At this week’s WWDC Keynote, Apple announced iCloud Private Relay, a privacy feature aimed towards further separating you and your browsing activity from people who want to track and collect data about you. iCloud Private Relay works for anyone with an iCloud+ subscription using iOS 15, iPadOS 15, and macOS Monterey, and when enabled it protects all your Safari browsing, all DNS queries, and any insecure web traffic from other apps.
How does iCloud Private Relay Work?
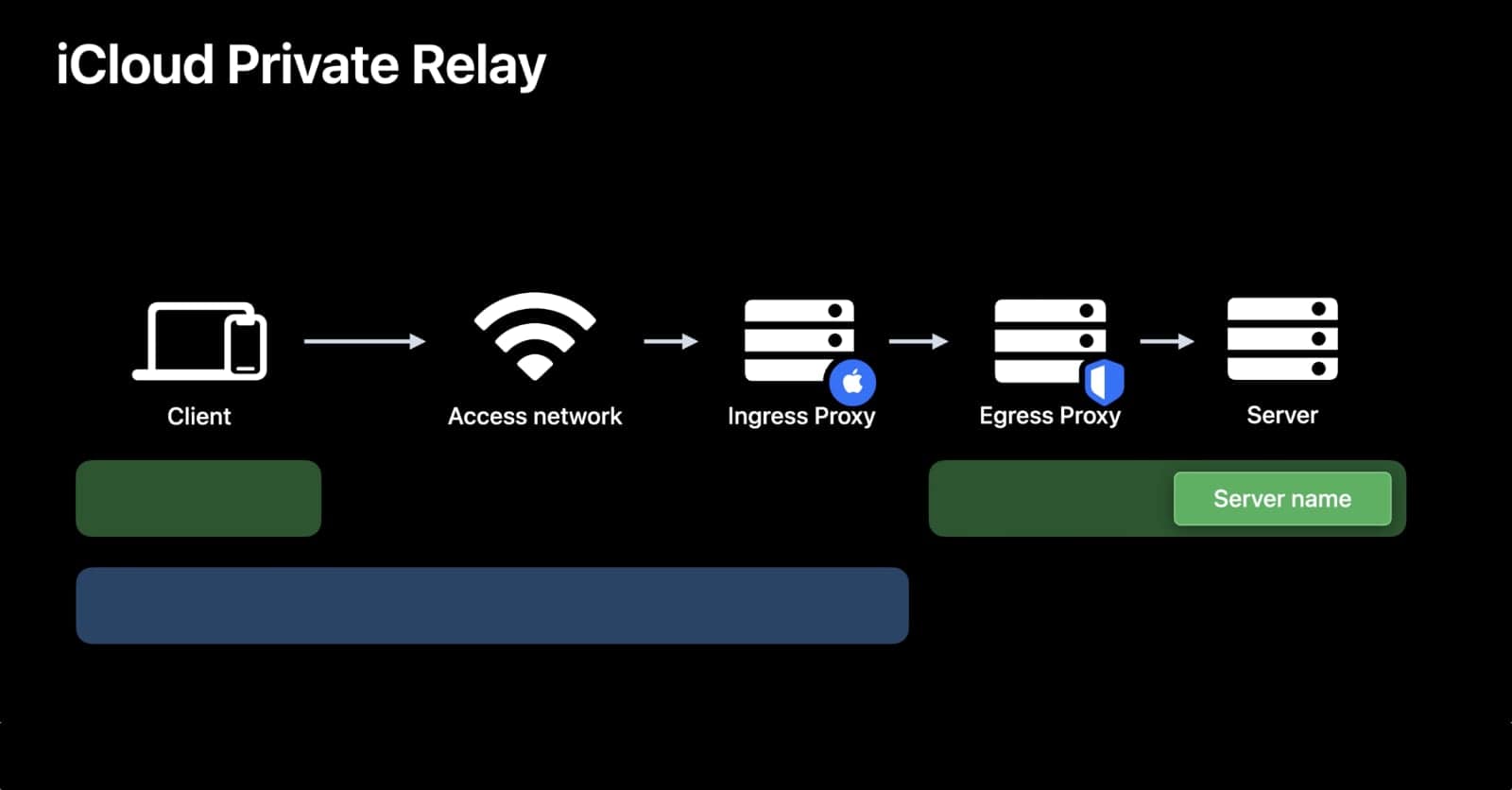
Apple’s iCloud Private Relay works similar to a VPN in that it routes your traffic through other servers, hiding your IP address from the websites you visit, and hiding your traffic from whomever manages your local network. Where it differs is that a VPN is generally just one server between you and the website you’re visiting. With a VPN, your traffic takes the route of You <> VPN Server <> Website. Private Relay adds another server to the mix, which ensures that no one in the chain—not even Apple—can see the whole picture: You <> Apple’s ingress server <> Content Provider’s Egress Server <> Website.
This is, as Apple calls it in their “Get Ready for iCloud Private Relay” WWDC Session on the topic, “Privacy by Design.”
Apple made specific mention that while the “Ingress Proxy” servers are run by Apple, the “Egress Proxy” (aka the server which communicates with the websites you visit) is not controlled by Apple and is under the control of “a (trusted) content provider”. This means that Apple doesn’t know what site(s) you’re visiting, and the third-party content provider doesn’t know who you are.
It’s a pretty ingenious system, and some might notice similarities with the Tor network, though that uses (at least) three servers to further anonymize things. Since anonymity is not the point of Private Relay, two servers are enough to completely satisfy the privacy requirement, and still allows Apple to keep things snappy (Tor, on the other hand, is notoriously slow).
