Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates, and offer some tips on how to avoid credit card shenanigans.
Security
Spotify Resets User Passwords Over Data Leak
Spotify has reset an unknown number of user passwords after a bug in its system exposed private data to business partners.
In a data breach notification filed with the California attorney general’s office, the music streaming giant said the data exposed “may have included email address, your preferred display name, password, gender, and date of birth only to certain business partners of Spotify.” The company did not name the business partners, but added that Spotify “did not make this information publicly accessible.”
Fortunately, those like me who created a Spotify account using Sign In with Apple shouldn’t have too much information leaked.
Hackers Hide Credit Card Web Skimmer Inside Image Metadata
MalwareBytes reports that hackers are using a new trick to skim credit card data form websites using a skimmer hidden inside image metadata.
We found skimming code hidden within the metadata of an image file (a form of steganography) and surreptitiously loaded by compromised online stores. This scheme would not be complete without yet another interesting variation to exfiltrate stolen credit card data. Once again, criminals used the disguise of an image file to collect their loot.
A devious, clever hack.
Apple Might Block Apps That do Not Comply With New Privacy Feature
Apple could block apps from the App Store if they fail to meet comply with its new privacy requirements, Craig Federighi has warned.
Apple and Cloudflare Created a New DNS Protocol
Apple and Cloudflare have teamed up to create a new DNS protocol called Oblivious DNS-over-HTTPS, or ODoH.
Scam Calls About Suspicious iCloud Activity are Appearing
Calls from scammers pretending to be from Apple and Amazon have been appearing lately. In the case of Apple, some of them mention suspicious iCloud activity.
In both scenarios, the scammers say you can conveniently press 1 to speak with someone (how nice of them!). Or they give you a phone number to call. Don’t do either. It’s a scam. They’re trying to steal your personal information, like your account password or your credit card number.
Here are the Top 5 Encrypted Cloud Storage Services
To accompany his roundup of encrypted DNS services, Andrew has a roundup of the best encrypted cloud storage services.
5 Encrypted DNS Services to Use on iOS and macOS
Switching from your ISP’s DNS is good because your browsing history could be sold. Here are five encrypted DNS services to use instead.
Twitter Supports Physical Security Keys for Two-Factor Authentication
Twitter announced on Wednesday that its mobile app now supports physical security keys for iPhone and Android. The company added support for these keys in 2018 but people could only use them in a browser. But switching to the WebAuthn protocol brings the method to mobile devices.
Now anyone with a security key set up on their Twitter account can use that same key to log in from their mobile device, so long as the key is supported. (A ton of security keys exist today that work across different devices, like YubiKeys and Google’s Titan key.)
Inside the iPhone Wi-Fi Exploit Apple Patched This Year
Google’s security firm Project Zero published a report on Tuesday detailing an iPhone Wi-Fi exploit that Apple patched earlier this year in iOS 13.5. It’s a long, 30,000 word blog post, but ArsTechnica has a good breakdown.
Beer developed several different exploits. The most advanced one installs an implant that has full access to the user’s personal data, including emails, photos, messages, and passwords and crypto keys stored in the keychain. The attack uses a laptop, a Raspberry Pi, and some off-the-shelf Wi-Fi adapters.
This Terminal Command Can Bypass Mac Privacy Protections
A UNIX command line tool called “ls” can be used to bypass Mac privacy protections like TCC (Transparency, Consent, and Control) and the sandbox. This provides unauthorized access to file metadata in directories that are supposed to be protected
I continue to believe that macOS “security” is mainly theater that only impedes the law-abiding Mac software industry while posing little problem for Mac malware. It doesn’t take a genius hacker to bypass macOS privacy protections: calling “ls” is a script kiddie level attack.
It affects macOS Big Sur, Catalina, and Mojave.
Security Friday on Wednesday, Black Friday Deals – TMO Daily Observations 2020-11-25
Andrew Orr joins host Kelly Guimont to discuss Security Friday news (even though it’s Wednesday) and point out some Black Friday deals.
