Apple is known for its “walled garden” approach, which promises users some safety in exchange for restrictive practices. One such restriction is with app installations. The company claims you can only do so safely through the App Store. However, tools like ESign circumvent this iOS limitation, allowing you to install apps externally.
You may be wondering whether deviating from the official method is worth the hassle, and what risks this brings. Check below all you need to know about the safety of ESign and how to use it.
What Exactly Is ESign? What Does It Do?
Except for users in the European Union, where other stores are allowed, installing apps from outside the App Store is complex. The procedure as a whole is called “sideloading“, but it comprises multiple smaller processes. ESign helps with some of them.
Understanding App Sideloading on iOS
All iOS apps need to be digitally signed, that is, a “trusted source” needs to certify they’re safe to use. For App Store apps, this is done via the App Store itself. If you want to install an app externally, on the other hand, you need to acquire this digital signature.
There are a few ways of doing that. We won’t explain each one in depth, since this isn’t the main goal of this article. In short, you can either “rent” a certificate, get one from Apple, or use a (limited) official bypass method.
When you “rent” a certificate, you pay a company to provide you the digital signature. Since Apple requires companies only sign their own apps, you can’t be sure the certificates come from legitimate sources. For that reason, they are often revoked, requiring you to re-sign the apps.
There are two types of certificates provided by Apple: free or paid ones. Free certificates come with restrictions, like only signing up to three simultaneous apps and requiring weekly revalidation. To get rid of these limitations, you need to subscribe to a paid Apple Developer account, which costs $99 annually.
The last method requires pretending your device is managed by an organization. Managed devices are work- or school-issued equipment, which, being the property of the employer/school, have some specificities.
One of them is being able to install apps from outside the App Store in an easier way. Many companies, e.g., have dedicated apps for their internal systems, which are better kept off the App Store. The IT department installs these apps, in-person or remotely, for employees to use. By faking an organization — and faking to be a member of it —, you’re able to sideload apps with fewer restrictions.
Emitting Certificates and Signing .IPA Files
Some (but not all) of the “certificate renting” platforms provide the apps already signed and ready for installation. If the service you chose doesn’t, or if you’re using your own certificates, you’ll need to sign them yourself.
We won’t detail how to emit a certificate, since this isn’t the focus of this guide. What you need to know is that you’ll end up with two files. One of them is a .p12 file, the other has a .mobileprovision extension. The .p12 file will be protected by a password you create when generating the certificate, be sure to remember it.
How To Download, Install, and Use ESign on iOS
You can sign apps with ESign in two ways: using ESign’s website or its app. In both cases, the procedure is very similar.
1. Using the ESign Site
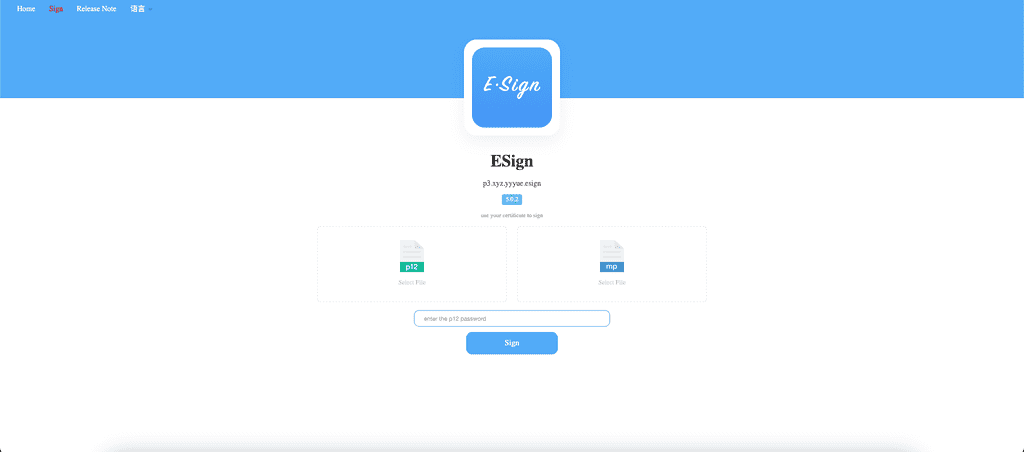
Via ESign’s site, you’ll simply upload the .p12 and .mobileprovision files, and provide the .p12 password. Tap Sign, then upload your app’s .ipa file. After the signing process finishes, you’ll be prompted to install the app.
