Andrew Orr and Bryan Chaffin join host Kelly Guimont dig deep into password managers, how they work, and why you need one.
Security
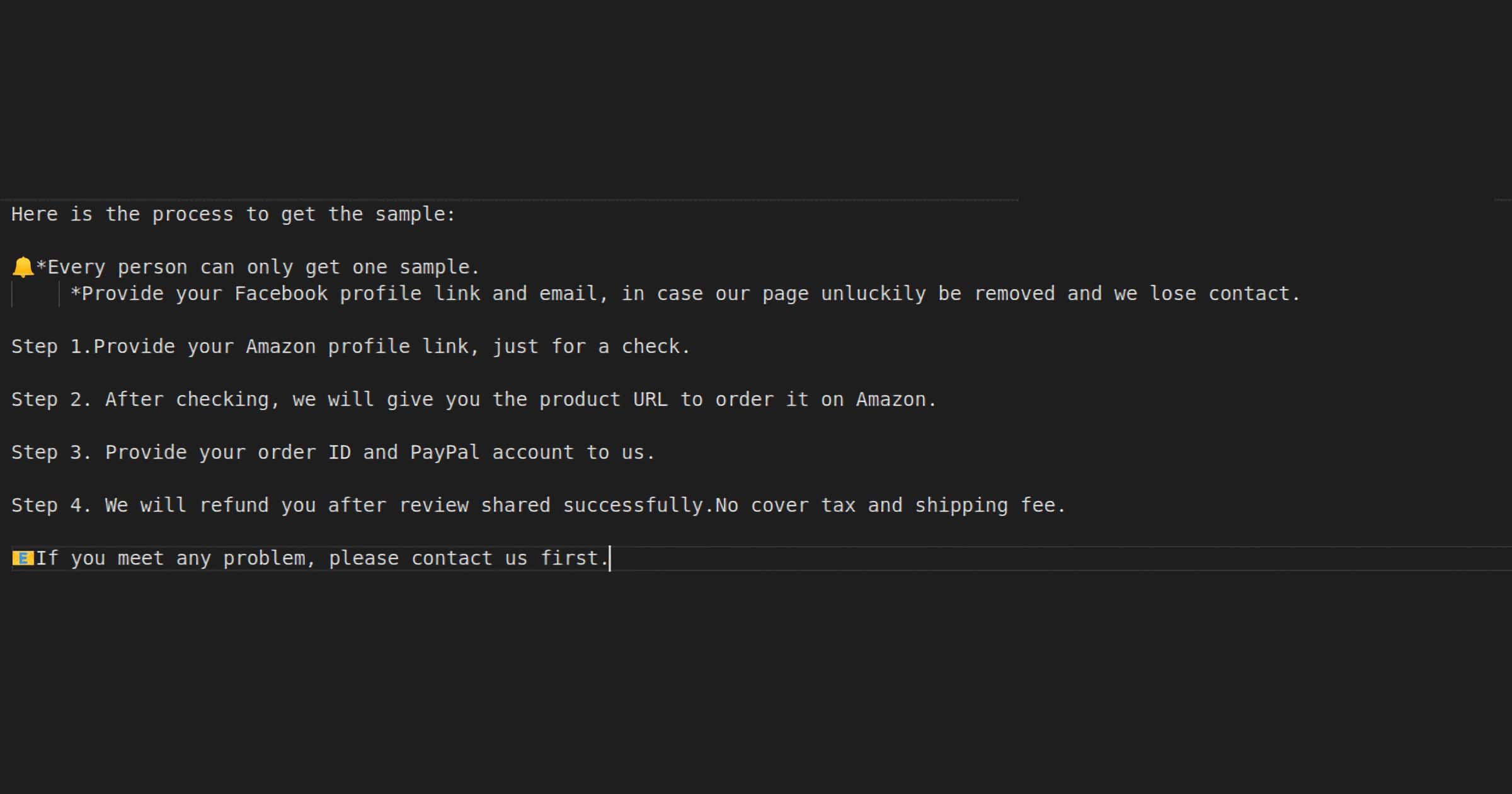
Amazon Data Breach Exposes 200,000 Fake Reviewers
Security researchers at SafetyDetectives found an insecure ElasticSearch database that potentially uncovers over 200,000 fake Amazon reviewers.