On the speed front, Private Relay uses QUIC (HTTP/3) connections, which happen over UDP port 443, which are engineered to be quite speedy.
What Traffic is Included in iCloud Private Relay?
An iCloud+ user running iOS 15, iPadOS15, or macOS Monterey with Private Relay enabled will have the following traffic routed through Private Relay:
- All Safari browsing
- All DNS queries
- Most App Traffic to insecure websites (aka TCP Port 80, or “http:” traffic).
What’s not included in Private Relay?
Private Relay is bypassed for everything not listed above, including:
- Local Traffic
- Private Domains
- VPNs, Proxies, and other Network Extensions
- Secure, “https:” traffic from your apps.
Who Controls These Egress Servers (aka Exit Nodes)?
Apple hasn’t said who the “content partners” are who run their Egress Servers, but CloudFlare is the only one which has shown up in my tests. I’m testing from one location in New Hampshire, USA, though, so my mileage might be very different from yours. If you see another content partner, let us know in the comments below.
Will Private Relay Make Sites Think I’m Browsing from a Different Location?
When using a VPN, it’s entirely possible for websites to incorrectly guess your location based upon the IP address of the VPN server. Sometimes that’s even the reason to use a VPN.
With Private Relay, Apple offers users two options: “Preserve Approximate Location” (the default), and “Use Broader Location.” By keeping the former option enabled, Private Relay’s Egress Servers will do their level best to use IP addresses which map to your general area, but they definitely won’t get more specific location right, nor would we want them to.
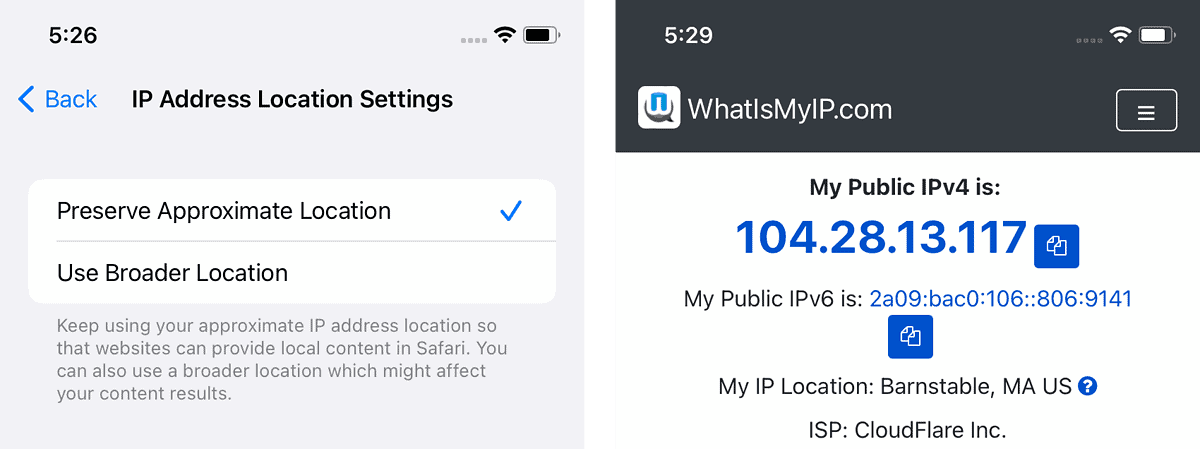
Apple’s suggestion is for apps and websites to explicitly request access to your location, with apps using CoreLocation to get the exact level of granularity they need. Whether websites will do this or not remains to be seen. Some currently do, some currently don’t. I don’t expect that to change!
Will Private Relay Make Me Browse More Slowly?
Technically speaking, any hop introduced into the “chain” of your network connections will slow things down. The real question is: how much will Private Relay slow things down? Based upon my tests with iOS 15 beta 1 on an iPhone XR, I’m not seeing any real negative effects. I got 33ms pings and 300Mbps+ in both directions. For testing, of course, I had to do everything in Safari. Running an app like Speed Test will bypass Private Relay because it uses secure network connections. Until I put macOS Monterey on a Mac I can’t really do a proper, Ethernet-connected bi-directional test.
But the TL;DR: I noticed absolutely no speed difference browsing with Private Relay enabled.
Conclusion
iCloud Private Relay works really well, and seems very well thought out by Apple. Quite frankly, this is one of the reasons I’ll be recommending folks upgrade to the latest operating systems come release-time this fall.
With the web (and beyond) full of fingerprinters and profilers, Private Relay is an elegant solution which should stop most of this in its tracks. Anyone who listens to my podcasts long enough will hear me rant about the “pixel tracking” which companies like Chartable and Podsights are doing, relating your IP address when you download a podcast to your IP address when you visit sponsors’ websites, and Private Relay’s Safari integration neuters this completely, if I’m understanding things correctly.
Thanks for this, Apple. I’m not always a fan of everything you do, but I’m a fan of this!
Excellent summary and deep dive, Dave.
“Anyone who listens to my podcasts long enough will hear me rant about the “pixel tracking” which companies like Chartable and Podsights are doing, relating your IP address when you download a podcast to your IP address when you visit sponsors’ websites, and Private Relay’s Safari integration neuters this completely, if I’m understanding things correctly.”
That’s what I understood.
Given that now there are now officially more authoritarian regimes than there are open democracies worldwide, and that many of these are committed surveillance states, it will be interesting to see how Private Relay is received.