2. Using the ESign iOS App
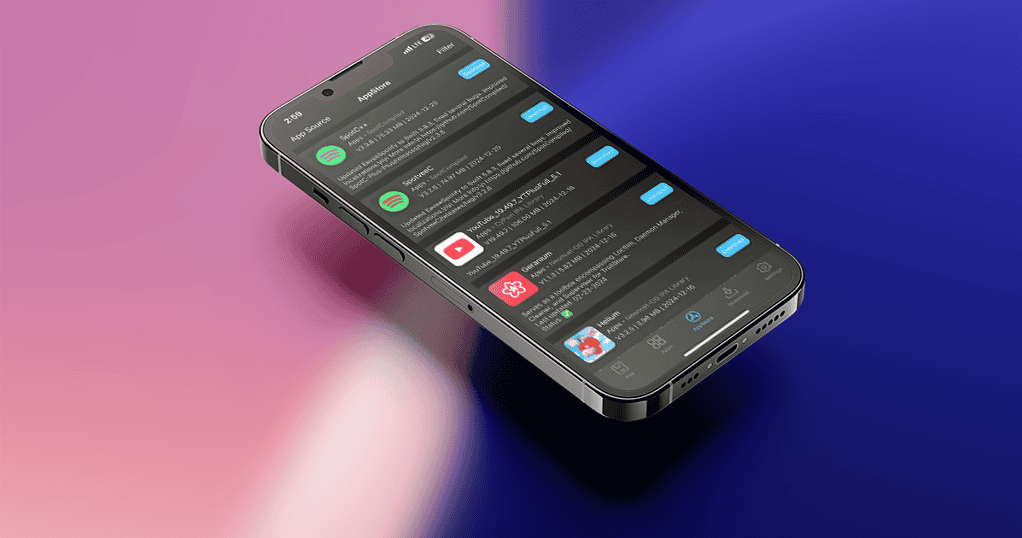
The ESign app makes it easier to download, sign, install, and organize sideloaded apps. It requires, however, a couple of additional steps to be used.
Firstly, you’ll need to choose whether to self-sign the ESign app itself or use a pre-signed version. We’ll cover the former first since it’s likely what most people will prefer. However, it involves some risks.
Installing a Pre-Signed Version of ESign
Time needed: 7 minutes
Before downloading ESign itself, you’ll need a DNS profile that prevents your iPhone from connecting to Apple’s signature verification servers. We’ll not link to any of these profiles, because their integrity can’t be guaranteed. Malicious DNS profiles may redirect traffic to phishing sites, so make sure you trust the website you’ll install yours from. After that, do the following:
- You’ll see a dialog saying This website is trying to download a configuration profile. Tap Allow.