These Amazon vendors send to reviewers a list of items/products for which they would like a 5-star review. The people providing the ‘fake reviews’ will then buy the products, leaving a 5-star review on Amazon a few days after receiving their merchandise.
Upon completion, the provider of the fake review will send a message to the vendor containing a link to their Amazon profile, along with their PayPal details.
Tor Exit Nodes Were Attacked in February 2021
A new report from Hacker News says that an unknown attacker managed to control over 27% of Tor exit nodes in February 2021.
“The entity attacking Tor users is actively exploiting tor users since over a year and expanded the scale of their attacks to a new record level,” an independent security researcher who goes by the name nusenu said in a write-up published on Sunday. “The average exit fraction this entity controlled was above 14% throughout the past 12 months.”
GitHub Adds Support for Security Keys Over SSH
GitHub announced on Monday that it enabled support for two-factor authentication security keys when members use them over SSH.
When used for SSH operations, security keys move the sensitive part of your SSH key from your computer to a secure external security key. SSH keys that are bound to security keys protect you from accidental private key exposure and malware. You perform a gesture, such as a tap on the security key, to indicate when you intend to use the security key to authenticate. This action provides the notion of “user presence.”
Rumbling with Gatekeeper — Mac Geek Gab 870
Apple’s protective engines usually do well at protecting our devices, but what happens when they go haywire? It’s time to Rumble, that’s what, and John and Dave are here to help! Listen as they answer your questions, share Cool Stuff Found, push out the Quick Tips and make it easy to learn at least five new things this week!