Amazon Sidewalk Shares Your Wi-Fi With Neighbors
Amazon Sidewalk is a new initiative by the company that creates a low-bandwidth network pooled from the personal networks of Amazon device owners.
Amazon Sidewalk is a shared network, coming later this year, that helps devices like Amazon Echo devices, Ring Security Cams, outdoor lights, and motion sensors work better at home and beyond the front door. When enabled, Sidewalk can unlock unique benefits for your device, support other Sidewalk devices in your community, and even open the door to new innovations like locating items connected to Sidewalk.
Of course, there are numerous privacy and security concerns, although Amazon does claim it has “strong encryption” without going into details.
Apple Security Chief Thomas Moyer Indicted in Concealed Weapons Permit Scandal
Thomas Moyer, Apple’s head of global security, is among four people indicted in a concealed weapons permit bribery scandal.
Walmart ‘Jetstream’ Routers Contain Backdoors
Researchers found backdoors found in Jetstream routers that lets a hacker remotely control the router and any device connected to it. This router is sold exclusively at Walmart.
CyberNews reached out to Walmart for comment and to understand whether they were aware of the Jetstream backdoor, and what they plan to do to protect their customers. After we sent information about the affected Jetstream device, a Walmart spokesperson informed CyberNews: “Thank you for bringing this to our attention. We are looking into the issue to learn more. The item in question is currently out of stock and we do not have plans to replenish it.”
Bad news for owners of these routers, but at least Walmart won’t sell them anymore.
Fraud Operation Targets Spotify Users With Leaked Database
In a similar situation to a Facebook scam, researchers uncovered an unsecured database with over 380 million records in a potential Spotify hacking operation.
The origins of the database and how the fraudsters were targeting Spotify are both unknown. The hackers were possibly using login credentials stolen from another platform, app, or website and using them to access Spotify accounts.