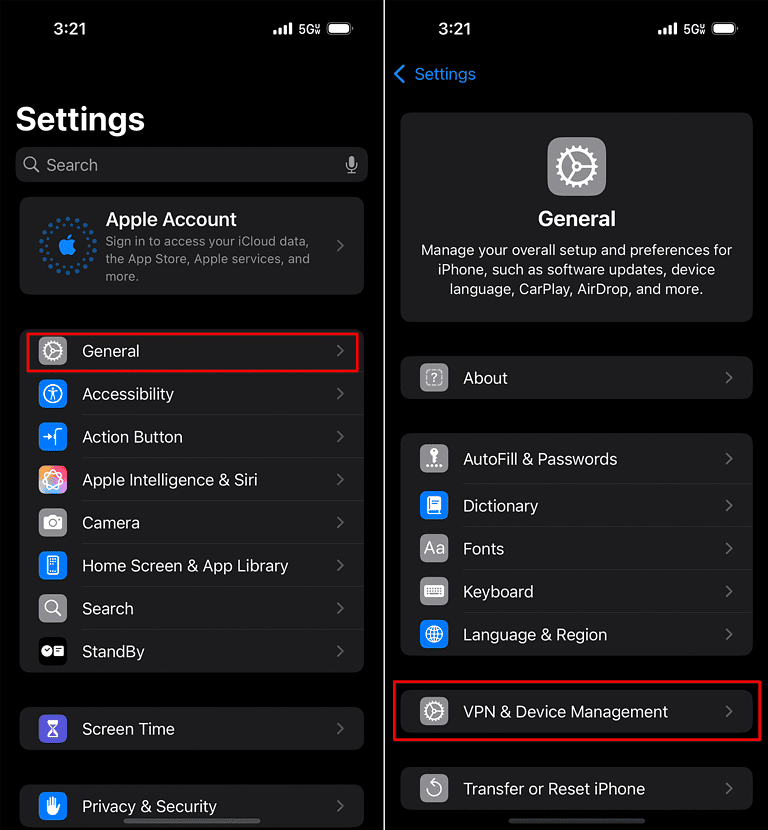
- A Profile Download dialog will appear. The text should be Review the profile in the Settings app if you want to install it.
- Go to Settings > General > VPN & Device Management. The DNS profile will appear under Downloaded Profile. Tap its name, then tap Install in the top-right corner.
 NOTE
NOTE
The website you downloaded the DNS profile from will likely offer a few pre-signed versions of ESign as well. Download your preferred one through the following method:
- After tapping the Download button, you’ll see a dialog saying [WEBSITE ADDRESS] would like to install “ESign”. Tap Install.
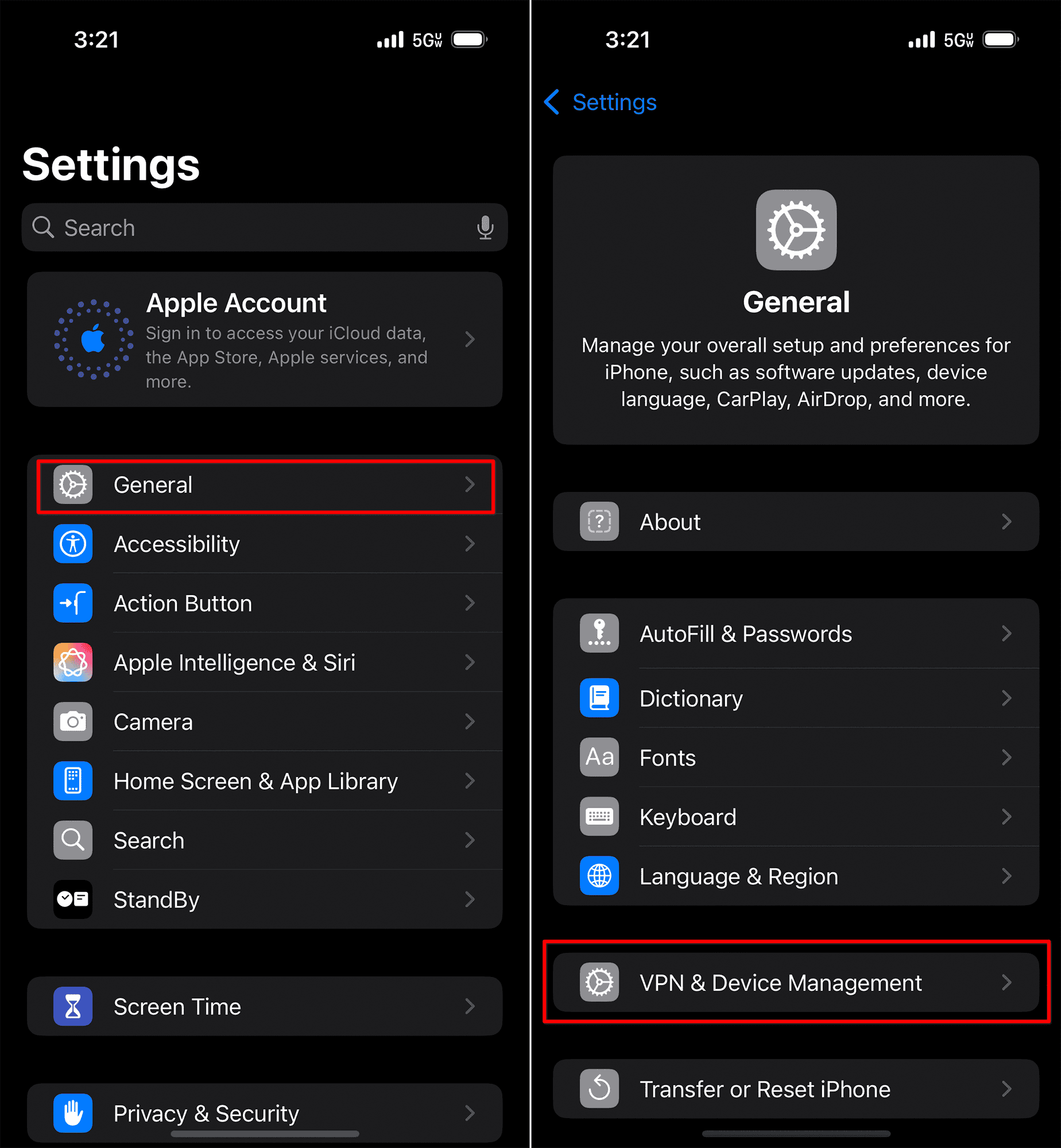
- Go to your home screen to check the installation progress. When it’s done, you’ll receive an Untrusted Enterprise Developer warning. Note the enterprise name and Tap Cancel.
- Go to Settings > General > VPN & Device Management. Under Enterprise App, tap the name that appeared in the previous step.
- Tap the Trust button.
Installing ESign Self-Signed
Just like you can sign apps on ESign’s page, you can sign the ESign app itself. That allows you to avoid DNS profiles and shady websites that go from clickbait to adware to potential malware installations. Here’s how to use ESign to sign ESign with your certificate signature (that’s a weird sentence, I know):
- Go to ESign’s page and tap Download IPA. You’ll see the usual download dialog from Safari. Tap Download.
- Now, go to the signing page. Upload your .p12 and .mobileprovision files, alongside ESign’s IPA file. You’ll see an “esign.yyyue.xyz” would like to install “ESign”. Tap Install.
 NOTE
NOTE
Using ESign