128 Million Apple Users Unknowingly Downloaded Malware in 2015
Emails published in the Epic v Apple trial on Friday revealed that 128 million users downloaded malware from the App Store in 2015.
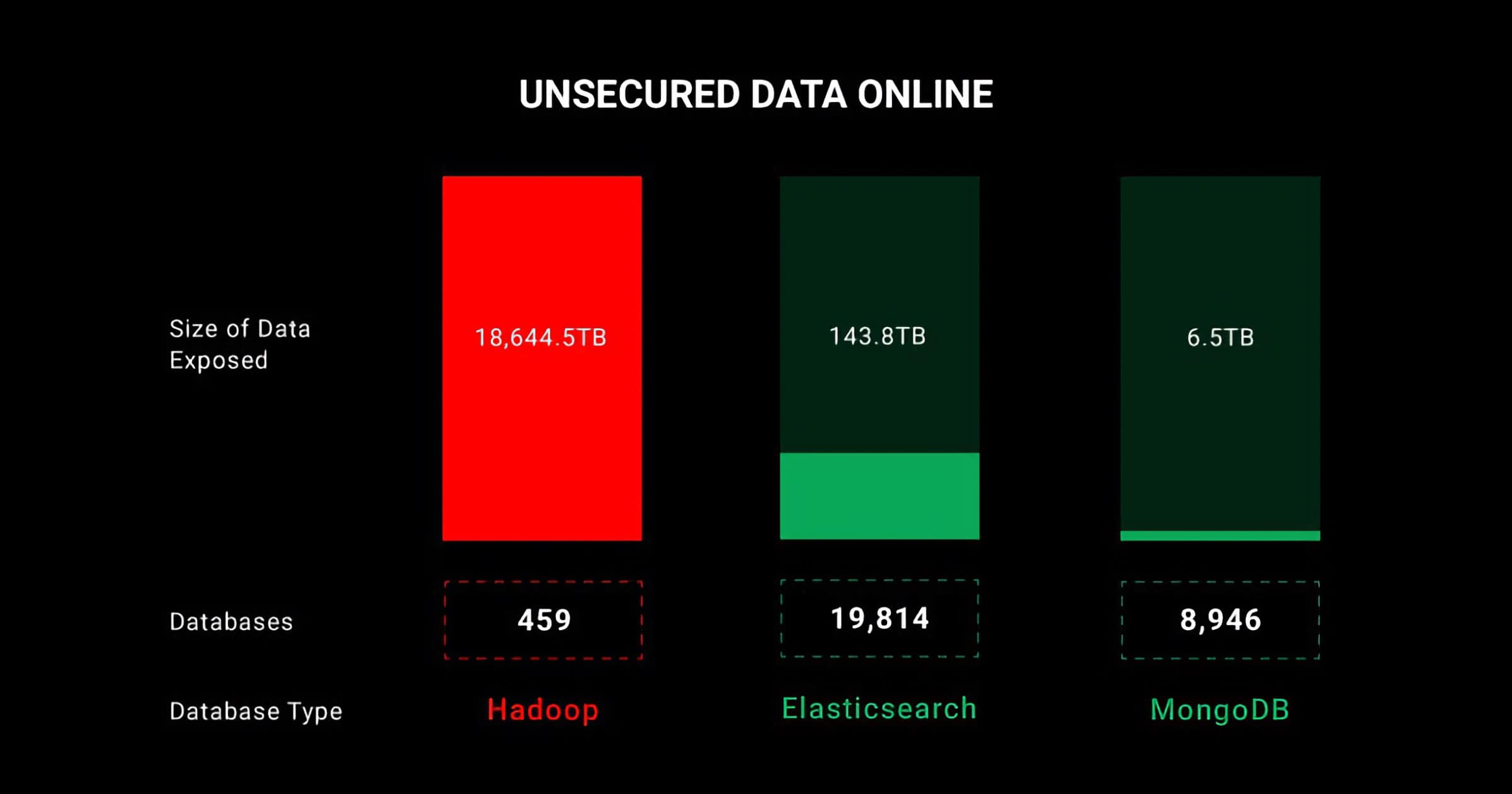
Over 29,000 Databases Expose 19 Petabytes of Data
Many companies aren’t properly securing their databases, like the one I wrote about this morning. But we have some numbers. CyberNews quotes “29,000 unprotected databases worldwide exposing 19 petabytes (19,000 terabytes, 19,000,000 gigabytes, etc) of data.
To conduct this investigation, we used a specialized search engine to scan for open databases of three of the most popular database types: Hadoop, MongoDB, and Elasticsearch. While performing the search, we made sure that the open databases we found required no authentication whatsoever and were open for anyone to access, as opposed to those that had default credentials enabled.
Many Top VPN Apps Have Inaccurate Privacy Labels
An analysis of 49 VPN apps in the App Store shows that many of them have inaccurate privacy labels, and others didn’t have a label at all.
Finnish Mental Health Startup Vastaamo Leaked Patient Data
Vastaamo ran the largest network of private mental-health providers in Finland. William Ralston tells the story on WIRED, and how hackers used the data to threaten patients.
A security flaw in the company’s IT systems had exposed its entire patient database to the open internet—not just email addresses and social security numbers, but the actual written notes that therapists had taken. A group of hackers, or one masquerading as many, had gotten hold of the data.
What an incompetent company. No anonymization of patient records, no encryption of data. In other words, unfortunately common. Two developers hired at Vastaamo were even arrested in a previous security breach.
