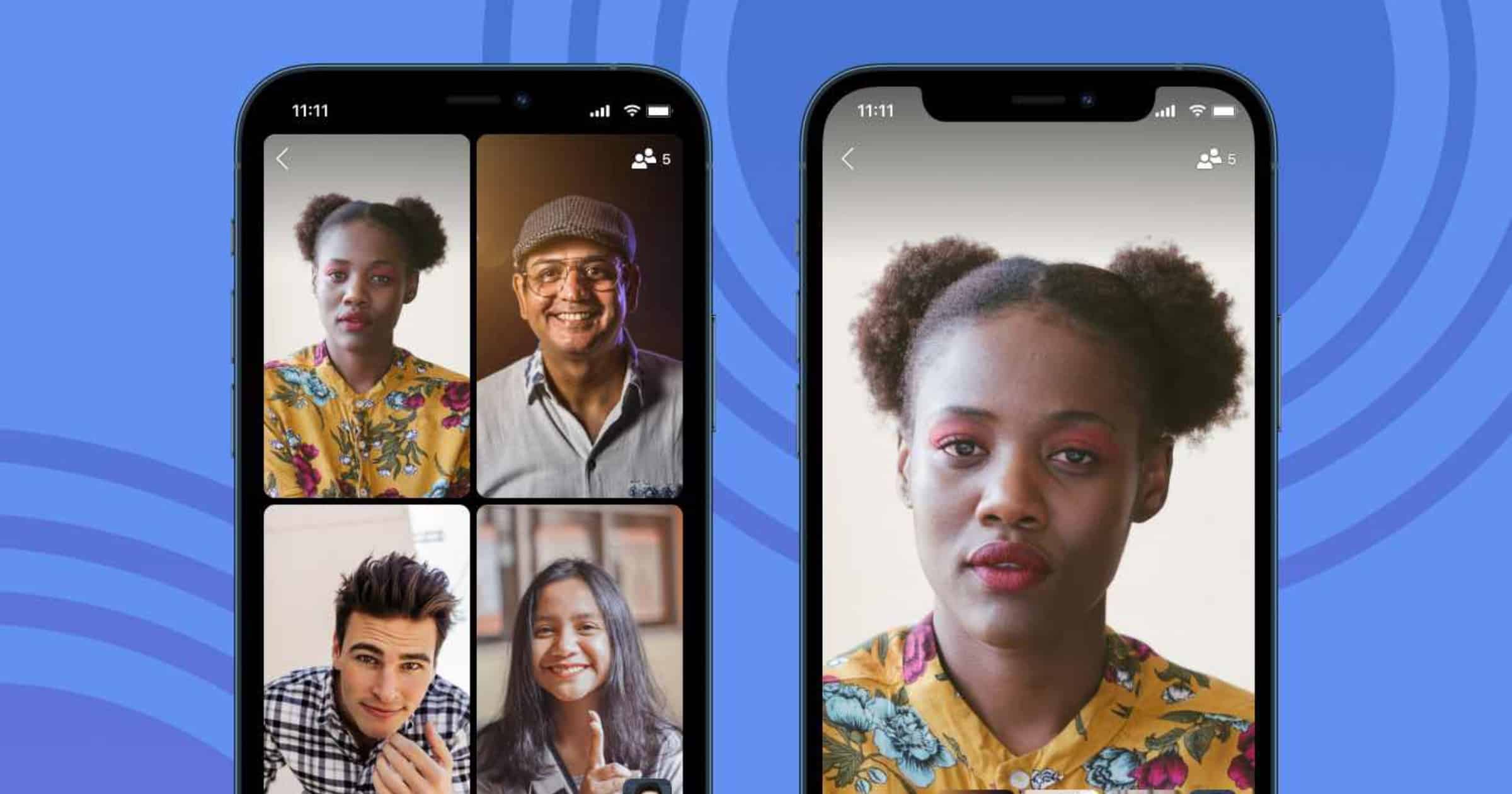
Private Messenger ‘Signal’ Adds Encrypted Group Video Calls
Good news for users of Signal. The app now supports group video calls, and they are end-to-end encrypted like the rest of the app’s communications.
Now when you open a group chat in Signal, you’ll see a video call button at the top. When you start a call, the group will receive a notification letting them know a call has started.
When you start or join a group call, Signal will display the participants in a grid view. You can also swipe up to switch to a view that automatically focuses the screen on who is speaking, and it will update in real time as the active speaker changes.
Here are the Top 5 Encrypted Cloud Storage Services
To accompany his roundup of encrypted DNS services, Andrew has a roundup of the best encrypted cloud storage services.
5 Encrypted DNS Services to Use on iOS and macOS
Switching from your ISP’s DNS is good because your browsing history could be sold. Here are five encrypted DNS services to use instead.