Working with Spotify, we confirmed that the database belonged to a group or individual using it to defraud Spotify and its users. We also helped the company isolate the issue and ensure its customers were safe from attack.
Update Google Chrome ASAP to Patch Two Zero Days
Two zero days in Chrome, CVE-2020-16013 and CVE-2020-16017, are “high severity” in nature and users should update the browser as soon as possible. The The Cybersecurity and Infrastructure Security Agency (CISA) says the security flaws are actively being exploited in the wild.
I can confirm that CVE-2020-16013 relates to the V8 JavaScript engine for Chrome and involves an incorrectly handled security check. Exploitation would most likely require an attacker to direct the victim to a malicious web page.
CVE-2020-16017, on the other hand, would appear to be a memory corruption vulnerability within the Chrome website sandboxing feature known as Site Isolation.
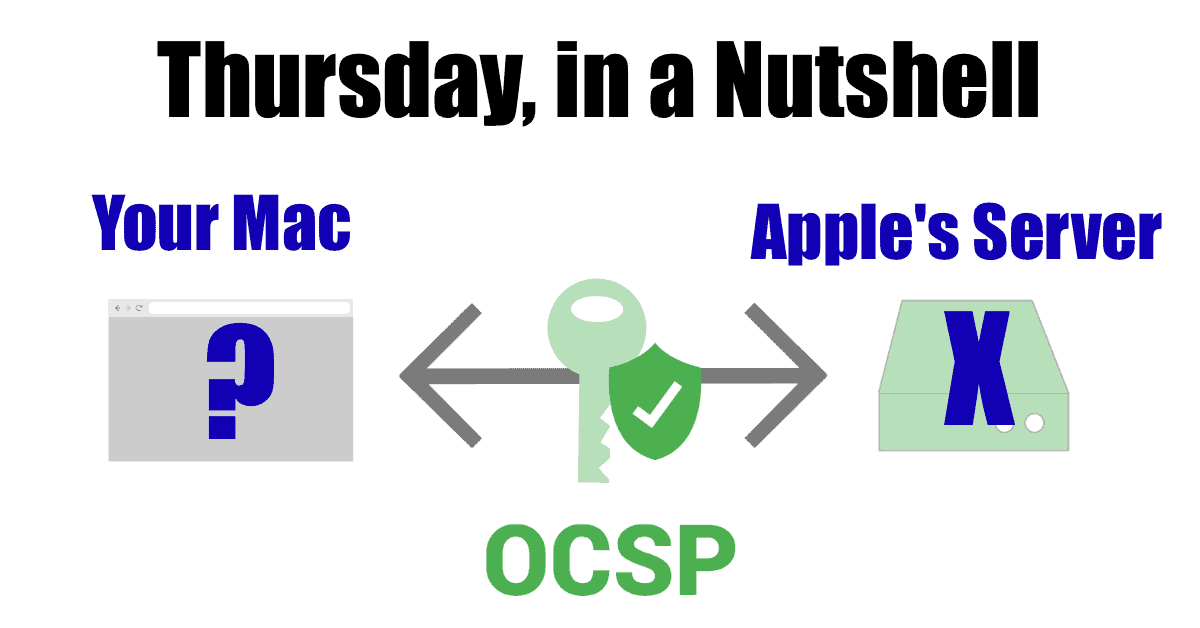
Was Your Mac Slow on Thursday? Apple's OCSP Server Was Likely the Cause
On Thursday, October 12th, right around 3:30pm EST, Apple’s OCSP server stopped responding. On the surface that doesn’t sound like much, but when you stop and realize this is the server responsible for authenticating the certificates at the core of all your apps, it starts to matter.
And matter it did! For about an hour yesterday, Mac apps wouldn’t launch (or would launch slowly), rebooting was super-slow (for the same reason), and even Zoom connections took minutes to connect.
Facebook Credit Card Scam Exposed via Data Leak
A phishing and credit card fraud operation has been targeting Facebook users and was recently uncovered due to an exposed database.
The fraudsters used the stolen login credentials to share spam comments on Facebook posts via the victims hacked account, directing people to their network of scam websites. These websites all eventually led to a fake Bitcoin trading platform used to scam people out of ‘deposits’ of at least €250.
However, the day after we discovered the database, it was attacked by the ongoing widespread Meow cyberattack, which completely wiped all its data.
Vertafore Data Breach Affects 27.7 Million Texan Drivers
Insurance software company Vertafore disclosed a data breach in which an unknown third-party accessed the personal information of 27.7 million drivers in Texas.