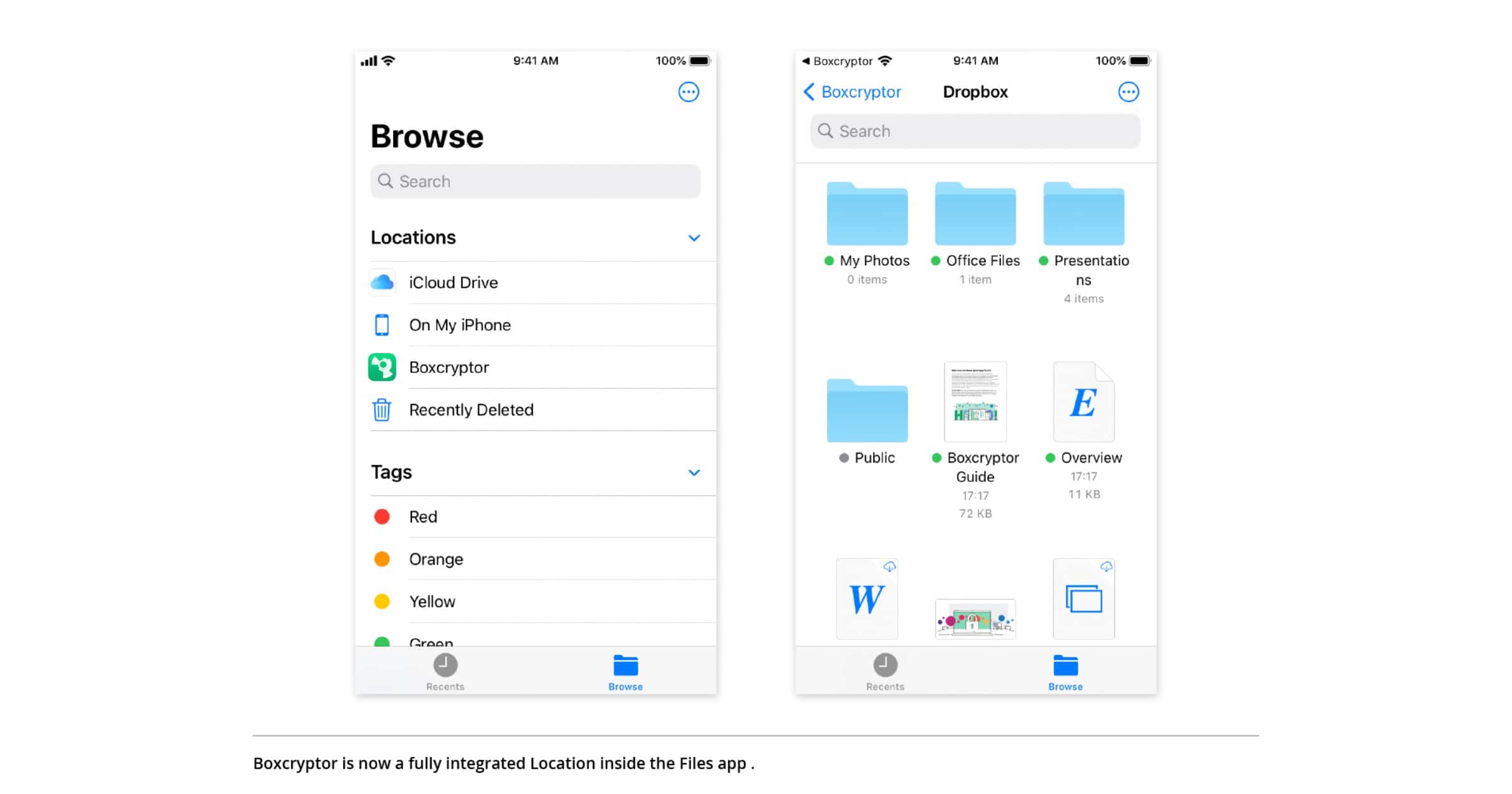
Encrypted Storage App ‘Boxcryptor’ Integrates Better With Files App
Boxcryptor received a major update for iOS and iPadOS that eliminates its own file browser. Instead, you’ll browse through your encrypted files completely within Apple’s Files app. Robert Freudenreich explains the decision: “By taking a ‘Files app first’ approach, we enable the best user experience for working with encrypted files in Apple’s Files app.” The integration with the Files app has been in place since iOS 11. But by eliminating the additional Boxcryptor-owned file browser, the Files app now becomes the exclusive file manager. For users, this primarily means an even simpler workflow.
IRS Asks For Help to Hack Hardware Cryptocurrency Wallets
The IRS is asking for help to hack into hardware cryptocurrency wallets that could be useful in criminal investigations.
The decentralization and anonymity provided by cryptocurrencies has fostered an environment for the storage and exchange of something of value, outside of the traditional purview of law enforcement and regulatory organizations. There is a portion of this cryptographic puzzle that continues to elude organizations—millions, perhaps even billions of dollars, exist within cryptowallets.
Experian’s API Exposed Credit Scores for Anyone to Discover
Credit bureau Experian recently fixed a flaw in its API that let anyone find a credit score of a person by typing in their name and mailing address.