Security Friday, Encryption Basics – TMO Daily Observations 2020-11-20
Andrew Orr join host Kelly Guimont to discuss Security Friday news, This Week in Facebook, and basic encryption for messaging and iOS files.
Encryption App ‘Cryptomator’ to Integrate With iOS Files
Cryptomator is my top recommendation for file encryption and it recently shared its late 2020 development roadmap.
What’s up with Cryptomator for iOS? For the last 6-7 months, we have been hard at work on a completely new app written in Swift.
What will be so special about the rewrite? Cryptomator will be fully integrated into the Files app. This comes with many benefits like thumbnails, support for third-party apps that can edit files directly inside the vault, and many more!
Great news. What I’ve also been hoping for is the ability to access Cryptomator vaults in external storage on iOS/iPadOS, like you can on the Mac.
NSA Avoids Discussing Back Doors in Commercial Products
The U.S. National Security agency is dodging questions about back doors in commercial products and whether it’s continuing this practice. The article mentions Dual EC, a type of encryption algorithm the NSA tried to get ratified as a global standard. Why? Because they could easily crack it.
Juniper Networks got into hot water over Dual EC two years later. At the end of 2015, the maker of internet switches disclosed that it had detected malicious code in some firewall products. Researchers later determined that hackers had turned the firewalls into their own spy tool here by altering Juniper’s version of Dual EC.
And that’s the reason we oppose these kinds of back doors or “weaknesses on purpose” on Security Friday. If one group can easily crack it, so eventually will other groups.
Zoom Rolls Out End-to-End Encryption for Video Calls
Starting next week, video conferencing app Zoom is finally adding end-to-end encryption to its platform.
Zoom’s E2EE offering uses public key cryptography. In short, the keys for each Zoom meeting are generated by participants’ machines, not by Zoom’s servers. Encrypted data relayed through Zoom’s servers is indecipherable by Zoom, since Zoom’s servers do not have the necessary decryption key. This key management strategy is similar to that used by most end-to-end encrypted messaging platforms today.
Good to see Zoom doing this; they’ve certainly had misses in the past. Update: The new version is now available for most users.
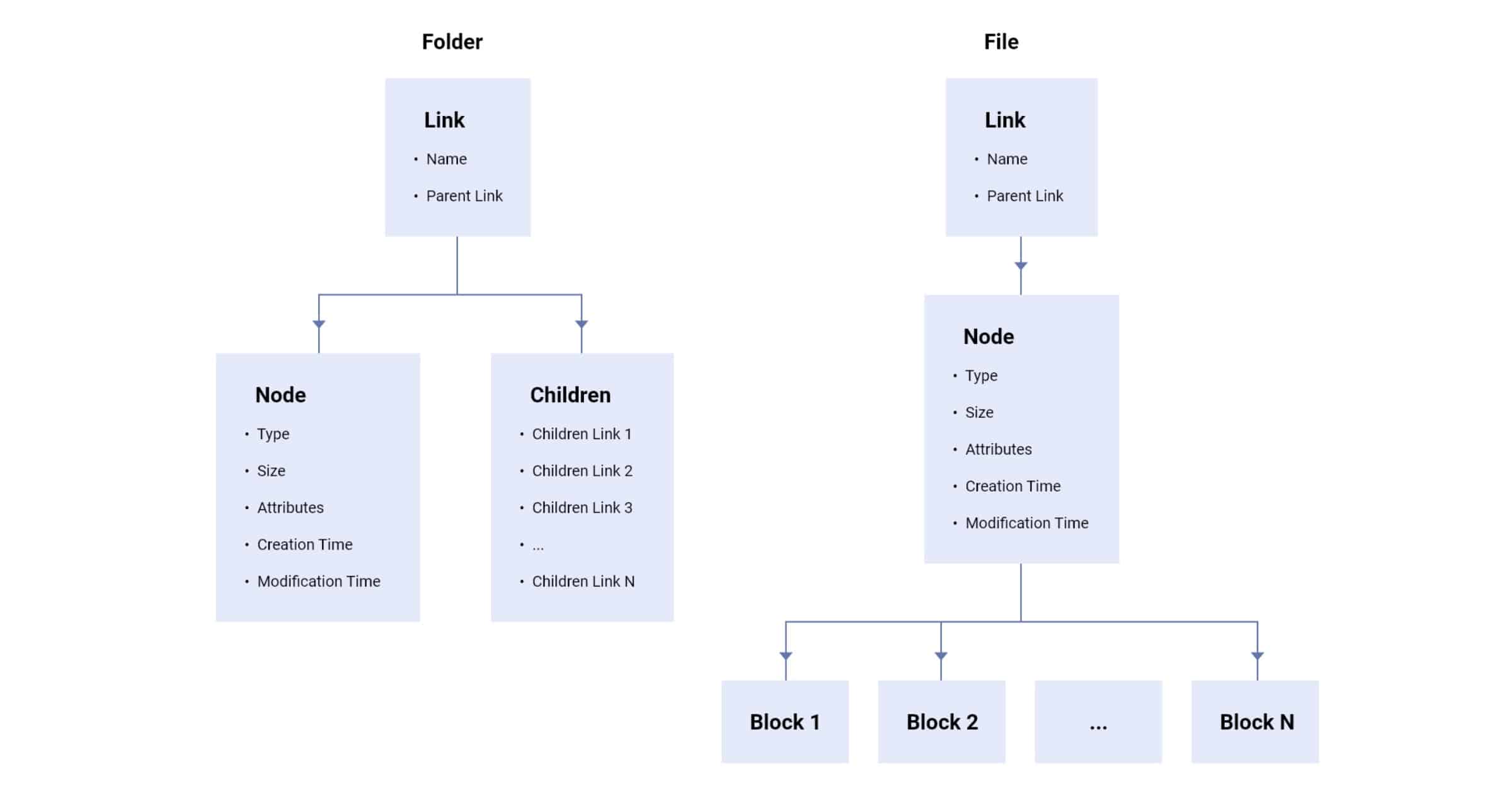
ProtonDrive’s End-to-End Encryption Security Revealed
ProtonDrive (from the makers of ProtonMail and ProtonVPN) is in the final stages of development before it gets a beta launch later in 2020. The team revealed its end-to-end encryption security in a blog post.