With the app installed, now it’s time to sideload stuff. ESign works pretty much like any other third-party iOS app store with sideloading capabilities. If you have used one previously, you’ll find it familiar.
The Files tab allows you to install certificates, either using .p12 and .mobileprovision files, or via pre-made .esigncert files. You can also sign and install standalone IPA files this way.
To add app repositories, go to the App Store tab and tap on the App Source button in the top right. After adding them, you can search and install your preferred apps.
The Apps tab shows your apps. They’re organized by “signed”, “not signed”, and “installed”.
Is ESign for iOS Safe?
There are a few things to consider about whether ESign is safe. That’s because the very definition of “safe” may mean a number of different things for each person.
If you take Apple’s definition of safe, for instance, ESign isn’t safe, but neither are any third-party app stores. That includes even reputable ones like AltStore PAL and Setapp, which are available only for users in the European Union. Thought, considering recent App Store malware discoveries and governments demanding backdoors, Apple itself wouldn’t be considered “safe” by Apple’s standards.
A reasonable cybersecurity-based approach wouldn’t necessarily consider ESign unsafe. The DNS installation method, however, is well into the definition of “unsafe”. You also need to consider that ESign doesn’t check the apps it is signing for malware. Therefore, the responsibility of not installing apps that may potentially present a security risk is up to you. An .ipa file promising, e.g., free access to paid streaming services, may very well host a slew of malicious code. This could put your data, and potentially your money, in danger.