Demirkapi declined to share with Experian the name of the lender or the website where the API was exposed. He refused because he said he suspects there may be hundreds or even thousands of companies using the same API, and that many of those lenders could be similarly leaking access to Experian’s consumer data.
Install macOS 11.3 ASAP to Patch a Huge Security Flaw
Apple released the newest versions of its operating systems on Monday, and macOS 11.3 patches a major security flaw.
Security Friday, Bad News All Around – TMO Daily Observations 2021-04-23
Andrew Orr joins host Kelly Guimont for the latest in Security Friday news, and this week there’s enough bad news for everyone to share!
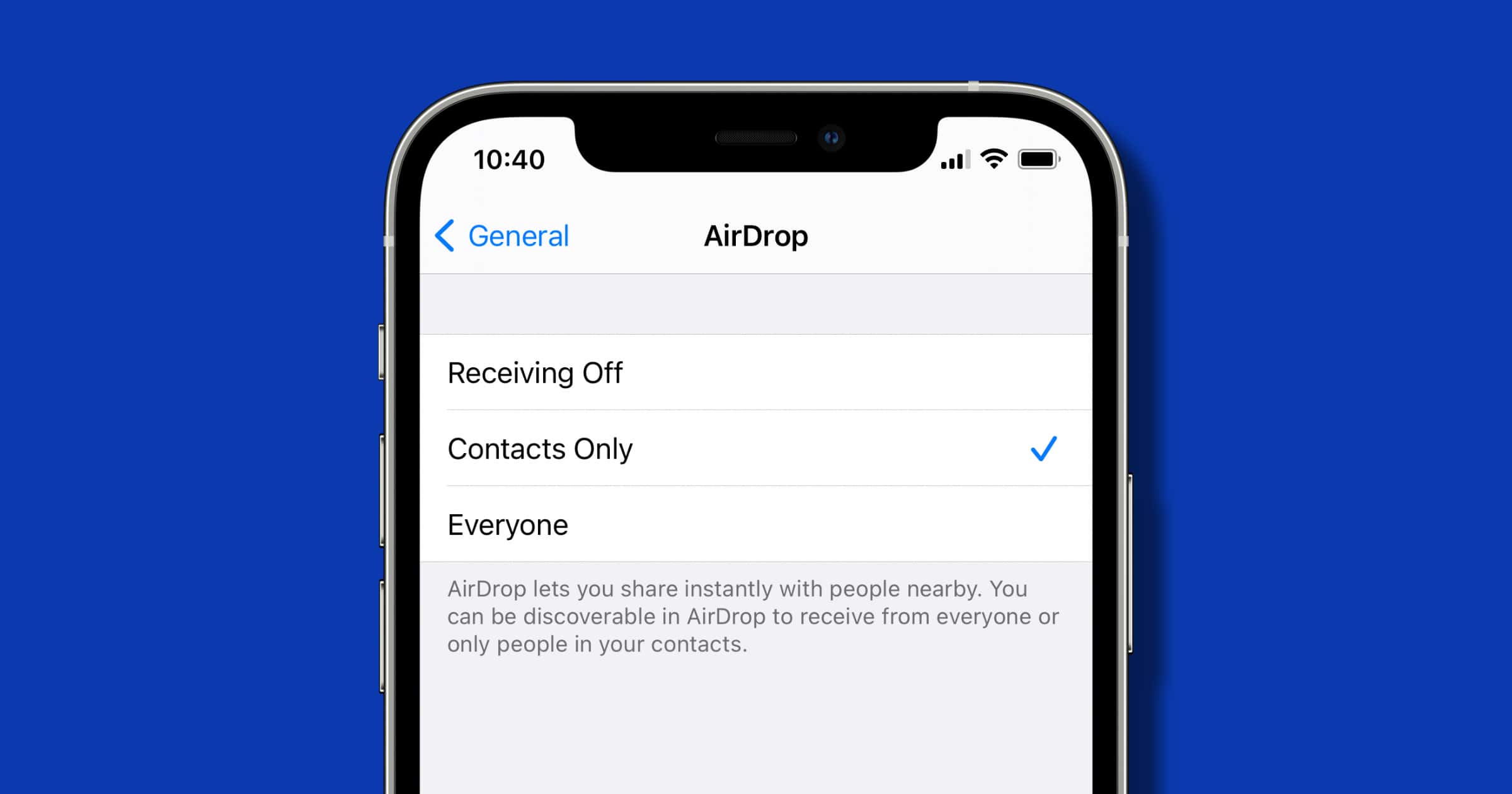
AirDrop Flaw Still Not Fixed After Two years
A team of researchers at TU Darmstadt discovered a flaw in AirDrop that could leak personal data. They notified Apple in May 2019.