The incident is believed to have taken place sometime between March 11 and August 1, and happened as a result of human error when three data files were inadvertently stored in an unsecured external storage service.
Exposed data included Texas driver license numbers, names, dates of birth, addresses, and vehicle registration histories.
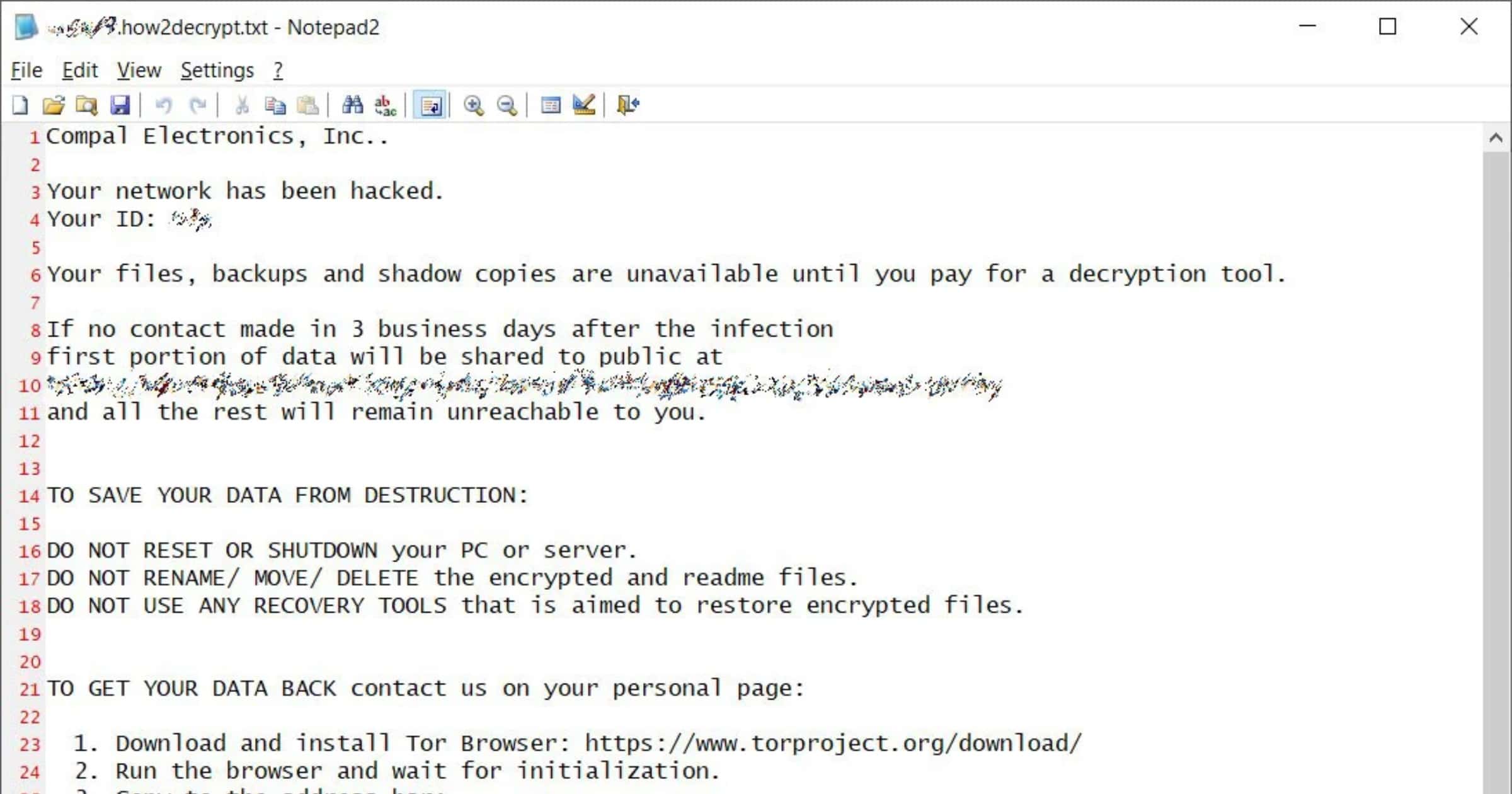
Compal Electronics Suffers DoppelPaymer Ransomware Attack
Computer manufacturer Compal Electronics has been hit by a DoppelPaymer ransomware attack, and the ransom is US$16.7 million.
DoppelPaymer is a ransomware operation known for attacking enterprise targets by gaining access to admin credentials and using them to spread throughout a Windows network. Once they gain access to a Windows domain controller, they deploy the ransomware payloads to all devices on the network.
According to the DoppelPaymer Tor payment site linked to in the ransom note, the ransomware gang is demanding 1,100 Bitcoins, or $16,725,500.00 at today’s prices, to receive a decryptor.
Security Friday, Now With Gift Picks – TMO Daily Observations 2020-11-06
Andrew Orr join host Kelly Guimont for Security Friday news, some ballot measures that passed, and even a security minded gift option.
Here are the Lock Screen Privacy Settings for iPhones and iPads
There are a number of Lock Screen privacy settings you can find on your iPhone and iPad to help secure your devices from people.
Michigan Prop 2 Passes; Police Need a Warrant to Search Your Devices
Voters in Michigan overwhelmingly passed Proposition 2 which adds “electronic data and electronic communications” to the state’s search and seizure laws.
The person, houses, papers, possessions, and electronic data and electronic communications of every person shall be secure from unreasonable searches and seizures. No warrant to search any place or to seize any person or things or to access electronic data or electronic communications shall issue without describing them, nor without probable cause, supported by oath or affirmation.
Translation: Michigan police need a warrant to search your electronic devices. And as a Michigander myself I definitely voted in favor of this.