Lastly, those with an “anything from China or Russia is dangerous” opinion will definitely want to steer clear from ESign. The app’s developer is Chinese, and the app states at the very beginning of its terms it collects usage information. ESign states it “conducts investigation, research, and analysis of user data”, “in order to improve the user’s experience and satisfaction”. There is some discussion in the sideloading community about what is being collected, and where is this data being sent. Whether this is a concern, though, is for you to decide.
Alternatives to ESign
Did the above get you to reconsider installing ESign on iOS? No problem, there are a few alternatives you may be interested in.
If you’re running an older iOS version, TrollStore may be an option. It only works up to iOS 17.0, however, and may raise similar concerns regarding security.

You may want to check iOSGods as well. I personally wouldn’t recommend it, because the service is ridden with ads. The paid version may be a gateway to paying for pirated content, too.
Another option is Aptoide, which is developed by the namesake company. To put things in perspective, Aptoide was one of the very first alternative app stores for Android — perhaps the first. The major downside is that, even in the European Union, it’s still in closed beta. Therefore, being able to use it at all is still hard. Also, their app catalog is quite small on iOS.
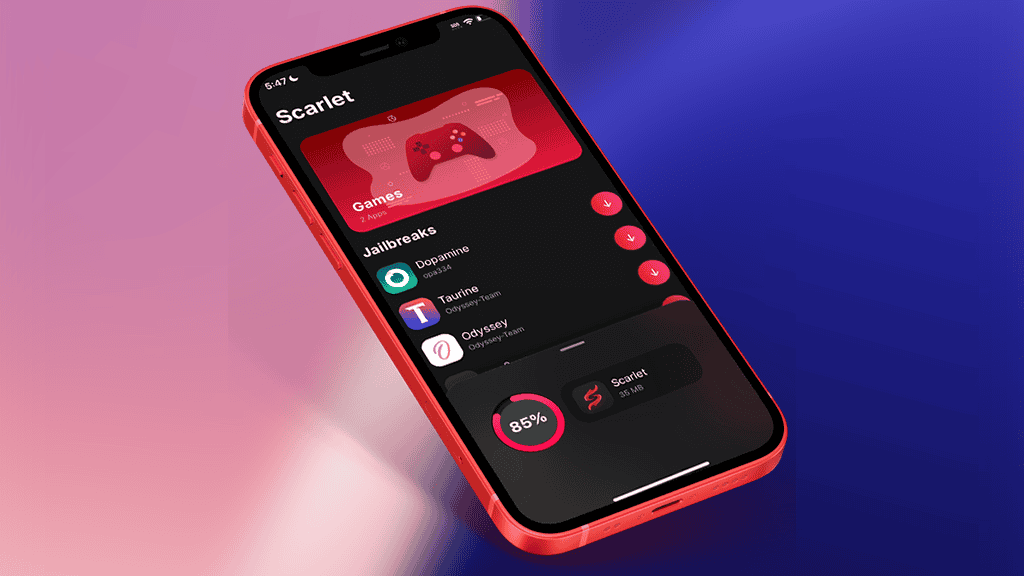
GBox and Scarlet are iOS apps more akin to ESign. That’s in the sense they are as much .ipa signing platforms as they are app stores — given you install the repositories. Out of the two, I’d recommend Scarlet for its looks, but both work similarly and well.
AltStore (the non-PAL version) and SideStore are sister projects: the latter is a fork of the former. They’re both very similar, so it’s a matter of personal taste.
Honorable mentions
Lastly, some mentions go to Feather and AppDB. Like AltStore, SideStore, and EU-only marketplaces, these focus more on being app stores. The main idea is to have a decent app catalog out of Apple’s walled garden. That way, you won’t need to hunt around for .ipa files. You’ll still need to provide certificates, though.

Sideloading is a lengthy and boresome process, and it’s that way by design. Apple thinks that, if it can’t convince you with arguments, the solution is tiring you out of the idea. If Hackintoshes and resoldered SSDs are any clue, this cat-and-mouse game will seemingly last a long time.