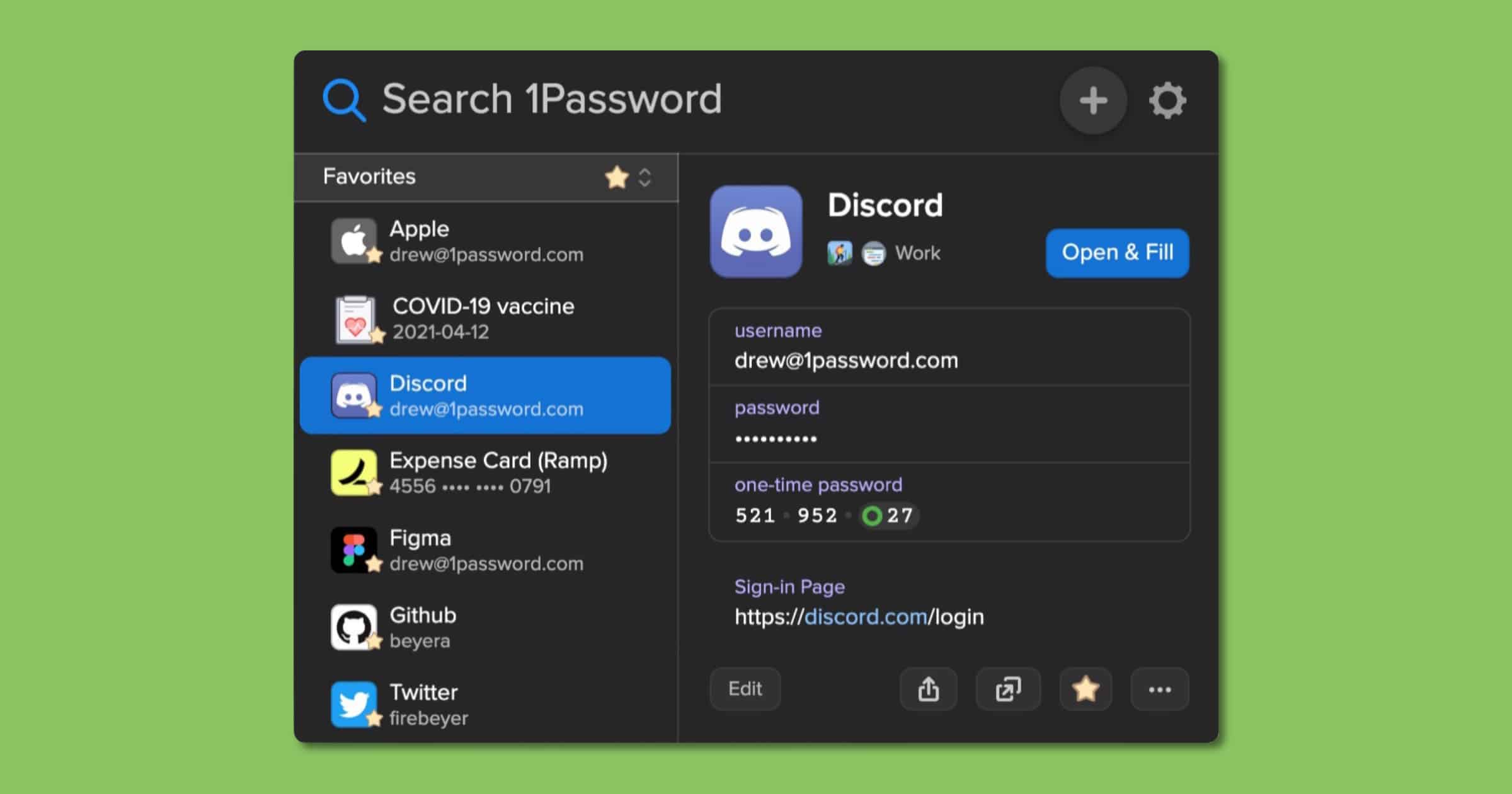
AgileBits announced on Wednesday that its 1Password browser extension supports biometric unlocking for Touch ID and others.
Security Friday
Flaw Found in M1 Chip Lets Apps Secretly Communicate
A security researcher found a flaw baked into M1 chips that could let any two apps to secretly exchange data.
Security Friday: Protected Photo Tips – TMO Daily Observations 2021-05-14
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and tips on how to store a photo (like a photo of a vaccination card).
What’s Wrong With AirTags? Stalkers and Security
One report about AirTag on Thursday show that more security researchers are exploring the device, and another says it is a “gift to stalkers.”
President Biden Signs Order to Improve U.S. Cybersecurity
After the attack on Colonial Pipeline, President Biden has signed an executive order to improve the nation’s cybersecurity.
The executive order requires IT service providers to share certain breach information with the government, modernizes and implements stronger cybersecurity standards in the federal government, establishes security standards for development of software sold to the government and will create an “energy star” label so that consumers can better determine whether software was developed securely.