Here’s How Signal Broke Into Cellebrite’s Hacking Device
Moxie Marlinspike of Signal wrote on Wednesday how he was able hack into a Cellebrite device. These devices are used by entities like law enforcement to brute force their way into devices like iPhones.
Given the number of opportunities present, we found that it’s possible to execute arbitrary code on a Cellebrite machine simply by including a specially formatted but otherwise innocuous file in any app on a device that is subsequently plugged into Cellebrite and scanned. There are virtually no limits on the code that can be executed.
A fascinating write-up. One can only imagine the thrill of taking a walk, seeing a package fall out of a truck, and finding out that it’s a Cellebrite device.
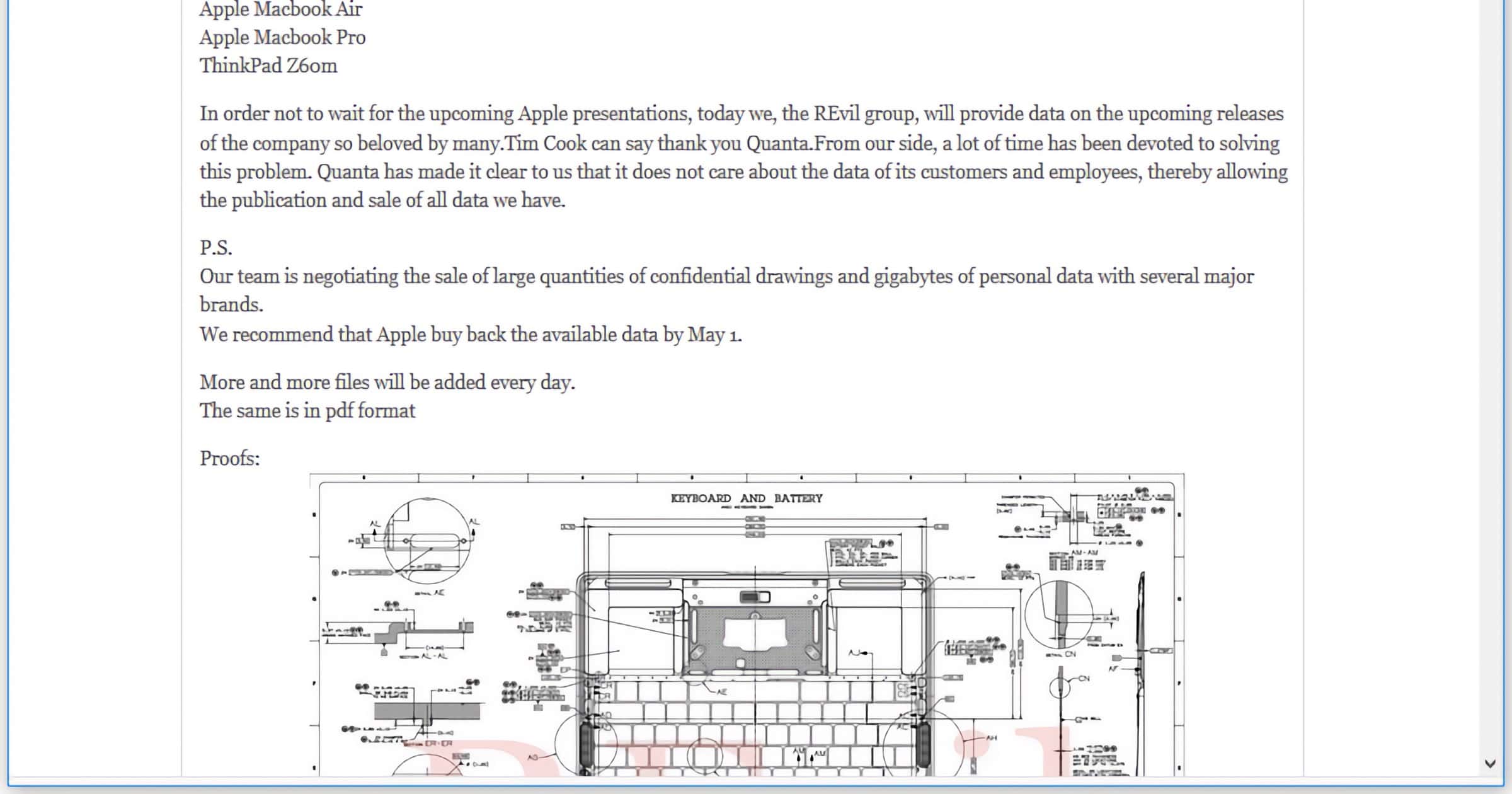
REvil Ransomware Crew Extorts Apple With Device Schematics
Timed with Apple’s spring event on Tuesday, the group behind REvil ransomware claims to have secret device schematics hacked from Quanta Computer.