Files and folders are arranged in a tree structure. Therefore, there is a recurring pattern where a file or folder’s asymmetric key is locked with a passphrase, which in turn is encrypted with the asymmetric key of their parent folder. All passphrases are signed with the address key of the user, without which a malicious server could forge the contents of the tree.
pCloud Update Lets Users Decide Where Files are Stored
pCloud is an encrypted cloud storage service, and a recent update gave users the ability to decide in which server their files are stored.
All pCloud users will be able to choose the server location where their files are stored. This will give users greater control over the security of their files. Once the choice of where to store the data is made during registration – in the US or Europe – it is practically impossible to transfer them without the user’s knowledge or permission. Currently, the option to select the server location is available only to newly registered users.
Senate Judiciary Committee Passes Anti-Privacy ‘EARN IT Act’
Today the Senate Judiciary Committee passed the EARN IT act, a bill that weakens Section 230 protections for social media companies in an attempt to fight online child abuse.
‘Lawful Access to Encrypted Data Act’ is Latest Encryption Attack
Senators Lindsey Graham (R-South Carolina), Tom Cotton (R-Arkansas) and Marsha Blackburn (R-Tennessee) introduced the Lawful Access to Encrypted Data Act yesterday. It seeks to bring back the Crypto Wars of the 1990s by crippling encryption with the introduction of backdoors.
Yet increasingly, technology providers are deliberately designing their products and services so that only the user, and not law enforcement, has access to content – even when criminal activity is clearly taking place. This type of “warrant-proof” encryption adds little to the security of the communications of the ordinary user, but it is a serious benefit for those who use the internet for illicit purposes.
”Adds little to the security of the communications of the ordinary user.” That’s the level of contempt these people have for the rest of us.
Zoom Backtracks, Will Give Free Users Encryption Protection
After a lot of negative attention from press and privacy advocates, Zoom has backtracked on its stance. It will provide free users with end-to-end encryption, a feature previously limited to paying customers.
The company said that free users will have to verify themselves with a phone number in a one-time process. It claimed that this will stop bad actors from creating multiple abusive accounts.
Zoom is also releasing an updated design of its end-to-end encryption solution on GitHub that intends to achieve a balance between “the legitimate right of all users to privacy and the safety of users.”
Good to see Zoom do this.
Security Friday: Ransomware, DNS Options – TMO Daily Observations 2020-06-12
Andrew Orr joins host Kelly Guimont to discuss Security Friday news including a new ransomware attack and some alternative DNS options.
IBM Releases Homomorphic Encryption Toolkit for iOS, macOS
IBM has released a toolkit for iOS and macOS to help developers to easily add homomorphic encryption into their programs.
While the technology holds great potential, it does require a significant shift in the security paradigm. Typically, inside the business logic of an application, data remains decrypted, Bergamaschi explained. But with the implementation of FHE, that’s no longer the case — meaning some functions and operations will change.
In other words, “There will be a need to rewrite parts of the business logic,” Bergamaschi said. “But the security that you gain with that, where the data is encrypted all the time, is very high.”
If you haven’t added homomorphic encryption to your technology watch list, be sure to do so. As I wrote in the past, this type of encryption lets a company perform computations on data while still keeping that data encrypted.
HideMyAss VPN 2-Yr Subscription: $79.99
We have a deal on a 2-year subscription to HideMyAss, a VPN featuring 256-bit AES encryption and a strict no logging policy. The subscription is good for unlimited installs with up to 5 connections at once, and 2-years is $79.99 through our deal.