Security Researcher Hacks Apple’s ‘Find My’ Network
Researcher Fabian Bräunlein found that Apple’s Find My location network can be used to “upload arbitrary data to the internet.”
Being inherent to the privacy and security-focused design of the Find My Offline Finding system, it seems unlikely that this misuse can be prevented completely.
CIDA Warns of New Ransomware ‘FiveHands’
FiveHands has been around since January but was recently used in a successful attack against an unknown organization.
Attackers were targeting unpatched SonicWall Secure Mobile Access SMA 100 remote access products, for which patches were released in February. The publicly available tools the group users including the SoftPerfect Network Scanner for Discovery and Microsoft’s own remote administration program, PsExec.exe and its related ServeManager.exe.
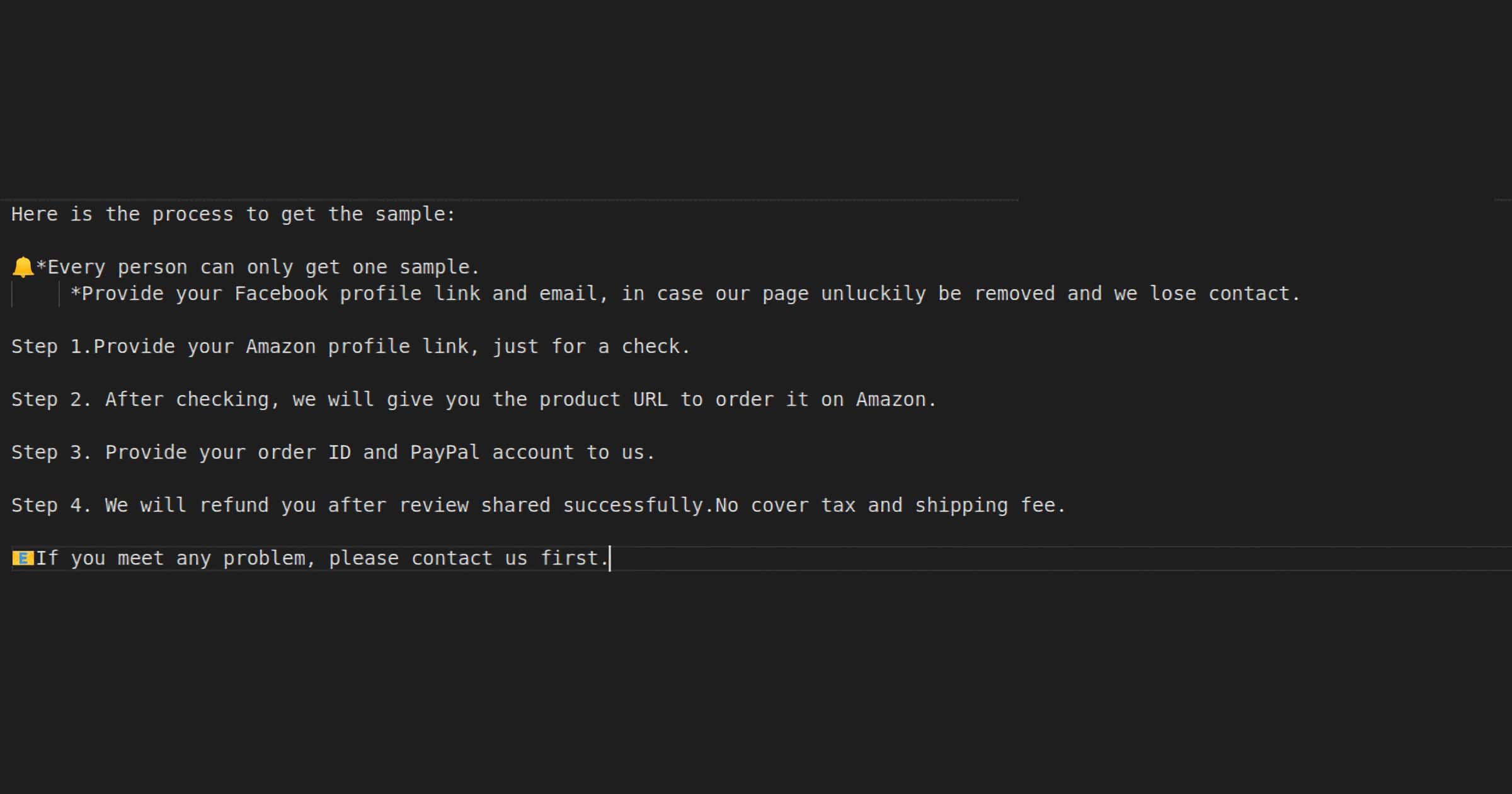
Amazon Data Breach Exposes 200,000 Fake Reviewers
Security researchers at SafetyDetectives found an insecure ElasticSearch database that potentially uncovers over 200,000 fake Amazon reviewers.