Geico Data Breach Exposed Driver’s Licenses in Early 2021
Geico revealed a data breach that occurred on its systems and hackers accessed driver’s licenses.
The insurance giant did not say how many customers were affected by the breach but said the fraudsters accessed customer driver’s license numbers between January 21 and March 1. Companies are required to alert the state’s attorney general’s office when more than 500 state residents are affected by a security incident.
Geico said it had “reason to believe that this information could be used to fraudulently apply for unemployment benefits in your name.”
Malvertising Campaign ‘Tag Barnakle’ Infected 120 Ad Servers
First discovered a year ago, malvertising campaign Tag Barnakle has infected over 120 ad servers to insert malicious code into ads.
Stein says that while last year Tag Barnakle had targeted users of desktop browsers with redirects to malware download sites, over the past year, the gang has switched to going after mobile users and redirecting them to online scams peddling various scammy products.
‘The New Oil’ Website is a Resource for Privacy
The creator of The New Oil shared his website that gives people resources on privacy. But it’s not just a list of private tools to use. Instead the goal is to give people context and explain concepts like data breaches, why strong passwords matter, encryption, and more.
Most of us are not strangers to the concept of surveillance capitalism and targeted advertising. Most of us don’t particularly care, either. After all, who wouldn’t want relevant ads for movies or products that might actually appeal to you or improve your life? The thing is, most of us don’t understand the aggressive measures these companies go to to create those marketing profiles, or the devastating effects they can have on people.
Investigative Report Reveals the Untold Story of the SolarWinds Cyberattack
We have a bit more news about the SolarWinds hack this week. NPR has wrapped up an investigation and reveals the “behind-the-scenes” story.
“Imagine those Reese’s Peanut Butter Cups going into the package and just before the machine comes down and seals the package, some other thing comes in and slides a razor blade into your Reese’s Peanut Butter Cup,” he said. Instead of a razor blade, the hackers swapped the files so “the package gets sealed and it goes out the door to the store.”
Security Friday and a Hitchhiker's Guide – TMO Daily Observations 2021-04-16
Andrew Orr joins host Kelly Guimont to discuss Security Friday news, and a very helpful Hitchhiker’s Guide (not that one).
Reddit Announces Public Bug Bounty Program
For the past three years Reddit has maintained a privacy bug bounty program for cybersecurity researchers with HackerOne. On Thursday the company announced a public program.
With our continued growth and visibility, we’re now ready to make the program public and expand the participation to anyone wanting to make a meaningful security impact on Reddit. As we scale the program, our priority will remain focused on protecting the privacy of our user data and identities. We know each security researcher has their own skills and perspective that they bring to the program, and we encourage anyone to submit a report that shows security impact. We’re super excited to hit this milestone and have prepared our team for what’s to come.
U.S. Sanctions Russia Over SolarWinds Cyberattack
The U.S. has imposed sanctions against Russia for election interference and its role in the devastating cyberattack known as SolarWinds.