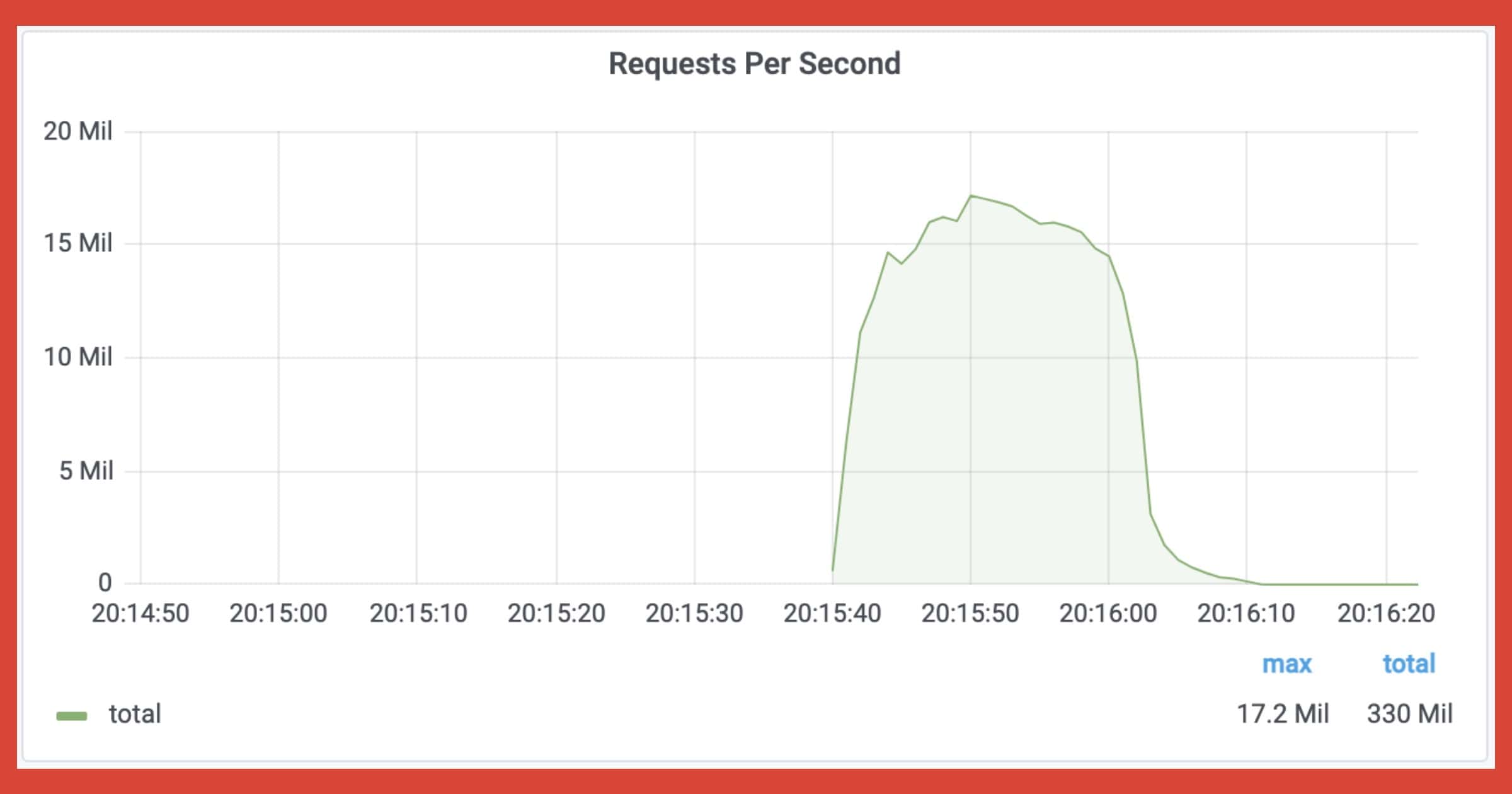
Netflow data refers to IP network traffic that can be collected as it enters or exits an interface. Using this aggregate data, it’s possible to trace network traffic even if a person uses a VPN. Internet service providers sell this information to third parties.
At a high level, netflow data creates a picture of traffic flow and volume across a network. It can show which server communicated with another, information that may ordinarily only be available to the server owner or the ISP carrying the traffic. Crucially, this data can be used for, among other things, tracking traffic through virtual private networks, which are used to mask where someone is connecting to a server from, and by extension, their approximate physical location.