These Amazon vendors send to reviewers a list of items/products for which they would like a 5-star review. The people providing the ‘fake reviews’ will then buy the products, leaving a 5-star review on Amazon a few days after receiving their merchandise.
Upon completion, the provider of the fake review will send a message to the vendor containing a link to their Amazon profile, along with their PayPal details.
These are the Most Data-Hungry Health and Fitness Apps
A recent study examined privacy policies of the top health and fitness apps to determine which ones track the most data.
Tor Exit Nodes Were Attacked in February 2021
A new report from Hacker News says that an unknown attacker managed to control over 27% of Tor exit nodes in February 2021.
“The entity attacking Tor users is actively exploiting tor users since over a year and expanded the scale of their attacks to a new record level,” an independent security researcher who goes by the name nusenu said in a write-up published on Sunday. “The average exit fraction this entity controlled was above 14% throughout the past 12 months.”
GitHub Adds Support for Security Keys Over SSH
GitHub announced on Monday that it enabled support for two-factor authentication security keys when members use them over SSH.
When used for SSH operations, security keys move the sensitive part of your SSH key from your computer to a secure external security key. SSH keys that are bound to security keys protect you from accidental private key exposure and malware. You perform a gesture, such as a tap on the security key, to indicate when you intend to use the security key to authenticate. This action provides the notion of “user presence.”
Security Friday and Facebook's Relationships – TMO Daily Observations 2021-05-07
Andrew Orr joins host Kelly Guimont for Security Friday’s news, including Facebook’s latest move involving your data.
Many Top VPN Apps Have Inaccurate Privacy Labels
An analysis of 49 VPN apps in the App Store shows that many of them have inaccurate privacy labels, and others didn’t have a label at all.
Finnish Mental Health Startup Vastaamo Leaked Patient Data
Vastaamo ran the largest network of private mental-health providers in Finland. William Ralston tells the story on WIRED, and how hackers used the data to threaten patients.
A security flaw in the company’s IT systems had exposed its entire patient database to the open internet—not just email addresses and social security numbers, but the actual written notes that therapists had taken. A group of hackers, or one masquerading as many, had gotten hold of the data.
What an incompetent company. No anonymization of patient records, no encryption of data. In other words, unfortunately common. Two developers hired at Vastaamo were even arrested in a previous security breach.
Security Friday: Zero Day, Passwords, and More! – TMO Daily Observations 2021-04-30
Andrew Orr joins host Kelly Guimont to discuss Security Friday news, including a credit bureau data leak, OS updates, and some password items.
IRS Asks For Help to Hack Hardware Cryptocurrency Wallets
The IRS is asking for help to hack into hardware cryptocurrency wallets that could be useful in criminal investigations.
The decentralization and anonymity provided by cryptocurrencies has fostered an environment for the storage and exchange of something of value, outside of the traditional purview of law enforcement and regulatory organizations. There is a portion of this cryptographic puzzle that continues to elude organizations—millions, perhaps even billions of dollars, exist within cryptowallets.
Experian’s API Exposed Credit Scores for Anyone to Discover
Credit bureau Experian recently fixed a flaw in its API that let anyone find a credit score of a person by typing in their name and mailing address.
Demirkapi declined to share with Experian the name of the lender or the website where the API was exposed. He refused because he said he suspects there may be hundreds or even thousands of companies using the same API, and that many of those lenders could be similarly leaking access to Experian’s consumer data.
Install macOS 11.3 ASAP to Patch a Huge Security Flaw
Apple released the newest versions of its operating systems on Monday, and macOS 11.3 patches a major security flaw.
Security Friday, Bad News All Around – TMO Daily Observations 2021-04-23
Andrew Orr joins host Kelly Guimont for the latest in Security Friday news, and this week there’s enough bad news for everyone to share!
Security Friday and a Hitchhiker's Guide – TMO Daily Observations 2021-04-16
Andrew Orr joins host Kelly Guimont to discuss Security Friday news, and a very helpful Hitchhiker’s Guide (not that one).
Security Friday: Exploits and Scammers – TMO Daily Observations 2021-04-09
Andrew Orr joins host Kelly Guimont to discuss (good) Security Friday news, including an in-depth look at phone scammers and tactics to stop them.
Security Friday: Privacy vs Security, App Tracking Updates – TMO Daily Observations 2021-04-02
Andrew Orr joins host Kelly Guimont to discuss new App Tracking Transparency news, other updates, and the difference between security and privacy.
Security Friday: News and Hardware Keys – TMO Daily Observations 2021-03-19
Andrew Orr joins host Kelly Guimont to discuss the abundance of news and updates this week, and explain what a hardware key is for your accounts.
Security Friday and HomeKit Cameras – TMO Daily Observations 2021-03-12
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and chat about HomeKit Secure Video and how to have a camera only you can see.