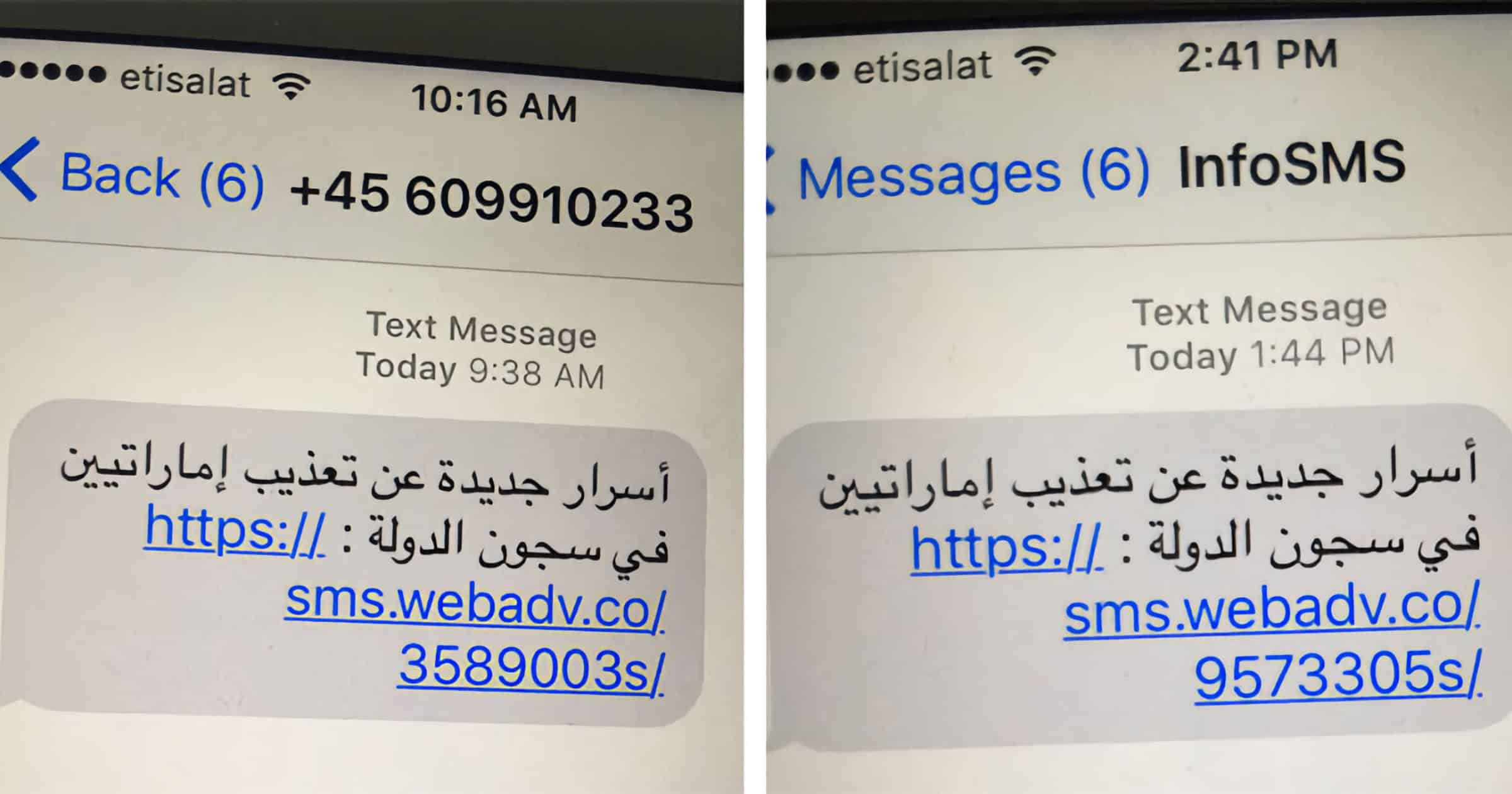
Spain’s prime minister’s iPhone fell victim to Pegasus spyware, as did the defense minister’s, proving the spyware is still alive and well.
NSO Group
Israel Wants to Know if Pegasus Spyware Used in Own Country
The government of Israel is opening an investigation to determine if its own law enforcement used Pegasus spyware against Israeli businesses.
NSO Targets: A List of People Infected With Pegasus Spyware
Omer Benjakob has put together a helpful list of NSO targets that includes every individual believed to have been infected with the group’s Pegasus spyware.
So far, targets have been found across the world: from India and Uganda to Mexico and the West Bank, with high-profile victims including U.S. officials and a New York Times journalist. Now, for the first time, Haaretz has assembled a list of confirmed cases involving Pegasus spyware.
Hacking US Diplomats in Uganda May Have Led to NSO Group Downfall
ArsTechnica shares the story of how U.S. diplomats in Uganda were hacked by Pegasus, a spyware tool from NSO Group.
Israeli and US officials declined to confirm that the Ugandan hack directly triggered a decision to blacklist NSO. But one US official who discussed the issue with Israel’s defense ministry said: “Look at the entire sequence of events here—this is careful, not by chance.” He added that putting NSO, one of the jewels of Israel’s tech community, on a US blacklist was designed to “punish and isolate” the company.
Adele's Shuffle Challenge and Apple's Stand on State-Sponsored Spyware, with Jeff Gamet - ACM 562
Bryan Chaffin and Jeff Gamet talk about Adele’s desire that we not shuffle her albums. They also look at Apple’s public stand against state-sponsored spyware.
Apple Begins to Alert Victims of NSO Group's Pegasus Spyware
On Tuesday Apple revealed it is suing NSO Group for its Pegasus spyware that attacks iPhone users. TechCrunch writes that the company has begun alerting victims.
The alerts — which Apple says are designed to inform and assist users who may have been targeted by state-sponsored attackers — were also sent to a number of users in El Salvador. This includes 12 employees from El Faro, an online digital newspaper that has been notoriously critical of the government, as well as two leaders of civil society organizations and two opposition politicians.
Apple Sues NSO Group Over Endangering iOS Users With Spyware
On Tuesday Apple announced it had filed a lawsuit against NSO Group and its parent company. The goal is to hold it accountable for its spyware.
Germany Secretly Purchased NSO Group Spyware 'Pegasus'
A report reveals that Germany’s Federal Criminal Police Office (BKA) had purchased the Pegasus spyware to monitor suspects.
NSO Group Tools Used to Hack Journalist Omar Radi’s iPhone
An investigation from Amnesty International reveals that NSO Group tools were used to target human rights journalist Omar Radi via his iPhone.
Through our investigation we were able to confirm that his phone was targeted and put under surveillance during the same period he was prosecuted. This illustrates how human rights defenders (HRDs) may often have to deal with the twin challenges of digital surveillance alongside other tactics of criminalisation at the hands of Moroccan authorities leading to a shrinking space for dissent.
The same NSO Group that hopes to woo American law enforcement with its dazzlingly array of hacking tools.
Facebook Tried to Buy a Hacking Tool to Spy on iPhone Users
According to court filings, when Facebook was in the early stages of building its spyware VPN called Onavo Protect, it noticed that it wasn’t as effective on Apple devices as it was on Android. So Facebook approached a hacking group called NSO Group to use its Pegasus malware.
According to the court documents, it seems the Facebook representatives were not interested in buying parts of Pegasus as a hacking tool to remotely break into phones, but more as a way to more effectively monitor phones of users who had already installed Onavo.
NSO Group Tool Harvests Targeted iCloud Data
Israel-based NSO Group claims it can harvest iCloud data in targeted attacks. It’s said to be a version of the Pegasus spyware.
Attackers using the malware are said to be able to access a wealth of private information, including the full history of a target’s location data and archived messages or photos, according to people who shared documents with the Financial Times and described a recent product demonstration.
When questioned by the newspaper, NSO denied promoting hacking or mass-surveillance tools for cloud services, but didn’t specifically deny that it had developed the capability described in the documents.
A Fix For That Scary WhatsApp Exploit is Live
An Israeli firm called NSO Group used a WhatsApp exploit to inject spyware on target devices. A fix for the exploit is live.
Given the stealthy way the attack was attempted, it’s impressive that WhatsApp caught it as quickly as they did. Engineers at Facebook have been busy sorting this one out over the weekend…Named CVE-2019-3568…affected versions include…WhatsApp for iOS prior to v2.19.51, WhatsApp Business for iOS prior to v2.19.51.
iPhone Spyware Used to Attack Saudi Dissidents
The Saudi regime is known for attacking Saudi dissidents, and iPhone spyware could have helped them do so with the help of NSO Group.